AWS Secrets Manager Boosting AWS Cloud Security
AWS Secrets Manager to boost cloud security on Amazon Web Service: Ever felt the chill of insecurely stored credentials? Managing API keys, database passwords, and other sensitive information can feel like walking a tightrope. But what if I told you there’s a secure, centralized solution that simplifies this process and dramatically improves your cloud security posture? That’s where AWS Secrets Manager comes in – a powerful tool that helps you protect your most valuable assets.
This post dives into how it works, its benefits, and how to integrate it into your workflows for a more secure cloud environment.
We’ll explore the core functionality of AWS Secrets Manager, highlighting its robust encryption, granular access controls, and automated rotation features. We’ll compare it to other secret storage methods, showcasing why it’s a superior choice for many organizations. We’ll also delve into practical examples, showing how to integrate Secrets Manager with services like EC2 and Lambda, and address common troubleshooting issues.
Get ready to level up your cloud security game!
Introduction to AWS Secrets Manager
AWS Secrets Manager is a fully managed service that helps you protect sensitive data, such as API keys, database credentials, and passwords. It simplifies the process of securely storing, accessing, and rotating these secrets, significantly improving your overall cloud security posture. Instead of embedding sensitive information directly into your applications or configuration files, you centralize it in Secrets Manager, reducing the risk of exposure and simplifying management.Secrets Manager provides a secure and centralized repository for your most sensitive data, offering a robust solution that addresses many of the challenges associated with traditional secret management practices.
By leveraging its features, you can streamline your operational workflows while bolstering your security defenses against data breaches.
Core Functionality of AWS Secrets Manager
AWS Secrets Manager’s core functionality revolves around the secure storage and retrieval of sensitive data. It offers features like encryption at rest and in transit, rotation schedules for secrets that need regular updates, and fine-grained access control using IAM policies. This ensures only authorized users and services can access specific secrets. The service integrates seamlessly with other AWS services, simplifying integration into existing workflows.
It also provides auditing capabilities, allowing you to track access and changes to your secrets, providing valuable insights into security and operational activities.
Benefits of Using Secrets Manager for Sensitive Data
Using AWS Secrets Manager offers several key advantages. It eliminates the risk of hardcoding secrets directly into applications, a common vulnerability. Centralized management simplifies the process of rotating secrets, reducing the window of vulnerability associated with compromised credentials. Access control features ensure only authorized entities can access sensitive information. Furthermore, Secrets Manager’s auditing capabilities provide a complete audit trail of all access and modifications, crucial for compliance and security investigations.
Finally, its integration with other AWS services streamlines the overall management of your cloud infrastructure.
Examples of Sensitive Data Suitable for Storage in Secrets Manager
Many types of sensitive data are ideal candidates for storage in AWS Secrets Manager. This includes:
- Database credentials: Usernames and passwords for accessing databases.
- API keys: Authentication keys for accessing third-party APIs and services.
- OAuth tokens: Tokens used for authorization in OAuth-based authentication flows.
- Certificates: SSL/TLS certificates and private keys for securing communication.
- SSH keys: Private keys for secure shell access to servers.
- License keys: Keys for accessing licensed software.
- Passwords for applications and services: Credentials for accessing various internal and external systems.
Storing this data in Secrets Manager helps protect it from unauthorized access and simplifies its management, contributing to a more secure and efficient operational environment.
Enhanced Security with AWS Secrets Manager: Aws Secrets Manager To Boost Cloud Security On Amazon Web Service
AWS Secrets Manager significantly bolsters your cloud security posture by providing a centralized, secure repository for sensitive data like database credentials, API keys, and certificates. This eliminates the risks associated with hardcoding secrets directly into your applications or storing them in insecure locations like configuration files. By centralizing secret management, you gain better control and visibility, making it easier to manage, rotate, and audit access to your most valuable assets.Secrets Manager offers substantial improvements over traditional methods of secret storage.
Previously, developers often resorted to embedding secrets directly within application code, storing them in plain text files, or using less secure cloud storage solutions. These approaches expose secrets to unauthorized access, potentially leading to data breaches and significant security vulnerabilities. Secrets Manager mitigates these risks through robust encryption, granular access control, and automated secret rotation.
