-
E-commerce Strategy

Reading Between the Lines How Informed Consumers Impact Online Retailers
Reading between the lines how the inform consumers act impacts online retailers tanium – Reading Between the Lines: How Informed…
Read More » -
Cybersecurity

Data Poisoning A Growing Threat to AI and Cybersecurity
Data poisoning a growing threat to cybersecurity and ai datasets – Data poisoning: a growing threat to cybersecurity and AI…
Read More » -
Cybersecurity News

Spain Defense Company Servers Hacked
Spain defense company servers hacked! The news broke like a thunderclap, sending shockwaves through the nation and raising serious questions…
Read More » -
Cybersecurity

Safeguarding the Fortress Googles Cyber War
Safeguarding the fortress googles battle against cyber attacks – Safeguarding the Fortress: Google’s battle against cyberattacks is a constant, high-stakes…
Read More » -
Cybersecurity

How Chaos Engineering Makes Corporate Networks Resilient to Cyber Attacks
How chaos engineering makes corporate networks resilient to cyber attacks is a question increasingly crucial in today’s digital landscape. We…
Read More » -
Cybersecurity

Can Negotiations Yield Success in Ransomware Attacks?
Can negotiations yield success in ransomware attacks? This question is increasingly critical in our hyper-connected world. Ransomware attacks are becoming…
Read More » -
Healthcare Technology

Britain NHS Software Provider Faces £6 Million Ransomware Penalty
Britain nhs software provider to face ransomware penalty of 6 million – Britain NHS software provider to face ransomware penalty…
Read More » -
Cybersecurity

Fake Antivirus Websites Now Delivering Malware
Fake antivirus websites now delivering malware are a growing threat. These cleverly disguised sites lure unsuspecting users into downloading malicious…
Read More » -
Cybersecurity

Radiant Security Gen AI SOC Copilot Your AI Security Partner
Radiant security gen ai soc co pilot – Radiant Security Gen AI SOC Copilot is revolutionizing cybersecurity. This innovative technology…
Read More » -
IT Security
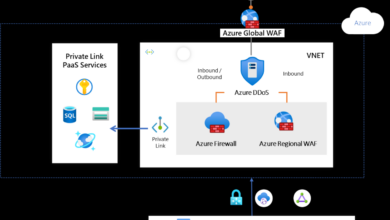
Zero Trust for Active Directory A Practical Guide
A practical guide to applying zero trust principles to active directory for microsoft on premises and hybrid environment protection –…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
