Attack Surface Management for SaaS Adoption
Attack Surface Management for the adoption of SaaS: It’s a phrase that’s buzzing around the tech world, and for good reason. We’re all moving to the cloud, embracing the flexibility and scalability of SaaS solutions. But with that move comes a whole new set of security challenges. This post dives deep into how Attack Surface Management (ASM) is crucial for navigating this increasingly complex landscape, protecting your business from the ever-growing threat of cyberattacks in a SaaS-centric world.
We’ll explore the key aspects of ASM, its practical applications, and what the future holds for this vital security discipline.
The rapid shift towards SaaS presents both incredible opportunities and significant risks. Understanding the unique vulnerabilities inherent in cloud-based applications is paramount. This isn’t just about patching software; it’s about understanding your entire attack surface – every exposed point where a malicious actor could potentially gain access to your sensitive data. We’ll look at how ASM helps identify, prioritize, and mitigate these risks, building a more robust and secure foundation for your organization.
Defining the SaaS Adoption Landscape
The Software as a Service (SaaS) model has fundamentally reshaped how businesses operate, transitioning from on-premise infrastructure to cloud-based solutions. This shift reflects a broader technological transformation impacting various industries, driving efficiency and fostering innovation. Understanding the current landscape of SaaS adoption is crucial for navigating its benefits and mitigating associated risks.The rapid expansion of SaaS adoption is undeniable.
Across sectors, from finance and healthcare to education and retail, organizations are increasingly relying on cloud-based applications for their core operations. This trend is driven by several key factors, leading to both opportunities and challenges.
SaaS Adoption Trends Across Industries, Attack surface management for the adoption of saas
The shift to SaaS is not uniform across all industries. While some sectors have embraced cloud solutions more readily than others, the overall trend indicates a significant and accelerating adoption rate. For example, the finance industry, traditionally cautious about data security, is progressively adopting SaaS for tasks like customer relationship management (CRM) and financial planning, driven by the need for scalability and real-time data access.
Similarly, healthcare providers are leveraging SaaS for electronic health records (EHR) and telehealth platforms, improving patient care and operational efficiency. However, regulatory compliance requirements in these sectors often present unique challenges to SaaS implementation. Retail businesses are rapidly adopting SaaS solutions for inventory management, e-commerce platforms, and supply chain optimization, enabling greater agility and responsiveness to market demands.
The education sector uses SaaS for learning management systems (LMS), collaborative tools, and student information systems, enhancing teaching and learning experiences.
Key Drivers and Challenges of SaaS Implementation
Several factors fuel the widespread adoption of SaaS. Cost savings, through reduced infrastructure investments and maintenance expenses, are a significant driver. Scalability and flexibility, allowing businesses to easily adjust their software needs as they grow or contract, are equally compelling. Improved collaboration, facilitated by cloud-based platforms, enhances team productivity and communication. Furthermore, the ease of deployment and rapid implementation of SaaS applications reduces time-to-market for new initiatives.
However, challenges remain. Data security and privacy concerns are paramount, particularly with sensitive data. Integration with existing legacy systems can be complex and costly. Vendor lock-in, the dependence on a single vendor, presents a potential risk. Finally, managing user access and permissions across multiple SaaS applications requires robust identity and access management (IAM) strategies.
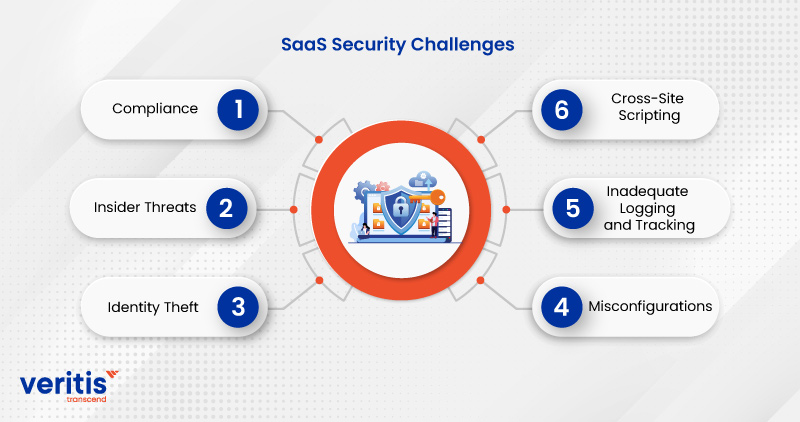
Security Concerns Arising from Increased SaaS Usage
The increasing reliance on SaaS applications brings inherent security risks. Data breaches, resulting from compromised vendor security or misconfigured user access, are a major concern. Data loss or corruption, due to unforeseen outages or system failures, can disrupt business operations. Compliance violations, stemming from inadequate data protection measures or failure to meet industry regulations, can lead to significant penalties.
