AWS Misconfiguration Cloud Security Risks
AWS services misconfiguration exposes users to risks related to cloud security – a chilling reality for many businesses relying on the cloud. This isn’t just about technical jargon; it’s about real-world consequences like data breaches, hefty fines, and reputational damage. We’ll dive into the common pitfalls, explore real-life examples of what can go wrong, and arm you with the knowledge to secure your AWS environment.
Think of it as your survival guide in the wild west of cloud computing.
From improperly configured S3 buckets to vulnerable EC2 instances and IAM roles with excessive permissions, the potential attack vectors are numerous. We’ll break down the specific types of misconfigurations, how they happen, and the devastating impact they can have. We’ll also explore the crucial role of human error and how robust security practices, including regular audits and penetration testing, are your best defense.
Types of AWS Misconfigurations
AWS misconfigurations are a leading cause of security breaches in the cloud. Understanding the common types and their impact is crucial for building secure and resilient cloud infrastructure. This post will delve into specific examples across various AWS services, highlighting the vulnerabilities and potential consequences. We’ll focus on practical examples to illustrate the real-world risks involved.
S3 Bucket Misconfigurations
Improperly configured Amazon S3 buckets are a frequent source of data breaches. A lack of appropriate access controls can expose sensitive data to unauthorized individuals or the public internet.
| Service | Misconfiguration Type | Vulnerability | Impact |
|---|---|---|---|
| Amazon S3 | Publicly Accessible Buckets | Anyone can access the bucket’s contents without authentication. | Data breaches, intellectual property theft, reputational damage, financial losses due to regulatory fines. |
| Amazon S3 | Insufficient Access Control Lists (ACLs) | Improperly configured ACLs allow unauthorized users or groups to access data. | Data leaks, unauthorized modification or deletion of data. |
| Amazon S3 | Missing Encryption | Data stored in the bucket is not encrypted, making it vulnerable to interception. | Data breaches, exposure of sensitive information. |
The mechanisms by which these misconfigurations expose users to risk are straightforward. Publicly accessible buckets lack any form of authentication, meaning anyone with the bucket’s URL can access its contents. Insufficient ACLs allow access beyond intended users, while a lack of encryption means data is transmitted and stored in plain text. The consequences can range from minor inconveniences to catastrophic data breaches, leading to significant financial and reputational damage.
For instance, a company might face hefty fines for violating data privacy regulations, or suffer loss of customer trust due to a public data leak.
EC2 Instance Misconfigurations
Misconfigured Amazon EC2 instances present a significant security risk. These vulnerabilities can lead to unauthorized access and compromise of the entire system.
| Service | Misconfiguration Type | Vulnerability | Impact |
|---|---|---|---|
| Amazon EC2 | Unpatched Operating Systems | Outdated software with known vulnerabilities allows attackers to exploit weaknesses. | System compromise, data breaches, malware infections, denial-of-service attacks. |
| Amazon EC2 | Weak or Default Passwords | Easily guessed or default passwords allow unauthorized access to the instance. | Complete system takeover, data theft, and malicious activity. |
| Amazon EC2 | Open Ports and Unnecessary Services | Open ports and services that are not required increase the attack surface. | Unauthorized access, malware infections, and denial-of-service attacks. |
These misconfigurations often result from a lack of proper security hardening. Unpatched operating systems are particularly dangerous, as they offer attackers a known entry point. Weak passwords provide easy access, while open ports and unnecessary services expand the attack surface, making it easier for attackers to find vulnerabilities. The consequences can range from simple unauthorized access to complete system compromise, leading to data breaches, financial losses, and reputational damage.
Consider a scenario where a company’s database server is compromised due to weak passwords – this could result in the loss of sensitive customer data, leading to legal action and financial penalties.
