-
Technology

Ingram Micro Acquires Cloud Harmonics Cybersecurity Boost
Ingram Micro acquires cybersecurity company Cloud Harmonics, signaling a significant move in the tech industry. This acquisition promises to bolster…
Read More » -
Remote Work

How to Make Remote Work Easy A Complete Guide
How to make remote work easy? This guide dives deep into the essential elements for successful remote work, from setting…
Read More » -
Financial Services
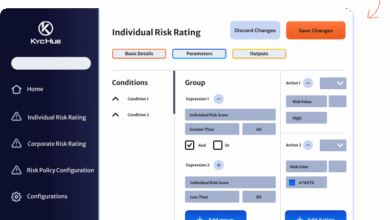
How to Make KYC Compliance Less Difficult for Banks
How to make KYC compliance less difficult for banks is a critical issue for financial institutions today. Navigating the complexities…
Read More » -
Cybersecurity

How to Become a CISO in 5 Steps
How to become a CISO in 5 steps: Ready to lead the charge in cybersecurity? This guide breaks down the…
Read More » -
Data Security
How to Achieve Maximum Security in Virtualized Data Centers
How to achieve maximum security in virtualized data centers is a critical concern for organizations today. Virtualization offers agility and…
Read More » -
Cybersecurity
How MFA Stops Healthcare Phishing
How MFA identity security can help prevent phishing scams targeting healthcare companies is crucial in today’s digital landscape. Phishing attacks…
Read More » -
Cybersecurity
Hive Ransomware A Deep Dive
Hive ransomware lets learn all about it, a critical topic in the ever-evolving cybersecurity landscape. This exploration delves into the…
Read More » -
Technology

Google to Offer Self-Destructing Email Service
Google to offer self destructing email service – Google to offer self-destructing email service, a revolutionary new feature that promises…
Read More » -
Technology
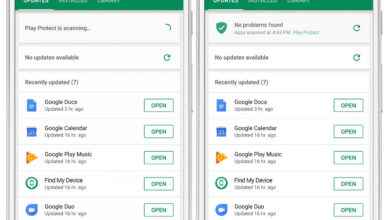
Google Play Protect Android Security Upgrade
Google perks up Android mobile security with Google Play Protect, enhancing the way we experience mobile safety. This update brings…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

