Benefits on Information Security Automation
Benefits on Information Security Automation: In today’s hyper-connected world, cybersecurity is paramount. Manual security processes are simply not cutting it anymore. The sheer volume of data, the sophistication of cyber threats, and the ever-evolving landscape demand a more efficient and robust approach. That’s where automation steps in, transforming how we protect our digital assets. This isn’t just about saving time; it’s about fundamentally strengthening our security posture and proactively mitigating risks.
Let’s dive into the game-changing advantages of automating information security.
From automating vulnerability scanning and patching to streamlining incident response and bolstering compliance efforts, the impact is undeniable. We’ll explore how automation boosts efficiency, reduces human error, enhances accuracy, and ultimately delivers significant cost savings and a powerful return on investment (ROI). We’ll even look at how it helps organizations scale their security operations to handle ever-growing data volumes and adapt to emerging threats.
Get ready to see how automation is revolutionizing the world of information security!
Enhanced Efficiency and Productivity
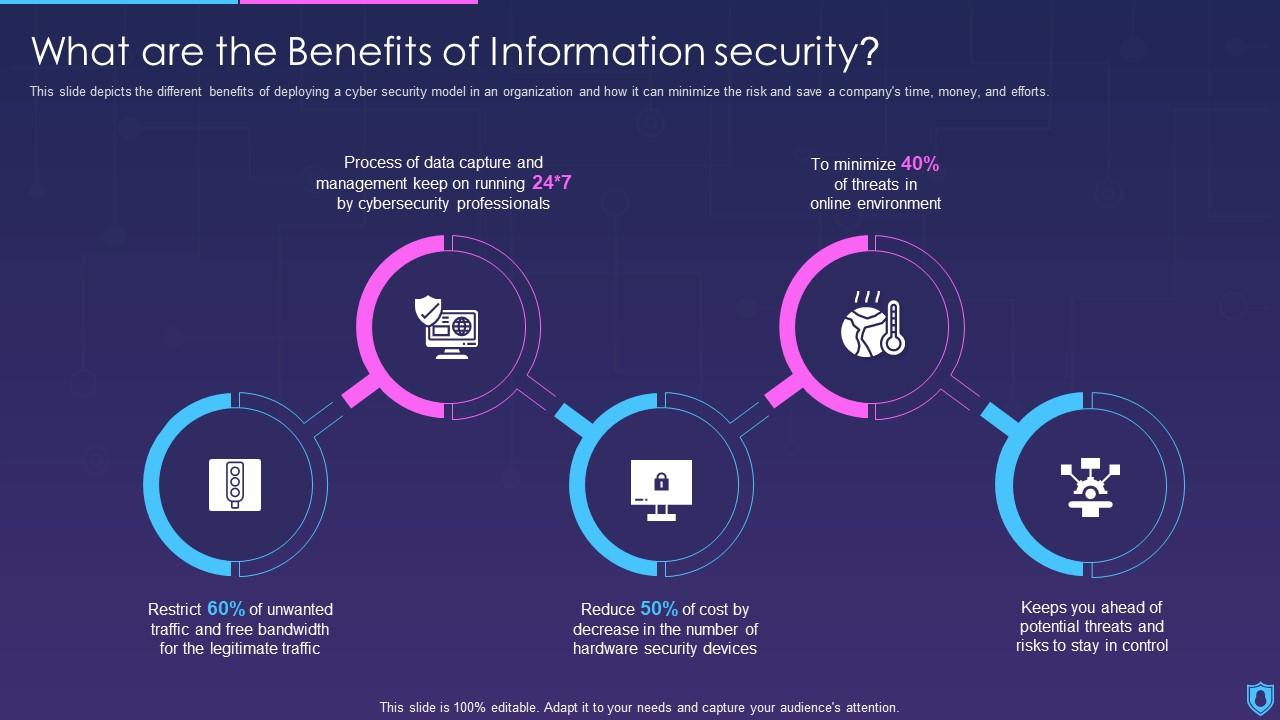
Automating information security tasks is no longer a luxury; it’s a necessity in today’s fast-paced digital landscape. Manual processes, while sometimes offering a sense of control, often fall short in terms of speed, scalability, and consistency, leaving security teams overwhelmed and potentially vulnerable. Automation provides a powerful solution, streamlining workflows and freeing up valuable human resources for more strategic initiatives.The benefits of automation are multifaceted, significantly impacting efficiency and productivity across the board.