Secret Storage Alternatives and Their Limitations, Aws secrets manager to boost cloud security on amazon web service
Storing secrets in plain text files or directly within application code presents obvious security risks. Unauthorized access, accidental exposure through version control systems (like Git), and difficulty in managing access control are major drawbacks. Even seemingly secure cloud storage options without dedicated secret management features often lack the granular control and audit capabilities of Secrets Manager. For instance, storing secrets in an S3 bucket, even with encryption enabled, might still be vulnerable if proper access controls aren’t implemented meticulously.
This often results in a higher risk of human error and potential breaches. Secrets Manager addresses these shortcomings by providing a purpose-built solution designed specifically for managing sensitive information.
Encryption and Access Control in AWS Secrets Manager
Secrets Manager employs robust encryption at rest and in transit to protect your secrets. Secrets are encrypted using AWS KMS (Key Management Service), a highly secure and auditable key management system. This ensures that even if an attacker gains access to the underlying storage, they cannot decrypt the secrets without the correct KMS keys. Furthermore, access to secrets is strictly controlled using IAM (Identity and Access Management) policies.
You can define fine-grained permissions, allowing only authorized users, roles, or services to access specific secrets. This granular control enables the principle of least privilege, minimizing the potential impact of a security breach. For example, a database administrator might only have access to database credentials, while a developer might only access API keys necessary for their specific application.
This precise access control dramatically reduces the attack surface.
Automated Secret Rotation
The automated secret rotation feature is a key differentiator for Secrets Manager. Regularly rotating secrets (e.g., database passwords) is a crucial security best practice, minimizing the impact of compromised credentials. Secrets Manager simplifies this process by allowing you to schedule automatic rotation for various secret types, ensuring your secrets are updated regularly without manual intervention. This automated approach significantly reduces the risk of outdated or compromised credentials remaining in use, providing a continuous security improvement.
For instance, rotating database passwords every 90 days mitigates the risk of a prolonged breach if a password is compromised. This minimizes the window of opportunity for malicious actors.
Integration with Other AWS Services
Secrets Manager isn’t a standalone solution; its true power lies in its seamless integration with other AWS services. By securely managing your secrets within Secrets Manager, you can significantly improve the security posture of your entire AWS infrastructure. This integration simplifies the process of accessing sensitive data, reducing the risk of hardcoding credentials and improving overall operational efficiency.The ability to integrate Secrets Manager with various AWS services is a key advantage.
This allows developers to easily retrieve secrets needed by their applications without compromising security. Let’s explore how this works in practice with some common services.
Secrets Manager Integration with Amazon EC2
Integrating Secrets Manager with Amazon EC2 involves configuring your EC2 instances to retrieve secrets at runtime. This eliminates the need to store credentials directly within the instance’s configuration files or scripts. Instead, your application can use the AWS SDKs to retrieve secrets from Secrets Manager securely. This approach significantly reduces the attack surface, as secrets are not persistently stored on the EC2 instance’s disk.
For example, you might store database credentials in Secrets Manager and have your EC2-based application retrieve them during startup. The application would then use these credentials to connect to the database. This ensures that even if an attacker compromises the EC2 instance, they won’t have direct access to the sensitive database credentials.
Secrets Manager Integration with AWS Lambda
AWS Lambda functions are inherently stateless, making Secrets Manager an ideal solution for managing secrets accessed by these functions. Lambda functions can be configured to retrieve secrets directly from Secrets Manager using environment variables or the AWS SDK. This allows you to avoid hardcoding sensitive information into your Lambda function code. For instance, an API Gateway-triggered Lambda function processing sensitive data might retrieve API keys from Secrets Manager.
This ensures that the API keys aren’t exposed in the Lambda function’s codebase, enhancing the overall security. Using the AWS SDK is recommended for more robust error handling and management of secrets.
Step-by-Step Guide: Integrating Secrets Manager into a New Application
Let’s walk through integrating Secrets Manager into a new Node.js application deployed on EC2. This guide highlights best practices and common pitfalls.
