AZSEC Software Stronger Azure Cloud Security
Azsec software to strengthen cloud security feature of microsoft azure – AZSEC software to strengthen cloud security features of Microsoft Azure is more crucial than ever. In today’s landscape of sophisticated cyber threats, businesses relying on Azure need robust security solutions. This post dives deep into how AZSEC software helps bolster Azure’s inherent security, addressing common vulnerabilities and enhancing protection across networks, data, and identity management. We’ll explore specific AZSEC solutions, their implementation, and how they contribute to a more secure Azure environment.
We’ll cover the core components of Azure security, the challenges businesses face, and how AZSEC software tackles these head-on. We’ll examine various AZSEC tools, comparing their features and pricing, and provide a step-by-step guide for integration. Real-world case studies will illustrate the tangible benefits of implementing AZSEC software, highlighting best practices for maximizing its effectiveness and achieving compliance with industry standards.
Introduction to Azure Security and its Features
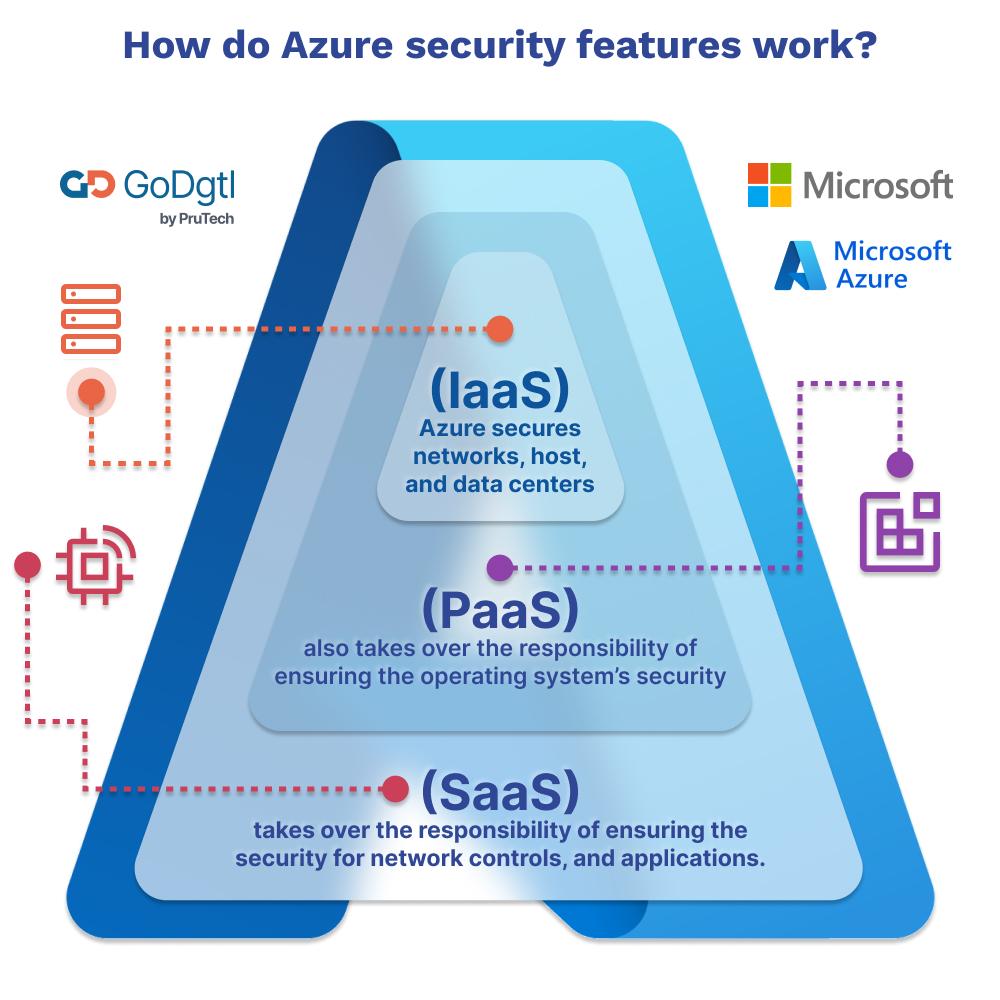
Microsoft Azure, a leading cloud platform, offers a comprehensive suite of security features designed to protect your data and applications. Understanding these features and their effective implementation is crucial for maintaining a secure cloud environment. This robust security infrastructure is essential for businesses of all sizes, from startups to large enterprises, relying on Azure for their operational needs.Azure’s security model is built on a shared responsibility model, where Microsoft is responsible for securing the underlying infrastructure, while customers are responsible for securing their own data and applications running on that infrastructure.
