Beware of This Malicious Android System Update
Beware of this malicious Android system update! Have you ever received a system update notification that felt…off? Maybe the wording was slightly awkward, the download link looked suspicious, or it asked for permissions that seemed excessive? This post dives deep into the world of fraudulent Android updates, revealing how to spot them, avoid them, and what to do if you suspect you’ve already fallen victim.
We’ll explore the sneaky tactics used by malicious actors and arm you with the knowledge to keep your data safe.
From understanding the characteristics of a fake update to learning how to verify its authenticity, we’ll cover everything you need to know to protect your Android device. We’ll look at real-world examples of the damage these updates can cause and provide practical steps to take if you encounter a suspicious update. Think of this as your ultimate guide to navigating the sometimes-dangerous world of Android system updates.
Identifying the Malicious Update: Beware Of This Malicious Android System Update
Spotting a fake Android system update can be tricky, but understanding the telltale signs can save you from a world of malware. These malicious updates often mimic legitimate ones, making it crucial to know how to differentiate them. This will help you protect your device and personal data from potential harm.
Fraudulent Android system updates share several characteristics that set them apart from legitimate ones. They often appear unexpectedly, lacking the usual notification style from the official Android operating system or your device manufacturer. The update might also promise unrealistic improvements or fixes, such as dramatically increased battery life or significantly boosted performance, raising immediate red flags. Additionally, the download source might be suspicious, leading to a download from an unfamiliar website or app store instead of the official channels.
Methods Used to Disguise Malicious Updates
Malicious actors employ various methods to make their fraudulent updates seem genuine. These deceptive tactics often exploit user trust and lack of awareness. They might use convincing branding, mimicking the official logos and styling of legitimate sources. The update notification itself may appear almost identical to a real system update, complete with progress bars and seemingly official language.
Furthermore, they might leverage social engineering techniques, creating a sense of urgency or fear to push users towards downloading and installing the malicious update.
Distinguishing Legitimate and Fraudulent Updates
The key to identifying a fake update lies in careful observation and verification. Always check the source of the update notification. Legitimate updates typically come directly from Google or your device manufacturer through the official system settings. Avoid clicking on links from unknown sources or emails. Scrutinize the update’s description carefully.
Beware of exaggerated claims or promises of unrealistic improvements. Pay close attention to the permissions requested during installation. A legitimate system update rarely requires access to sensitive data or unusual permissions.
Examples of Deceptive Update Notifications
Imagine receiving a notification claiming a critical system update is needed to fix a security vulnerability, but the notification is poorly written, contains grammatical errors, or links to an unfamiliar website. This is a clear sign of a potential scam. Another example could be an update notification promising a massive performance boost that sounds too good to be true. A pop-up claiming your device is infected and requiring an immediate update from an unknown source should be treated with extreme caution.
Comparison of Legitimate and Malicious Update Sources
| Source | Notification Style | Download Link Appearance | Permissions Requested |
|---|---|---|---|
| Google Play Store/Official Device Manufacturer Website | Consistent with official branding; clear and concise language; often includes version number | Secure HTTPS link; clearly identifies the source | Standard system permissions; nothing excessive or unusual |
| Suspicious Website/Third-party App Store | Poorly designed; grammatical errors; uses urgent or fear-inducing language | Unsecured HTTP link; unclear or suspicious source | Excessive permissions; access to sensitive data (contacts, location, etc.) |
Understanding the Risks
Installing a malicious Android system update can have severe consequences, potentially leading to significant data loss and financial harm. It’s crucial to understand the potential threats before blindly accepting any update, especially those from untrusted sources or those that deviate from the official update process. The risks extend far beyond a simple system crash; they encompass the compromise of sensitive personal information and the potential for your device to be used for malicious activities.The potential consequences of installing a malicious update are far-reaching and can significantly impact your digital life and even your financial security.
A compromised device can be used for various malicious purposes, ranging from identity theft to financial fraud. The level of risk depends on the specific malware embedded within the update and the level of access it gains to your system.
Types of Compromised Data
Malicious updates can target a wide range of personal data. This includes everything from your contact list and photos to your banking details, passwords, and location data. The update might be designed to steal specific types of data, depending on the attackers’ motives. For instance, a financially motivated attacker might focus on stealing banking credentials, while a stalker might prioritize location data and contact information.
