Authentication Is Outdated A New Approach to Identification
Authentication is outdated a new approach to identification – Authentication Is Outdated: A New Approach to Identification – passwords and even multi-factor authentication (MFA) are feeling increasingly creaky in today’s digital world. We’re facing a perfect storm of sophisticated cyberattacks and user frustration with endless login processes. This isn’t just about security; it’s about creating a seamless and intuitive online experience. It’s time to explore the exciting new frontiers of identification, from behavioral biometrics to decentralized identity systems, and see how they can revolutionize how we prove who we are online.
This post delves into the limitations of traditional methods, highlighting vulnerabilities and exploring emerging technologies that offer enhanced security and improved user experience. We’ll examine the privacy and ethical considerations surrounding these new approaches, and look at successful implementations that pave the way for a more secure and user-friendly digital future. Get ready to ditch the password fatigue and embrace the future of identification!
The Limitations of Traditional Authentication Methods: Authentication Is Outdated A New Approach To Identification
For years, we’ve relied on passwords and, more recently, multi-factor authentication (MFA) to secure our digital lives. However, these methods, while offering a degree of protection, are increasingly showing their limitations in the face of sophisticated cyberattacks and evolving user expectations. This post delves into the vulnerabilities inherent in these traditional approaches.
Password-Based System Vulnerabilities
Password-based systems, the cornerstone of authentication for decades, are inherently vulnerable. The reliance on easily guessable or reusable passwords presents a significant security risk. Weak passwords, often chosen for convenience, are easily cracked using brute-force attacks or dictionary attacks. Furthermore, phishing attacks, where malicious actors trick users into revealing their credentials, remain a highly effective method of compromising accounts.
Data breaches, exposing millions of passwords in plain text or easily crackable hashes, further exacerbate the problem. The inherent weaknesses of password-based systems highlight the need for more robust and secure authentication methods.
Multi-Factor Authentication (MFA) Fatigue
While MFA adds an extra layer of security by requiring multiple verification factors (e.g., password, one-time code from an authenticator app, biometric scan), its effectiveness is hampered by “MFA fatigue.” Users, bombarded with multiple authentication prompts throughout the day, often bypass MFA for convenience, especially when dealing with less critical accounts. This circumvention significantly reduces the security benefits of MFA.
The constant need to juggle multiple authentication methods can also lead to user frustration and reduced productivity. This demonstrates that even improved security measures can be undermined by user behavior and the inherent friction they introduce.
Examples of Successful Attacks Exploiting Traditional Authentication Methods
The 2017 Equifax data breach, resulting from a vulnerability in their systems that allowed attackers to exploit a known Apache Struts flaw, exposed the personal information of nearly 150 million people. This highlights the dangers of outdated systems and inadequate patching. Another example is the 2013 Target data breach, where hackers gained access to customer payment information through a compromised third-party vendor.
This demonstrates the vulnerability of supply chains and the importance of robust security measures across an entire organization. These breaches underscore the limitations of relying solely on passwords and even MFA, as attackers constantly seek new ways to bypass these security measures.
Comparison of Authentication Methods
The following table compares password-based authentication, MFA, and biometrics in terms of security and user experience:
| Method | Security | User Experience | Cost |
|---|---|---|---|
| Password-Based | Low (vulnerable to brute-force, phishing, etc.) | High (easy to use, but requires remembering passwords) | Low |
| MFA | Medium (significantly improves security but susceptible to MFA fatigue) | Medium (more secure but can be inconvenient) | Medium |
| Biometrics | High (difficult to replicate, but vulnerable to spoofing) | High (convenient but can be intrusive and require specialized hardware) | High |
Emerging Technologies in Identification
The limitations of traditional authentication methods are clear: passwords are easily compromised, and even multi-factor authentication can be circumvented with sophisticated attacks. Fortunately, a new wave of technologies is emerging, offering more robust and user-friendly identification solutions. These advancements leverage behavioral biometrics, blockchain technology, and decentralized identity systems to create a more secure and privacy-respecting digital landscape.
Behavioral Biometrics for Authentication
Behavioral biometrics offer a powerful alternative to traditional methods by analyzing user behavior patterns. Instead of relying on static identifiers like passwords or fingerprints, this approach focuses on dynamic characteristics such as typing rhythm, mouse movements, and scrolling habits. These unique patterns are difficult to replicate, making it a robust security measure. For example, a system could analyze the subtle variations in how a user types their password, creating a unique behavioral fingerprint.