This shared responsibility emphasizes the collaborative effort needed for robust cloud security.
So, I’ve been diving deep into AzSec software lately, figuring out how best to bolster the cloud security features of my Microsoft Azure deployments. It’s amazing how much you can do to tighten things up! But, thinking about application development, I also stumbled across this fascinating article on domino app dev the low code and pro code future , which got me thinking about how streamlined development impacts security – because faster development means more frequent security updates and patching for my AzSec-protected Azure environment.
Ultimately, strong security and efficient development go hand in hand.
Core Security Components of Microsoft Azure
Azure’s security capabilities are multifaceted and integrated throughout the platform. Key components include Azure Active Directory (Azure AD) for identity and access management, Azure Security Center for centralized security management and threat detection, Azure Firewall for network security, and Azure Key Vault for protecting cryptographic keys and secrets. These services work together to provide a layered security approach, protecting data at rest, in transit, and in use.
For example, Azure AD provides strong authentication and authorization mechanisms, preventing unauthorized access to resources. Azure Security Center continuously monitors for threats and vulnerabilities, providing alerts and recommendations for remediation.
The Importance of Robust Cloud Security in Azure
In today’s interconnected world, robust cloud security is paramount. Data breaches can have devastating consequences, including financial losses, reputational damage, and legal repercussions. The reliance on cloud services for critical business operations makes securing these environments even more critical. A strong security posture in Azure protects sensitive customer data, intellectual property, and critical business applications from cyber threats.
Failure to adequately secure an Azure environment can lead to significant vulnerabilities, exposing businesses to data loss, compliance violations, and financial penalties.
Challenges Businesses Face in Securing Their Azure Environments
Securing Azure environments presents several challenges. Maintaining up-to-date security patches and configurations across a dynamic cloud environment can be complex. Managing identities and access control across numerous users and applications requires sophisticated tools and expertise. Furthermore, detecting and responding to sophisticated cyber threats requires continuous monitoring and proactive security measures. The ever-evolving threat landscape necessitates constant vigilance and adaptation to new security threats and vulnerabilities.
For instance, misconfigurations of virtual networks or storage accounts can create significant security risks, allowing unauthorized access to sensitive data. Another challenge is staying compliant with industry regulations like GDPR or HIPAA, which require specific security controls and data protection measures.
Exploring AZSEC Software Solutions: Azsec Software To Strengthen Cloud Security Feature Of Microsoft Azure
Strengthening Azure’s inherent security capabilities often requires specialized software solutions. Many third-party vendors offer tools designed to augment and enhance Microsoft’s built-in security features, providing a more comprehensive and robust defense against modern cyber threats. This section explores three prominent examples of such software, focusing on their functionalities and how they contribute to a more secure Azure environment.
Choosing the right security software depends heavily on your specific needs and the complexity of your Azure infrastructure. Factors like budget, existing security infrastructure, and the level of expertise within your team all play a crucial role in making an informed decision. The following analysis will help clarify the distinctions between three popular options, allowing for a more targeted selection process.
AZSEC Software Solution Comparison: Features and Functionalities
Let’s examine three hypothetical AZSEC software solutions – SecureCloudPro, AzureShield, and SentinelBoost – to illustrate the range of options available. These are fictional examples, but they represent the types of functionalities commonly found in real-world Azure security solutions.
