Best Practice Identifying and Mitigating Sunburst Impact
Best practice identifying and mitigating the impact of Sunburst is crucial in today’s threat landscape. This sophisticated supply-chain attack, leveraging compromised software updates, highlights the need for robust security measures. We’ll delve into understanding Sunburst’s mechanics, identifying key indicators of compromise (IOCs), and implementing effective mitigation strategies to protect your systems. From proactive patching to advanced threat detection, we’ll explore a comprehensive approach to neutralize this potent threat.
We’ll cover everything from recognizing suspicious network activity and registry modifications to implementing strong incident response plans. This isn’t just about reacting to an attack; it’s about building a resilient security posture that anticipates and prevents future incidents. Think of it as a layered defense, where each step strengthens your overall security. Get ready to shore up your defenses and learn how to effectively combat Sunburst attacks!
Understanding Sunburst Attacks
Sunburst, a sophisticated and devastating supply-chain attack, highlights the vulnerabilities inherent in relying on third-party software. Understanding its mechanics, entry points, and tools is crucial for bolstering cybersecurity defenses. This exploration delves into the intricacies of Sunburst, providing insights into its modus operandi and real-world impact.
Sunburst Attack Mechanics
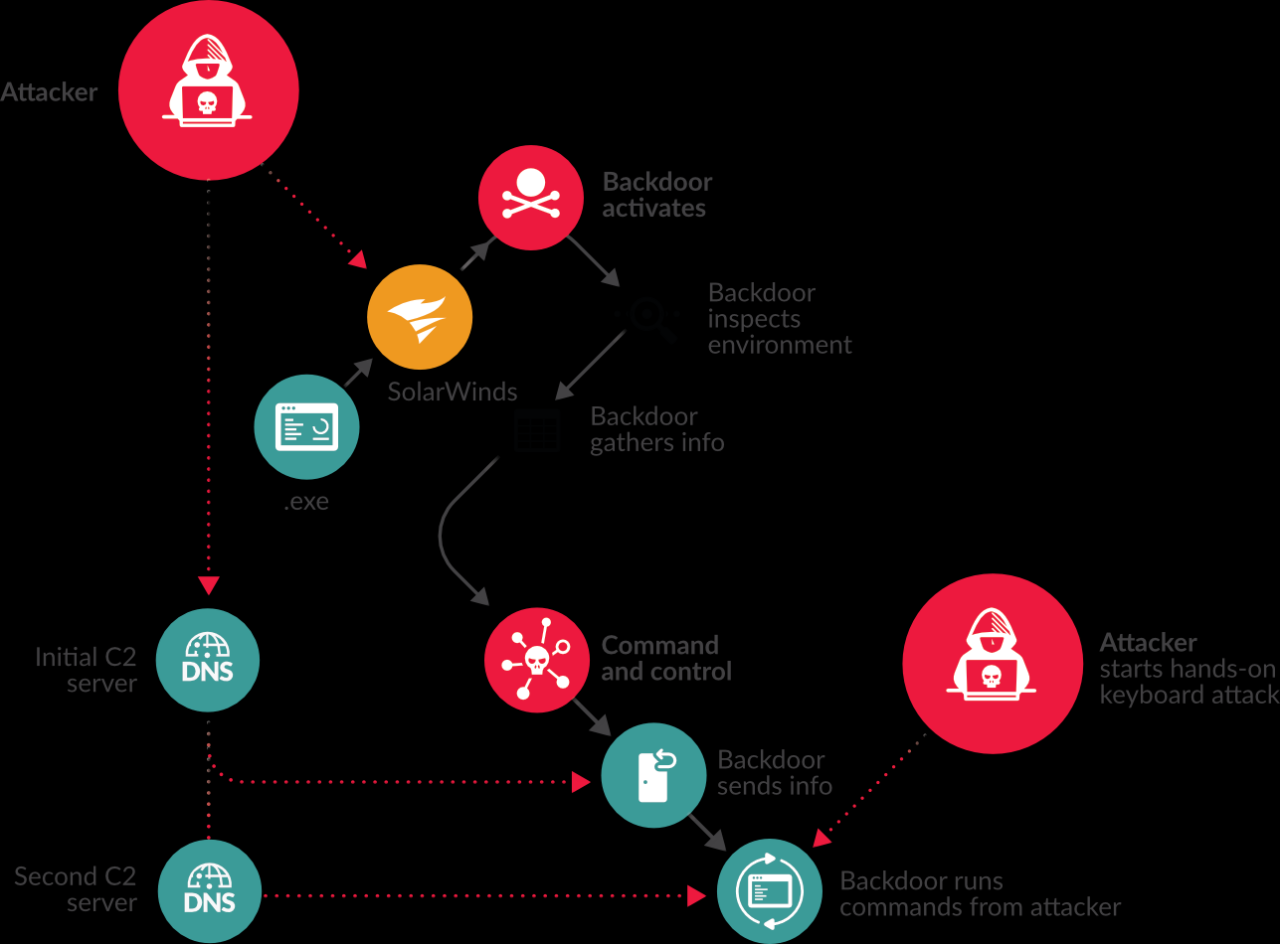
The Sunburst attack leveraged a malicious software update to SolarWinds Orion, a widely used network monitoring platform. Attackers compromised the Orion build process, inserting a backdoor—a piece of malicious code—into legitimate software updates. This backdoor, dubbed Sunburst or Solorigate, allowed attackers to silently infiltrate thousands of SolarWinds customers. The attack proceeded in phases: initial compromise of the SolarWinds build system, insertion of the backdoor into legitimate updates, deployment to SolarWinds customers, and finally, lateral movement within victim networks.
This multi-stage approach ensured stealth and widespread impact.
Sunburst Entry Points
The primary entry point for the Sunburst attack was the SolarWinds Orion software update mechanism. Attackers exploited a vulnerability in the software’s update process, gaining access to the build environment and modifying legitimate software updates. This method is highly effective because it leverages trust; organizations typically assume that updates from trusted vendors are safe. Other entry points, once the initial compromise was achieved, included leveraging compromised accounts and exploiting vulnerabilities within victim networks.
Tools and Techniques Employed in Sunburst
