Australian Immigration Offices Face Critical Cyber Threats
Australian immigration offices are extremely vulnerable to cyber attacks, a chilling reality that threatens the integrity of our immigration system and the personal data of countless applicants. We’re not talking about minor inconveniences here; we’re talking about sophisticated attacks that could expose sensitive personal information, disrupt vital services, and severely damage Australia’s reputation on the world stage. This post delves into the vulnerabilities, the potential consequences, and what needs to be done to secure our digital borders.
The sheer volume and sophistication of cyberattacks targeting government agencies worldwide are alarming. Australian immigration offices, with their vast databases of personal information, are prime targets. From data breaches exposing sensitive personal details to ransomware attacks crippling vital services, the potential damage is immense. This vulnerability isn’t just a theoretical concern; it’s a real and present danger that demands immediate attention and robust solutions.
Vulnerability Assessment of Australian Immigration Offices
The increasing reliance on digital systems within Australian immigration offices presents a significant challenge in maintaining data security and operational integrity. Government agencies, including those managing immigration processes, are prime targets for cybercriminals due to the sensitive personal data they hold and the potential disruption a successful attack can cause. This assessment explores the vulnerabilities within the IT infrastructure of these offices and the potential consequences of exploitation.
Common Cyberattacks Targeting Government Agencies
Government agencies are frequently targeted by various cyberattacks, including phishing campaigns, ransomware attacks, and denial-of-service (DoS) attacks. Data breaches are a particularly serious concern, as they can expose sensitive personal information like passport details, visa applications, and biometric data. The impact of a data breach can be devastating, leading to identity theft, financial loss for individuals, and significant reputational damage for the government agency involved.
Furthermore, disruptions to immigration processes caused by cyberattacks can lead to delays in visa applications, travel disruptions for individuals, and broader economic consequences.
Specific Vulnerabilities in Australian Immigration Office IT Infrastructure
Three key vulnerabilities that could be exploited by cybercriminals in Australian immigration offices include outdated software, insufficient employee training on cybersecurity best practices, and inadequate network security. Outdated software often contains known vulnerabilities that cybercriminals can exploit to gain unauthorized access. Insufficient employee training can lead to human error, such as clicking on malicious links in phishing emails, which can provide a pathway for attackers to infiltrate systems.
Inadequate network security, such as a lack of robust firewalls and intrusion detection systems, can leave the network vulnerable to various attacks.
Potential Consequences of a Successful Cyberattack
A successful cyberattack on an Australian immigration office could have severe consequences. Data loss would be a major concern, potentially exposing sensitive personal information of applicants and citizens. Service disruption could lead to significant delays in visa processing, impacting individuals’ travel plans and potentially harming Australia’s international reputation. Reputational damage resulting from a data breach or service disruption could erode public trust in the government’s ability to protect sensitive information.
Financial penalties and legal ramifications could also arise from non-compliance with data protection regulations. In addition, the recovery process following a successful cyberattack can be costly and time-consuming, requiring significant resources to restore systems and data.
Vulnerability Types and Mitigation Strategies
| Vulnerability Type | Exploitation Method | Potential Impact | Mitigation Strategy |
|---|---|---|---|
| Outdated Software | Exploiting known vulnerabilities in outdated software to gain unauthorized access. | Data breach, service disruption, reputational damage. | Regular software updates and patching, vulnerability scanning. |
| Phishing Attacks | Tricking employees into revealing credentials or downloading malware via deceptive emails. | Data breach, malware infection, ransomware attack. | Security awareness training, multi-factor authentication, email filtering. |
| Weak Passwords | Guessing or cracking easily guessable passwords. | Unauthorized access to systems and data. | Enforcing strong password policies, password managers. |
| Insufficient Network Security | Exploiting vulnerabilities in network infrastructure (e.g., firewalls, intrusion detection systems). | Denial-of-service attacks, data breaches. | Implementing robust firewalls, intrusion detection/prevention systems, regular security audits. |
| Insider Threats | Malicious or negligent actions by employees with access to sensitive data. | Data theft, sabotage, service disruption. | Background checks, access control policies, regular security awareness training. |
Cybersecurity Measures and their Effectiveness
The vulnerability of Australian immigration offices to cyberattacks necessitates a thorough examination of their current cybersecurity measures and a comparison with international best practices. This analysis will highlight areas for improvement and suggest concrete steps to strengthen the security posture of these crucial government institutions. The effectiveness of current systems, employee training, and potential improvements will be explored.