The more sensitive the information stored on your device, the greater the potential for harm.
Methods of Data Access, Beware of this malicious android system update
Malicious updates employ various techniques to gain access to personal information. These can include exploiting vulnerabilities in the Android operating system, using phishing techniques to trick users into granting permissions, or simply installing keyloggers or other monitoring software that secretly records your keystrokes and other activities. Some updates might even install themselves as a system process, making them difficult to detect and remove.
They might also exploit vulnerabilities in other apps installed on your device to gain broader access to your system. For example, an update posing as a legitimate app update might actually install malware that then accesses contacts and messages through the permissions granted to the seemingly benign app.
Real-World Examples of Malicious Updates
While specific details of malicious updates are often kept confidential for security reasons, numerous instances of fraudulent updates leading to data breaches and financial losses have been reported. For example, news reports have highlighted cases where fake updates have installed malware capable of stealing banking information, leading to significant financial losses for affected users. These reports often highlight the lack of awareness amongst users and the difficulty in differentiating legitimate updates from malicious ones.
The consequences range from identity theft to the complete loss of control over the device.
Potential Damage Caused by Malware
The damage caused by malware delivered through fraudulent updates can be substantial. Here’s a summary:
- Data theft: Personal information (contacts, photos, messages, financial details, etc.) is stolen and potentially used for identity theft or financial fraud.
- Financial loss: Bank accounts are compromised, leading to unauthorized transactions and monetary losses.
- Device control: Attackers gain complete control of the device, using it for malicious activities such as sending spam or participating in botnets.
- Privacy violation: Location data, browsing history, and other sensitive information is collected and potentially shared without the user’s consent.
- System instability: The device becomes unstable, crashes frequently, or becomes unusable due to malware interference.
- Ransomware attacks: Files are encrypted and held hostage until a ransom is paid.
Prevention and Detection

Protecting your Android device from malicious system updates requires a proactive approach. Understanding how to verify updates and identify potentially harmful apps is crucial for maintaining your device’s security. This section Artikels practical steps and best practices to safeguard your Android device.
Knowing how to spot a fake update is just as important as knowing where to find legitimate ones. A multi-layered approach, combining careful verification with strong security habits, offers the best protection.
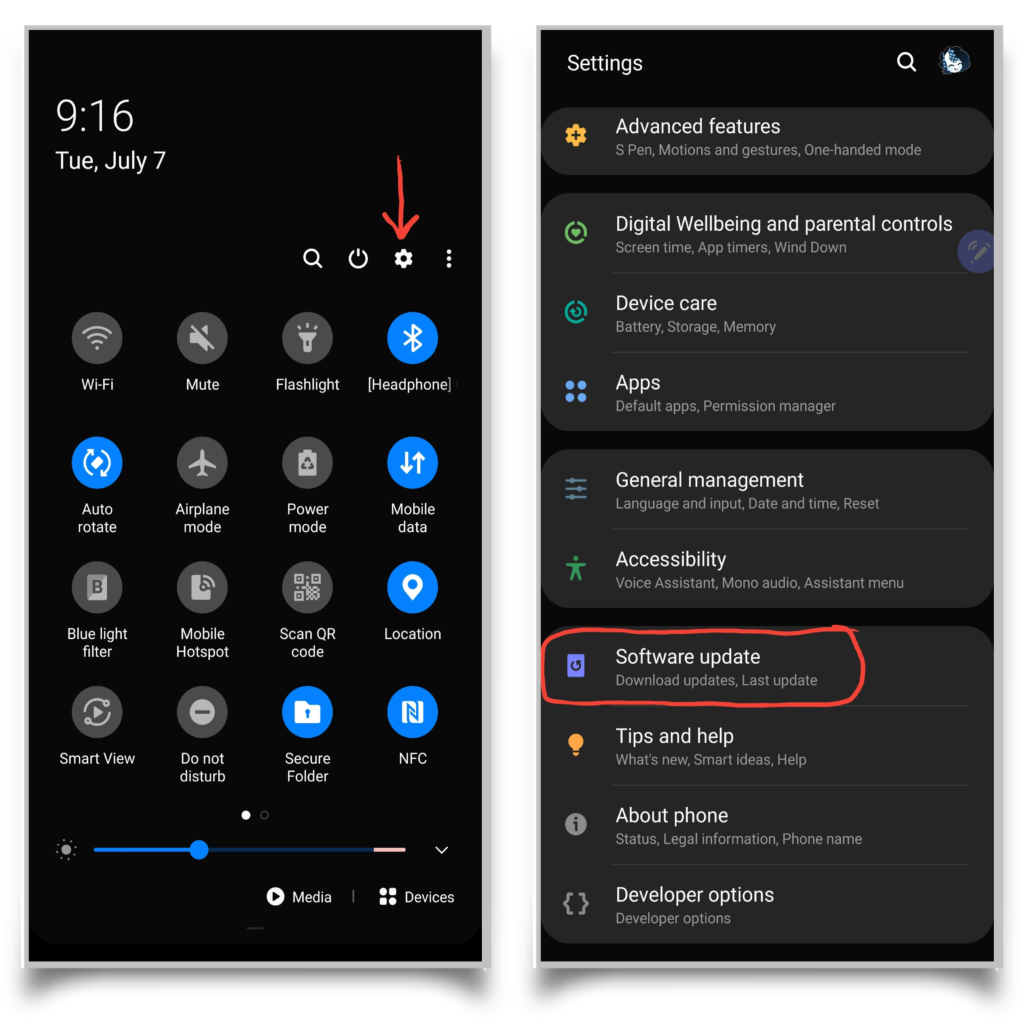
Authenticating Android System Updates
Verifying the authenticity of an Android system update is paramount. A fraudulent update can compromise your entire device. Follow these steps to ensure you’re installing a legitimate update:
- Check the Source: Only download updates directly from the official Android OS update mechanism or through your device manufacturer’s trusted channels (e.g., an app specifically designed for software updates from the manufacturer). Avoid third-party websites or apps claiming to offer faster or alternative updates.
- Verify the Update Details: Before initiating the update, carefully examine the update’s details. Look for the version number, release date, and a description of the changes and improvements. Compare this information with the official release notes available on your manufacturer’s website or Android’s support pages. Discrepancies should raise red flags.
- Examine the Digital Signature: Android uses digital signatures to verify the authenticity of updates. While this is a technical process not readily accessible to all users, it is a key component of secure updates. Trusting reputable sources and update channels effectively leverages this security feature.
- Check for Security Warnings: Your Android device may display security warnings or alerts during the update process if something seems amiss. Pay close attention to any such messages and do not proceed if there are concerns.
- Observe the Update Process: Legitimate updates usually have a clear and consistent process, with progress bars and clear instructions. Be wary of updates that seem rushed, incomplete, or that request unusual permissions.
Identifying Malicious Apps
Malicious apps can masquerade as legitimate update tools, tricking users into installing malware. Careful scrutiny of apps is essential.
- Check App Permissions: Before installing any app, particularly those related to system updates, carefully review the permissions it requests. An app that needs access to sensitive data like contacts, location, or financial information without a clear reason should be treated with suspicion.
- Read App Reviews: Examine user reviews on the app store. Negative reviews mentioning suspicious activity, malware, or unexpected behavior should raise concerns. Look for patterns or consistent complaints.
- Verify the Developer: Research the app developer. A reputable developer will usually have a clear online presence and positive feedback. Avoid apps from unknown or untrusted developers.
- Use a Reputable Antivirus App: A good antivirus app can help detect and block malicious apps before they can install or cause harm. Keep your antivirus software up-to-date and regularly scan your device.
Best Practices for Android Device Protection
Several proactive measures can significantly reduce the risk of malicious updates.
- Keep Your Software Updated: Regularly update your Android operating system and all your apps to the latest versions. These updates often include security patches that address known vulnerabilities.
- Enable Automatic Updates (where appropriate): Configure your device to automatically download and install updates when available. This ensures your system is always protected against the latest threats.
- Be Wary of Suspicious Links and Emails: Avoid clicking on links or opening attachments from unknown or untrusted sources. These can lead to malicious websites or downloads.
- Use Strong Passwords and Biometric Authentication: Protect your device with a strong password or use biometric authentication (fingerprint, facial recognition) to prevent unauthorized access.