By automating repetitive and time-consuming tasks, security teams can focus on higher-level responsibilities such as threat hunting, incident response, and security architecture design. This shift in focus leads to a more proactive and effective security posture, minimizing risks and maximizing protection.
Automated Security Processes and Reduced Manual Effort
Automating various security processes drastically reduces manual effort and the time spent on routine tasks. For instance, vulnerability scanning, once a labor-intensive process involving manual configuration, scanning, and analysis, can now be automated using specialized tools. These tools automatically scan systems for vulnerabilities, generate reports, and even prioritize remediation efforts based on severity levels. Similarly, tasks like log analysis, user provisioning, and security awareness training can be automated, freeing up security personnel to concentrate on more complex challenges.
Automated patch management ensures systems are consistently updated with the latest security patches, reducing the window of vulnerability exploitation. Automated incident response systems can detect and respond to security incidents in real-time, minimizing damage and downtime.
Impact of Automation on Team Productivity and Resource Allocation
The impact of automation on team productivity is transformative. With automated systems handling routine tasks, security teams can accomplish more in less time. This increased efficiency allows for better resource allocation, enabling organizations to optimize their security investments. Instead of dedicating a large team to repetitive tasks, organizations can reassign personnel to more strategic roles, such as developing and implementing advanced security strategies, improving incident response capabilities, or focusing on emerging threats.
This optimized resource allocation directly contributes to a more robust and proactive security posture. For example, a team previously spending 50% of its time on manual vulnerability scanning could redirect that time towards proactive threat hunting, significantly improving the overall security landscape.
Comparison of Manual vs. Automated Vulnerability Scanning
The following table illustrates the time savings achieved by automating vulnerability scanning:
| Task | Manual Process | Automated Process | Time Saved |
|---|---|---|---|
| Vulnerability Scanning of 100 Servers | Manual configuration, scanning, and analysis; potentially taking multiple days or even weeks depending on server complexity and team size. Requires significant manual effort and expertise for report interpretation. | Automated scanning and reporting using a vulnerability scanner; typically completing the scan within hours, depending on the number of servers and the scanner’s capabilities. Automated report generation with prioritized vulnerability listings. | Days or weeks reduced to hours. Significant reduction in manual effort. |
Improved Accuracy and Reduced Human Error
Automation in information security significantly minimizes the risk of human error, a leading cause of security breaches. Human fallibility, including fatigue, distraction, and misinterpretation, introduces vulnerabilities that automated systems can effectively mitigate. By automating repetitive tasks and enforcing consistent security policies, organizations can drastically reduce the likelihood of costly and damaging incidents.The inherent limitations of human attention and the potential for mistakes are dramatically reduced through the implementation of automated security systems.
These systems operate with unwavering precision and consistency, eliminating the unpredictable element of human judgment in critical security functions. This leads to more reliable security posture and faster response times to potential threats.
Examples of Human Error and Automation Prevention, Benefits on information security automation
Human error accounts for a significant percentage of security incidents. A common example is the accidental clicking of a phishing link, leading to malware infection or credential theft. Automated systems, such as email security gateways with advanced threat detection, can identify and block suspicious emails before they reach the user’s inbox. Another example involves misconfiguration of security settings, leaving systems vulnerable to exploitation.
Automated configuration management tools can ensure consistent and secure settings across all devices and applications, preventing such vulnerabilities. Finally, slow response times to security alerts, often due to staff overload or lack of expertise, can allow attacks to escalate. Automated systems can prioritize alerts based on severity and trigger immediate responses, such as isolating infected systems or initiating incident response procedures.
Consistent Application of Security Policies through Automation
Consistent enforcement of security policies is crucial for maintaining a robust security posture. Human oversight, however, is susceptible to inconsistency and oversight. Automation ensures that security policies are applied uniformly across all systems and users, regardless of time or workload. For example, an automated system can consistently monitor user access attempts, block unauthorized access, and log all activity for auditing purposes.
This eliminates the possibility of inconsistent application of access control policies due to human fatigue or varying interpretations. Furthermore, automated vulnerability scanning and patching ensure that systems are consistently updated with the latest security patches, minimizing the window of vulnerability.
Scenario: Preventing Accidental Data Exposure
Imagine a scenario where a database administrator needs to temporarily grant broader access permissions to a colleague for a specific task. Without automation, this could lead to human error, such as forgetting to revoke those permissions afterward. This oversight could leave sensitive data exposed for an extended period, creating a significant security risk. An automated system, however, could be configured to automatically revoke those elevated permissions after a predetermined time or upon completion of the specific task.