Australian immigration offices employ a range of cybersecurity measures, including firewalls, intrusion detection systems, and data encryption. However, the effectiveness of these measures varies significantly across different offices, and some fall short of the robust standards recommended by international organizations like NIST (National Institute of Standards and Technology) and ENISA (European Union Agency for Cybersecurity). A comprehensive review is needed to identify gaps and implement necessary upgrades.
Authentication and Authorization Mechanisms
The effectiveness of authentication and authorization mechanisms in protecting sensitive immigration data is paramount. While multi-factor authentication (MFA) is increasingly implemented, its adoption isn’t universal across all offices. Examples of weaknesses include reliance on easily guessable passwords in some systems and a lack of robust access control policies, potentially allowing unauthorized access to sensitive data. The use of strong, unique passwords coupled with MFA, coupled with regular password rotation, would significantly enhance security.
Furthermore, the implementation of a robust privilege access management (PAM) system, controlling and monitoring access to sensitive data, is crucial. Without a comprehensive PAM, even strong authentication can be circumvented by users with excessive privileges.
Employee Training and Awareness Programs
Effective employee training is crucial for mitigating cyber threats. Phishing attacks, social engineering, and malware remain significant threats, and employees are often the weakest link in the security chain. A comprehensive training program should include regular awareness sessions, simulated phishing attacks, and clear guidelines on handling suspicious emails and attachments.
Sample Training Module:
Module 1: Introduction to Cybersecurity Threats
-Overview of common threats (phishing, malware, ransomware). Module 2: Recognizing and Reporting Phishing Attempts
– Practical exercises identifying suspicious emails and websites. Module 3: Secure Password Practices
-Guidelines for creating and managing strong, unique passwords. Module 4: Data Security and Handling
– Procedures for handling sensitive data, including encryption and secure storage. Module 5: Social Engineering Awareness
-Understanding and recognizing social engineering tactics.
Module 6: Incident Response Procedures
-Steps to take in case of a security incident, including reporting procedures. This module should be delivered through a combination of online training, interactive workshops, and regular refreshers.
Crucial Cybersecurity Improvements
Several crucial improvements could significantly enhance the security posture of Australian immigration offices. These improvements should be prioritized and implemented strategically:
- Implement a centralized security information and event management (SIEM) system: This will provide real-time monitoring and threat detection across all offices.
- Mandate multi-factor authentication (MFA) across all systems: This will significantly reduce the risk of unauthorized access.
- Conduct regular security audits and penetration testing: Identify vulnerabilities and weaknesses before malicious actors can exploit them.
- Invest in advanced threat detection and response capabilities: This includes implementing artificial intelligence (AI) and machine learning (ML) based security solutions.
- Strengthen data encryption and backup procedures: Ensure sensitive data is protected both in transit and at rest, with regular backups stored securely offline.
Data Protection and Privacy Concerns: Australian Immigration Offices Are Extremely Vulnerable To Cyber Attacks

The vulnerability of Australian immigration offices to cyberattacks presents significant risks, none greater than the potential for data breaches involving the sensitive personal information of immigration applicants. This sensitive data, including biometric information, financial details, and health records, demands the highest level of protection, both legally and ethically. Failure to adequately safeguard this information can have devastating consequences for individuals and severely damage public trust in the immigration system.The legal and ethical implications of a data breach are far-reaching.
Under the Australian Privacy Act 1988, organizations handling personal information have obligations to take reasonable steps to protect that information from misuse, interference, loss, and unauthorized access, modification, or disclosure. A breach can lead to significant fines, reputational damage, and legal action from affected individuals. Ethically, a breach represents a profound failure to uphold the trust placed in the immigration system by vulnerable individuals seeking refuge or permanent residency.
