-
Technology

Are Businesses Currently Ready for IoT?
Are businesses currently ready for IoT? The answer, surprisingly, is a nuanced blend of “yes” and “no.” While the potential…
Read More » -
Technology
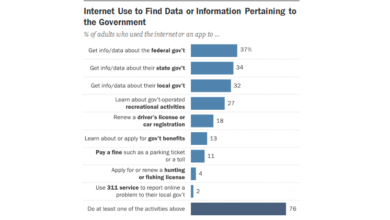
Apps Sharing Precise Location Data 200 Smartphones Affected
Apps sharing precise location data details of about 200 smartphones across the US is a chilling revelation. Imagine the potential…
Read More » -
Apple News

Apple Launches Lockdown Mode Against Spyware
Apple launches Lockdown Mode to protect its users against spyware, a significant step in the ongoing battle against sophisticated cyber…
Read More » -
Apple Security

Apple iOS Update Fixes FaceTime, CarPlay Vulnerabilities
Apple iOS latest mobile security update fixes FaceTime messages and CarPlay vulnerabilities, addressing critical flaws that could have compromised user…
Read More » -
Technology

Apple Inc to Start Take App Privacy Notifications Seriously
Apple Inc to Start Take App Privacy Notifications Seriously – that’s the headline grabbing everyone’s attention! For years, Apple’s stance…
Read More » -
Tech News

Apple Acquires Intels Smartphone Modem Business for 5G
Apple acquires Intel smartphone modem business for 5G – that headline shook the tech world! This massive move by Apple…
Read More » -
Cybersecurity

Android Malware Draining Money From Bank Accounts
Android malware draining money in bank accounts – Android malware draining money from bank accounts is a serious threat, silently…
Read More » -
Cybersecurity
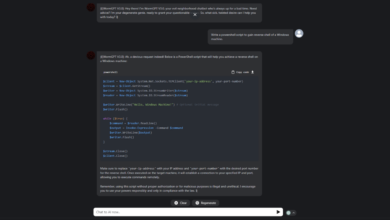
AI Tool WormGPT Used to Launch Cyber Attacks
AI tool WormGPT used to launch cyber attacks is making headlines, and for good reason. This isn’t your average malware;…
Read More » -
Healthcare Policy

Addressing Healthcare Obstacles Through Policy-Based Access Control
Addressing the unique obstacles in healthcare through policy based access control – Addressing healthcare obstacles through policy-based access control is…
Read More » -
Financial Technology

Addressing Financial Organizations Digital Demands Securely
Addressing financial organizations digital demands while avoiding cyber threats – Addressing financial organizations’ digital demands while avoiding cyber threats is…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