This eliminates the risk of human error and ensures that access remains strictly controlled, safeguarding sensitive data. This automated approach guarantees consistent and timely revocation of access, regardless of the administrator’s workload or memory.
Strengthened Security Posture
Automating information security tasks significantly bolsters your overall security posture. Manual processes, while sometimes necessary, are inherently prone to human error and are simply unable to keep pace with the ever-increasing volume and sophistication of cyber threats. Automation provides a scalable and consistent approach to security, leading to more robust defenses and faster response times.Automation enhances security across several key areas.
It allows for continuous monitoring and analysis of systems, identifying vulnerabilities and potential threats far more quickly than human analysts working alone. It also enables the rapid deployment of security controls and the immediate execution of remediation actions, minimizing the window of vulnerability and reducing the impact of successful attacks.
Automated Security Controls vs. Manual Controls
Automated security controls offer a significant advantage over manual controls in terms of speed, consistency, and scalability. Manual processes are slow, prone to human error, and struggle to maintain consistent application across a large and complex IT infrastructure. For example, imagine manually patching thousands of servers across a global network – a task that is both time-consuming and highly susceptible to mistakes.
Automation, however, can deploy patches consistently and efficiently across the entire infrastructure in a fraction of the time. This consistency is crucial in ensuring that all systems are equally protected, minimizing the risk of exploitation through unpatched vulnerabilities. The scalability of automated controls also allows organizations to easily adapt to changes in their infrastructure or to emerging threats, something manual controls simply cannot achieve effectively.
Improved Threat Detection and Response
Automation dramatically improves threat detection and response capabilities. Automated systems can analyze vast quantities of security data in real-time, identifying patterns and anomalies that might go unnoticed by human analysts. This allows for the detection of threats much earlier in the attack lifecycle, when mitigation is easier and less costly. Furthermore, automated response mechanisms can instantly implement countermeasures, such as blocking malicious IP addresses or isolating infected systems, preventing further damage.
Consider a distributed denial-of-service (DDoS) attack; automated systems can detect the surge in traffic and automatically implement mitigation techniques, such as rate limiting or traffic filtering, much faster than human intervention could manage. This rapid response can significantly reduce the impact of the attack.
Automated Security Tools and Their Benefits
The effectiveness of a strengthened security posture hinges on the proper utilization of automated security tools. A well-integrated suite of tools working in concert can significantly reduce risk.
Here’s a list of some key tools and their benefits:
- Security Information and Event Management (SIEM) systems: Collect and analyze security logs from various sources, providing a centralized view of security events and facilitating threat detection and incident response. Benefits include improved visibility into security events, faster threat detection, and streamlined incident response.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for malicious activity and either alert administrators (IDS) or automatically block malicious traffic (IPS). Benefits include proactive threat detection and prevention, minimizing the impact of attacks.
- Vulnerability scanners: Automatically identify security vulnerabilities in systems and applications. Benefits include proactive identification of weaknesses, allowing for timely remediation and reducing the attack surface.
- Endpoint Detection and Response (EDR) solutions: Monitor endpoint devices (computers, laptops, mobile devices) for malicious activity. Benefits include improved detection of malware and other threats on endpoints, facilitating faster incident response.
- Security Orchestration, Automation, and Response (SOAR) platforms: Automate security workflows, improving efficiency and effectiveness of security operations. Benefits include improved incident response times, reduced manual effort, and increased consistency in security operations.
Cost Savings and ROI: Benefits On Information Security Automation
Automating information security tasks isn’t just about improving efficiency; it’s a strategic investment that delivers significant cost savings and a strong return on investment (ROI). By automating repetitive, manual processes, organizations can free up valuable human resources, reduce the risk of costly errors, and ultimately lower their overall security budget. This translates to a healthier bottom line and the ability to reinvest those savings in other critical areas of the business.Automating various security functions leads to a substantial reduction in operational costs.
The most significant savings stem from minimizing human intervention in tasks prone to errors, such as vulnerability scanning, incident response, and log analysis. Reduced labor costs, coupled with the prevention of costly security breaches, paint a compelling picture of the financial benefits.
Cost Savings Associated with Automated Security Solutions
The potential cost savings vary significantly depending on the specific security solutions implemented. For instance, automating vulnerability scanning can reduce the time spent on manual patching, potentially saving hundreds or even thousands of hours annually, depending on the size of the network and the frequency of scans. Similarly, automating incident response through Security Information and Event Management (SIEM) systems can significantly reduce the time it takes to identify and remediate security incidents, minimizing downtime and potential financial losses.