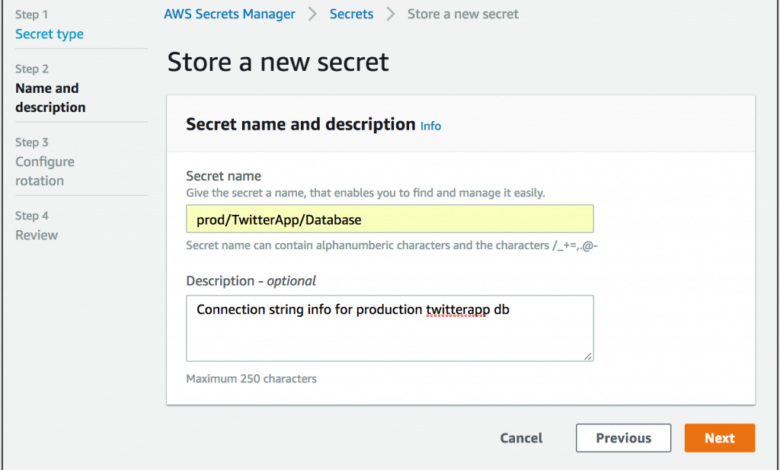
- Create a Secret in Secrets Manager: Navigate to the Secrets Manager console and create a new secret. Provide a descriptive name (e.g., “database-credentials”) and enter your sensitive data in the appropriate fields. Remember to rotate your secrets regularly.
- Configure IAM Roles: Create an IAM role with permissions to access the specific secret you created. This role will be assigned to your EC2 instance. Ensure the principle of least privilege is followed; only grant the necessary permissions.
- Install the AWS SDK: In your Node.js application, install the AWS SDK for JavaScript:
npm install aws-sdk - Retrieve the Secret: Use the AWS SDK to retrieve the secret from Secrets Manager within your application code. This involves configuring the SDK with your AWS credentials (typically through the IAM role assigned to your EC2 instance) and making a call to the Secrets Manager API. Handle potential errors gracefully.
- Deploy to EC2: Deploy your application to your EC2 instance, ensuring the instance profile is correctly configured with the IAM role granting access to Secrets Manager.
Remember to always follow the principle of least privilege when configuring IAM roles. Grant only the necessary permissions to access specific secrets, minimizing the potential impact of a security breach. Regularly rotate your secrets to further enhance security.
Implementing Rotation and Access Control
Secrets Manager’s strength lies not just in storing secrets securely, but also in managing their lifecycle effectively. This involves implementing robust rotation strategies and carefully controlling access using IAM. Failing to do so leaves your application vulnerable, even with secrets safely stored. Let’s dive into the practical aspects of securing your secrets through rotation and access control.
A well-defined secret rotation strategy is crucial for minimizing the risk of compromised credentials. Regularly rotating secrets reduces the window of vulnerability, ensuring that even if a secret is leaked, its lifespan is limited. This approach complements other security measures and strengthens your overall security posture. This is particularly important for secrets used in sensitive operations such as database connections or API keys.
Secret Rotation Strategies
Designing a robust secret rotation strategy requires considering several factors, including the sensitivity of the secret, the application’s requirements, and the frequency of access. There’s no one-size-fits-all solution, but a well-structured approach involves defining a rotation schedule, automating the process, and carefully monitoring any errors or anomalies.
For example, a database password might require rotation every 90 days, while an API key used less frequently could be rotated every 180 days. Secrets Manager provides the tools to automate this process, including Lambda functions triggered on a schedule or in response to specific events. You should always test your rotation process thoroughly in a non-production environment before deploying it to production.
IAM Roles and Policies for Secure Access
IAM (Identity and Access Management) is the cornerstone of AWS security. By leveraging IAM roles and policies, you can granularly control which users, services, and applications have access to your secrets. This principle of least privilege is vital – grant only the necessary permissions to each entity. Avoid using root accounts or overly permissive policies whenever possible.
Securing your AWS environment is crucial, and AWS Secrets Manager is a fantastic tool for managing sensitive data like API keys and database passwords. But strong security practices extend beyond just infrastructure; consider how your application development impacts security. Learning about modern development approaches like those described in this article on domino app dev the low code and pro code future can help you build more secure applications from the ground up.
Ultimately, robust security needs a holistic approach, integrating secure coding practices with tools like AWS Secrets Manager for a truly fortified cloud presence.
Instead of granting direct access to secrets using user credentials, it’s best practice to leverage IAM roles. These roles are temporary credentials associated with specific AWS services or applications. This way, even if a service account is compromised, the access is limited by the role’s permissions. You can then use IAM policies to define precisely which actions (like `GetSecretValue`) a role is allowed to perform on specific secrets.
Example policy snippet (allowing only `GetSecretValue` for a specific secret):
“Version”: “2012-10-17”,
“Statement”: [“Effect”: “Allow”,
“Action”: [
“secretsmanager:GetSecretValue”
],
“Resource”: “arn:aws:secretsmanager:REGION:ACCOUNT-ID:secret:MY-SECRET-NAME-abcdefg”]
Potential Vulnerabilities and Mitigation Strategies
Despite implementing robust rotation and access control, certain vulnerabilities can still exist. Understanding these vulnerabilities and implementing proactive mitigation strategies is essential for maintaining a strong security posture.