IAM Role and Policy Misconfigurations
Improperly configured Identity and Access Management (IAM) roles and policies can grant excessive permissions, allowing unauthorized access to resources.
| Service | Misconfiguration Type | Vulnerability | Impact |
|---|---|---|---|
| IAM | Overly Permissive Policies | Policies grant excessive permissions to users or roles, allowing access beyond what’s necessary. | Unauthorized access to sensitive resources, data breaches, and potential misuse of services. |
| IAM | Lack of Role Rotation | Using long-lived access keys increases the risk of compromise. | Increased vulnerability to attacks, prolonged unauthorized access if keys are compromised. |
| IAM | Insufficient Logging and Monitoring | Lack of proper logging and monitoring makes it difficult to detect suspicious activity. | Delayed detection of security incidents, increased damage from attacks. |
The principle of least privilege dictates that users and roles should only be granted the minimum necessary permissions. Overly permissive policies violate this principle, increasing the risk of unauthorized access. A lack of role rotation increases the window of vulnerability if access keys are compromised. Insufficient logging and monitoring hinders the detection of malicious activity. The consequences can include unauthorized data access, resource misuse, and significant security breaches.
For example, an employee with overly permissive IAM permissions could accidentally or maliciously delete critical data, causing significant disruption and financial loss.
Impact on Data Security and Privacy

AWS misconfigurations represent a significant threat to data security and privacy. Improperly configured services can expose sensitive data, leading to breaches, regulatory fines, and reputational damage. Understanding the potential impact and implementing robust security measures is crucial for organizations leveraging the AWS cloud. This section explores the consequences of misconfigurations on data security and privacy, illustrating the risks with real-world examples and a hypothetical scenario.The ramifications of AWS misconfigurations extend far beyond simple data exposure.
Depending on the nature of the misconfiguration and the type of data involved, organizations face a cascade of potential negative consequences, including financial penalties, legal repercussions, loss of customer trust, and damage to brand reputation. Compliance with regulations like GDPR and CCPA is paramount, and failure to adhere to these standards can result in substantial fines. Data breaches resulting from misconfigurations can also severely impact an organization’s ability to operate effectively, potentially leading to business disruption and operational downtime.
Real-World Examples of AWS Misconfiguration Incidents
Several high-profile incidents highlight the devastating consequences of AWS misconfigurations. These examples underscore the importance of meticulous configuration management and robust security practices.
- In 2017, a misconfigured S3 bucket belonging to a major technology company exposed millions of user records, including personal details and sensitive financial information. This breach resulted in significant reputational damage and legal repercussions.
- Another incident involved a misconfigured Amazon RDS database, leading to unauthorized access and the exposure of customer data. The lack of proper access controls and encryption contributed to the severity of the breach.
- A healthcare provider experienced a data breach due to an improperly configured IAM role, allowing unauthorized access to sensitive patient data. This incident highlighted the critical need for strong identity and access management practices within AWS environments.
Hypothetical Scenario: Misconfiguration Leading to Data Breach
Imagine a company storing customer credit card information in an Amazon S3 bucket. Due to a misconfiguration, the bucket’s access control list (ACL) is set to public, allowing anyone with the bucket’s URL to access its contents. A malicious actor discovers the misconfigured bucket and downloads the sensitive credit card data. This leads to a massive data breach, resulting in financial losses for the company, potential legal action from affected customers, and significant reputational damage.
The company faces substantial fines under regulations like GDPR and CCPA for failing to adequately protect personal data. Furthermore, the company’s customers experience identity theft and financial fraud, further compounding the negative impact of the breach.