The potential for identity theft, fraud, and emotional distress caused by a data breach is substantial.
Legal and Ethical Implications of a Data Breach
A data breach involving sensitive personal information of immigration applicants carries severe legal and ethical consequences. The Australian Privacy Act 1988 mandates organizations to implement reasonable security measures to protect personal information. Breaches can result in significant penalties under the Act, including substantial fines and reputational damage. Furthermore, individuals affected by a breach may pursue legal action for compensation for losses incurred, including financial losses and emotional distress.
Ethically, a breach represents a violation of trust, particularly given the vulnerable position of many immigration applicants. The potential for exploitation and further harm to already vulnerable individuals is a serious ethical consideration. Transparency and accountability are crucial in mitigating the damage caused by a breach.
Strategies for Ensuring Data Privacy and Compliance
Implementing robust data protection measures is paramount. This includes adhering to the Australian Privacy Act 1988 and relevant international standards like the GDPR, even where not directly applicable. Strong access controls, encryption both in transit and at rest, regular security audits, and employee training on data security protocols are essential. Data minimization – collecting only necessary data and retaining it only for as long as required – is crucial.
Implementing a Data Loss Prevention (DLP) system to monitor and prevent sensitive data from leaving the network unauthorized is also vital. Regular penetration testing and vulnerability assessments should be conducted to identify and address weaknesses proactively. Finally, a well-defined incident response plan is necessary to manage and mitigate the impact of any breach.
Hypothetical Data Breach Scenario and Incident Response
Imagine a scenario where a malicious actor gains unauthorized access to an immigration office’s database through a phishing attack targeting an employee. The attacker exfiltrates a significant amount of personal data, including passport numbers, addresses, and health information of thousands of applicants. The incident response would involve immediate containment of the breach, isolating affected systems and preventing further data loss.
A forensic investigation would be launched to determine the extent of the breach and identify the attacker. Notification of affected individuals and relevant authorities (like the Office of the Australian Information Commissioner) is crucial, along with public communication to manage reputational damage. Remediation involves restoring data integrity, enhancing security measures, and implementing preventative measures to avoid future breaches.
Post-incident review is vital to learn from the event and improve security protocols.
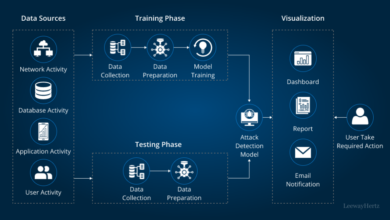
Data Lifecycle Flowchart
The following describes a flowchart illustrating the data lifecycle within an Australian immigration office. The flowchart would begin with Data Collection, where data is gathered through various channels (applications, interviews, etc.). Security controls at this stage include data validation and sanitization to prevent malicious input. Next is Data Processing, where data is verified, analyzed, and used for decision-making.
Seriously, the news about Australian immigration offices being vulnerable to cyberattacks is terrifying. We need robust, secure systems, and that’s where advancements like those discussed in domino app dev the low code and pro code future become crucial. Improved application development could help shore up these vital systems and prevent sensitive data breaches. The stakes are incredibly high when dealing with immigration data; we need to prioritize stronger digital defenses immediately.
Security controls here include access control lists restricting access to authorized personnel only, with different access levels based on roles. Then comes Data Storage, where data is securely stored in encrypted databases and servers. Security controls involve encryption, regular backups, and physical security of data centers. Data Usage involves accessing and utilizing the data for processing applications.
Security controls include multi-factor authentication, audit trails, and regular security reviews. Finally, Data Disposal involves securely deleting data when it is no longer needed, complying with retention policies. Security controls here involve secure deletion methods to prevent data recovery. The flowchart would visually represent these stages and their associated security controls using standard flowchart symbols (rectangles for processes, diamonds for decisions, etc.).
International Best Practices and Collaboration

Australia’s immigration system faces significant cybersecurity challenges, necessitating a thorough examination of international best practices and collaborative efforts to enhance its resilience. By learning from other nations and engaging in global partnerships, Australia can bolster its defenses and protect sensitive data. This involves not only adopting advanced technologies but also fostering a culture of proactive security awareness and continuous improvement.