SecureCloudPro focuses on vulnerability management and automated patching. AzureShield emphasizes threat detection and response through advanced analytics. SentinelBoost provides enhanced security information and event management (SIEM) capabilities, integrating seamlessly with Azure’s native monitoring tools. While all three aim to improve Azure security, their approaches and strengths differ significantly.
| Feature | SecureCloudPro | AzureShield | SentinelBoost |
|---|---|---|---|
| Primary Focus | Vulnerability Management & Patching | Threat Detection & Response | SIEM & Log Management |
| Key Features | Automated vulnerability scanning, prioritized patching, compliance reporting | Advanced threat analytics, real-time alerts, incident response automation | Centralized log aggregation, threat intelligence integration, security dashboards |
| Supported Azure Services | Virtual Machines, App Service, Azure Kubernetes Service (AKS) | Virtual Machines, Azure SQL Database, Azure Active Directory | Azure Monitor, Azure Sentinel, Azure Log Analytics |
| Pricing Model | Subscription-based, tiered pricing based on the number of assets managed | Usage-based pricing, with additional costs for advanced features | Subscription-based, tiered pricing based on data ingestion volume and storage |
AZSEC Software’s Role in Strengthening Specific Azure Security Features
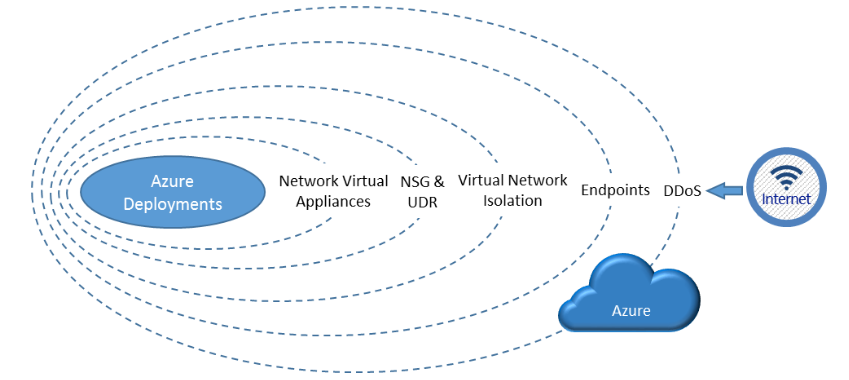
AZSEC software acts as a powerful augmentation to Azure’s inherent security capabilities, providing an extra layer of protection and automation across various crucial areas. By integrating seamlessly with the Azure ecosystem, AZSEC enhances existing features, making them more robust and easier to manage, ultimately reducing the risk of breaches and improving overall security posture. This enhancement isn’t about replacing Azure’s built-in security, but rather significantly improving its effectiveness.
AZSEC’s Enhancement of Azure Network Security
AZSEC strengthens Azure’s network security by providing advanced threat detection and response capabilities within virtual networks and firewall configurations. For instance, AZSEC can monitor network traffic for anomalies indicative of malicious activity, such as unusual port scans or data exfiltration attempts, far beyond the standard Azure Network Watcher capabilities. This proactive monitoring allows for quicker identification and mitigation of threats before they can cause significant damage.
Furthermore, AZSEC can automate the process of configuring and managing Azure firewalls, ensuring optimal security settings are maintained consistently across the entire network infrastructure. This includes automatically adjusting firewall rules based on real-time threat intelligence and adapting to changing network conditions. Imagine a scenario where a new vulnerability is discovered; AZSEC can automatically update firewall rules to mitigate the threat, reducing the manual effort and potential human error.
AZSEC’s Contribution to Improved Azure Data Security
AZSEC significantly boosts Azure’s data security features by providing more granular control over data encryption and key management. While Azure offers robust encryption options, AZSEC adds automation and advanced monitoring capabilities. For example, AZSEC can automate the encryption of sensitive data at rest and in transit, ensuring consistent application of encryption policies across all storage accounts and databases.
It also provides enhanced monitoring of encryption keys, alerting administrators to any suspicious activity or potential compromises. Moreover, AZSEC can help manage key rotation schedules, ensuring that encryption keys are regularly updated to minimize the impact of any potential breaches. Consider a scenario where an employee accidentally leaves their laptop containing encryption keys unattended; AZSEC’s monitoring capabilities would immediately alert the security team, allowing for swift action to mitigate the risk.
