-
Online Security

Safeguarding Your Gmail Account Fraud Defense Strategies
Safeguarding your gmail account strategies to defend against fraud – Safeguarding your Gmail account: strategies to defend against fraud is…
Read More » -
Cloud Computing

Google Cloud Enhanced Security, Simplified
Google Cloud to offer enhanced security with simplicity and convergence—that’s the exciting news! Forget juggling complex security tools; Google’s latest…
Read More » -
Cybersecurity

Ine Security Alert The Steep Cost of Neglecting Cybersecurity Training
Ine security alert the steep cost of neglecting cybersecurity training – Ine Security Alert: The Steep Cost of Neglecting Cybersecurity…
Read More » -
Cybersecurity
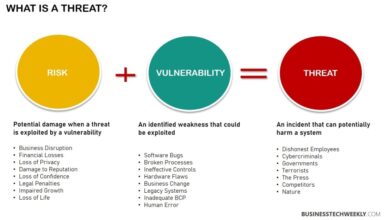
Webinar Vulnerability Risk Management The Lynchpin of Proactive Security
Webinar vulnerability risk management the lynchpin of proactive security – Webinar Vulnerability Risk Management: The Lynchpin of Proactive Security. In…
Read More » -
Cybersecurity
UK Says No to Ransom Passwords Admin 123456 & Qwerty
Uk says no to ransom passwords such as admin 123456 and qwerty – UK Says No to Ransom Passwords: Admin…
Read More » -
Cybersecurity

Why We Need to Make Passwords a Thing of the Past
Why we need to make passwords a thing of the past is a question that’s increasingly relevant in our hyper-connected…
Read More » -
Online Security

YouTube Offers AI Chatbot Help for Hacked Accounts
YouTube offers AI chatbot assistance for hacked accounts – it sounds like science fiction, right? But this innovative approach to…
Read More » -
Software Development

The Developers Guide to Secure Coding Six Steps to Secure Software
The developers guide to secure coding the six steps towards secure software development – The Developers Guide to Secure Coding:…
Read More » -
Cybersecurity

How a Data-Driven Approach Can Fix Cybersecuritys Short Blanket Problem (Picus Security)
How a data driven approach to threat exposure can fix the short blanket problem picus security – How a data-driven…
Read More » -
Cybersecurity

Navigating Digital Cyberthreats with AI-Powered Cryptography
Navigating the labyrinth of digital cyberthreats using ai powered cryptographic agility – Navigating the labyrinth of digital cyberthreats using AI-powered…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