The Sunburst attack employed a range of sophisticated tools and techniques. The backdoor itself was a highly customized piece of malware designed for persistence and stealth. Attackers used techniques like domain fronting to mask their command-and-control (C2) servers, making it harder to detect their activity. Further, they leveraged legitimate tools and protocols to blend in with normal network traffic.
This combination of custom malware and the exploitation of existing infrastructure made the attack particularly difficult to detect. The attackers also used techniques to evade detection by security tools, such as code obfuscation and anti-analysis techniques.
Real-World Sunburst Incidents and Their Impact, Best practice identifying and mitigating the impact of sunburst
The Sunburst attack affected numerous organizations worldwide, including government agencies, technology companies, and critical infrastructure providers. The attack’s widespread nature and the sensitive data compromised had significant geopolitical and economic ramifications. For example, several US government agencies were compromised, leading to concerns about data breaches and potential espionage. The attack also caused significant reputational damage to SolarWinds and its customers.
The financial cost associated with remediation, legal fees, and reputational damage was substantial for affected organizations. The long-term impact included increased cybersecurity awareness and a renewed focus on supply chain security.
Identifying Sunburst Indicators of Compromise (IOCs): Best Practice Identifying And Mitigating The Impact Of Sunburst
Identifying the telltale signs of a Sunburst infection is crucial for timely remediation and preventing further damage. Sunburst, with its sophisticated techniques, leaves behind a subtle trail of digital breadcrumbs that skilled analysts can leverage to detect its presence. This involves understanding the malware’s behavior, its interaction with the system, and the specific artifacts it creates. By focusing on key indicators of compromise (IOCs), organizations can significantly improve their detection capabilities.
Network Traffic Patterns Associated with Sunburst
Sunburst’s activity often manifests in unusual network traffic patterns. The malware establishes connections to command-and-control (C2) servers, often using seemingly benign protocols to evade detection. These connections may be characterized by infrequent, irregular communication, possibly encrypted, and targeting specific IP addresses or domains that are not typically associated with the compromised system’s normal operations. Analyzing network flow data for unusual destinations, especially those hidden behind seemingly legitimate domains, is key to uncovering this activity.
Furthermore, the use of specific ports or protocols not commonly used by the organization should raise suspicion. For example, a sudden increase in HTTPS traffic to an unknown server could indicate a potential compromise. A thorough examination of DNS logs can also reveal suspicious domain lookups that point to C2 infrastructure.
