-
Technology

Zero Trust CIO & CTO Advantage in Corporate Environments
How zero trust helps CIOs and CTOs in corporate environments is a critical issue. Zero trust security is rapidly reshaping…
Read More » -
Cybersecurity
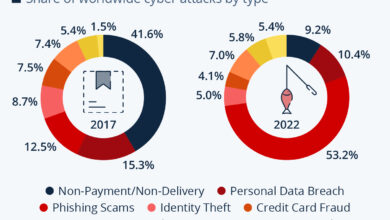
How to Make 5 Million a Day in Cybercrime A Risky Proposition
How to make 5 million a day in cybercrime? This is a tempting question, but the reality is far more…
Read More » -
Cybersecurity

How to Defend Against Zero-Click Attacks
How to defend against zero click attacks – How to defend against zero-click attacks is crucial in today’s threat landscape.…
Read More » -
Software Development

How Shifting Left Speeds Compliance Processes
How shifting left speeds compliance processes is a critical topic in modern software development. It involves integrating compliance considerations early…
Read More » -
Cybersecurity

WannaCrys Windows OS Impact A Deep Dive
How many windows oses were hit with wanna cry ransomware – How many Windows OSes were hit with WannaCry ransomware?…
Read More » -
Data Management
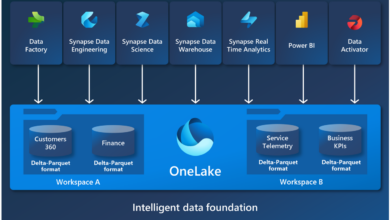
How Data Fabric Boosts Security Governance
How data fabric architecture helps enhance security governance is crucial in today’s data-driven world. Data fabric provides a flexible and…
Read More » -
Technology
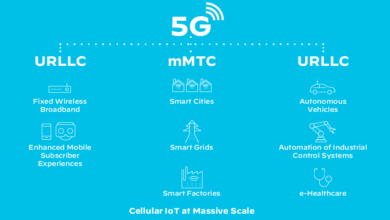
How 5G Technology Offers a Secure Network
How 5G technology offers a secure network is a critical aspect of its development. 5G’s advanced architecture introduces a new…
Read More » -
Healthcare Technology

HIMSS19 Recap A Cybersecurity Wake-Up Call
With HIMSS19 recap a cybersecurity wake up call, healthcare organizations are facing a stark reality: cybersecurity threats are more sophisticated…
Read More » -
Technology

Google Assistant Mobile Security Alert
Heres a mobile security alert for Google Assistant users, a critical piece of information for all users. This alert covers…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