Lack of visibility into the security posture of SaaS applications and the difficulty in enforcing consistent security policies across a multi-vendor environment pose additional challenges. For instance, a company using multiple CRM platforms from different vendors might find it difficult to maintain a unified security policy across all platforms. The lack of control over the underlying infrastructure can also increase the vulnerability of SaaS deployments.
Understanding Attack Surface Management (ASM)
Attack Surface Management (ASM) is crucial in today’s SaaS-heavy environment. It’s no longer enough to just secure your internal network; the expanding footprint of cloud-based applications and services creates a vast and constantly shifting attack surface that needs proactive monitoring and management. ASM helps organizations identify, prioritize, and remediate vulnerabilities across this expanded attack surface, minimizing the risk of breaches.ASM fundamentally involves identifying all assets connected to your organization, both within and outside your traditional network perimeter.
Securing SaaS adoption requires a robust attack surface management strategy, especially as we integrate more applications. This is where understanding development methodologies becomes crucial; for example, the shift towards low-code/no-code platforms like those discussed in this insightful article on domino app dev the low code and pro code future , impacts how we manage our attack surface. Ultimately, a well-defined approach to attack surface management is essential for any organization embracing SaaS and modern development practices.
This includes SaaS applications, cloud infrastructure, on-premises systems, and even shadow IT. Once identified, ASM solutions analyze these assets to pinpoint vulnerabilities, misconfigurations, and exposed credentials that could be exploited by attackers. The core functionalities include automated discovery, vulnerability assessment, risk prioritization, and remediation guidance. A key component is continuous monitoring to track changes in the attack surface and ensure that newly discovered vulnerabilities are addressed promptly.
ASM Solution Comparison
Several ASM solutions are available, each with its own strengths and weaknesses. The choice of the right tool depends heavily on an organization’s specific needs, size, and technical capabilities. The following table compares five popular ASM tools:
| Vendor | Key Features | Pricing Model | Integration Capabilities |
|---|---|---|---|
| Azure Sentinel | Vulnerability management, threat intelligence integration, security information and event management (SIEM) capabilities, automated threat detection and response. | Subscription-based, tiered pricing | Integrates with various Azure services and third-party tools via APIs and connectors. |
| CrowdStrike Falcon | Endpoint detection and response (EDR), threat intelligence, vulnerability assessment, and incident response capabilities. | Subscription-based, tiered pricing | Integrates with various security tools and platforms through APIs and connectors. |
| Rapid7 InsightVM | Vulnerability scanning, asset discovery, risk assessment, and remediation guidance. | Subscription-based, tiered pricing | Integrates with various IT infrastructure and security tools through APIs and connectors. |
| Tenable.io | Vulnerability management, asset discovery, risk assessment, and compliance reporting. | Subscription-based, tiered pricing | Integrates with various IT infrastructure and security tools through APIs and connectors. |
| Qualys | Vulnerability management, compliance management, asset discovery, and web application scanning. | Subscription-based, tiered pricing | Integrates with various IT infrastructure and security tools through APIs and connectors. |
Best Practices for Implementing an ASM Program
Implementing a successful ASM program requires a strategic approach. It’s not just about choosing the right tool; it’s about integrating ASM into a broader security strategy. This involves establishing clear ownership and responsibilities, defining a comprehensive asset inventory process, prioritizing remediation based on risk, and establishing clear communication channels. Regularly reviewing and updating the ASM program is essential to keep pace with the ever-changing threat landscape and the evolution of SaaS adoption within the organization.
For example, regularly scanning for newly discovered vulnerabilities and promptly addressing critical issues helps to maintain a strong security posture. Furthermore, integrating ASM with other security tools like SIEM and SOAR systems enhances overall security effectiveness and incident response capabilities. Finally, continuous employee training on security best practices is paramount to mitigating risks associated with human error.
The Intersection of ASM and SaaS Security
The shift to cloud-based SaaS applications has revolutionized how businesses operate, offering unprecedented flexibility and scalability. However, this transition also introduces a new set of security challenges that traditional on-premise security models often struggle to address. Understanding these unique vulnerabilities and leveraging Attack Surface Management (ASM) is crucial for maintaining a robust security posture in a SaaS-centric environment.SaaS applications, by their very nature, present a distributed and dynamic attack surface.