Registry Modifications Indicative of Sunburst
Sunburst, like many other forms of malware, makes modifications to the Windows Registry. These changes are often subtle and designed to persist the infection and maintain access. Specific registry keys associated with scheduled tasks, startup programs, or service configurations might be altered to include malicious entries. Analyzing registry hives for newly created keys, altered values, or unexpected permissions can help identify these modifications.
For instance, the creation of a new scheduled task that runs a suspicious executable or the modification of a legitimate service to point to a malicious binary are strong indicators of compromise. The specific registry keys targeted by Sunburst may vary, but careful examination using tools like RegRipper can reveal these alterations.
Utilizing SIEM Systems for Sunburst IOC Detection
Security Information and Event Management (SIEM) systems play a vital role in identifying Sunburst IOCs. SIEM solutions collect and analyze security logs from various sources, including network devices, servers, and endpoints. By correlating events and applying threat intelligence, SIEMs can identify suspicious patterns indicative of Sunburst’s activity. For example, a SIEM system can be configured to alert on unusual network connections to known malicious IP addresses or domains associated with Sunburst.
Similarly, it can detect unusual registry modifications, such as the creation of new keys or the alteration of existing ones. Effective use of SIEM relies on proper configuration, comprehensive log collection, and the creation of relevant detection rules based on known Sunburst IOCs. The ability to perform real-time threat hunting and correlation of events is crucial for timely detection.
Analyzing System Logs for Suspicious Sunburst Activities
Analyzing system logs from affected machines is crucial for understanding the extent of the compromise and identifying any further malicious activities. This involves reviewing logs from various sources, including the Windows Event Log, security logs, and application logs. Focus should be placed on events related to process creation, network connections, file system modifications, and registry changes. Suspicious activities include the execution of unknown or unusual processes, connections to suspicious IP addresses or domains, the creation or modification of files in unexpected locations, and changes to system configurations.
The use of log analysis tools can aid in the identification of patterns and anomalies that might otherwise go unnoticed. Careful review of these logs, ideally correlated with network traffic data, is crucial for confirming Sunburst infection and identifying the extent of the attack.
Common Sunburst IOCs and Detection Methods
| IOC | Description | Detection Method | Example |
|---|---|---|---|
| Suspicious Network Connections | Connections to known malicious IP addresses or domains associated with Sunburst C2 servers. | Network traffic analysis, SIEM alerts, DNS log review | Outbound connections to an obfuscated domain resolving to a known malicious IP address. |
| Registry Modifications | Changes to registry keys related to scheduled tasks, startup programs, or services. | Registry analysis, SIEM alerts, log review | Creation of a new scheduled task executing a malicious binary. |
| Unusual Process Creation | Execution of processes with unusual names, paths, or parent processes. | Endpoint Detection and Response (EDR) tools, process monitoring, log analysis | A process with a seemingly random name launched from a temporary directory. |
| File System Modifications | Creation or modification of files in unexpected locations, particularly those with suspicious names or extensions. | File integrity monitoring, EDR tools, log analysis | Creation of a new DLL file in the system32 directory. |
Mitigating the Impact of Sunburst
The Sunburst supply chain attack highlighted the critical need for robust security measures beyond traditional endpoint protection. Successfully mitigating the impact of such sophisticated attacks requires a multi-layered approach encompassing proactive prevention, stringent access controls, and a well-defined incident response plan. Ignoring any of these aspects leaves your organization vulnerable to significant damage.
Proactive Measures: Software Updates and Patching
Regular and timely patching is paramount in preventing Sunburst-like attacks. Vulnerabilities exploited by malicious actors are often known and patched by software vendors. Failing to apply these updates creates an open door for attackers. A comprehensive patching strategy should include not only operating systems but also all third-party software, especially those with network access or administrative privileges.
Automated patching systems, combined with rigorous testing in a controlled environment before deployment to production systems, can significantly reduce the risk of exploitation. Prioritization of patches based on criticality and vulnerability scoring is crucial for managing the workload effectively. Regular vulnerability scans and penetration testing can identify and address potential weaknesses before attackers find them.
