Best Practices for Securing Azure Compute 2
Best practices for securing Azure compute 2 cover a wide range of crucial strategies, from fundamental security principles to advanced incident response techniques. This comprehensive guide explores the critical aspects of securing Azure virtual machines, app services, and functions, ensuring robust protection against potential threats. We’ll delve into network security, identity and access management, data security, vulnerability management, monitoring, and incident response.
Understanding the unique security requirements for each Azure compute service is paramount. The document provides actionable steps and practical examples, empowering readers to implement effective security measures within their own Azure environments. The detailed comparison tables and practical advice help you quickly identify and address potential vulnerabilities.
Security Fundamentals for Azure Compute 2
Azure compute services are critical for modern applications, but their security is paramount. Protecting these resources from threats is essential for maintaining data integrity, availability, and compliance. This exploration delves into the core security principles for Azure compute, common vulnerabilities, and best practices for securing various Azure compute services.Core security principles for Azure compute resources revolve around a layered approach, encompassing network security, identity management, and data protection.
This multifaceted strategy mitigates potential risks and enhances the overall security posture. Adhering to industry best practices and proactively addressing vulnerabilities are key components of a robust security framework.
Core Security Principles
Azure compute security is built upon several fundamental principles. These include the principle of least privilege, ensuring that users and applications only have the necessary permissions to perform their tasks, and role-based access control (RBAC), which grants granular control over access to resources. Implementing strong access controls is crucial to minimize the impact of a security breach.
Common Security Threats and Vulnerabilities
Azure compute services face various threats, including malicious actors attempting unauthorized access, denial-of-service attacks, and vulnerabilities in software components. Malicious code injection, weak passwords, and insecure configurations are common avenues for attackers. Understanding these threats is critical to developing appropriate mitigation strategies.
Least Privilege Access and RBAC
Least privilege access and role-based access control (RBAC) are fundamental to secure Azure compute resources. Limiting access to only the necessary permissions significantly reduces the potential damage from a compromised account. RBAC enables fine-grained control over resource access, making it easy to enforce least privilege policies and audit actions.
Securing Azure Virtual Machines (VMs) at the Operating System Level
Securing Azure VMs at the operating system level involves a multi-faceted approach. Regular patching of operating systems and applications is crucial. Using strong passwords and multi-factor authentication (MFA) enhances account security. Employing intrusion detection and prevention systems (IDS/IPS) and firewalls at the operating system level can detect and block malicious activity. Implementing appropriate security configurations on the VMs is also essential.
Securing Virtual Network Configurations
Secure virtual network configurations are vital for isolating Azure compute resources and preventing unauthorized access. Implementing network segmentation, using virtual networks and subnets to isolate resources, and applying network security groups (NSGs) to control traffic flow are key strategies. Network security groups (NSGs) are critical in filtering inbound and outbound traffic to VMs.
Comparison of Azure Compute Services
| Compute Service | Inherent Security Features |
|---|---|
| Virtual Machines (VMs) | High level of customization and control. Offers flexibility in configuring security features. |
| App Services | Built-in security features such as authentication and authorization. Prevents direct access to underlying infrastructure. |
| Functions | Designed with security in mind, limiting access to the code. Handles authentication and authorization automatically. |
Network Security Best Practices
Azure Virtual Machines (VMs) are frequently targeted by malicious actors, making robust network security crucial. Effective network configurations are the cornerstone of securing Azure compute resources, and these best practices provide a framework for achieving that goal. Proper implementation minimizes risks, ensuring the integrity and availability of your applications and data.Network security encompasses a broad spectrum of measures, from configuring virtual networks and subnets to implementing network security groups (NSGs) and securing communication paths.
By understanding and applying these best practices, organizations can significantly reduce vulnerabilities and enhance the overall security posture of their Azure deployments.
Secure Network Configurations for Azure VMs
Virtual networks (VNETs) are fundamental to isolating and segmenting Azure resources. Creating a well-defined VNET structure ensures that traffic is confined to authorized paths, limiting the impact of potential breaches. Subnets further refine this segmentation, logically grouping VMs with similar functions or security requirements. Proper subnet design is essential for granular control over network access. Network security groups (NSGs) are critical for enforcing access control rules at the network level.
