-
Product Development

Aftermarket Shouldnt Be An Afterthought
Aftermarket shouldnt be an afterthought – Aftermarket shouldn’t be an afterthought; it’s the unsung hero of product longevity and customer…
Read More » -
Health Insurance

Volt MX Health Insurance Your Guide
Volt MX Health Insurance: Navigating the world of healthcare can be a maze, but understanding your options is key to…
Read More » -
Healthcare Technology

Modernizing Endpoint Management Platform Healthcare
Modernizing endpoint management platform healthcare is no longer a luxury, but a necessity. In today’s interconnected world, healthcare organizations face…
Read More » -
Education

Best Data Analytics Degrees Your Path to a Rewarding Career
Best data analytics degrees are more than just academic pursuits; they’re your ticket to a future brimming with exciting opportunities…
Read More » -
Economics

Why Small Business Cyberattacks Could Prompt Next Recession
Why small business cyberattacks could prompt next recession – Why small business cyberattacks could prompt the next recession? It’s a…
Read More » -
Business Management

Myths Compliance Is Too Much
Myths compliance is too much – Myths: Compliance Is Too Much – that’s the common cry from many businesses today.…
Read More » -
Cybersecurity
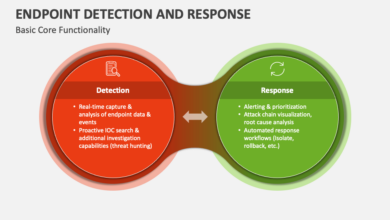
Endpoint Detection Response Guide A Practical Overview
Endpoint detection response guide – Endpoint Detection and Response (EDR) Guide: This deep dive isn’t just another tech manual; it’s…
Read More » -
Education Security

What is GESS and How Can Schools Use It?
What is the global education security standard GESS and how can schools use it? That’s the burning question we’re tackling…
Read More » -
Cybersecurity
Why Major American Companies Held a Joint Cyber Drill and You Should Too
Why major American companies held a joint cyber drill and you should too is a question worth exploring. In today’s…
Read More » -
Cybersecurity
History of Cybersecurity and Cyber Threats
History of cybersecurity and cyber threats: From the earliest forms of protecting information through physical security and rudimentary cryptography to…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