Securing Remote Access and Controlling Privileged Accounts
Securing remote access points is crucial, especially in today’s increasingly distributed work environment. The use of multi-factor authentication (MFA) for all remote access should be mandatory, significantly reducing the risk of unauthorized access even if credentials are compromised. Implementing strong password policies and regularly rotating passwords for privileged accounts is also vital. Least privilege access controls ensure users only have the permissions necessary to perform their tasks, limiting the potential damage if a system is compromised.
Regular audits of privileged accounts, including monitoring of their activity and access patterns, can help detect suspicious behavior early on. Consider using privileged access management (PAM) solutions to centralize and manage privileged accounts, enhancing control and visibility.
Incident Response for a Sunburst Attack: Containment and Eradication
A well-defined incident response plan is critical for minimizing the impact of a Sunburst-style attack. The first step is immediate containment of the infected systems, isolating them from the network to prevent further lateral movement. This often involves disconnecting the affected machines from the internet and internal network segments. Next, a thorough investigation is needed to determine the extent of the compromise, identifying all affected systems and data.
This involves analyzing logs, network traffic, and system events to understand the attacker’s actions and the data potentially accessed or exfiltrated. Eradication involves removing the malware and restoring systems to a clean state, often through a combination of malware removal tools, system reimaging, and data restoration from backups. Post-incident activity monitoring is crucial to ensure the attacker hasn’t left any backdoors or persistent mechanisms.
Recovering Systems Compromised by Sunburst
System recovery following a Sunburst attack requires a systematic approach. First, verify the integrity of your backups, ensuring they are not compromised. Then, restore systems from known good backups, prioritizing critical systems and data. Once systems are restored, validate their functionality and security posture. This includes verifying the integrity of critical applications and data, patching any vulnerabilities identified during the incident response, and reconfiguring security settings as needed.
Thorough testing of the restored systems is crucial to ensure they are fully functional and secure before bringing them back online. Post-recovery monitoring should continue to detect any lingering malicious activity. A detailed post-incident review should be conducted to identify weaknesses in security posture and implement improvements to prevent future incidents.
Strengthening Network Security Against Sunburst
Sunburst, a sophisticated supply-chain attack, highlights the critical need for robust network security measures. While no single solution guarantees complete protection, a multi-layered approach combining strong network segmentation, advanced security controls, and proactive threat intelligence significantly reduces the risk and impact of such attacks. This section explores practical strategies for strengthening your network’s defenses against Sunburst and similar threats.
Network Segmentation’s Role in Limiting Sunburst’s Impact
Network segmentation divides a network into smaller, isolated segments. If a compromised system resides within one segment, the attacker’s lateral movement is restricted, preventing widespread infection. For instance, isolating critical systems like domain controllers and financial applications into their own highly secured segments limits the damage even if a less critical segment is compromised. This approach minimizes the attack surface and contains the breach, limiting the attacker’s ability to access sensitive data and critical infrastructure.
Effective segmentation requires careful planning and implementation, considering factors like traffic flow, application dependencies, and security requirements for each segment.
Robust Network Security Controls to Prevent Sunburst Attacks
Several robust network security controls can significantly reduce the likelihood of a successful Sunburst-style attack. These include implementing strong authentication mechanisms like multi-factor authentication (MFA) to prevent unauthorized access, regularly patching and updating all software and firmware to address known vulnerabilities, and utilizing advanced threat protection solutions like next-generation firewalls (NGFWs) that leverage advanced threat intelligence to detect and block malicious traffic based on known attack signatures and behaviors.
Intrusion detection and prevention systems (IDPS) are also crucial, providing real-time monitoring and alerting for suspicious activities within the network. Regular security audits and penetration testing help identify and address weaknesses before attackers can exploit them.
Security Architecture Incorporating Threat Intelligence Feeds
A comprehensive security architecture should actively incorporate threat intelligence feeds to proactively detect and respond to Sunburst-like threats. These feeds provide up-to-date information on emerging threats, including indicators of compromise (IOCs), enabling organizations to proactively identify and mitigate risks. Integrating threat intelligence into security information and event management (SIEM) systems allows for correlation of security events with known threats, providing context and facilitating faster incident response.
This proactive approach involves continuously monitoring network traffic and system logs for suspicious activity, comparing them against the threat intelligence data to identify potential compromises early. A well-defined incident response plan is essential to effectively manage and contain any identified breach.