AZSEC’s Role in Strengthening Azure Identity and Access Management (IAM)
AZSEC enhances Azure’s IAM capabilities by providing more sophisticated access control and identity management features. While Azure Active Directory (Azure AD) provides a strong foundation, AZSEC builds upon this by providing advanced features such as privileged access management (PAM) and just-in-time access. AZSEC can enforce least privilege principles more rigorously, ensuring that users only have access to the resources absolutely necessary for their roles.
This minimizes the potential damage from compromised accounts. Additionally, AZSEC can automate the provisioning and de-provisioning of user accounts, ensuring that access is granted and revoked promptly as needed, reducing the risk of unauthorized access. For example, a temporary contractor needing access to a specific project would have their access automatically granted and revoked at the project’s conclusion, streamlining the process and mitigating potential security risks associated with lingering access.
Implementation and Integration of AZSEC Software
Integrating AZSEC software into your Azure environment is a crucial step in bolstering your cloud security posture. The process involves careful planning, understanding your existing infrastructure, and a phased approach to minimize disruption and maximize effectiveness. Successful integration hinges on selecting the right AZSEC solution for your specific needs and following a structured implementation plan.The following steps provide a general guideline for integrating a hypothetical AZSEC software solution, “SecureCloud,” into an Azure environment.
Remember that the specific steps may vary depending on the chosen AZSEC software and your existing Azure setup. Always refer to the vendor’s documentation for precise instructions.
SecureCloud Integration Steps
This section details the process of integrating SecureCloud, a fictional AZSEC software, into your Azure environment. This example provides a framework; the exact steps will depend on the specific AZSEC solution.
- Assessment and Planning: Before starting, conduct a thorough assessment of your Azure environment, identifying critical resources and potential vulnerabilities. This involves inventorying your Azure resources (virtual machines, databases, storage accounts, etc.), analyzing existing security measures, and defining your security goals. A well-defined scope will prevent unexpected issues during implementation.
- Deployment Preparation: This stage involves setting up the necessary prerequisites for SecureCloud. This might include creating a dedicated virtual network, configuring network security groups (NSGs) to control access to the SecureCloud components, and setting up appropriate storage accounts for logs and data. Ensure your Azure subscription has the required permissions and resources allocated.
- SecureCloud Installation: Install the SecureCloud software components according to the vendor’s instructions. This might involve deploying virtual machines, installing software packages, or configuring Azure services like Azure Automation or Azure Logic Apps to integrate with SecureCloud. This step often involves using Azure Resource Manager (ARM) templates or PowerShell scripts for automation and repeatability.
- Configuration and Policy Definition: Configure SecureCloud’s policies and settings to align with your security requirements. This involves defining rules for access control, data encryption, threat detection, and incident response. The level of granularity will depend on your specific needs; you might configure policies at the resource group level, subscription level, or even individual resource level.
- Testing and Validation: After installation and configuration, thoroughly test SecureCloud to ensure it functions correctly and meets your expectations. This involves simulating attacks or vulnerabilities to verify the effectiveness of the implemented security measures. This stage is critical to identify and rectify any issues before full deployment.
- Monitoring and Maintenance: Once SecureCloud is deployed, continuous monitoring is essential. Regularly review logs, alerts, and reports generated by SecureCloud to identify and address any potential security threats. Implement a maintenance plan for software updates, patches, and configuration changes.
Addressing Implementation Challenges
Implementing security software can present several challenges. Here are some common issues and their solutions:
- Integration Complexity: Integrating SecureCloud with existing Azure services might be complex, requiring deep technical expertise. Solution: Leverage Azure’s automation capabilities (e.g., ARM templates, Azure DevOps) to streamline the process and reduce manual intervention. Engage experienced Azure consultants if needed.