Even if someone gains access to their password, their typing style would likely differ significantly, triggering an alert. The continuous monitoring aspect of behavioral biometrics also provides an extra layer of security, detecting anomalies in real-time and flagging suspicious activity. This proactive approach can effectively mitigate the risks associated with compromised credentials or malware.
Blockchain Technology for Secure Identity Management
Blockchain technology, known for its secure and transparent nature, offers a promising solution for managing digital identities. By storing identity data on a distributed ledger, blockchain eliminates the single point of failure inherent in centralized systems. This decentralized approach makes it significantly more resistant to hacking and data breaches. Furthermore, blockchain’s cryptographic features ensure the integrity and authenticity of identity information, preventing unauthorized modifications.
Imagine a system where your identity is securely stored on a blockchain, accessible only with your cryptographic key. This would allow you to selectively share verified attributes with different services, providing granular control over your personal data while maintaining its security. Such a system could revolutionize how we manage our digital identities, enhancing privacy and security.
Decentralized vs. Centralized Identity Systems: Security Implications
Decentralized identity systems, often built on blockchain technology, offer enhanced security and privacy compared to their centralized counterparts. In a centralized system, a single entity controls all user data, making it a vulnerable target for cyberattacks. A breach in a centralized system can compromise the identities of millions of users. Decentralized systems, on the other hand, distribute the control and responsibility for identity management across multiple nodes, making them significantly more resilient to attacks.
The loss of a single node doesn’t compromise the entire system. Furthermore, users have greater control over their data in a decentralized system, choosing what information to share and with whom. This granular control enhances privacy and reduces the risk of data misuse. However, decentralized systems can be more complex to implement and manage than centralized ones, requiring careful consideration of scalability and interoperability.
Passwordless Authentication Systems: Successful Implementations
Passwordless authentication systems are gaining traction as a more secure and user-friendly alternative to traditional password-based logins. These systems leverage various technologies, including biometrics, one-time passwords (OTPs), and public key cryptography, to verify user identity without requiring passwords. Google’s “passwordless” login, which utilizes a combination of phone verification and security keys, is a prime example. This system allows users to log into their Google accounts without entering a password, relying instead on a secure, second-factor authentication method.
Microsoft’s Azure Active Directory also offers passwordless authentication options, utilizing methods like FIDO2 security keys and Windows Hello facial recognition. These successful implementations demonstrate the feasibility and effectiveness of passwordless authentication, paving the way for a more secure and streamlined online experience.
Okay, so we all know password-based authentication is, frankly, ancient history. We need something better, a more seamless approach to identification. This is where the exciting advancements in application development come in, like those explored in this article on domino app dev the low code and pro code future , which could totally revolutionize how we build secure, user-friendly systems.
Ultimately, the future of secure identification hinges on innovative development practices, and that’s where the real game-changer lies.
Privacy and Security Implications of New Approaches
The shift away from traditional passwords towards more advanced biometric and behavioral authentication methods offers significant advantages in terms of usability and security. However, this transition also introduces a new set of privacy and security challenges that require careful consideration and robust mitigation strategies. The inherent sensitivity of the data involved necessitates a proactive approach to safeguarding user information and maintaining trust.The increased reliance on sophisticated technologies, particularly artificial intelligence (AI), in identification processes presents both opportunities and risks.
While AI can enhance accuracy and efficiency, it also raises concerns regarding bias, transparency, and the potential for misuse. Balancing the benefits of these new technologies with the need to protect individual privacy is a crucial task for developers, policymakers, and users alike.
Potential Privacy Risks Associated with Advanced Biometric Identification
Biometric data, such as fingerprints, facial scans, and voice prints, is inherently sensitive. A breach of this data can have far-reaching consequences, leading to identity theft, fraud, and even physical harm. For instance, a compromised facial recognition system could be used to unlock sensitive information or impersonate an individual. The persistent nature of biometric data—unlike passwords which can be changed—exacerbates these risks.
Data minimization, meaning collecting only the necessary biometric data, and strict access control measures are vital to mitigate these threats. Furthermore, the potential for bias in biometric systems, leading to disproportionate misidentification of certain demographics, needs careful consideration and ongoing monitoring.
The Importance of Data Anonymization and Encryption in New Authentication Systems
Data anonymization and encryption are paramount to protecting user privacy in passwordless authentication systems. Anonymization techniques, such as differential privacy or data masking, can help to obscure identifying information while preserving the utility of the data for authentication purposes. Strong encryption, using robust algorithms and key management practices, is crucial to prevent unauthorized access to sensitive biometric or behavioral data, even if a breach occurs.