Automated threat intelligence platforms can further reduce costs by identifying and mitigating threats before they escalate into major incidents. Consider a mid-sized company with 500 employees. Manual vulnerability scanning might take a security team a week, costing several thousand dollars in labor. An automated system might complete the same task in a few hours, dramatically reducing this cost.
Return on Investment (ROI) of Information Security Automation
Calculating the ROI of information security automation requires a comprehensive cost-benefit analysis. This involves quantifying the costs of implementation (software licenses, hardware, training, etc.) and comparing them to the projected savings (reduced labor costs, avoided breach costs, improved efficiency). A positive ROI indicates that the investment in automation pays for itself through reduced costs and increased efficiency. For example, a company that invests $50,000 in a SIEM system might see a reduction in incident response time, resulting in $100,000 in avoided downtime costs within the first year, yielding a positive ROI of $50,000.
The long-term ROI is even more significant as the system continues to prevent breaches and improve efficiency over time.
Hypothetical Cost-Benefit Analysis: Phishing Prevention
Let’s consider a hypothetical scenario: a company experiences an average of 10 successful phishing attacks per year, each costing $10,000 in remediation, investigation, and potential data breach fines. The total annual cost is $100,000. Implementing an automated phishing prevention system costs $20,000 annually (including software, maintenance, and employee training). If the system reduces successful phishing attacks by 80%, the company will save $80,000 annually ($100,0000.80).
Subtracting the annual cost of the system ($20,000), the net savings are $60,000, representing a significant ROI. This analysis demonstrates that even a relatively modest investment in automation can yield substantial returns by preventing costly security breaches.
Scalability and Adaptability
Automation is the key to unlocking truly scalable and adaptable information security. In today’s dynamic threat landscape, a static security posture is simply not enough. Organizations need systems that can grow and evolve alongside their business, effortlessly handling increasing data volumes and adapting to new threats and technologies as they emerge. This is where the power of automation truly shines.Automation enables organizations to scale their security operations effectively by automating repetitive tasks, allowing security teams to focus on more strategic initiatives.
This scalability isn’t just about handling more data; it’s about handling it
- efficiently* and
- effectively*. Instead of being bogged down in manual processes, security teams can proactively address emerging threats and vulnerabilities, improving overall security posture and resilience.
Automation’s Adaptability to Evolving Threats
The ability to adapt to emerging threats is critical. Automation allows security systems to learn and evolve. For example, machine learning algorithms used in intrusion detection systems (IDS) can be trained on new attack patterns and adapt their detection capabilities accordingly. As new malware families emerge, automated sandboxing solutions can quickly analyze and categorize these threats, updating security policies in real-time.
This proactive adaptation ensures that security measures remain relevant and effective against the latest threats, preventing costly breaches and data loss. Consider a scenario where a new zero-day exploit is discovered. A manually managed system would require significant time and effort to patch and update. An automated system, however, could detect the exploit, deploy patches across the network, and potentially even isolate affected systems automatically, minimizing the impact of the attack.
Handling Large Volumes of Security Data
Modern organizations generate massive amounts of security data. Logs from servers, firewalls, endpoints, and cloud services all contribute to a flood of information. Manual analysis of this data is simply impractical. Automation steps in to provide solutions. Security Information and Event Management (SIEM) systems, for example, leverage automation to collect, correlate, and analyze this data, identifying potential threats and security incidents much faster than human analysts could.
Automated threat intelligence platforms can also process and correlate threat feeds from various sources, providing valuable context and improving the accuracy of threat detection. This ability to efficiently process large volumes of data is crucial for maintaining a strong security posture in a data-rich environment.
System Architecture for Scalable Automation
The following describes a system architecture diagram illustrating how automation scales with organizational growth. Imagine a three-tiered architecture:
Tier 1: Data Ingestion and Collection. This layer comprises various agents and sensors deployed across the organization’s infrastructure (on-premises, cloud, and edge). These agents collect security logs, events, and other relevant data from diverse sources. This layer scales horizontally by adding more agents as the organization expands its infrastructure.
Tier 2: Data Processing and Analysis. This layer houses the core automation components, including SIEM, threat intelligence platforms, and security orchestration, automation, and response (SOAR) tools. These tools correlate data from Tier 1, analyze for threats, and generate alerts. This layer scales vertically by upgrading the processing power of the servers or horizontally by adding more processing nodes to handle increased data volumes. Load balancing is crucial at this level to ensure even distribution of workload.