They provide a granular mechanism for filtering inbound and outbound traffic based on source/destination IP addresses, ports, and protocols. Comprehensive NSG configurations are vital for preventing unauthorized access to VMs.
Network Traffic Filtering with NSGs
Network Security Groups (NSGs) are the primary mechanism for controlling network traffic. NSG rules define permitted and prohibited traffic flows. For instance, a rule could allow inbound traffic only from specific IP addresses or a Virtual Private Cloud (VPC). Rules can also be defined based on destination ports, such as allowing only SSH (port 22) traffic to a specific VM.
Outbound rules can prevent unauthorized data exfiltration or unwanted internet connections. Effective implementation involves carefully crafted rules that balance security with application functionality.
Azure Network Security Solutions
Azure offers various network security solutions beyond NSGs. Azure Firewall is a dedicated firewall service for protecting entire virtual networks. It can inspect and filter traffic at the gateway level, providing a strong first line of defense. Azure Bastion is a secure jump server that enables secure remote access to VMs without exposing them directly to the public internet.
This significantly reduces the attack surface. Point-to-site VPNs allow secure connections from on-premises devices to Azure resources, while Site-to-Site VPNs facilitate secure communication between on-premises networks and Azure. Each solution has specific use cases and advantages, and the optimal choice depends on the specific security needs and deployment architecture.
Securing Communication Between Azure Compute Resources and External Networks
Secure communication between Azure compute resources and external networks is paramount. Use VPNs (Virtual Private Networks) to encrypt traffic between on-premises networks and Azure. Ensure proper configuration of VPN gateways and connections to ensure secure communication channels. Implement secure protocols (like HTTPS) for external communication to protect data in transit. Use Azure Load Balancers to distribute traffic and manage access from external networks.
Secure Network Segmentation Strategies
Network segmentation is a critical security strategy. It isolates different parts of your network, limiting the impact of a breach. By creating separate subnets for different teams or applications, you reduce the potential for lateral movement by attackers. This isolates vulnerabilities, ensuring that if one part of the network is compromised, the rest remains unaffected.
Azure Network Security Best Practices Table, Best practices for securing azure compute 2
| Best Practice | Description | Example |
|---|---|---|
| Virtual Network Segmentation | Divide resources into logical groups (subnets) based on function or security requirements. | Create separate subnets for development, staging, and production environments. |
| Network Security Groups (NSGs) | Control inbound and outbound traffic using rules based on source/destination, ports, and protocols. | Allow SSH traffic (port 22) only from specific IP addresses to a web server VM. |
| Azure Firewall | Gateway-level firewall for protecting entire virtual networks. | Use Azure Firewall to block all inbound traffic except for specific application ports. |
| Azure Bastion | Secure jump server for remote access to VMs. | Use Azure Bastion for SSH access to VMs, reducing the attack surface. |
Identity and Access Management (IAM) Strategies: Best Practices For Securing Azure Compute 2
Securing access to your Azure compute resources is paramount. Effective Identity and Access Management (IAM) is crucial for controlling who can interact with your virtual machines, storage, and other resources. This strategy establishes a strong defense against unauthorized access and ensures compliance with security best practices. Properly implemented IAM ensures only authorized personnel can perform specific actions on your Azure infrastructure.Azure Active Directory (Azure AD) and Role-Based Access Control (RBAC) are the cornerstones of a robust IAM strategy in Azure.
They provide a granular level of control over access to resources, allowing you to define specific permissions for different users and roles. This fine-grained control minimizes the potential impact of a security breach and ensures accountability for actions within your Azure environment.
Securing Access to Azure Compute Resources
Azure Active Directory (Azure AD) acts as the central identity provider for your Azure resources. By leveraging Azure AD, you can manage user accounts, group memberships, and authentication methods for all your Azure services, including compute resources. Role-Based Access Control (RBAC) allows you to assign specific roles to users and groups, granting them only the permissions needed to perform their tasks.
This minimizes the attack surface and ensures that only authorized individuals can access and manage your Azure compute resources.