- Insufficient Logging and Monitoring: Without proper logging and monitoring, detecting unauthorized access or failed rotation attempts can be challenging. Implement CloudTrail to track all API calls made to Secrets Manager and set up appropriate alerts to notify you of suspicious activity.
- Hardcoded Secrets: Storing secrets directly within application code is a significant vulnerability. Always retrieve secrets from Secrets Manager at runtime. This ensures that secrets are not exposed in version control systems or other repositories.
- Overly Permissive IAM Policies: Granting excessive permissions to IAM roles or users increases the attack surface. Regularly review and audit IAM policies to ensure they follow the principle of least privilege.
- Lack of Rotation: Failing to rotate secrets regularly increases the risk of compromise. Establish a clear rotation schedule and automate the process using Secrets Manager’s capabilities.
Practical Examples and Use Cases
AWS Secrets Manager offers a robust and secure solution for managing sensitive data, significantly improving the overall security posture of your AWS deployments. Its ease of use and integration with other AWS services make it a valuable asset for various applications, regardless of scale or complexity. Let’s explore some practical examples to illustrate its benefits.
Database Credential Management
Secrets Manager simplifies the management of database credentials by providing a centralized, secure repository. Instead of hardcoding credentials directly into your application code, you store them as secrets within Secrets Manager. Your application then retrieves these credentials securely at runtime. This approach eliminates the risk of exposing sensitive information in version control systems or configuration files. For instance, a web application connecting to a MySQL database can leverage Secrets Manager to securely store and retrieve the database username, password, and connection string.
This eliminates the need to manage these credentials manually, reducing the risk of human error and accidental exposure. Each application instance can fetch credentials independently, ensuring that even if one instance is compromised, the entire system’s security isn’t jeopardized.
API Keys and Tokens
Many applications rely on third-party APIs, often requiring API keys and access tokens. These credentials, if exposed, can grant unauthorized access to sensitive data or functionality. Secrets Manager provides a safe and controlled environment for storing and managing these credentials. Consider a scenario where an e-commerce platform integrates with a payment gateway. The API keys and tokens needed for this integration can be securely stored in Secrets Manager, retrieved by the application only when needed, and rotated regularly to minimize the impact of potential breaches.
The platform can automatically rotate these secrets, further enhancing security.
SSH Keys
Securing access to your servers is paramount. Traditionally, SSH keys are often stored insecurely, posing a significant risk. Secrets Manager allows you to securely store and manage SSH keys, enabling secure access to your EC2 instances or other server environments. This eliminates the risk of accidental exposure or unauthorized access through compromised files. Imagine a DevOps team managing multiple servers.
Using Secrets Manager to store and manage SSH keys ensures that only authorized personnel can access the servers, reducing the attack surface and strengthening overall security. This process can be integrated with automated deployment pipelines, providing seamless and secure access to server environments.
Cost and Security Comparison: Secrets Manager vs. Alternatives
Choosing the right solution for secret management is crucial. Below is a comparison of AWS Secrets Manager against some common alternatives, highlighting cost and security implications. Note that costs can vary depending on usage and specific configurations.
| Feature | AWS Secrets Manager | Hardcoded Credentials | Configuration Files | Third-Party Solutions |
|---|---|---|---|---|
| Security | High: Encryption at rest and in transit, access control, audit trails, rotation | Low: Credentials exposed in code, easily compromised | Medium: Depends on file permissions and access controls; still vulnerable to breaches | Variable: Depends on the specific solution and its security features. |
| Cost | Variable: Based on API calls and storage usage, generally cost-effective for larger deployments | Low initial cost, but high potential for remediation costs from breaches | Low initial cost, but high potential for remediation costs from breaches | Variable: Can range from low to high depending on the chosen solution and features. |
| Management | Easy: Centralized management, automation capabilities, versioning | Difficult: Manual management, prone to errors | Difficult: Manual management, prone to errors, version control challenges | Variable: Depends on the solution’s interface and features. |
| Scalability | High: Easily scales to accommodate growing needs | Low: Difficult to manage at scale | Low: Difficult to manage at scale | Variable: Depends on the solution’s architecture. |
Monitoring and Auditing Secrets Manager
Effective monitoring and auditing are crucial for maintaining the security and compliance of your AWS Secrets Manager. By regularly reviewing access logs and implementing alerts, you can proactively identify and respond to potential threats, ensuring your sensitive data remains protected. This involves understanding how to leverage the built-in features of Secrets Manager to track activity and establish a robust audit trail.