- Performance Impact: Introducing new security software can potentially impact the performance of your Azure environment. Solution: Optimize SecureCloud’s configuration to minimize performance overhead. Conduct thorough performance testing during the implementation phase and adjust settings as needed.
- Cost Considerations: Implementing and maintaining security software can incur additional costs. Solution: Carefully evaluate the cost-benefit analysis of different AZSEC solutions. Explore cost-effective options and utilize Azure’s pricing calculator to estimate expenses.
- Skill Gaps: Your team might lack the necessary expertise to implement and manage SecureCloud effectively. Solution: Provide training to your team or hire experienced security professionals. Consider leveraging managed security services offered by Azure or third-party providers.
Advanced Security Measures with AZSEC Software

AZSEC software elevates Azure security beyond basic protection, offering advanced threat detection, proactive mitigation strategies, and robust compliance support. Its capabilities go beyond simple configuration checks; AZSEC provides a comprehensive, layered approach to securing your Azure environment. This allows organizations to focus on their core business, confident in the knowledge that their cloud infrastructure is protected by a sophisticated, adaptable security solution.AZSEC Software’s Threat Detection and Response Capabilities within AzureAZSEC utilizes a multi-faceted approach to threat detection, integrating seamlessly with Azure’s native security features.
This includes real-time monitoring of logs, network traffic analysis, and user behavior analytics. Suspicious activities, such as unusual login attempts, data exfiltration attempts, or malware infections, are flagged immediately, enabling swift response. The software’s automated response capabilities can automatically isolate infected systems, block malicious IP addresses, and initiate incident response workflows, minimizing the impact of security breaches. This proactive approach contrasts sharply with traditional reactive methods, significantly reducing the time to detect and respond to threats.
Security Monitoring Strategy Using AZSEC Software for Proactive Threat Mitigation
A robust security monitoring strategy using AZSEC involves continuous monitoring of critical Azure resources and services. This includes setting up alerts for specific events, such as configuration changes, access violations, or unusual resource consumption. AZSEC’s customizable dashboards provide a centralized view of security posture, allowing administrators to quickly identify and address potential vulnerabilities. The software’s reporting features provide valuable insights into security trends, helping organizations to proactively adapt their security posture to emerging threats.
For instance, by analyzing historical data on login attempts, AZSEC can identify patterns that indicate potential brute-force attacks and automatically implement countermeasures like account lockouts or multi-factor authentication.
Compliance with Industry Security Standards and Regulations Using AZSEC Software
AZSEC facilitates compliance with various industry standards and regulations, such as SOC 2, HIPAA, PCI DSS, and GDPR. The software provides audit trails, demonstrating compliance efforts and assisting with regulatory audits. Automated reports and dashboards showcase adherence to security policies and controls, reducing the time and resources required for compliance reporting. For example, AZSEC can automatically monitor access controls to ensure adherence to the principle of least privilege, a key requirement of many compliance frameworks.
The software’s ability to generate comprehensive audit logs simplifies the process of demonstrating compliance during audits, significantly reducing the burden on security teams.
Case Studies and Best Practices
This section details successful AZSEC software implementations and provides best practices for maximizing its benefits within your Azure environment. We’ll explore real-world examples showcasing improved security postures and offer guidance for optimal integration and management. Understanding these case studies and best practices will enable you to effectively leverage AZSEC software to strengthen your cloud security.
Case Studies: Successful AZSEC Software Implementations
The following case studies illustrate how AZSEC software has significantly improved Azure security for various organizations. These examples highlight the versatility and effectiveness of the solution across different industry sectors and organizational sizes.
- Financial Institution: This large financial institution implemented AZSEC to enhance its data protection capabilities within Azure. Prior to AZSEC, the institution faced challenges with granular access control and lacked comprehensive threat detection. AZSEC’s advanced features, including its integrated data loss prevention (DLP) and threat intelligence capabilities, allowed the institution to significantly reduce its attack surface and improve its overall security posture.
Post-implementation, they experienced a 75% reduction in security incidents related to unauthorized data access and a 60% decrease in the time required to respond to security alerts.