Managing User Accounts and Permissions
Careful management of user accounts and permissions is critical for maintaining security. Implement strong password policies and enforce regular password changes. Use strong passwords with a combination of upper and lowercase letters, numbers, and special characters. Regularly review and revoke access for employees who leave the organization or whose roles change.
Implementing Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security to your Azure environment. By requiring users to provide multiple verification methods (e.g., password, code from a mobile app, security key), MFA significantly reduces the risk of unauthorized access even if a password is compromised. Implement MFA for all user accounts, including service accounts, to safeguard your Azure resources.
Managing and Auditing Access to Azure Compute Resources
Regularly monitor and audit access to your Azure compute resources. Use Azure Monitor logs to track user activities and identify any suspicious patterns. Review access logs regularly and investigate any unusual or unexpected access attempts. This proactive approach to monitoring ensures you can detect and respond to potential security threats promptly. Regularly review and update your access policies to ensure they align with your current security needs.
Azure AD Roles and Permissions
The following table Artikels different Azure AD roles and their associated permissions for managing Azure compute resources:
| Role | Permissions |
|---|---|
| Owner | Full access to all Azure resources, including compute resources. |
| Contributor | Extensive permissions for managing resources, including compute resources. |
| Reader | Limited permissions to view resources, including compute resources. |
| Virtual Machine Contributor | Specific permissions related to managing virtual machines, including adding, deleting, and configuring them. |
| Virtual Machine Operator | Permissions for operating virtual machines, such as starting, stopping, and restarting them. |
Data Security and Encryption
Protecting sensitive data within Azure compute resources is paramount. Robust encryption strategies for data at rest and in transit, coupled with secure storage options and proactive data loss prevention (DLP) measures, are crucial for maintaining confidentiality and integrity. This section details best practices for securing sensitive data within Azure VMs, compares and contrasts different encryption methods, and provides a comprehensive overview of secure storage options.Data encryption, both at rest and in transit, is a cornerstone of data security in the cloud.
Properly implemented, these techniques ensure that data remains confidential and inaccessible to unauthorized parties, even if the storage or transmission channels are compromised. Implementing strong encryption is essential to protect against data breaches and ensure compliance with industry regulations.
Data Encryption Strategies
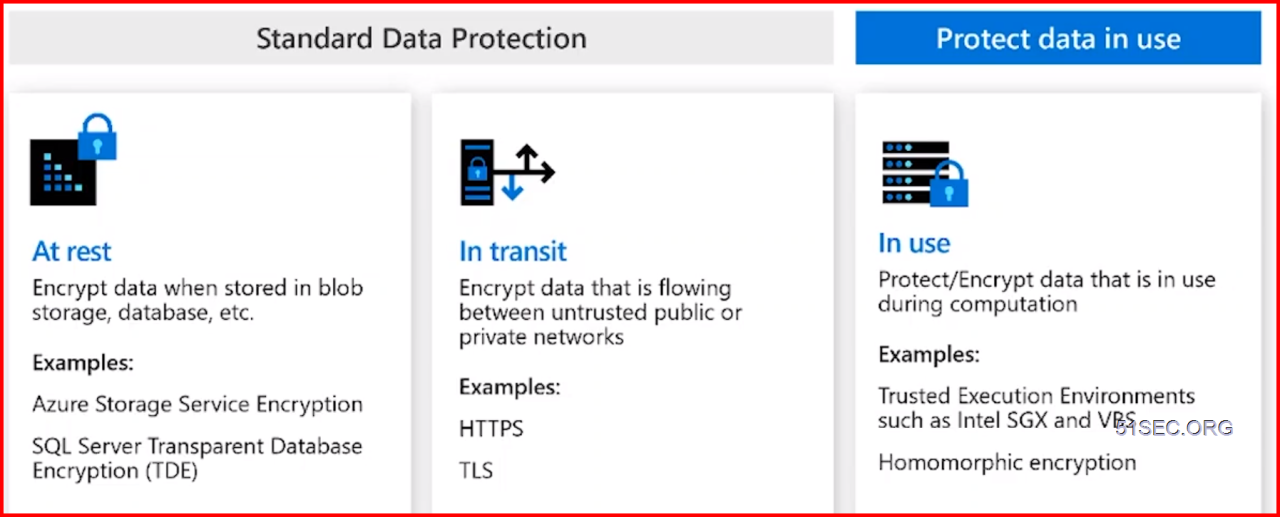
Data encryption safeguards data confidentiality by converting readable data into an unreadable format. This process requires a key for decryption, which should be securely managed and protected. There are two primary types of data encryption: data at rest and data in transit.
