-
Cybersecurity

AI User Data Leak A Critical Bug Vulnerability
Chatgpt users data leaked because of bug vulnerability – AI user data leaked because of a critical bug vulnerability—that’s the…
Read More » -
Cybersecurity

CDK Global Faced Second Ransomware Attack
Cdk global faced second ransomware attack – CDK Global faced a second ransomware attack, a chilling repeat performance that underscores…
Read More » -
Cybersecurity
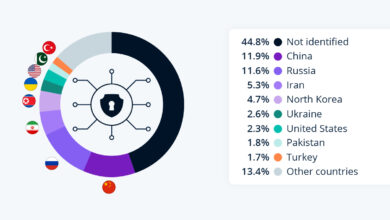
CEE Countries Are Vulnerable to Cyber Attacks
CEE Countries Are Vulnerable to Cyber Attacks: It’s a chilling reality. These nations, often facing complex geopolitical landscapes and undergoing…
Read More » -
Cybersecurity

Can Ransomware Gangs Be Neutralized? Exploring Cyber Extortion Strategies
Can ransomware gangs be neutralized exploring strategies to combat cyber extortion – Can ransomware gangs be neutralized? Exploring strategies to…
Read More » -
Cybersecurity

Can Biometric Monitoring Improve Data Center Cybersecurity?
Can biometric monitoring improve the cybersecurity posture of data centers? Absolutely! In today’s world of increasingly sophisticated cyber threats, traditional…
Read More » -
Software Development

Build Smarter, More Secure Applications with PulseVADC Community Edition
Build smarter more secure applications with pulse vadc community edition – Build smarter, more secure applications with PulseVADC Community Edition!…
Read More » -
Health & Technology

British Pregnant Women Unwittingly Share Genetic Data with China
British pregnant women are unwittingly handing over their gentic data to china – British pregnant women are unwittingly handing over…
Read More » -
Cybersecurity

Britain Starts Issuing Early Warnings to Ransomware Victims
Britain starts issuing early warning to ransomware victims – a significant move in the ongoing battle against cybercrime. This proactive…
Read More » -
International Relations

Britain and US Jointly Vow to Fight Russian Cyberattacks
Britain and US jointly vow to fight back Russian cyber attacks – a headline that screams urgency and collaboration in…
Read More » -
WordPress Security
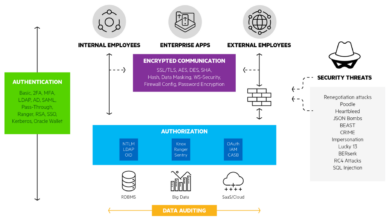
Bringing Authentication Security Out of the Dark Ages Enzoic
Bringing authentication security out of the dark ages enzoic – Bringing authentication security out of the dark ages with Enzoic…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