Tier 3: Response and Remediation. This layer executes automated responses based on the analysis in Tier 2. This might include blocking malicious IP addresses, patching vulnerabilities, or isolating infected systems. This layer can also scale horizontally by adding more automation agents to execute remediation tasks across the infrastructure. This layer may also integrate with ticketing systems and incident management tools to facilitate human intervention when necessary.
This architecture allows for both vertical and horizontal scaling. As the organization grows, more agents can be added in Tier 1, more processing power in Tier 2, and more automation agents in Tier 3. This modular design ensures that the security automation system can adapt to the changing needs of the organization, providing a scalable and resilient security posture.
Faster Incident Response
In today’s always-on digital world, rapid incident response is critical. A swift and efficient reaction to security breaches minimizes damage, maintains business continuity, and protects reputation. Automation plays a pivotal role in achieving this speed and efficiency. By automating various stages of the incident response lifecycle, organizations can significantly reduce the time it takes to identify, analyze, and resolve security incidents.Automation accelerates the incident response lifecycle by automating repetitive, time-consuming tasks.
This allows security teams to focus on more complex and strategic aspects of incident handling, rather than being bogged down in manual processes. Automated systems can perform tasks such as threat detection, log analysis, vulnerability scanning, and system patching much faster than human analysts, leading to quicker identification and resolution of security issues. This speed is crucial in minimizing the impact of breaches, preventing data loss, and reducing overall downtime.
Automated Security Tools for Faster Incident Detection and Resolution
Several automated security tools contribute to faster incident detection and resolution. These tools leverage machine learning, artificial intelligence, and advanced analytics to identify anomalies and potential threats in real-time. Examples include Security Information and Event Management (SIEM) systems, which aggregate and analyze security logs from various sources to identify suspicious activity. Another example is Intrusion Detection and Prevention Systems (IDPS), which monitor network traffic for malicious activity and automatically block or mitigate threats.
Automated vulnerability scanners identify security weaknesses in systems and applications, enabling proactive patching and mitigation. Furthermore, Security Orchestration, Automation, and Response (SOAR) platforms integrate and automate various security tools, creating a more efficient and streamlined incident response process.
Impact of Automation on Minimizing the Impact of Security Breaches
The impact of a security breach can be significantly minimized through automation. Automated systems can rapidly contain breaches by isolating affected systems, preventing further propagation of malware, and limiting access to sensitive data. Automated incident response processes ensure that predefined remediation steps are executed quickly and consistently, reducing the window of vulnerability and minimizing the potential for damage.
For instance, an automated system could immediately quarantine an infected machine upon detection of malicious activity, preventing it from spreading the infection to other systems. Automated forensics tools can rapidly collect and analyze evidence, enabling faster investigation and remediation. The faster the response, the lower the potential financial losses, reputational damage, and legal repercussions.
Automated Incident Response Process Flowchart
The following describes a flowchart illustrating the automated incident response process.Imagine a flowchart with distinct boxes connected by arrows.* Box 1: Security Event Detection: Automated systems (SIEM, IDPS, etc.) detect a suspicious event (e.g., a failed login attempt, unusual network traffic). The arrow points to Box 2.* Box 2: Alert Triage and Analysis: The system analyzes the event to determine its severity and potential impact.
Machine learning algorithms help prioritize alerts based on risk level. The arrow points to Box 3.* Box 3: Incident Confirmation and Containment: If the event is confirmed as a security incident, automated actions are initiated to contain the threat (e.g., isolating infected systems, blocking malicious IP addresses). The arrow points to Box 4.* Box 4: Incident Investigation and Remediation: Automated tools collect forensic data and analyze the root cause of the incident.
Automated remediation steps are executed (e.g., patching vulnerabilities, restoring backups). The arrow points to Box 5.* Box 5: Recovery and Post-Incident Activity: Systems are restored to normal operation, and lessons learned are documented to prevent future incidents. The arrow points to Box 6.* Box 6: Monitoring and Prevention: Continuous monitoring and automated threat hunting are implemented to prevent similar incidents from occurring in the future.This automated process significantly reduces the time required for incident response, minimizing the overall impact of a security breach.
The speed and efficiency provided by automation allow organizations to react swiftly and effectively, protecting their valuable assets and maintaining business continuity.