- Data at Rest Encryption: This refers to encrypting data stored in Azure storage accounts, databases, or other data repositories. Azure provides various encryption options for data at rest, including encryption at the storage level and encryption for specific database systems. This approach protects data even if unauthorized access is gained to the storage system.
- Data in Transit Encryption: This involves encrypting data during transmission between different systems or locations. Transport Layer Security (TLS) is a common method for encrypting data in transit, ensuring secure communication between clients and Azure services. Using HTTPS for all communication channels is a vital practice to protect sensitive data during transmission.
Secure Storage Options for Sensitive Data
Azure offers a variety of storage services. Choosing the appropriate storage option for sensitive data requires careful consideration of security needs and compliance requirements. The selection should factor in data access policies, encryption capabilities, and auditing mechanisms.
- Azure Disk Encryption: This service encrypts virtual machine disks at rest, providing an extra layer of protection for data stored on VMs. It is crucial to leverage Azure Disk Encryption to protect sensitive data on VMs.
- Azure Key Vault: This service is a secure vault for managing encryption keys. Storing encryption keys in Key Vault ensures that they are protected from unauthorized access and use.
- Azure Storage Encryption: Different Azure storage services offer encryption capabilities. Using appropriate encryption for storage tiers protects data stored within Azure storage services. The choice depends on the type of data being stored and the required level of security.
Data Loss Prevention (DLP) Measures
Data Loss Prevention (DLP) measures are critical to prevent sensitive data from leaving the organization’s control. These measures can involve policies, tools, and technologies designed to identify and block sensitive data from unauthorized access or transfer.
- Access Control Policies: Implement strict access control policies to restrict access to sensitive data based on user roles and permissions. This helps minimize the risk of unauthorized data exposure.
- Data Classification: Categorize data based on sensitivity to implement appropriate security measures. Proper data classification is the foundation of effective DLP policies.
- Monitoring and Auditing: Implement monitoring and auditing mechanisms to track data access and usage patterns. Monitoring helps to identify suspicious activity and prevent data breaches.
Securing Sensitive Data Within Azure VMs
Securing sensitive data within Azure VMs involves a multi-faceted approach encompassing encryption, access control, and monitoring. Protecting sensitive data within Azure VMs involves careful planning and implementation of appropriate security measures.
- Secure Configuration: Configure Azure VMs with strong passwords and use principle of least privilege to limit access to sensitive data.
- Regular Updates: Keep all VM software and operating systems updated to patch security vulnerabilities. Timely updates are essential for maintaining VM security.
- Network Segmentation: Segment networks to isolate sensitive VMs from other resources. Network segmentation limits potential impact of security breaches.
Comparison of Data Encryption Methods in Azure
Azure offers several encryption methods, each with its own strengths and weaknesses. The choice of method depends on the specific security needs and use case.
- Customer-managed encryption keys (CMEK): Allows customers to control and manage their encryption keys, providing greater control over data security. CMEK provides greater control over data security.
- Azure-managed encryption keys (MAK): Azure manages the encryption keys, simplifying key management for users. MAK simplifies key management, but users have less control over the keys.
Data Encryption Options for Different Data Types
The choice of encryption method should be tailored to the sensitivity and type of data.
| Data Type | Encryption Method (Example) | Description |
|---|---|---|
| Customer PII | Azure Disk Encryption with CMEK | Provides strong encryption for sensitive customer data at rest. |
| Financial Transactions | Azure Database Encryption | Ensures security of financial data within Azure databases. |
| Application Logs | Azure Storage Encryption | Provides encryption for application logs stored in Azure storage. |
Vulnerability Management and Patching
Staying ahead of cyber threats requires proactive vulnerability management and patching strategies for Azure compute resources. Ignoring vulnerabilities can lead to significant security breaches, exposing sensitive data and impacting operational efficiency. A robust approach involves continuous monitoring, automated patching, and a deep understanding of common threats.Regular vulnerability scanning and patching are critical components of a strong security posture.
