-
Cybersecurity

Cloud IT Company Evaporates Cyber Threat Warning for Windows Users
Cloud it company evaporate issues cyber threat warning for windows users – Cloud IT Company Evaporates issues cyber threat warning…
Read More » -
Cybersecurity

Clop Ransomware Gang Leaks NHS Documents Due to Ransom Rejection
Clop ransomware gang leaks NHS documents due to ransom rejection – that headline alone screams chaos, right? It’s a chilling…
Read More » -
Chinese Technology

Chinas Move Towards Automated Data Security Compliance
Chinas move towards automated data security compliance – China’s move towards automated data security compliance is reshaping the digital landscape,…
Read More » -
Strategy & Tactics
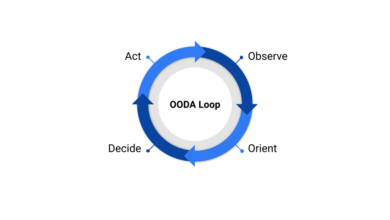
Breaking the OODA Loop Mastering Decision-Making
Breaking the OODA loop – it sounds like something from a spy thriller, doesn’t it? And in a way, it…
Read More » -
E-commerce Security

Breaking Down E-commerce Fraud The Five Pillars
Breaking down e commerce fraud the five pillars of fraud – Breaking Down E-commerce Fraud: The Five Pillars – sounds…
Read More » -
Cybersecurity
Best Practice Identifying and Mitigating Sunburst Impact
Best practice identifying and mitigating the impact of Sunburst is crucial in today’s threat landscape. This sophisticated supply-chain attack, leveraging…
Read More » -
Finance

UK Banks Forcing Customers into Online Frauds?
Banks in the uk forcing customers to online frauds – UK Banks Forcing Customers into Online Frauds? It sounds unbelievable,…
Read More » -
Cloud Security

AZSEC Software Stronger Azure Cloud Security
Azsec software to strengthen cloud security feature of microsoft azure – AZSEC software to strengthen cloud security features of Microsoft…
Read More » -
Cybersecurity

Avoid Storing This Data on Mobile to Curb Privacy and Security Concerns
Avoid storing this data on mobile to curb privacy and security concerns – it’s a mantra we should all be…
Read More » -
Cybersecurity

Automated Unified Visibility and Evaluation for Security Yes, Its Possible 2
Automated unified visibility and evaluation for security yes its possible 2 – Automated Unified Visibility and Evaluation for Security: Yes,…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