Best Practices for Secure AWS Configuration
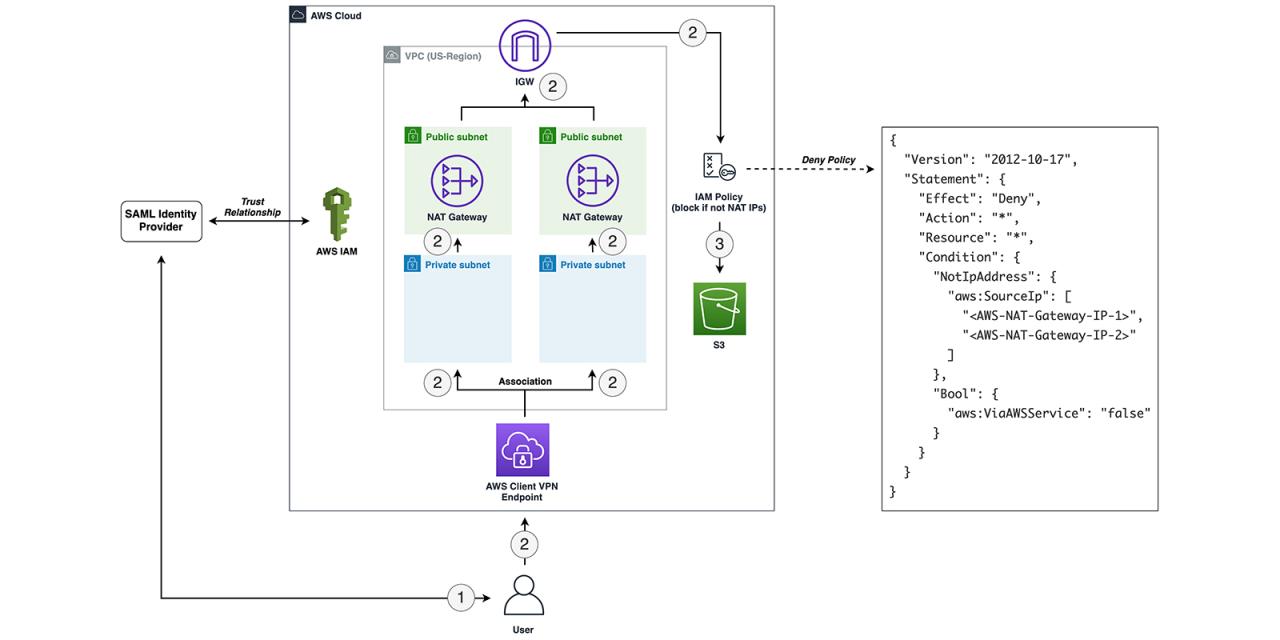
Securing your AWS environment requires a proactive and multi-layered approach. Ignoring best practices can lead to significant security vulnerabilities, exposing your data and applications to compromise. This section Artikels key strategies for building a robust and secure AWS infrastructure. Implementing these practices will significantly reduce your risk profile.
A well-defined security strategy is paramount. It should encompass all aspects of your AWS deployment, from initial design and provisioning to ongoing monitoring and maintenance. Remember that security is an ongoing process, not a one-time event.
Least Privilege Access Control
Implementing the principle of least privilege is fundamental to secure AWS configuration. This principle dictates that users and services should only be granted the minimum necessary permissions to perform their tasks. Overly permissive permissions create unnecessary attack surfaces. By limiting access, you significantly reduce the potential impact of a compromised account or service.
For example, instead of granting a user full administrator access, grant them only the specific permissions required for their role. This could include read-only access to certain S3 buckets or the ability to manage EC2 instances within a specific VPC. Regularly review and refine these permissions to ensure they remain appropriate.
Encryption at Rest and in Transit
Data encryption is crucial for protecting sensitive information both while it’s stored (at rest) and while it’s being transmitted (in transit). Encryption adds an extra layer of security, even if a breach occurs. AWS provides a variety of encryption services to help you implement this critical security control.
Encryption at rest protects data stored in services like Amazon S3, Amazon EBS, and Amazon RDS. You can use AWS managed keys (KMS) or your own keys to encrypt your data. Encryption in transit protects data as it travels between different AWS services or between your on-premises network and AWS. This is typically achieved using HTTPS or TLS for communication and VPNs for network connectivity.
Checklist of Best Practices for Securing AWS Services
This checklist provides a comprehensive overview of crucial security measures. Regularly review and update your configurations to maintain a high level of security.
- Enable Multi-Factor Authentication (MFA): Require MFA for all user accounts, including administrative accounts. This adds an extra layer of security beyond passwords.
- Regularly Rotate Access Keys: Rotate your AWS access keys regularly (at least every 90 days) to mitigate the risk of compromised credentials.
- Implement Strong Password Policies: Enforce strong password policies for all users, requiring complexity and regular changes.
- Use Security Groups and Network ACLs: Restrict network access to your instances using security groups and network ACLs. Only allow necessary inbound and outbound traffic.
- Enable AWS Shield: AWS Shield protects your applications against DDoS attacks. Enable this service to mitigate the risk of service disruptions.
- Monitor CloudTrail Logs: Regularly review CloudTrail logs to monitor API calls and detect any suspicious activity.