Automated systems, coupled with human oversight, provide a layered approach that minimizes risk while allowing for efficient resource allocation. This proactive approach is far more effective than reactive measures following a breach.
While best practices for securing Azure compute 2 are crucial, understanding vulnerabilities in related services like Azure Cosmos DB is equally important. For example, recent security concerns surrounding Azure Cosmos DB have highlighted potential weaknesses in data storage security, which should be considered alongside standard compute security practices. To learn more about these specific vulnerabilities, check out the details at Azure Cosmos DB Vulnerability Details.
Ultimately, a comprehensive approach to securing Azure compute 2 involves considering the entire ecosystem, not just the compute instances themselves.
Regular Vulnerability Scanning and Patching Procedures
A proactive approach to vulnerability management involves regularly scanning Azure compute resources for known vulnerabilities. These scans should be scheduled and automated, ideally on a weekly or even daily basis. Tools and services are available to automate the scanning process and provide detailed reports. The reports should be analyzed for critical vulnerabilities, and remediation steps should be prioritized based on the severity and potential impact.
Best practices for securing Azure compute 2 involve robust network configurations and access controls. Crucially, understanding the potential vulnerabilities in your AI code is just as important, like those covered in the article Deploying AI Code Safety Goggles Needed. Ultimately, incorporating these proactive security measures will significantly bolster the overall security posture of your Azure compute environment.
Patching should be applied promptly and securely to all identified vulnerabilities, following a defined patching schedule and procedure. This ensures consistent compliance with security best practices and reduces the window of opportunity for attackers.
Automating Patching and Security Updates
Automating patching and security updates is crucial for maintaining a secure Azure environment. This reduces the risk of human error, ensures timely updates, and allows for scalability. Azure offers various tools and features to streamline the process, such as Azure Automation, which can be configured to automatically apply updates to virtual machines (VMs) and other compute resources. Configuration management tools can be integrated into the workflow to ensure consistent security settings across the environment.
Furthermore, the automation process should include validation steps to verify that the updates have been applied successfully without introducing unforeseen conflicts or performance issues.
Common Vulnerabilities in Azure Compute Environments
Common vulnerabilities in Azure compute environments include misconfigurations of security settings, outdated software, and weak credentials. These vulnerabilities are often exploited by attackers to gain unauthorized access or execute malicious code. Outdated operating systems and applications are particularly vulnerable to known exploits, highlighting the importance of regular patching. Insecure default configurations also represent a significant risk. By understanding these common pitfalls, organizations can proactively address them to mitigate the potential for exploitation.
Threat Intelligence Integration
Integrating threat intelligence into vulnerability management is vital for staying ahead of emerging threats. Threat intelligence feeds provide information about current and evolving threats, enabling organizations to prioritize patching efforts and enhance their security posture. By analyzing threat intelligence, organizations can identify vulnerabilities that are currently being exploited and adapt their patching strategies to address these emerging threats.
This proactive approach minimizes the risk of falling victim to sophisticated attacks.
Methods for Monitoring and Detecting Security Incidents
Monitoring and detecting security incidents is crucial for responding to threats effectively. This requires a robust security information and event management (SIEM) solution to collect and analyze logs from Azure resources and applications. By implementing intrusion detection systems (IDS), organizations can monitor for malicious activities and respond quickly to potential threats. Security information and event management (SIEM) solutions are key to aggregating and analyzing security logs from various sources, providing a comprehensive view of the security posture.
Real-time monitoring and alerts are critical for timely incident response.