A comparative analysis reveals that many developed nations, including the UK, Canada, and the US, have implemented more sophisticated cybersecurity frameworks than Australia. These frameworks often incorporate proactive threat hunting, advanced analytics for early detection of anomalies, and robust incident response plans. Areas where Australia could improve include investing more heavily in employee cybersecurity training, adopting zero-trust architectures, and enhancing the integration of artificial intelligence and machine learning into its security infrastructure.
Furthermore, a more robust public-private partnership approach, fostering information sharing and collaboration between government agencies and the private sector, could significantly improve Australia’s overall cybersecurity posture.
International Organizations Offering Cybersecurity Guidance
Several international organizations provide valuable guidance for governments on cybersecurity best practices. Their recommendations emphasize a holistic approach encompassing technology, processes, and people. Understanding these recommendations is crucial for improving Australia’s immigration cybersecurity.
Three key organizations are the Organisation for Economic Co-operation and Development (OECD), the International Telecommunication Union (ITU), and the Cybersecurity and Infrastructure Security Agency (CISA) of the United States. The OECD offers guidelines on digital government security, emphasizing risk management and international cooperation. The ITU focuses on global cybersecurity standards and frameworks, promoting interoperability and collaboration between nations. CISA provides comprehensive resources and guidance on various cybersecurity issues, including incident response and threat intelligence sharing.
Their combined recommendations highlight the importance of strong authentication, data encryption, regular security audits, vulnerability management, and employee training.
Benefits of International Collaboration in Cybersecurity
International collaboration offers significant advantages in addressing cyber threats targeting immigration systems. Sharing threat intelligence allows agencies to proactively identify and mitigate emerging risks. A coordinated response to attacks can significantly reduce the impact and facilitate faster recovery. Joint exercises and capacity building initiatives enhance the overall cybersecurity capabilities of participating nations.
The benefits extend beyond immediate threat response. Collaboration fosters the development of common standards and best practices, promoting interoperability and streamlining information exchange between immigration agencies globally. This leads to a more resilient and interconnected global system better equipped to withstand cyberattacks. The development of shared resources, such as threat intelligence platforms and incident response playbooks, further strengthens the collective defence posture.
Hypothetical Scenario: Successful International Cooperation in Responding to a Cyberattack
Imagine a sophisticated phishing campaign targeting immigration agencies in Australia, Canada, and the UK. The attackers successfully compromise some systems, attempting to steal personal data of applicants.
Upon detection, the Australian Cyber Security Centre (ACSC) immediately shares the threat intelligence with its counterparts in Canada’s Communications Security Establishment (CSE) and the UK’s National Cyber Security Centre (NCSC). The three agencies collaborate to identify the source of the attack, analyse the malware, and develop a coordinated response. The ACSC leads in developing a patch for the vulnerability exploited in the attack, while the CSE shares its expertise in identifying and neutralizing the attackers’ infrastructure.
The NCSC contributes by coordinating communications with affected individuals and managing public relations. This coordinated effort quickly neutralizes the threat, minimizes data breaches, and strengthens the collective resilience of the three nations’ immigration systems. The roles are distributed based on each agency’s specific expertise and resources, ensuring efficient and effective response.
Technological Solutions and Future Recommendations
The vulnerability of Australian immigration offices to cyberattacks necessitates a proactive approach to bolstering cybersecurity infrastructure. Implementing advanced technologies and enhancing existing security measures are crucial steps in mitigating risks and safeguarding sensitive data. This section explores three emerging technologies and proposes a prioritized list of technological upgrades, considering both budgetary constraints and realistic implementation timelines.
Artificial Intelligence in Cybersecurity, Australian immigration offices are extremely vulnerable to cyber attacks
AI offers significant potential for enhancing cybersecurity. AI-powered systems can analyze vast amounts of data to identify anomalies and potential threats in real-time, far exceeding the capabilities of traditional security systems. For example, AI can detect unusual login attempts, identify malware, and predict potential attacks based on historical data and emerging threat patterns. This proactive approach allows for swift responses and minimizes the impact of successful breaches.