Unlike on-premise systems where security perimeters are relatively well-defined, SaaS applications exist within a shared responsibility model, where the vendor manages the underlying infrastructure while the customer is responsible for securing their own data and configurations. This shared responsibility can lead to blind spots if not properly managed, leaving organizations vulnerable to a wider range of threats.
Unique Security Challenges of SaaS Applications
The inherent characteristics of SaaS introduce several unique security risks. Data breaches, unauthorized access, misconfigurations, and insufficient identity and access management (IAM) are all amplified in the SaaS context. For example, a misconfigured SaaS application could inadvertently expose sensitive data to unauthorized users or even the public internet. Similarly, weak passwords or a lack of multi-factor authentication (MFA) can leave accounts vulnerable to credential stuffing attacks.
Furthermore, the rapid pace of SaaS adoption often outstrips an organization’s ability to effectively manage the resulting expanded attack surface, leading to increased risk.
Mitigating SaaS-Related Security Risks with ASM
Attack Surface Management (ASM) provides a comprehensive approach to identifying, assessing, and mitigating these SaaS-related risks. ASM solutions offer visibility into the entire SaaS ecosystem, including all applications, users, and configurations. This visibility allows security teams to proactively identify vulnerabilities and misconfigurations before they can be exploited. By continuously monitoring the attack surface, ASM can detect and alert on suspicious activity, enabling rapid response to potential threats.
Furthermore, ASM facilitates the implementation of strong security policies and controls, such as least privilege access, MFA, and regular security audits, ensuring that SaaS applications are configured securely and used responsibly.
Hypothetical Security Architecture for a SaaS-Heavy Organization
Imagine a company, “GlobalTech,” heavily reliant on SaaS applications for CRM, ERP, HR, and collaboration. Their security architecture would integrate ASM as a central component. The ASM solution would continuously scan and monitor all their SaaS applications, identifying vulnerabilities and misconfigurations. This data would feed into a centralized security information and event management (SIEM) system, providing a holistic view of security posture.
GlobalTech would implement strong IAM policies enforced by the ASM system, including MFA and least privilege access, minimizing the impact of potential breaches. Automated remediation workflows, triggered by ASM alerts, would quickly address identified vulnerabilities. Regular security assessments and penetration testing, guided by ASM insights, would ensure the ongoing security of their SaaS ecosystem. Finally, GlobalTech would maintain a comprehensive inventory of all their SaaS applications and associated configurations, constantly updated by the ASM system, enabling better risk management and compliance efforts.
This approach minimizes their attack surface, enhances their response capabilities, and improves overall security posture.
Practical Applications of ASM in SaaS Environments

Attack Surface Management (ASM) isn’t just a buzzword; it’s a critical component of a robust SaaS security strategy. In today’s interconnected world, where businesses rely heavily on SaaS applications and their integrations, understanding and managing your attack surface is paramount. This section delves into the practical applications of ASM within the context of SaaS, showing how it helps identify, prioritize, and ultimately mitigate risks.ASM tools provide a systematic approach to identifying vulnerabilities within a SaaS ecosystem.
These tools typically leverage automated discovery methods, scanning for exposed assets, misconfigurations, and vulnerabilities across your entire SaaS landscape. This includes not only the SaaS applications themselves but also their associated integrations, APIs, and user accounts. The output of these scans is then analyzed and prioritized based on factors such as severity, likelihood of exploitation, and business impact.
This allows security teams to focus their efforts on the most critical vulnerabilities first.
Identifying and Prioritizing SaaS Vulnerabilities with ASM Tools
ASM tools employ various techniques to identify vulnerabilities within a SaaS environment. These include automated discovery scans that identify exposed assets, configuration checks that look for misconfigurations, and vulnerability assessments that pinpoint known security flaws. Prioritization is typically based on a risk scoring system that combines vulnerability severity with the likelihood of exploitation and the potential impact on the business.
For example, a high-severity vulnerability in a critical application with a high likelihood of exploitation would receive a higher priority than a low-severity vulnerability in a less critical application. This prioritization helps security teams efficiently allocate resources and address the most significant risks. Sophisticated ASM platforms often provide dashboards visualizing this risk landscape, enabling better decision-making.
Reducing Attack Surface from SaaS Integrations and Third-Party APIs
The proliferation of SaaS integrations and third-party APIs significantly expands the attack surface. ASM helps mitigate this risk by providing visibility into these connections. By mapping out all integrations and APIs, ASM tools identify potential vulnerabilities stemming from insecure configurations or insecure coding practices within these third-party components. For instance, an ASM tool might detect an API with insufficient authentication, allowing unauthorized access to sensitive data.
This visibility allows security teams to enforce secure coding practices, implement robust authentication mechanisms, and negotiate stronger security controls with third-party vendors. The result is a reduced attack surface and a more secure SaaS ecosystem.