Comparison of Security Solutions for Mitigating Sunburst Attacks
Endpoint Detection and Response (EDR) solutions provide real-time monitoring and analysis of endpoint activity, detecting malicious behavior and providing insights into attacker actions. They are crucial for detecting and responding to post-compromise activity. Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources, correlating events to identify patterns and potential threats. While EDR focuses on endpoint security, SIEM offers a broader view of the entire network security landscape.
The ideal approach often involves integrating both EDR and SIEM to provide a comprehensive security posture. For example, an EDR solution might detect suspicious file execution on an endpoint, while the SIEM system can correlate this event with other suspicious activities across the network, providing a more complete picture of the attack. This combined approach provides greater visibility and enables faster and more effective incident response.
Post-Incident Activities and Lessons Learned
A Sunburst attack, while devastating, presents a crucial opportunity for significant security improvement. A thorough post-incident analysis isn’t just about recovery; it’s about transforming the incident into a catalyst for a stronger, more resilient security posture. Ignoring this phase leaves your organization vulnerable to future attacks, potentially with even more severe consequences.The importance of a comprehensive post-incident analysis lies in its ability to pinpoint the exact vulnerabilities exploited by the attackers.
This goes beyond simply patching the immediate hole; it requires a deep dive into the systems, processes, and human factors that contributed to the breach. Identifying these weaknesses allows for targeted remediation, preventing similar attacks in the future. Failing to conduct a thorough analysis risks repeating the same mistakes, leaving your organization exposed to similar threats.
So, you’re tackling best practice for identifying and mitigating the impact of Sunburst? A robust security strategy is key, and that often involves leveraging modern development approaches. This is where understanding the evolving landscape of domino app dev the low code and pro code future comes in; faster development cycles can help you quickly deploy patches and strengthen your defenses against sophisticated threats like Sunburst.
Ultimately, returning to Sunburst mitigation, remember proactive monitoring and regular updates are paramount.
Post-Incident Activity Checklist
A structured approach to recovery is vital. Rushing the process can lead to incomplete remediation and lingering vulnerabilities. This checklist ensures a comprehensive and methodical response.
- Isolate affected systems: Immediately disconnect compromised systems from the network to prevent further lateral movement of the attacker.
- Secure evidence: Create forensic images of affected systems and network devices before making any changes. This ensures preservation of crucial evidence for investigation and analysis.
- Identify the extent of the breach: Determine which systems and data were accessed or compromised. This might involve analyzing logs, reviewing network traffic, and conducting interviews with affected personnel.
- Restore systems from backups: Use clean backups to restore affected systems to a pre-compromise state, ensuring that the malware is completely removed.
- Patch vulnerabilities: Implement all necessary security patches and updates to address the vulnerabilities exploited by the attackers. This includes both software and firmware updates.
- Review and update security policies: Analyze existing security policies and procedures to identify gaps and weaknesses exposed by the attack. Update these policies to address these shortcomings.
- Conduct employee training: Educate employees on security best practices and the importance of recognizing and reporting suspicious activity. This is crucial to prevent future social engineering attacks.
- Monitor for further activity: Continue to monitor systems and network traffic for any signs of lingering malware or further malicious activity.
Improving Security Posture Based on Lessons Learned
The post-incident analysis should be more than a simple checklist; it should be a catalyst for organizational change. Analyzing the attack’s timeline, techniques, and the vulnerabilities exploited will reveal critical weaknesses in your security architecture.For instance, a Sunburst attack highlights the need for robust endpoint detection and response (EDR) solutions, supply chain security measures, and a strong security information and event management (SIEM) system capable of detecting anomalies in network traffic.
A post-mortem review might reveal a lack of multi-factor authentication (MFA), allowing attackers easier access. The process of improving your security posture should include a thorough reassessment of your access control policies, focusing on the principle of least privilege. This means granting users only the access they need to perform their job duties, minimizing the potential impact of a compromised account.
Developing and Implementing a Comprehensive Incident Response Plan
A well-defined incident response plan is not a luxury; it’s a necessity. This plan should Artikel clear procedures for detecting, responding to, and recovering from security incidents, including those similar to Sunburst. The plan should include:
- Clear roles and responsibilities: Define who is responsible for each stage of the incident response process.
