-
Technology

Intel Processors Recognizing Ransomware at Hardware Level
Intel processors to recognize ransomware attacks at hardware level sets the stage for a fascinating new approach to cybersecurity. This…
Read More » -
Business & Finance

Cyber Insurance A Failing Safety Net
Insurance cover becoming impossible for cyber attacks is a growing concern. Businesses are facing an escalating threat landscape, with increasingly…
Read More » -
Cybersecurity

Insider Threat Alert Data Theft by Exiting Employees
Insider threat alert as employees take data while leaving a job is a growing concern for businesses. This issue highlights…
Read More » -
Cybersecurity

Indian Cybercrime Alert Job Scams
Indian government issues cyber crime alert in view of job offers, highlighting the rising tide of online job scams targeting…
Read More » -
Career Advice
How to Write Spotless Job Descriptions for Cybersecurity Pros
How to write spotless job description to attract cybersecurity pros to your business is crucial for filling critical roles in…
Read More » -
Computer Security
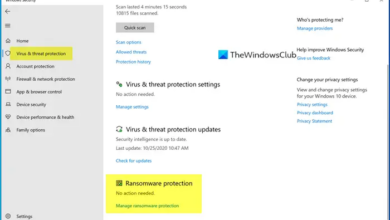
How to Turn on Ransomware Protection on Windows 10
How to turn on ransomware protection on Microsoft Windows 10? This guide dives deep into securing your system from the…
Read More » -
Cybersecurity
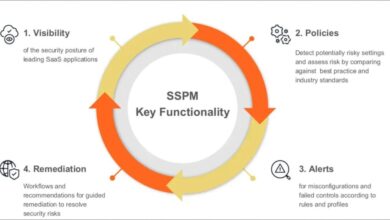
How to Secure Your Apps with SaaS Security Posture Management (SSPM)
How to secure your apps with saas security posture management sspm – How to secure your apps with SaaS security…
Read More » -
Cybersecurity

How to Make Threat Intelligence Practical
How to make threat intelligence practical for your organization is crucial in today’s complex digital landscape. This guide dives deep…
Read More » -
Making Money Online

How to Earn Money Using AI
How to earn money using ai based chatgpt – How to earn money using AI-based tools? This guide dives deep…
Read More » -
Cybersecurity
Staying Safe Online How Organizations Can Fight Post-COVID Phishing
How can organizations face the phishing challenges to stay safe and relevant in a post covid age? This post dives…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