Integrating ASM into an Existing SaaS Security Framework
Integrating ASM into your existing SaaS security framework is a multi-step process that requires careful planning and execution.
- Step 1: Assessment and Planning: Begin by assessing your current SaaS security posture and identifying gaps. Determine the scope of your ASM implementation, including which SaaS applications and integrations will be included. Define clear goals and objectives for the ASM program.
- Step 2: Tool Selection and Deployment: Choose an ASM tool that aligns with your needs and budget. Consider factors such as scalability, integration capabilities, and reporting features. Deploy the chosen tool according to the vendor’s instructions, ensuring proper configuration and integration with existing security systems.
- Step 3: Data Collection and Analysis: Allow the ASM tool to collect data on your SaaS environment. Analyze the results to identify vulnerabilities and prioritize them based on risk. This often involves correlating vulnerability data with business context to understand the potential impact.
- Step 4: Remediation and Validation: Develop and implement remediation plans to address identified vulnerabilities. This might involve patching software, configuring security settings, or working with third-party vendors to resolve issues. After remediation, validate the effectiveness of the fixes to ensure the vulnerabilities have been successfully mitigated.
- Step 5: Continuous Monitoring and Improvement: ASM is not a one-time activity. Continuously monitor your SaaS environment for new vulnerabilities and changes in risk. Regularly review and update your ASM strategy to adapt to the ever-evolving threat landscape. This includes staying up-to-date on emerging threats and vulnerabilities.
Future Trends in ASM for SaaS
The rapid expansion of SaaS adoption presents a continuously evolving threat landscape. Understanding and adapting to these changes is crucial for maintaining robust security postures. Future trends in Attack Surface Management (ASM) for SaaS will be heavily influenced by the increasing sophistication of attacks and the ever-growing complexity of cloud environments. This necessitates a proactive and adaptive approach to security.The increasing reliance on SaaS applications introduces new vulnerabilities and attack vectors.
Traditional security approaches often struggle to keep pace with the dynamic nature of cloud-based services, making advanced ASM strategies essential.
Emerging Threats and Vulnerabilities in SaaS
The shift towards SaaS has introduced a new set of security challenges. These include vulnerabilities stemming from misconfigurations in cloud environments, API security flaws, and the increasing prevalence of sophisticated phishing and social engineering attacks targeting SaaS users. For example, a misconfigured access control list (ACL) on a SaaS application could expose sensitive data to unauthorized users or even malicious actors.
Similarly, vulnerabilities in the APIs used to integrate SaaS applications with other systems can create entry points for attackers. The rise of shadow IT, where employees use unsanctioned SaaS applications, further exacerbates the problem, creating blind spots in an organization’s security posture.
The Role of Automation and AI in Enhancing ASM for SaaS
Automation and Artificial Intelligence (AI) are poised to play a transformative role in enhancing ASM capabilities for SaaS. AI-powered tools can automate the discovery and assessment of attack surfaces, continuously monitoring for new vulnerabilities and misconfigurations. Machine learning algorithms can analyze vast amounts of security data to identify patterns and anomalies indicative of potential threats, enabling proactive mitigation strategies.
For instance, an AI-powered ASM system could automatically detect and alert security teams to a newly discovered vulnerability in a specific SaaS application used by the organization, even before a public exploit is available. This level of automation drastically reduces the time to remediation, minimizing the window of vulnerability. Furthermore, AI can help prioritize remediation efforts by focusing on the most critical vulnerabilities, optimizing resource allocation and improving overall security efficiency.
Evolution of ASM to Meet Future SaaS Challenges
The future of ASM for SaaS will be characterized by a greater emphasis on proactive threat detection, automated remediation, and continuous monitoring. We can expect to see the emergence of more integrated and comprehensive ASM solutions that seamlessly integrate with existing security tools and cloud platforms. For example, future ASM tools might incorporate features like automated vulnerability patching, integrated threat intelligence feeds, and real-time risk scoring to provide a holistic view of an organization’s SaaS security posture.
This integrated approach will help organizations proactively identify and mitigate risks, reducing their overall attack surface and improving their resilience against cyber threats. The increasing adoption of cloud-native security tools and the development of more sophisticated threat detection techniques will further enhance the effectiveness of ASM in SaaS environments. We can also expect to see a greater focus on security automation and orchestration, enabling organizations to automate many aspects of their security operations, from vulnerability scanning to incident response.