AWS Secrets Manager provides comprehensive logging capabilities, allowing you to track all access attempts to your secrets. These logs contain detailed information such as the timestamp of the access, the user or service that accessed the secret, the IP address, and the outcome of the request (successful or unsuccessful). This granular level of detail is essential for identifying unauthorized access, analyzing usage patterns, and complying with various security and regulatory standards.
Secret Access Logs
AWS CloudTrail logs all API calls made to Secrets Manager. This includes actions like creating, retrieving, updating, and deleting secrets. You can access these logs through the CloudTrail console, and they provide a complete audit trail of all activities performed within Secrets Manager. Analyzing these logs helps to identify any anomalies or unauthorized access attempts. For example, a sudden surge in access attempts from an unusual IP address could indicate a potential security breach.
You can filter and search these logs based on various parameters such as user, time, and action to easily pinpoint specific events. Furthermore, CloudTrail integrates with other AWS services, allowing you to integrate these logs into your existing security information and event management (SIEM) systems for centralized monitoring and analysis.
Auditing Secret Access for Compliance
Regular auditing of secret access is essential for maintaining compliance with various security and regulatory standards such as HIPAA, PCI DSS, and SOC 2. By reviewing the CloudTrail logs, you can verify that access to your secrets is controlled and adheres to your organization’s security policies. This process involves analyzing the logs for any unauthorized access, unusual activity patterns, or violations of your access control policies.
You should establish a regular auditing schedule, for instance, a monthly review of access logs, and document the findings. This documentation is critical for demonstrating compliance during audits and investigations. A well-defined auditing process ensures that any security incidents are detected and addressed promptly.
Setting Up Alerts for Suspicious Activities
Proactive monitoring is key to mitigating security risks. AWS CloudWatch can be configured to generate alerts based on specific events within Secrets Manager logs. You can create custom metrics and dashboards to monitor key performance indicators (KPIs) such as the number of secret access attempts, the number of failed access attempts, and the frequency of secret rotations. For example, you could set an alert to trigger if the number of failed login attempts exceeds a predefined threshold, indicating a potential brute-force attack.
Similarly, you can set alerts for unusual access patterns, such as access from unexpected geographical locations or during unusual hours. These alerts provide timely notifications of potential security breaches, allowing for prompt investigation and remediation. The ability to customize alerts based on your organization’s specific security needs is a crucial feature for proactive threat detection.
Best Practices for Secure Secret Management
AWS Secrets Manager is a powerful tool, but its effectiveness hinges on proper configuration and usage. Implementing robust security practices ensures your sensitive data remains protected from unauthorized access and breaches. This section Artikels crucial best practices to maximize the security of your secrets.
Effective secret management isn’t a one-time task; it’s an ongoing process requiring vigilance and proactive measures. Failing to prioritize security can lead to significant financial and reputational damage, exposing your organization to substantial risk. Let’s delve into the key aspects of securing your secrets within AWS Secrets Manager.
Least Privilege Access Control
Implementing the principle of least privilege is paramount. This means granting users and services only the necessary permissions to access specific secrets. Overly permissive access policies significantly increase the attack surface. By meticulously defining access policies based on the “need-to-know” principle, you minimize the potential impact of compromised credentials. For instance, a database service should only have access to the database credentials stored in Secrets Manager, not to other secrets like API keys or SSH keys.
This granular control ensures that even if one secret is compromised, the damage is contained.
Regular Rotation of Secrets
Secrets, especially those with high privileges, should be rotated regularly. This minimizes the window of vulnerability if a secret is somehow compromised. Secrets Manager facilitates automated rotation for several services, reducing manual intervention and human error. Establishing a robust rotation schedule – perhaps every 90 days or even more frequently for highly sensitive secrets – is crucial for maintaining a strong security posture.
Failing to rotate secrets regularly increases the risk of prolonged exploitation if a breach occurs.