- Communication protocols: Establish clear communication channels for keeping stakeholders informed throughout the incident.
- Escalation procedures: Artikel the process for escalating incidents to higher management as needed.
- Recovery procedures: Detail the steps for restoring systems and data after an incident.
- Regular testing and updates: The plan should be regularly tested and updated to ensure its effectiveness and relevance.
Regular tabletop exercises simulating various attack scenarios, including Sunburst-like attacks, are crucial for testing the plan’s effectiveness and identifying areas for improvement. This proactive approach significantly improves your organization’s preparedness and reduces the impact of future incidents. For example, simulating a compromised software update scenario, similar to Sunburst, allows your team to practice the steps Artikeld in your incident response plan, identifying bottlenecks and refining your procedures before a real incident occurs.
Illustrating Sunburst Attack Vectors
Understanding the mechanics of a Sunburst attack requires visualizing its progression. This involves understanding how the initial compromise leads to widespread lateral movement within a targeted network. The attack doesn’t rely on a single vulnerability but rather leverages a combination of techniques to achieve persistence and data exfiltration.
A typical Sunburst attack vector begins with a compromised software update mechanism. Imagine a legitimate software update server, perhaps for a widely used IT management tool like SolarWinds Orion. The attackers gain access to this server and inject malicious code into the software update package. This malicious code, often a backdoor, is seamlessly integrated into the legitimate software. When unsuspecting users download and install the update, they unknowingly install the malware as well.
Sunburst Attack Stages
The attack unfolds in several key stages. First, the compromised update is downloaded and installed. This initial infection establishes a foothold within the victim’s system. Second, the malware establishes persistence, meaning it ensures it remains active even after a system reboot. This is often achieved through registry entries or scheduled tasks.
Third, the malware begins its lateral movement, spreading throughout the network by exploiting internal vulnerabilities and leveraging existing network access credentials. This phase often involves the exploitation of weak passwords, default credentials, or vulnerabilities in other software within the network. Finally, the attackers exfiltrate data, either stealing sensitive information directly or establishing a command-and-control server for remote access and control.
Scenario: Sunburst Attack Propagation
Let’s envision a scenario where a large corporation, Acme Corp, uses SolarWinds Orion. Acme Corp downloads and installs the compromised Orion update. The malicious code silently installs itself, remaining undetected. The malware then leverages the Orion platform’s network access to map the internal network infrastructure, identifying high-value targets like financial databases or sensitive employee data. It exploits known vulnerabilities in other systems to gain access, spreading like wildfire.
It might exploit a weakness in a legacy application server or use stolen credentials to access other accounts with elevated privileges. The malware then establishes a covert communication channel back to a command-and-control server controlled by the attackers, allowing them to remotely access and control the compromised systems. The attackers can then download sensitive data, potentially exfiltrating intellectual property, financial records, or customer data, depending on their objectives.
This exfiltration could happen over extended periods, making detection difficult. The attackers might also use the compromised systems to launch further attacks against other organizations.
Epilogue
Successfully mitigating the impact of a Sunburst attack requires a multi-faceted approach that combines proactive security measures with a robust incident response plan. By understanding the attack vectors, identifying key IOCs, and implementing strong security controls, organizations can significantly reduce their vulnerability. Remember, vigilance and continuous improvement are key to staying ahead of evolving threats like Sunburst. Don’t wait for an attack – proactively strengthen your security posture today!
FAQ Corner
What is the difference between EDR and SIEM?
Endpoint Detection and Response (EDR) focuses on individual endpoints (computers, servers) to detect and respond to threats. Security Information and Event Management (SIEM) collects and analyzes security logs from various sources across the network to identify broader threats and security breaches.
How can I tell if my organization has been affected by Sunburst?
Look for unusual network traffic, registry modifications, and suspicious processes. Consult your security logs and consider using threat intelligence feeds to identify known Sunburst IOCs. Professional security assessments can also help.
What’s the role of threat intelligence in Sunburst mitigation?
Threat intelligence provides crucial information about the latest attack techniques, IOCs, and tactics used by attackers. By subscribing to reputable threat intelligence feeds, organizations can proactively identify and mitigate potential Sunburst attacks before they occur.