This will be crucial in managing the ever-growing complexity of SaaS environments and maintaining a robust security posture. For example, a company using multiple SaaS applications could leverage an automated system to automatically patch vulnerabilities across all their applications as soon as a new patch is released, minimizing downtime and exposure.
Case Studies: Attack Surface Management For The Adoption Of Saas
Real-world examples offer invaluable insights into the effectiveness – and pitfalls – of Attack Surface Management (ASM) in SaaS environments. By examining both successful and unsuccessful implementations, we can glean best practices and avoid common mistakes. The following case studies highlight crucial aspects of planning, execution, and ongoing maintenance within the context of SaaS security.
Successful ASM Implementation at GlobalTech
GlobalTech, a multinational corporation heavily reliant on SaaS applications for various business functions, successfully implemented an ASM program. Their initial challenge was the sheer volume and diversity of SaaS applications in use across different departments, leading to a fragmented and unmanageable attack surface. To address this, they first conducted a comprehensive SaaS inventory, utilizing both manual and automated discovery methods.
This provided a clear picture of their entire SaaS ecosystem, including applications, users, and associated permissions.Next, GlobalTech integrated their ASM solution with existing Security Information and Event Management (SIEM) and Identity and Access Management (IAM) systems. This allowed for automated vulnerability detection and real-time threat monitoring. The ASM platform continuously monitored for misconfigurations, outdated software, and unauthorized access attempts.
Furthermore, they established a robust vulnerability remediation process, prioritizing fixes based on risk level and business impact. This involved close collaboration between IT, security, and individual business units to ensure timely and effective patching and configuration changes. GlobalTech also invested in employee training to increase awareness of SaaS security risks and best practices. This multi-faceted approach resulted in a significant reduction in their attack surface and improved overall security posture.
Failed ASM Implementation at InnovateCorp
InnovateCorp’s ASM implementation, conversely, proved less successful. They initially adopted a “set it and forget it” approach, failing to integrate their ASM solution with other security tools and neglecting regular monitoring and updates. The lack of integration resulted in incomplete data and a fragmented view of their attack surface. Furthermore, they underestimated the time and resources required for ongoing maintenance and remediation.
This led to a backlog of vulnerabilities and a delayed response to emerging threats. The absence of employee training also contributed to the failure, leaving employees vulnerable to phishing attacks and other social engineering tactics.
The failure of InnovateCorp’s ASM program underscores the importance of continuous monitoring, integration with other security tools, and ongoing employee training. A passive approach to ASM is ineffective; it requires active management, regular updates, and a commitment to ongoing remediation. Ignoring these crucial aspects can lead to a false sense of security and ultimately, increased vulnerability.
Comparison of Approaches and Best Practices
The contrasting experiences of GlobalTech and InnovateCorp highlight several key differences. GlobalTech adopted a proactive, integrated approach, emphasizing continuous monitoring, proactive vulnerability remediation, and employee training. InnovateCorp, on the other hand, took a passive approach, lacking integration, regular updates, and adequate training. This highlights the critical need for a holistic strategy that encompasses not only the technology but also the people and processes involved.Best practices for successful ASM implementation in SaaS environments include: a comprehensive SaaS inventory, integration with existing security tools, automated vulnerability detection and remediation, regular monitoring and updates, and robust employee training.
Pitfalls to avoid include a passive approach, lack of integration, inadequate resource allocation, and neglecting employee training. A successful ASM program requires a commitment to ongoing management and a culture of security awareness across the entire organization.
Final Thoughts
Successfully navigating the SaaS security landscape requires a proactive and comprehensive approach. Attack Surface Management isn’t just a nice-to-have; it’s a necessity. By understanding your attack surface, implementing effective ASM strategies, and staying ahead of emerging threats, you can significantly reduce your risk and protect your valuable data. The journey towards a secure SaaS environment is ongoing, but with the right tools and understanding, you can confidently embrace the cloud while mitigating the inherent security challenges.
So, let’s build a safer digital future, one managed attack surface at a time!
FAQ Summary
What are the common mistakes companies make when adopting SaaS?
Common mistakes include neglecting proper security configurations, failing to adequately vet third-party SaaS providers, and lacking a comprehensive data loss prevention strategy.
How much does ASM software typically cost?
Pricing varies greatly depending on the vendor, features, and the size of your organization. Expect a range from a few hundred dollars per month to tens of thousands.
Can ASM tools integrate with my existing security infrastructure?
Most modern ASM tools offer various integration capabilities with SIEMs, SOAR platforms, and other security solutions. However, compatibility should be verified before purchasing.
Is ASM only for large enterprises?
No, even small and medium-sized businesses (SMBs) can benefit from ASM. There are solutions available that cater to different organizational sizes and budgets.