- Utilize AWS Config: Use AWS Config to assess the compliance of your AWS resources with your defined security standards.
- Employ IAM Roles for EC2 Instances: Instead of using access keys directly, use IAM roles for EC2 instances to grant temporary permissions.
- Regularly Patch and Update Systems: Keep your operating systems and applications up-to-date with the latest security patches.
- Implement Automated Security Scanning: Utilize automated security scanning tools to identify vulnerabilities in your AWS environment.
Tools and Techniques for Identifying and Mitigating Misconfigurations
Finding and fixing AWS misconfigurations is crucial for maintaining a secure cloud environment. Fortunately, a range of tools and techniques are available to help automate this process and improve your overall security posture. These tools offer varying levels of sophistication and integration, allowing you to tailor your approach based on your specific needs and resources.
AWS Config
AWS Config is a fully managed service that provides an audit trail of your AWS resource configurations. It continuously monitors and records changes, allowing you to track configurations over time and identify deviations from your desired state. This enables proactive identification of potential security vulnerabilities stemming from misconfigurations.
Security Auditing Tools
Beyond AWS Config, numerous third-party security auditing tools integrate with AWS to provide more comprehensive assessments. These tools often offer advanced features like automated vulnerability scanning, compliance reporting, and remediation guidance. They can analyze your entire AWS environment, identifying misconfigurations that might be missed by manual checks or even AWS Config alone. Examples include CloudSploit, Lacework, and Snyk.
Seriously, AWS misconfigurations are a HUGE cloud security headache – leaving your data vulnerable is never a good look. But building secure apps is easier than you think, especially with platforms like those discussed in this great article on domino app dev the low code and pro code future. Understanding the development process helps mitigate those AWS risks by creating more robust and secure applications from the ground up.
So, let’s all work towards better security practices!
Automated Remediation
Several tools offer automated remediation capabilities. These tools can automatically fix identified misconfigurations, reducing the manual effort required and minimizing the window of vulnerability. This automation is a key element in building a robust and scalable security posture. However, careful planning and testing are crucial before implementing automated remediation to avoid unintended consequences.
Monitoring and Alerting Systems
Implementing a robust monitoring and alerting system is essential for early detection of potential misconfigurations. This system should continuously monitor your AWS environment for changes and alert you to any deviations from your security baselines. You can leverage AWS CloudWatch, integrating it with AWS Config and other security tools, to create custom dashboards and alerts. For example, you could set up an alert triggered whenever an S3 bucket is created without server-side encryption enabled.
| Tool | Functionality | Strengths | Weaknesses |
|---|---|---|---|
| AWS Config | Continuous monitoring and recording of AWS resource configurations. Provides an audit trail and allows for compliance checks. | Built-in AWS service, integrates well with other AWS services, provides a comprehensive audit trail. | Can be complex to configure for comprehensive coverage. Requires careful setup to avoid alert fatigue. |
| CloudTrail | Provides a log of AWS API calls. Useful for identifying unauthorized changes or suspicious activity. | Comprehensive logging of API calls, useful for security investigations and compliance audits. | Requires careful analysis of logs; large volumes of data can make analysis challenging. |
| Third-party Security Auditing Tools (e.g., CloudSploit, Lacework) | Automated vulnerability scanning, compliance reporting, and remediation guidance. Often offer more advanced features than built-in AWS tools. | Advanced features, comprehensive vulnerability scanning, often provide remediation recommendations. | Can be expensive, requires integration with AWS environment, may require specialized expertise. |
| CloudWatch | Monitoring and alerting service. Can be integrated with other AWS services to monitor for specific events and metrics. | Flexible and customizable, allows for creation of custom dashboards and alerts. | Requires expertise to configure effectively, can generate large volumes of data if not configured carefully. |
Comparison of Security Automation Approaches
Different approaches to security automation exist within the AWS ecosystem. A purely manual approach is highly inefficient and prone to human error. A fully automated approach, while ideal in theory, may require significant upfront investment and careful planning to avoid unintended consequences. A hybrid approach, combining automated tools with manual oversight, often provides the best balance between efficiency and security.
This allows for automation of routine tasks while retaining human judgment for complex or nuanced situations.