For example, end-to-end encryption ensures that only the authorized user and the authentication system can access the decrypted data. Regular security audits and penetration testing are also essential to identify and address vulnerabilities in the system.
Ethical Considerations of Using AI in Identification Processes
The use of AI in identification processes raises several ethical considerations. Algorithmic bias, for instance, can lead to unfair or discriminatory outcomes. AI models trained on biased data may misidentify or unfairly target certain demographic groups. Transparency and explainability are also crucial; users should understand how AI-driven identification systems work and the basis for their decisions. Accountability mechanisms are needed to address errors or biases in the system and to ensure that individuals have recourse if they are unfairly affected.
The potential for misuse of AI in surveillance and profiling also needs careful consideration and robust regulatory frameworks.
Best Practices for Securing User Data in a Passwordless Environment
Protecting user data in a passwordless environment requires a multi-layered approach. Here are some key best practices:
- Implement multi-factor authentication (MFA) to add an extra layer of security beyond biometrics or behavioral data.
- Employ robust encryption techniques, such as end-to-end encryption, to protect data both in transit and at rest.
- Regularly update and patch authentication systems to address security vulnerabilities.
- Conduct thorough security audits and penetration testing to identify and mitigate potential weaknesses.
- Implement strict access control measures to limit access to sensitive data to authorized personnel only.
- Adopt a principle of least privilege, granting users only the necessary access rights.
- Establish clear data retention policies and procedures for securely deleting data when it is no longer needed.
- Provide users with clear and concise information about how their data is collected, used, and protected.
User Experience and Acceptance of New Methods
The shift towards more secure authentication methods presents a significant challenge: ensuring these new systems are not only robust but also user-friendly. A complex and frustrating authentication process, no matter how secure, will inevitably lead to user resistance and ultimately, a failure to adopt the new technology. The key lies in balancing strong security with a seamless and intuitive user experience.Designing user-friendly interfaces for complex authentication systems requires careful consideration of several factors.
The cognitive load placed on the user needs to be minimized, and the process should be clear and predictable. Overly complicated workflows, confusing terminology, and lengthy procedures all contribute to user frustration and a higher likelihood of errors. Furthermore, the design should accommodate users with varying levels of technical proficiency, ensuring accessibility for all.
Intuitive and Secure User Interfaces
Several examples showcase the possibility of intuitive and secure user interfaces. Biometric authentication, such as fingerprint scanning or facial recognition, offers a relatively seamless experience, requiring minimal user interaction. However, even with these seemingly simple methods, careful design is crucial. For example, clear visual feedback during the scanning process, such as a progress bar or animation, can improve user experience.
Similarly, well-designed password managers, while using complex algorithms, can present a simple interface that allows users to securely manage and access their credentials without remembering numerous complex passwords. These password managers often employ features such as autofill and two-factor authentication, adding layers of security without sacrificing usability. Another example is the use of push notifications for two-factor authentication, which provides a simple and secure way to verify user identity without requiring the user to remember or type in a code.
Educating Users about New Authentication Approaches
Effective user education is paramount for successful adoption. Clear and concise communication, utilizing various channels such as online tutorials, FAQs, and in-app guides, is vital. The focus should be on explaining the benefits of the new system, highlighting improved security and convenience, rather than solely focusing on the technical aspects. Addressing common concerns, such as privacy implications, and providing assurances about data protection are also essential.
For example, a clear explanation of how biometric data is stored and protected, coupled with a straightforward privacy policy, can alleviate user anxieties. Gamification techniques, such as rewarding users for completing security steps, can also encourage engagement and improve user understanding.
The Importance of User Feedback
User feedback is not just beneficial; it’s essential. Collecting feedback throughout the design and implementation process allows for iterative improvements, ensuring the final product meets user needs and expectations. Methods for collecting feedback include surveys, usability testing, and user interviews. Analyzing this feedback can reveal usability issues, security concerns, and areas for improvement. For instance, user testing might reveal that a particular step in the authentication process is confusing or time-consuming, allowing developers to simplify the process.
Continuously monitoring user feedback post-launch is equally crucial, enabling ongoing refinement and adaptation to evolving user needs and emerging security threats. This iterative approach ensures that the authentication system remains both secure and user-friendly over time.