Regular Security Assessments and Penetration Testing
Regular security assessments and penetration testing are not optional; they are essential. These assessments should evaluate the configuration of Secrets Manager, its integration with other services, and the overall security posture of your systems that utilize secrets managed by Secrets Manager. Penetration testing simulates real-world attacks to identify vulnerabilities before malicious actors exploit them. These assessments should include both automated scans and manual reviews to identify weaknesses and misconfigurations that could compromise your secrets.
The frequency of these assessments should be determined by your risk tolerance and the sensitivity of the data stored. For organizations handling highly sensitive information, more frequent assessments might be necessary.
Impact of Neglecting Security Best Practices
Neglecting security best practices can have devastating consequences. A data breach resulting from insecure secret management can lead to significant financial losses due to fines, legal fees, and remediation costs. Reputational damage can be equally detrimental, impacting customer trust and business relationships. Furthermore, compromised secrets can lead to unauthorized access to sensitive data, potentially resulting in identity theft, intellectual property theft, and other serious security incidents.
For example, a compromised AWS access key stored insecurely could grant attackers complete control over your AWS environment, leading to a catastrophic breach. The cost of remediation after such an incident often far outweighs the investment in proactive security measures.
Cost Optimization with AWS Secrets Manager
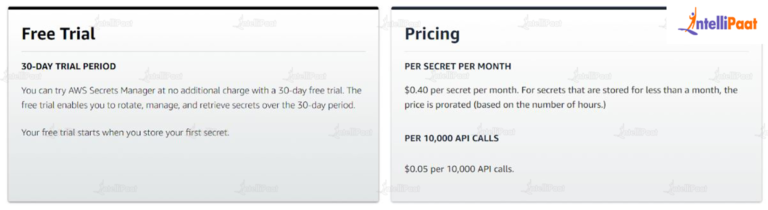
Managing secrets securely is paramount, but it shouldn’t break the bank. AWS Secrets Manager offers robust security, but understanding its pricing model and employing smart strategies is key to keeping costs under control. This section explores practical ways to optimize your spending while maintaining a high level of security for your sensitive data.AWS Secrets Manager’s pricing is based on the number of secrets stored and the number of API calls made.
Understanding this fundamental pricing structure allows you to proactively manage expenses. High usage of API calls, for example, due to frequent rotation or access, will directly impact your bill. Therefore, efficient management practices can significantly reduce costs.
Pricing Model Breakdown
AWS Secrets Manager charges based on two primary factors: storage and API requests. The storage cost is dependent on the amount of data stored in Secrets Manager, while API requests cover actions such as retrieving, creating, updating, and deleting secrets. These costs are calculated per region, and understanding regional pricing differences can be beneficial for cost optimization. For example, a company with a global presence might find that strategically placing secrets in less expensive regions for less frequently accessed data can significantly lower their overall cost.
This strategy requires careful planning to ensure security and compliance are not compromised.
Strategies for Reducing Costs
Minimizing unnecessary API calls is a crucial aspect of cost optimization. This can be achieved through careful planning of secret access patterns and implementing efficient rotation schedules. For instance, instead of frequently rotating secrets unnecessarily, a more deliberate schedule aligned with security best practices and application needs will reduce API calls and associated costs. Furthermore, leveraging IAM policies and least privilege access control can reduce the number of API calls made by limiting who can access and interact with the secrets.
By granting only necessary permissions, you prevent unnecessary requests and reduce your overall bill.
Efficient Secret Rotation
Secret rotation is a critical security practice, but overly frequent rotation can inflate costs. Finding the optimal balance between security and cost is crucial. A well-defined rotation schedule based on risk assessment and regulatory requirements, rather than arbitrary intervals, will help minimize unnecessary costs. For example, a company handling highly sensitive payment information might require more frequent rotation than one managing less critical configuration data.
A risk-based approach will ensure security without incurring unnecessary expenses.
Leveraging IAM Policies for Access Control
Implementing strict IAM policies is not just a security best practice; it’s also a cost-saving measure. By granting only the necessary permissions to access secrets, you significantly reduce the potential for accidental or unauthorized access, thereby minimizing the need for remediation and reducing API calls. Using granular permissions prevents unnecessary API calls and contributes to overall cost reduction.
A well-structured IAM policy minimizes the surface area for potential breaches and reduces the risk of incurring costs associated with security incidents.
Monitoring and Alerting
Regularly monitoring your Secrets Manager usage and setting up cost alerts helps proactively manage expenses. AWS provides tools to track your spending and identify areas for potential savings. Setting up alerts for unexpected spikes in usage allows for timely intervention and prevents unforeseen cost overruns. This proactive approach is essential for maintaining budget control. For example, an alert triggered by a sudden increase in API calls might indicate a security breach or a misconfigured application, allowing for immediate investigation and resolution.