Implementing a Robust Monitoring and Alerting System
A robust monitoring and alerting system involves several key steps. First, define clear security baselines and identify critical resources requiring close monitoring. Next, integrate AWS Config, CloudTrail, and other relevant services with CloudWatch. Configure CloudWatch to monitor for specific events and metrics, and set up alerts to notify you of any deviations from your baselines. Finally, regularly review and refine your monitoring and alerting system to ensure it remains effective and efficient.
This iterative process is crucial for adapting to evolving threats and maintaining a strong security posture.
Incident Response and Recovery: Aws Services Misconfiguration Exposes Users To Risks Related To Cloud Security
AWS misconfigurations can lead to significant security breaches, impacting data integrity, confidentiality, and availability. A robust incident response plan is crucial for minimizing damage and ensuring a swift recovery. This plan should be regularly tested and updated to reflect changes in your AWS environment and evolving threat landscapes.A well-defined incident response plan facilitates a coordinated and effective reaction to security incidents, reducing downtime and reputational damage.
It provides a structured approach to handling crises, ensuring that all necessary steps are taken in a timely manner. Furthermore, a detailed post-incident review helps identify weaknesses and improve future responses.
Incident Response Plan
A comprehensive incident response plan should include the following steps:
- Preparation: Establish clear roles and responsibilities, define communication channels, and create a documented incident response process. This includes identifying key personnel, establishing escalation paths, and pre-approving communication templates. Regular training exercises will ensure that the team is well-versed in their roles and responsibilities.
- Detection and Analysis: Implement robust monitoring and logging to detect potential security breaches promptly. This involves setting up alerts for suspicious activities and regularly reviewing security logs. Once a potential incident is identified, analyze its scope and impact, gathering all relevant information. The analysis should include identifying the root cause of the incident and determining the affected systems and data.
- Containment: Isolate affected systems and prevent further damage. This may involve shutting down affected services, restricting network access, or revoking compromised credentials. The goal is to limit the breach’s spread and minimize its impact.
- Eradication: Remove the root cause of the incident. This might involve patching vulnerabilities, removing malware, or restoring systems from backups. A thorough investigation is necessary to ensure that all traces of the breach are eliminated.
- Recovery: Restore affected systems and data to a functional state. This involves bringing systems back online, restoring data from backups, and verifying the integrity of the restored data. Prioritize restoring critical systems and data first.
- Post-Incident Activity: Conduct a thorough post-incident review to identify lessons learned and improve future responses. This includes documenting the incident, analyzing the root cause, and implementing corrective actions to prevent similar incidents from occurring in the future. The findings should be shared with relevant stakeholders and incorporated into updated security policies and procedures.
Minimizing Impact of Security Breaches
Effective mitigation strategies focus on preventing data exfiltration, limiting unauthorized access, and ensuring business continuity. These strategies should be integrated into the incident response plan. For example, implementing multi-factor authentication (MFA) can significantly reduce the risk of unauthorized access, even if credentials are compromised. Regular backups, stored securely and offsite, allow for rapid recovery of data in the event of a breach.
Furthermore, encryption of sensitive data both in transit and at rest adds another layer of protection, making it difficult for attackers to access even if they gain unauthorized access to systems. The implementation of a robust change management process helps to minimize the risk of misconfigurations that could lead to security vulnerabilities.
Importance of Regular Security Assessments and Penetration Testing
Regular security assessments and penetration testing are vital for proactive identification and mitigation of misconfigurations. Security assessments provide a comprehensive overview of the security posture of your AWS environment, identifying potential vulnerabilities and weaknesses. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities before malicious actors can exploit them. By regularly performing these assessments, organizations can identify and address misconfigurations before they lead to security incidents, thus reducing the risk of data breaches and other security incidents.
A well-defined schedule for both assessments and testing ensures consistent monitoring and improvement of the security posture of the cloud environment. For instance, a company might schedule penetration testing quarterly and security assessments annually, adapting the frequency based on the risk profile of their specific environment.