Vulnerability Scanning Tools
| Tool | Features | Strengths | Weaknesses |
|---|---|---|---|
| Azure Security Center | Vulnerability scanning, threat detection, and security recommendations | Built-in, comprehensive features, integration with Azure services | Limited customization compared to third-party tools |
| Nessus | Wide range of scans, including vulnerability scanning, configuration audits, and compliance checks | Extensive scanning capabilities, detailed reports | Can be complex to deploy and manage |
| OpenVAS | Open-source vulnerability scanner, with a wide range of plugins | Cost-effective, flexible, and customizable | Requires more technical expertise to configure |
| Qualys | Comprehensive vulnerability management platform, offering a wide range of services including vulnerability scanning, risk management, and compliance | Extensive features, comprehensive reporting | More expensive than some open-source alternatives |
This table provides a brief overview of popular vulnerability scanning tools. Each tool has its own strengths and weaknesses, so the best choice depends on the specific needs and resources of the organization.
Monitoring and Logging
Keeping a watchful eye on your Azure compute resources is crucial for proactively identifying and addressing potential security issues. Robust monitoring and logging systems are essential for detecting anomalies, suspicious activities, and breaches in real-time. This proactive approach allows you to respond swiftly to incidents, minimizing the impact and damage.Comprehensive logging and alerting systems provide a detailed record of events occurring within your Azure environment.
This data allows for the analysis of patterns, identification of potential threats, and the implementation of preventive measures. By understanding the flow of events, you can better anticipate and mitigate security risks.
Importance of Security Monitoring and Logging
Effective monitoring and logging are critical for detecting and responding to security incidents. They provide a detailed record of events, enabling security teams to identify suspicious activities and take appropriate action. By correlating logs from various sources, security teams can build a comprehensive picture of events, leading to faster incident response and improved security posture.
Implementing Comprehensive Logging and Alerting Systems
Implementing a robust logging and alerting system requires careful consideration of various factors. The first step involves choosing the right logging solutions for your Azure environment. Azure Monitor is a powerful platform for collecting and analyzing logs from various sources. Integration with other Azure services enhances visibility and allows for a holistic view of your security posture.
Alerting systems should be configured to trigger notifications for specific events, such as unauthorized access attempts or unusual resource usage. These alerts can be sent to security teams, allowing them to investigate and respond promptly.
Using Azure Monitor for Security Monitoring
Azure Monitor provides a central platform for collecting and analyzing logs from various Azure resources. Its powerful query language enables the construction of complex queries to identify specific events. This centralized approach enhances visibility and allows for correlation of events across different services. By leveraging Azure Monitor, security teams can gain a holistic understanding of the security posture of their Azure environment.
Creating Custom Alerts for Security Events
Custom alerts allow you to proactively monitor for specific security events. These alerts can be triggered by various factors, such as specific log entries or deviations from expected resource usage patterns. By configuring alerts based on your specific security needs, you can receive notifications for critical events, allowing for faster incident response. For instance, an alert could be triggered when a user attempts to access a resource outside of their authorized permissions.
Analyzing Security Logs for Identifying Potential Threats
Analyzing security logs is a crucial aspect of threat identification. Security teams should regularly review logs for patterns, anomalies, and suspicious activities. This involves using log analysis tools to identify and investigate potential threats. By leveraging log correlation techniques, security teams can identify the root cause of events and implement appropriate countermeasures. For instance, a sudden increase in failed login attempts from a specific IP address may indicate a brute-force attack.
Talking about best practices for securing Azure Compute 2, it’s crucial to consider the broader security landscape. For example, recent news like the Department of Justice Offers Safe Harbor for MA Transactions ( Department of Justice Offers Safe Harbor for MA Transactions ) highlights the importance of staying informed about evolving legal and regulatory frameworks. Ultimately, understanding these contexts helps in developing robust security measures for Azure Compute 2 deployments.
Azure Monitoring Tools and Functionalities
| Monitoring Tool | Functionality |
|---|---|
| Azure Monitor Logs | Collects and stores logs from various Azure resources. Provides a powerful query language for searching and analyzing logs. |
| Azure Monitor Metrics | Tracks performance metrics and resource utilization. Allows for the creation of dashboards and alerts based on metrics. |
| Azure Security Center | Provides a central security management platform. Includes threat detection, vulnerability management, and compliance monitoring. |
| Azure Sentinel | Provides a threat intelligence and security information and event management (SIEM) solution. Offers advanced threat hunting and investigation capabilities. |
Incident Response and Disaster Recovery
Securing Azure compute environments requires robust incident response and disaster recovery strategies. Effective planning for these scenarios can mitigate damage, minimize downtime, and ensure business continuity. This section details crucial steps for handling security incidents and safeguarding against disruptions.