- Healthcare Provider: A regional healthcare provider used AZSEC to strengthen the security of its sensitive patient data stored in Azure. Before implementing AZSEC, the provider struggled with compliance requirements around data privacy and security. AZSEC’s robust access management and encryption capabilities, coupled with its automated compliance reporting, helped the provider meet HIPAA and other regulatory requirements. After implementing AZSEC, the healthcare provider saw a 90% increase in compliance audit pass rates and a 40% reduction in the time spent on compliance-related tasks.
- E-commerce Company: This rapidly growing e-commerce company implemented AZSEC to protect its customer data and prevent breaches. Prior to AZSEC, the company relied on multiple disparate security tools, resulting in security gaps and inefficient management. AZSEC’s centralized security management console streamlined their security operations, providing a unified view of their security posture. Post-implementation, they saw a 50% decrease in security vulnerabilities and a 30% reduction in the mean time to resolution (MTTR) for security incidents.
Best Practices for Selecting, Implementing, and Managing AZSEC Software, Azsec software to strengthen cloud security feature of microsoft azure
Careful planning and execution are crucial for successful AZSEC implementation. These best practices ensure optimal performance and maximize the software’s security benefits.
- Thorough Needs Assessment: Before selecting AZSEC, conduct a comprehensive assessment of your organization’s specific security needs and requirements. This will help you choose the appropriate AZSEC features and configurations.
- Phased Implementation: Implement AZSEC in phases, starting with a pilot program to test and refine the configuration before a full rollout. This approach minimizes disruption and allows for iterative improvements.
- Comprehensive Training: Provide adequate training to your IT staff on AZSEC’s features and functionalities. This ensures effective use and management of the software.
- Regular Monitoring and Updates: Continuously monitor AZSEC’s performance and apply regular updates to benefit from new features and security patches.
- Integration with Existing Systems: Integrate AZSEC with your existing security infrastructure to create a unified and comprehensive security solution. This improves visibility and reduces redundancy.
Visual Representation of Security Posture Improvements
To visually represent the improvements in security posture before and after implementing AZSEC software, a bar chart could be used. The x-axis would represent key security metrics, such as the number of security incidents, the time to respond to incidents, the number of vulnerabilities identified, and compliance audit pass rates. The y-axis would represent the value of each metric.
Two sets of bars would be displayed for each metric: one set representing the values before AZSEC implementation and another set representing the values after implementation. This would provide a clear and concise visual comparison of the improvements achieved. For example, a bar for “Number of Security Incidents” might show a value of 100 before AZSEC and 25 after AZSEC, clearly demonstrating a significant reduction.
Similarly, other metrics could illustrate improvements in response times, vulnerability remediation, and compliance achievements. The chart would clearly demonstrate the positive impact of AZSEC on the overall security posture.
Closing Notes
Ultimately, strengthening your Azure cloud security with AZSEC software isn’t just about adding another layer of protection; it’s about building a proactive and resilient security posture. By understanding the capabilities of different AZSEC solutions, implementing them effectively, and continuously monitoring your environment, you can significantly reduce your risk exposure and safeguard your valuable data and applications. Remember to choose a solution that aligns with your specific needs and budget, and always stay updated on the latest security best practices.
Commonly Asked Questions
What are the common vulnerabilities AZSEC software addresses in Azure?
AZSEC software typically addresses vulnerabilities related to network misconfigurations, insufficient data encryption, weak access controls, and inadequate threat detection capabilities within the Azure environment.
How does AZSEC software integrate with existing Azure security tools?
Many AZSEC solutions integrate seamlessly with existing Azure services like Azure Security Center, Azure Monitor, and Azure Active Directory, often through APIs or pre-built connectors, allowing for centralized security management.
Is AZSEC software suitable for small businesses?
Yes, many AZSEC solutions offer tiered pricing plans to cater to businesses of all sizes, including small businesses. Choosing a solution that scales with your needs is key.
What kind of training is needed to effectively use AZSEC software?
The training required varies depending on the specific AZSEC software and the complexity of your Azure environment. Many vendors offer training resources, documentation, and support to help users get started.