-
Cybersecurity

BlackCat Ransomware Hits Australian Law Firm
Blackcat ransomware group breaches australia hwl ebsworth law firm servers – BlackCat ransomware group breaches Australia’s HWL Ebsworth law firm…
Read More » -
Cybersecurity
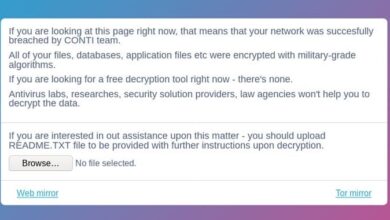
Conti Ransomware Targets Wind Turbine Giant Nordex
Conti ransomware targets wind turbine giant Nordex – a chilling headline that throws a spotlight on the increasingly vulnerable nature…
Read More » -
Cybersecurity

Cring Ransomware Spreading Fortinet Vulnerability Exploited
Cring ransomware spreading because of fortinet vulnerability – Cring ransomware spreading because of a Fortinet vulnerability is a serious threat…
Read More » -
Cybersecurity
Cyber Attack on Apex Laboratory Ransomware Suspected
Cyber attack on Apex Laboratory n ransomware suspected – the headlines screamed it, and the implications are chilling. A leading…
Read More » -
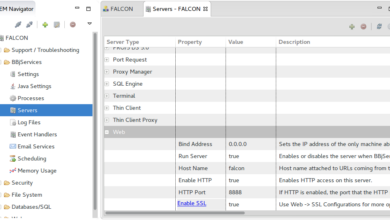
Oracle Database Administration
Simplify Oracle UCM/HCM Data Loading with Workload Automation
Simplify the data loading using oracle ucm and hcm data loader plugins with workload automation – Simplify Oracle UCM and…
Read More » -
Business Technology

Self Service Catalog On-Demand Business Flows
Self service catalog a business oriented interface to submit on demand business flows – Self service catalog: a business-oriented interface…
Read More » -
Cybersecurity

Ensuring Passwordless Job Scheduling with CyberArk Integration
Ensuring passwordless job schedulation with cyberark integration – Ensuring Passwordless Job Scheduling with CyberArk Integration: Tired of managing countless passwords…
Read More » -
SAP Administration

SAP Secure Network Connection & Workload Automation How They Work Together
Sap secure network connection and workload automation how to works together – SAP Secure Network Connection and Workload Automation: How…
Read More » -
Marketing

How to Limit Offer Fields in Interact Presentations
How to limit the offer fields in Interact offer presentations? It’s a question more marketers should be asking! Overwhelming users…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.