Incident Response Strategies
Responding to security incidents in Azure requires a well-defined and practiced incident response plan. This plan should Artikel procedures for identifying, containing, eradicating, recovering, and learning from incidents. Critical steps include promptly isolating compromised resources, escalating issues to the appropriate teams, and diligently documenting all actions.
Incident Containment Procedures
Containment is a crucial step in incident response. Quickly isolating compromised resources prevents further damage and allows for focused remediation efforts. This involves identifying and blocking access to affected systems and data, while maintaining audit trails. The specific containment methods will vary based on the nature of the incident, but the goal is to minimize the scope of the impact.
A critical aspect is to ensure that containment does not hinder legitimate operations.
Implementation of Incident Response Plans
Implementing a robust incident response plan requires careful planning and regular testing. This includes establishing clear roles and responsibilities for each team member, outlining communication protocols, and defining procedures for data preservation and analysis. The plan should be reviewed and updated regularly to reflect evolving threats and technologies.
Disaster Recovery Strategies for Azure Compute Resources
Azure offers a range of disaster recovery strategies for compute resources, ensuring business continuity in case of outages. These strategies encompass various replication and failover mechanisms to ensure minimal downtime. Key considerations include the level of data protection required and the acceptable recovery time objective (RTO).
Azure Compute Resource Configurations for High Availability
Several Azure compute resource configurations facilitate high availability. For example, using Azure Availability Zones ensures that your resources are distributed across multiple physical locations, minimizing the impact of single points of failure. Implementing Azure Load Balancing distributes traffic across multiple instances of your application, ensuring high availability and performance. Automated scaling features help adjust resource capacity based on demand.
Using Azure Virtual Machines in a highly available configuration ensures high availability and fault tolerance, while using Azure Kubernetes Service (AKS) can further increase the reliability and scalability of your applications.
Azure Disaster Recovery Options and Costs
| Disaster Recovery Option | Description | Estimated Cost (USD/Month) |
|---|---|---|
| Geo-redundant storage | Replicates data across different regions, offering fast recovery options. | $0.01 – $0.10/GB/Month |
| Azure Site Recovery | Provides comprehensive disaster recovery capabilities for virtual machines and applications. | $0.02 – $0.50/VM/Hour |
| Azure Backup | Provides backup and recovery options for data and applications. | Variable, based on storage needs. |
| Azure Virtual Machines in multiple availability zones | Ensures high availability by distributing virtual machines across different physical locations. | Variable, based on VM size and configuration. |
Note: Costs are estimates and can vary based on specific configurations and usage. It is highly recommended to consult Microsoft Azure pricing for the most accurate and up-to-date cost information.
Summary
In conclusion, securing Azure compute resources demands a multi-faceted approach, encompassing various layers of security. By meticulously following the best practices Artikeld in this guide, organizations can significantly enhance the security posture of their Azure deployments. Remember that proactive security measures are key to maintaining a robust and resilient cloud infrastructure. Regular audits, vulnerability assessments, and continuous monitoring are essential for long-term success.
Essential Questionnaire
What are some common security threats targeting Azure compute services?
Common threats include unauthorized access, malicious code injection, denial-of-service attacks, and data breaches. Proper configuration and strong security practices mitigate these risks.
How can I automate patching and security updates for Azure VMs?
Azure provides automation tools and scripts to streamline patching and security updates. Leveraging these tools is crucial for maintaining a secure environment.
What is the importance of data loss prevention (DLP) measures in Azure?
DLP measures help prevent sensitive data from leaving the organization’s control, protecting it from unauthorized access and misuse. Proper implementation of DLP policies within Azure is essential.
What are the different types of Azure network security solutions?
Azure offers various network security solutions, including virtual networks, subnets, network security groups (NSGs), and Azure Firewall. Choosing the appropriate solution depends on the specific security needs.