Enhanced Compliance and Auditing
Automation is a game-changer when it comes to navigating the complex landscape of information security compliance. Manual processes are prone to errors and inconsistencies, making it difficult to consistently meet regulatory requirements. Automation streamlines these processes, significantly reducing the risk of non-compliance and the associated penalties.Automation helps maintain compliance by consistently applying security policies and controls across all systems and data.
This ensures that security standards are consistently met, regardless of the volume of data or the number of systems involved. Automated systems can also generate comprehensive audit trails, providing a clear record of all security-related activities, making investigations easier and more efficient.
Automated Tools for Security Audits and Reporting
Several automated tools simplify the process of conducting security audits and generating reports. Security Information and Event Management (SIEM) systems, for example, collect and analyze security logs from various sources, identifying potential threats and vulnerabilities. These systems can automatically generate reports on security incidents, compliance status, and other relevant metrics. Configuration management databases (CMDBs) provide a centralized repository of information about IT assets, allowing for automated checks against security baselines and standards.
Automating information security tasks is a game-changer, boosting efficiency and reducing human error. This is especially true when building applications, as seen in the exciting developments discussed in this article on domino app dev the low code and pro code future , where streamlined development leads to faster security implementations. Ultimately, faster development cycles mean quicker deployment of security updates and patches, further enhancing overall protection.
Vulnerability scanners automate the process of identifying security weaknesses in systems and applications, and penetration testing tools simulate real-world attacks to assess the effectiveness of security controls. These tools generate detailed reports, facilitating a quicker and more comprehensive audit process.
Automated Log Management and Analysis for Compliance
Automated log management and analysis is critical for compliance. Manually reviewing vast quantities of log data is impractical and error-prone. Automated systems can efficiently collect, parse, and analyze logs from diverse sources, identifying patterns and anomalies that might indicate security breaches or compliance violations. These systems can be configured to trigger alerts based on predefined rules, enabling timely responses to potential issues.
Furthermore, automated log analysis can provide evidence of compliance with regulations, simplifying the audit process and reducing the time and resources required. For instance, an automated system can verify that access controls are properly configured and enforced by continuously monitoring log entries related to user authentication and authorization.
Compliance Standards and Automation
The benefits of automation extend across a wide range of compliance standards. Effective automation strategies can significantly simplify the process of meeting these requirements.
- PCI DSS (Payment Card Industry Data Security Standard): Automation aids in maintaining secure payment card data through automated vulnerability scanning, penetration testing, and access control management. Automated systems can continuously monitor for compliance with PCI DSS requirements, generating alerts for any deviations.
- HIPAA (Health Insurance Portability and Accountability Act): Automation helps ensure the privacy and security of protected health information (PHI) by automating access control, data encryption, and audit logging. Automated systems can continuously monitor for compliance with HIPAA requirements, providing auditable trails of all access to PHI.
- GDPR (General Data Protection Regulation): Automation facilitates compliance with GDPR requirements related to data subject access requests, data breach notifications, and data security. Automated systems can assist with data mapping, consent management, and data subject right fulfillment.
- ISO 27001 (Information Security Management Systems): Automation supports the implementation and maintenance of an ISMS by automating risk assessments, vulnerability management, and incident response. Automated systems can help organizations demonstrate compliance with ISO 27001 requirements through consistent monitoring and reporting.
Final Summary
Ultimately, the benefits of automating information security are clear: increased efficiency, reduced risk, improved compliance, and significant cost savings. It’s no longer a luxury but a necessity for organizations of all sizes. By embracing automation, we’re not just keeping up with the evolving threat landscape; we’re getting ahead of it. So, ditch the manual processes and embrace the future of security – a future powered by automation.
It’s time to transform your security strategy and reap the rewards of a more proactive, efficient, and secure digital environment.
FAQs
What are the biggest challenges in implementing security automation?
The biggest hurdles often include integrating automation tools with existing systems, the need for skilled personnel to manage and maintain these systems, and the initial investment cost.
How can I measure the ROI of security automation?
Track metrics like reduced incident response time, decreased number of security incidents, lower operational costs, and improved compliance audit scores. Compare these before and after automation implementation.
Is security automation suitable for small businesses?
Absolutely! While larger enterprises might use more extensive systems, smaller businesses can benefit from readily available, cost-effective automation tools to address their specific security needs.
What types of security tasks are best suited for automation?
Repetitive tasks like vulnerability scanning, log analysis, patching, and basic threat detection are prime candidates for automation. More complex tasks might require human oversight but can still benefit from partial automation.





