-
Cloud Security

Best Practices to Safeguard Data Across Hybrid Cloud Environments
Best practices to safeguard data across hybrid cloud environments are more crucial than ever. The hybrid cloud, with its blend…
Read More » -
Cybersecurity

Bots Compromise Jersey Computers for Cyberattacks
Bots compromise jersey computers to use them for cyber attacks – Bots compromise Jersey computers to use them for cyberattacks…
Read More » -
Technology

Google AI Aggression Downgrades Alphabet
Google ai aggression makes bernstein research downgrade alphabet – Google AI Aggression Downgrades Alphabet: Whoa, that’s a headline that grabbed…
Read More » -
Cybersecurity

Venn Redefines Remote Work Security with BYOPC
Venn redefines remote work security with innovative byo pc solution – Venn redefines remote work security with its innovative BYOPC…
Read More » -
Cybersecurity

Repeat Ransomware Attacks on 78 Victims Who Paid
Repeat ransomware attacks on 78 of victims who pay – it sounds unbelievable, right? But it’s a chilling reality highlighting…
Read More » -
Cybersecurity

Beware of this Russia Oxford Vaccine Email Cyber Scam
Beware of this Russia Oxford Vaccine Email Cyber Scam! Remember those frantic days of the pandemic? The desperate hunt for…
Read More » -
Data Analytics & Business Intelligence
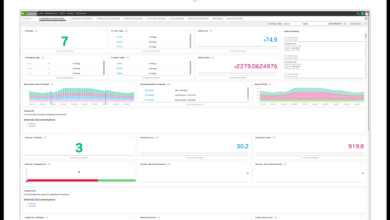
HWA Observability Splunk, Metrics, & Inventory Planning
Hwa observability over splunk generating business metrics inventory planning – HWA observability over Splunk generating business metrics for inventory planning…
Read More » -
IT Security
Connect to Axway Secure Transport with Workload Automation
Connect to Axway Secure Transport with Workload Automation – sounds complex, right? But it’s actually a game-changer for secure data…
Read More » -
Data Analytics

Configuring ELK Components in Unica Discover 12.1.2
Configuring elk components in unica discover 12 1 2 – Configuring ELK components in Unica Discover 12.1.2 might sound intimidating,…
Read More »
Privacy Overview
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookies
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.