-
Cybersecurity

Apple Mac Computers Ransomware & Spyware Threat
Apple Mac computers are now being targeted with ransomware and spyware, a fact that’s shaken the long-held belief of Mac’s…
Read More » -
Android
Android 13 Promises More on Mobile Security and Privacy
Android 13 promises more on mobile security and privacy – and boy, does it deliver! This latest Android iteration isn’t…
Read More » -
Cybersecurity

Almost All Financial Apps Are Vulnerable to Cyber Attacks
Almost all financial apps are vulnerable to cyber attacks. It’s a scary thought, isn’t it? We trust these apps with…
Read More » -
Cybersecurity

Alerts, Events, Incidents Where Should Your Security Team Focus?
Alerts events incidents where should your security team focus – Alerts, events, incidents: where should your security team focus? It’s…
Read More » -
Aviation Security
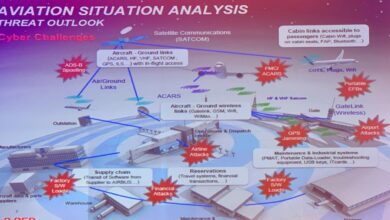
Airlines Under Constant Cyberattack Threat, Says Eurocontrol Data
Airlines under constant threat of cyber attacks says eurocontrol data – Airlines Under Constant Cyberattack Threat, Says Eurocontrol Data –…
Read More » -
Technology

AI iPhones Data Security Concerns for Users
Ai integration into iphones raises data security concerns for x – AI integration into iPhones raises data security concerns for…
Read More » -
Cybersecurity

AI-Fueled Cyber Attacks A Growing Threat
Ai fueled cyber attacks a growing threat to critical infrastructure – AI-fueled cyber attacks: a growing threat to critical infrastructure.…
Read More » -
Cybersecurity

Agenda Ransomware VMware & 17k Exchange Servers Under Attack
Agenda ransomware targeting vmware and 17k microsoft exchange servers vulnerable to cyber attacks – Agenda ransomware targeting VMware and 17,000…
Read More » -
Cloud Computing

Secure Cloud Adoption in Critical Infrastructure
Adoption of secure cloud services in critical infrastructure is no longer a futuristic concept; it’s a present-day necessity. Imagine a…
Read More » -
Mobile App Development

A Comprehensive Guide to Mobile Application Security Testing
A comprehensive guide to mobile application security testing is more than just a technical manual; it’s your survival guide in…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