The Role of Human Error in AWS Misconfigurations
Let’s face it: despite the sophisticated technology involved, human error remains a significant contributor to AWS misconfigurations. While automation and robust security tools are crucial, they can’t account for the unpredictable nature of human actions. Understanding the ways humans inadvertently introduce vulnerabilities is key to building a truly secure cloud environment. This section delves into the common types of human error and provides practical steps to mitigate their impact.
The complexity of the AWS ecosystem, with its vast array of services and configurations, often overwhelms even experienced administrators. The pressure to meet deadlines, coupled with a lack of thorough understanding of security best practices, frequently leads to mistakes. These errors can range from simple typos in access control lists (ACLs) to more complex misconfigurations of security groups or S3 buckets.
The consequences can be severe, exposing sensitive data to unauthorized access, resulting in data breaches, financial losses, and reputational damage.
Examples of Human Errors Leading to Security Vulnerabilities
Human error manifests in various ways within the AWS environment. For instance, accidentally granting overly permissive permissions to an IAM user or role can expose sensitive data. Misconfiguring security groups, allowing inbound traffic from anywhere on the internet, creates a wide-open entry point for malicious actors. Similarly, leaving S3 buckets publicly accessible without proper encryption enables unauthorized access to stored data.
Incorrectly configuring VPCs or forgetting to enable multi-factor authentication (MFA) are further examples of how simple human mistakes can have significant security repercussions. A real-world example involves a company accidentally exposing customer data by leaving an S3 bucket publicly accessible, leading to a massive data breach and significant fines. Another example could be an employee accidentally deleting a crucial security group, resulting in service disruption and potential security risks.
Recommendations for Training and Awareness Programs, Aws services misconfiguration exposes users to risks related to cloud security
Effective training and awareness programs are vital to minimizing human error. A comprehensive program should incorporate the following:
Regular training sessions are essential to reinforce the importance of security best practices and keep employees updated on the latest threats and vulnerabilities. These sessions should go beyond simple presentations; they should include hands-on exercises and simulated scenarios to allow employees to practice applying security configurations in a safe environment. Moreover, it’s crucial to create a culture of security awareness where employees feel empowered to report potential security issues without fear of retribution.
This involves clear communication channels and a well-defined incident reporting process.
- Regular Security Awareness Training: Conduct frequent training sessions covering AWS security best practices, common misconfigurations, and the implications of human error.
- Hands-on Workshops and Simulations: Provide practical, interactive training that allows employees to experience the consequences of misconfigurations in a safe, controlled environment.
- Role-Based Training: Tailor training content to the specific roles and responsibilities of individuals, focusing on the security aspects relevant to their tasks.
- Gamification and Interactive Modules: Use engaging methods to enhance learning and retention, such as quizzes, interactive scenarios, and gamified challenges.
- Regular Security Audits and Assessments: Conduct periodic security audits and assessments to identify potential vulnerabilities and areas for improvement. This allows for proactive identification of potential risks before they lead to misconfigurations or breaches.
- Clear Communication Channels and Incident Reporting Procedures: Establish clear communication channels and a well-defined incident reporting process to encourage employees to report security concerns promptly and without fear of repercussions.
- Implement a “Security Champions” Program: Identify and train employees as “security champions” within their teams to promote security awareness and best practices.
Last Recap
Securing your AWS environment isn’t a one-time task; it’s an ongoing commitment. By understanding the common misconfigurations, implementing best practices, and leveraging available tools, you can significantly reduce your risk profile. Remember, proactive security measures are far more cost-effective than reactive incident response. Stay vigilant, stay informed, and stay secure in the cloud!
FAQ Section
What are the most common types of AWS misconfigurations?
Common misconfigurations include improperly configured S3 buckets (public access), overly permissive IAM roles, insecure EC2 instances (open ports), and lack of encryption.
How can I detect AWS misconfigurations?
Utilize AWS Config, security auditing tools, and penetration testing to identify vulnerabilities. Regular security assessments are also crucial.
What is the role of encryption in mitigating AWS misconfigurations?
Encryption, both at rest and in transit, significantly reduces the impact of a breach by rendering stolen data unreadable. It’s a fundamental security best practice.
What should I do if I suspect a misconfiguration?
Immediately follow your incident response plan. Isolate affected resources, investigate the root cause, and remediate the issue. Consider notifying relevant authorities if a data breach has occurred.