Future Trends in Identification and Authentication
The landscape of authentication is poised for a dramatic shift, driven by advancements in computing power, cryptographic techniques, and our increasing immersion in digital environments. We’re moving beyond passwords and even biometric scans towards a future where identification is seamless, secure, and deeply integrated into our daily lives. This evolution will be shaped by several key technological advancements and societal changes.
Quantum Computing’s Role in Securing Authentication
Quantum computing, while still in its nascent stages, holds the potential to revolutionize security, both by breaking existing encryption methods and by creating entirely new, quantum-resistant ones. Currently, many authentication systems rely on algorithms vulnerable to attacks from sufficiently powerful quantum computers. The future will see a transition to post-quantum cryptography (PQC), algorithms designed to withstand attacks from both classical and quantum computers.
This shift will involve updating existing infrastructure and developing new authentication protocols built on PQC principles, ensuring the long-term security of our digital identities. The NIST (National Institute of Standards and Technology) is already leading the effort in standardizing PQC algorithms, paving the way for widespread adoption.
A Hypothetical Future Authentication System
Imagine a world where your identity is verified not by a password or fingerprint, but by a unique, continuously evolving biometric signature based on your brainwave patterns. This signature, combined with advanced cryptographic techniques, would be nearly impossible to replicate or steal. Access to your accounts and devices would be granted through a secure, near-instantaneous verification process involving a wearable device that constantly monitors and transmits this biometric data, encrypted using PQC.
This system would offer a high degree of security while maintaining a seamless user experience, eliminating the need for cumbersome passwords or other traditional authentication methods. The system would also incorporate decentralized identity management, giving users greater control over their data and reducing reliance on centralized authorities.
The Metaverse’s Impact on Identity and Authentication, Authentication is outdated a new approach to identification
The metaverse presents both opportunities and challenges for identity and authentication. The immersive nature of virtual worlds necessitates robust and reliable authentication systems to ensure user security and prevent identity theft. We can expect to see the rise of decentralized identity platforms within the metaverse, allowing users to control their digital identities across various virtual environments. These platforms will likely integrate various authentication methods, including biometrics, behavioral analysis, and potentially even verifiable credentials, creating a complex but secure ecosystem for managing digital identities in this new frontier.
The challenge will be to balance the need for strong security with the desire for a seamless and user-friendly experience in these highly interactive virtual spaces.
Timeline for Authentication Method Adoption (Next Decade)
The adoption of various authentication methods will likely follow a phased approach over the next decade. While passwords will likely remain in use for simpler applications, their dominance will gradually diminish. Biometric authentication (fingerprint, facial recognition) will see widespread adoption, particularly in mobile devices and access control systems. However, concerns around privacy and security will continue to limit their use in high-security applications.
We can anticipate a significant increase in the adoption of multi-factor authentication (MFA), combining multiple authentication methods for enhanced security. Finally, advanced methods like behavioral biometrics and decentralized identity systems will see gradual but significant growth, driven by the increasing demand for stronger security and user privacy in the metaverse and other emerging digital environments. This transition will not be uniform, with different sectors and applications adopting new technologies at varying rates.
For instance, financial institutions will likely adopt advanced authentication methods sooner than smaller businesses.
Case Studies of Successful Implementations
Passwordless authentication and other advanced identification methods are no longer futuristic concepts; they’re being successfully deployed by organizations across various sectors. This section delves into specific examples showcasing the benefits and challenges of implementing these new approaches. We’ll explore how different companies have transitioned to more secure and user-friendly identification systems, highlighting the key factors that contributed to their success.