However, limitations exist. AI systems require extensive training data, and their effectiveness depends heavily on the quality and quantity of this data. Furthermore, sophisticated attackers may attempt to circumvent AI-based defenses through adversarial attacks, specifically designed to fool the AI system. The implementation of AI also requires significant investment in infrastructure and expertise.
Blockchain Technology for Data Integrity
Blockchain’s decentralized and immutable nature makes it ideal for securing sensitive data. By storing immigration records on a blockchain network, the integrity and authenticity of the data can be significantly enhanced. Any unauthorized alteration would be immediately detectable, improving transparency and accountability. For example, a blockchain system could securely manage visa applications, ensuring that records cannot be tampered with and maintaining a verifiable audit trail.
However, the scalability of blockchain technology for large-scale applications remains a challenge. The complexity of integrating blockchain into existing systems and the need for specialized expertise represent significant barriers to implementation. Furthermore, the energy consumption associated with some blockchain networks is a concern.
Advanced Encryption Techniques
Robust encryption is fundamental to cybersecurity. Implementing advanced encryption techniques, such as post-quantum cryptography, which is designed to resist attacks from quantum computers, is crucial to future-proofing the security of immigration data. Advanced encryption algorithms, combined with strong key management practices, can significantly reduce the risk of data breaches. For example, employing end-to-end encryption for all communications and data storage can protect sensitive information even if a system is compromised.
However, the complexity of implementing and managing advanced encryption can be significant, requiring specialized skills and potentially impacting system performance. The cost of implementing and maintaining these systems also needs to be considered.
Prioritized Technological Upgrades
Considering budget constraints and implementation timelines, a prioritized approach to technological upgrades is recommended. Phase 1 should focus on implementing robust multi-factor authentication (MFA) across all systems and improving employee cybersecurity awareness training. Phase 2 would involve upgrading existing security information and event management (SIEM) systems with AI-powered threat detection capabilities. Phase 3 would focus on exploring the feasibility of blockchain technology for specific high-value data sets, starting with pilot projects.
The implementation of post-quantum cryptography should be considered a long-term goal, aligned with industry standards and technological advancements.
Proposed Multi-Layered Security Architecture
Imagine a layered security system akin to a castle’s defenses. The outermost layer comprises perimeter security, including firewalls, intrusion detection systems, and robust network segmentation. The next layer involves endpoint security, protecting individual computers and devices with antivirus software, endpoint detection and response (EDR) tools, and strong access controls. The innermost layer safeguards sensitive data with advanced encryption, data loss prevention (DLP) tools, and regular data backups stored in secure offsite locations.
This multi-layered approach provides comprehensive protection, ensuring that even if one layer is compromised, other layers remain in place to prevent a complete breach. The system is constantly monitored and updated through a central Security Operations Center (SOC) using AI-driven threat intelligence.
Final Summary
The vulnerability of Australian immigration offices to cyberattacks is a serious issue demanding immediate and comprehensive action. While existing security measures offer some protection, significant improvements are needed to truly safeguard sensitive data and maintain the integrity of the immigration process. A multi-pronged approach, incorporating technological upgrades, enhanced employee training, and international collaboration, is essential to bolstering cybersecurity and protecting the nation’s digital borders.
The future of secure immigration processing depends on it.
Key Questions Answered
What types of data are most at risk in a cyberattack on Australian immigration offices?
Applicant personal information (names, addresses, dates of birth, passport details), visa application details, biometric data, and internal government documents are all highly vulnerable.
What is the role of employee training in preventing cyberattacks?
Employee training is crucial. It equips staff to recognize and report phishing attempts, understand password security, and follow safe data handling practices. Regular training and awareness programs significantly reduce the risk of human error, a major vulnerability.
What are the legal consequences of a data breach?
A data breach can lead to hefty fines under the Australian Privacy Act, legal action from affected individuals, and reputational damage for the government. Compliance with regulations like GDPR (if applicable) is also paramount.
How can international collaboration improve cybersecurity?
Sharing threat intelligence, best practices, and coordinated responses to cross-border attacks enhances overall security. International cooperation allows for faster response times and more effective mitigation strategies.