-
Business

How Can Businesses Lower Cyber Attack Risks?
How can businesses lower the risks of cyber attacks? This is a critical question for organizations in today’s digital landscape.…
Read More » -
IT Certifications

Top Cloud Security Certifications for IT Pros
Heres the list of the top cloud security certifications for it professionals – Here’s the list of the top cloud…
Read More » -
Healthcare

Healthcare Security Life & Death Stakes
Healthcare security security with life and death consequences is paramount. A single lapse in security can have devastating effects, jeopardizing…
Read More » -
Technology

Harnessing Defensive AI Digital Realm Safeguarding
Harnessing defensive AI safeguarding the digital realm is crucial in today’s interconnected world. This exploration delves into the core principles…
Read More » -
Cybersecurity

Global Cyber Threats Government Action Plan
Government cybersecurity is a global problem heres how agencies can address it. The digital age has brought unprecedented opportunities, but…
Read More » -
Technology

Google Spies on You Online & Real World
Google spies on you online and in the real world, collecting an astonishing amount of data about your life. From…
Read More » -
Finance

Googles $1M Crypto Mining Insurance
Google offers cryptomining protection of 1 million if it fails, a bold move that’s shaking up the industry. This insurance,…
Read More » -
Technology
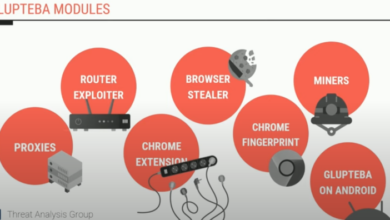
Google Lawsuit Blockchain Botnet Operators
Google files lawsuit against blockchain botnet operators, alleging a sophisticated campaign of cyberattacks targeting its services. These attacks, facilitated by…
Read More » -
Digital Marketing

Google Facebook Ads Deception and Data Theft
Google Facebook ads are deceptive and information stealing. This investigation delves into the questionable practices employed by these platforms, exploring…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