Microsoft’s Adoption of Passwordless Authentication
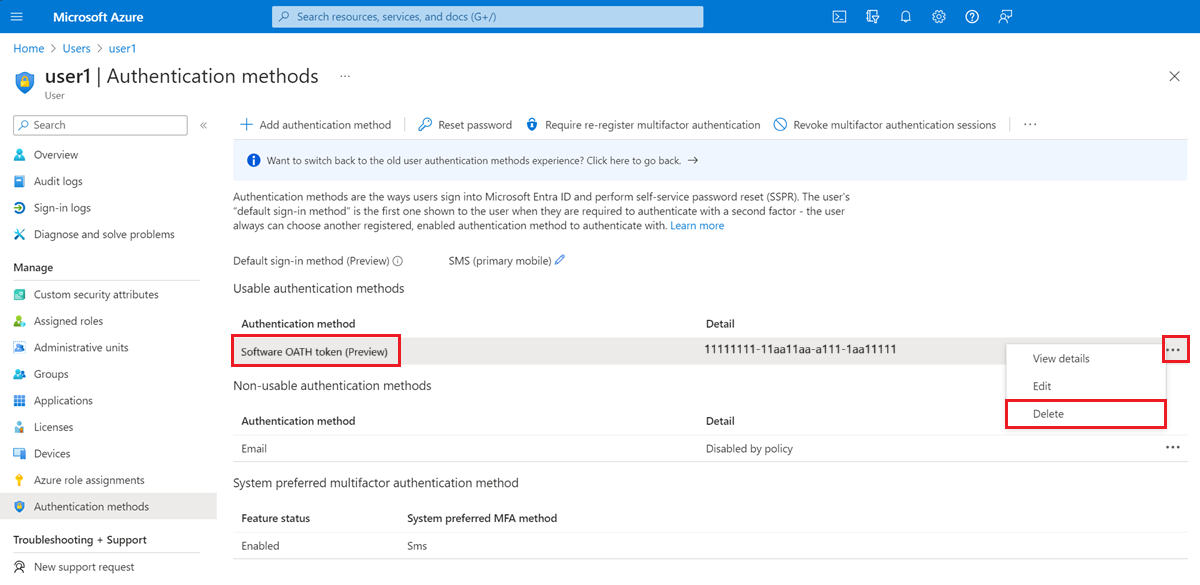
Microsoft has been a significant proponent of passwordless authentication, integrating it into its Azure Active Directory (Azure AD) platform. Their approach utilizes a multi-factor authentication (MFA) system leveraging various methods like Windows Hello (using biometric data like fingerprints or facial recognition), authenticator apps (like Microsoft Authenticator), and security keys (FIDO2 compliant). This multifaceted approach allows users to choose the authentication method best suited to their devices and security preferences.
The benefits include a significant reduction in password-related security breaches, improved user experience through streamlined login processes, and enhanced overall security posture. The implementation involved a phased rollout, allowing Microsoft to address any technical issues or user concerns before widespread adoption.
Duolingo’s Transition to a Frictionless Login Experience
Language learning platform Duolingo implemented a passwordless login system based on email verification and social logins. Their focus was on creating a frictionless user experience that minimized barriers to entry, particularly for casual users. This approach prioritized ease of use over complex security protocols. While less robust than MFA solutions employed by organizations with higher security requirements, the success lies in its ability to balance security with a user-friendly interface, which directly contributes to increased user engagement and retention.
The simplicity of the system, requiring only an email address or a social media account for login, reduced the barrier to entry significantly, resulting in higher user registration and active user base.
Key Factors Contributing to Success
Several factors contributed to the success of these implementations. Firstly, a phased rollout allowed for iterative improvements and addressed any unforeseen challenges. Secondly, user education and support were crucial in ensuring smooth transitions and user acceptance. Thirdly, selecting the appropriate authentication method based on the organization’s specific security needs and user demographics proved vital. Finally, strong leadership and commitment from the organization were essential for driving the change and overcoming any resistance.
Comparison of Security and User Experience
| Organization | Authentication Method | Security Level | User Experience |
|---|---|---|---|
| Microsoft | MFA (Biometrics, Authenticator App, Security Keys) | High | Good (Multiple options cater to different user preferences) |
| Duolingo | Email Verification/Social Login | Medium | Excellent (Extremely simple and fast) |
Final Conclusion
The shift away from traditional authentication is not just a technological upgrade; it’s a fundamental change in how we approach online security and user experience. By embracing innovative technologies like behavioral biometrics and decentralized identity systems, we can create a future where security is seamless, intuitive, and respects user privacy. While challenges remain, the potential benefits—enhanced security, improved user experience, and greater privacy—make the transition to a passwordless future a compelling and necessary evolution.
Top FAQs
What are the biggest risks associated with password-based authentication?
Password-based systems are vulnerable to phishing, brute-force attacks, and data breaches. Weak or reused passwords significantly increase these risks.
How do behavioral biometrics work?
Behavioral biometrics analyze unique user patterns like typing rhythm, mouse movements, and scrolling behavior to verify identity. It’s a passive and continuous authentication method.
What is MFA fatigue, and why is it a problem?
MFA fatigue occurs when users become frustrated with the multiple authentication steps required, leading to them bypassing security measures or using weaker methods.
What are the privacy concerns around biometric data?
Biometric data is highly sensitive and requires robust security measures to prevent unauthorized access, misuse, and potential discrimination.
