-
Cybersecurity

Bioterrorists Trick COVID-19 Vaccine Developers with Malware
Bioterrorists to trick covid 19 vaccine developers with malware – Bioterrorists trick COVID-19 vaccine developers with malware – a chilling…
Read More » -
AWS Security
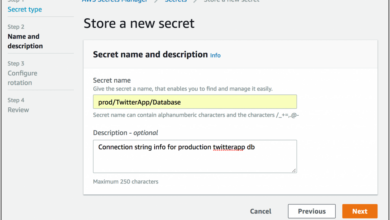
AWS Secrets Manager Boosting AWS Cloud Security
AWS Secrets Manager to boost cloud security on Amazon Web Service: Ever felt the chill of insecurely stored credentials? Managing…
Read More » -
Cybersecurity

Automation Is Key to Strengthen Cybersecurity Says IBM
Automation is key to strengthen cybersecurity says IBM, and this statement couldn’t be more relevant in today’s increasingly complex threat…
Read More » -
Cybersecurity
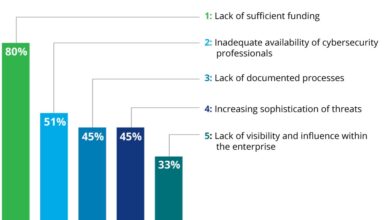
Australia Faces 10 Million Cyber Attacks Yearly, Says Deloitte
Australia faces 10 million cyber attacks a year says deloitte – Australia faces 10 million cyber attacks a year, says…
Read More » -
Ecommerce Security

5 Ways to Protect Your Ecommerce Business
5 Ways to Protect Your Ecommerce Business: Running an online store is exciting, but it also comes with serious risks.…
Read More » -
Financial Security

Are You Scam Aware Or A Sitting Duck?
Are you scam aware or a sitting duck? In today’s digital world, scams are everywhere, lurking in emails, texts, and…
Read More » -
Apple News

Apple to Launch App That Will Generate and Store Passwords
Apple to launch app that will have ability to generate and store passwords – Apple to Launch App That Will…
Read More » -
Apple iOS
Apple Makes iOS 12 Mobile Security Impeccable
Apple Makes iOS 12 Mobile Security Impeccable. Remember when iOS 12 dropped? It felt like a fortress compared to previous…
Read More » -
Tech News
Apple and Android Patch Critical Mobile Vulnerabilities
Apple and Android release slew of mobile security measures to patch vulnerabilities – that’s the headline grabbing everyone’s attention lately!…
Read More » -
Apple News

Apple Acquires Firm to Boost iPhone 8 Security
Apple acquires mobile security firm to boost its iPhone 8 build – that headline alone sparked a whirlwind of speculation!…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