Troubleshooting Common Issues
AWS Secrets Manager, while incredibly robust, can occasionally present challenges. Understanding common problems and their solutions is crucial for maintaining a secure and efficient environment. This section provides a practical guide to resolving some of the most frequently encountered issues. We’ll cover troubleshooting steps for access permission problems and secret rotation difficulties.
Access Permission Issues
Incorrectly configured IAM permissions are a leading cause of Secrets Manager problems. Users might be unable to retrieve secrets due to insufficient privileges, leading to application failures or operational delays. This often manifests as error messages indicating an access denied. Resolving these issues requires careful review and adjustment of IAM policies.
- Verify IAM User/Role Permissions: Check the IAM policy attached to the user or role attempting to access the secret. Ensure the policy explicitly grants the necessary permissions, such as `secretsmanager:GetSecretValue` for retrieving secrets. A common mistake is using overly restrictive policies.
- Check Secret Policy: Examine the secret’s resource-based policy. This policy controls access to the secret itself, independent of IAM user/role permissions. Ensure that the appropriate AWS accounts or IAM principals are granted access with the correct actions.
- Use AWS CLI to Debug: The AWS Command Line Interface (CLI) can be invaluable for troubleshooting. Use the `aws secretsmanager get-secret-value` command with appropriate parameters. Error messages returned by the CLI often pinpoint the specific problem.
- IAM Role Delegation: If an application is running on an EC2 instance, ensure the instance role has the correct permissions to access the secret. Review the instance profile associated with the EC2 instance.
- Least Privilege Principle: Always adhere to the principle of least privilege. Grant only the minimum necessary permissions to users and roles to access secrets. Overly permissive policies increase the risk of security breaches.
Secret Rotation Issues
Automated secret rotation is a key security feature of Secrets Manager, but issues can arise. Failures to rotate secrets can expose your applications to vulnerabilities. Troubleshooting these issues requires understanding the rotation process and its configuration.
- Rotation Lambda Function Errors: Secret rotation relies on a Lambda function. Check CloudWatch logs for errors within this function. Common causes include insufficient permissions for the Lambda function to access the secret or the target service (e.g., RDS).
- Rotation Schedule Verification: Confirm that the rotation schedule is correctly configured. Check the rotation lambda function’s configuration and ensure it’s set to rotate the secret at the desired frequency.
- Target Service Configuration: Verify the configuration of the target service (e.g., database credentials). Ensure the target service is correctly configured to accept updated credentials from the rotation process. For example, an RDS instance needs to be configured to accept a new password.
- Secret Version History: Examine the secret’s version history to verify successful rotations. A lack of new versions may indicate a problem with the rotation process.
- Rotation Lambda Function Permissions: The Lambda function needs appropriate permissions to update the secret. Verify that it has the `secretsmanager:PutSecretValue` permission.
Final Review
Securing your secrets is paramount in today’s cloud-centric world. AWS Secrets Manager offers a comprehensive solution to manage and protect sensitive data, significantly enhancing your overall security posture. By implementing robust rotation strategies, leveraging IAM roles, and adhering to best practices, you can mitigate risks and build a more resilient infrastructure. Don’t leave your secrets vulnerable – embrace the power of AWS Secrets Manager and sleep soundly knowing your data is safe.
FAQ Compilation
What happens if I forget my Secrets Manager master key?
AWS doesn’t store your master key; it’s managed by the KMS service. If you lose access to your KMS key, you’ll need to follow AWS’s key recovery procedures, which might involve contacting support.
Can I use Secrets Manager with non-AWS services?
While primarily designed for AWS, you can indirectly use Secrets Manager with external services. You’d typically retrieve secrets from Secrets Manager using an AWS Lambda function or EC2 instance, then relay that information to your external service.
How does Secrets Manager handle compliance requirements?
Secrets Manager helps with compliance by providing detailed audit logs, enabling you to track all access and changes. This facilitates compliance with regulations like SOC 2, PCI DSS, and HIPAA, but you’ll still need to configure and manage your environment appropriately.
Is Secrets Manager free?
No, Secrets Manager is a paid service with pricing based on the number of secrets stored and API calls made. There are free tiers for initial usage, but costs increase with higher usage.