- Back Up Your Data Regularly: Regular backups allow you to restore your data in case of a compromise or device failure.
Android’s Built-in Security Features
Android incorporates several security features designed to prevent malicious updates.
- Google Play Protect: This built-in security feature scans apps for malware and other threats before and after installation. It also monitors installed apps for suspicious activity.
- Verification of Apps from Google Play Store: Downloading apps exclusively from the official Google Play Store reduces the risk of installing malicious software. The Play Store has its own verification processes.
- App Sandbox: Each app runs in its own isolated environment (sandbox), limiting its access to other apps and system resources, thus minimizing the impact of a compromised app.
- Permission System: The Android permission system requires apps to explicitly request permission to access sensitive data or functionalities. Users can review and manage these permissions.
Response and Mitigation

Discovering a malicious Android system update on your device can be alarming, but swift action can significantly minimize the damage. This section Artikels the crucial steps to take if you suspect your Android device has been compromised by a fraudulent update. Remember, proactive measures are key to protecting your data and privacy.Responding to a suspected malicious update requires a multi-faceted approach, combining immediate defensive actions with reporting to relevant authorities to help prevent others from falling victim.
The process involves identifying the malicious software, removing it from your device, and reporting the incident to facilitate its removal from circulation.
Removing a Malicious Update
The first priority is to isolate the device from the internet to prevent further data exfiltration or communication with the malicious server. Next, immediately power down your device. This action is crucial in preventing the malware from running and causing more harm. Once powered off, try restarting your device in safe mode. Safe mode typically disables third-party apps, including the malicious update if it’s an app disguised as an update.
If the device behaves normally in safe mode, the problem likely originates from a recently installed application. You can then uninstall the suspicious app. If the problem persists even in safe mode, consider performing a factory reset. This will erase all data on your device, so it’s crucial to back up your data beforehand if possible (though be cautious, as backups from a compromised device may also contain malware).
A factory reset should be performed only as a last resort, after attempting to remove the update through other means. Following the factory reset, ensure to update your device to the legitimate system update from the official source.
Seriously, guys, be wary of that rogue Android update circulating – it’s a real headache! I’ve been trying to focus on more positive tech news, like the exciting developments in domino app dev the low code and pro code future , which is a much more pleasant distraction. But back to that malicious update; make sure your antivirus is up-to-date before even considering installing anything suspicious!
Reporting a Suspected Malicious Update
Reporting a malicious update is vital for protecting other users. Your report provides valuable information to security researchers and developers, enabling them to identify and address the threat quickly. You should gather as much information as possible about the malicious update, including the update’s name, version number, any observed unusual behavior, and the source from which you downloaded it.
The more detailed your report, the more effective it will be. Reporting should be done through official channels to ensure your report reaches the right people.
Resources for Assistance
If you’re struggling to remove the malicious update or need further assistance, several resources can help. Contacting your mobile carrier’s technical support is a good starting point, as they may have specific procedures for dealing with malicious software on their network. Many reputable cybersecurity firms also offer support services, providing expertise in malware removal and device recovery. Online forums and communities focused on Android security can be helpful sources of information and peer support.
However, always exercise caution when seeking advice online and verify the credibility of the source before following any instructions.
Reputable Sources for Reporting Malicious Software
It is important to report malicious software to reputable organizations that can take action. Here are some reputable sources for reporting malicious software:
- Google Play Protect: Google’s built-in security system can detect and report malicious apps.
- Android Security Team (Google): Google’s Android Security Team actively investigates security threats. While they may not have a public reporting portal for individual users, reporting to Google Play Protect will often reach them.
- Your Mobile Carrier: Your carrier’s security team may be able to assist with removing malicious software and identifying the source of the attack.
- National Cybersecurity Agencies (e.g., CISA in the US, NCSC in the UK): These agencies often have mechanisms for reporting cyber threats, including malicious software.
- Antivirus Software Vendors: Reputable antivirus software companies often have mechanisms for submitting samples of malicious software for analysis.
Visual Representation of Threats
Malicious Android system updates often employ deceptive visual elements to trick users into installing them. Understanding these visual cues is crucial for effective prevention. These deceptive tactics rely on mimicking legitimate update notifications, exploiting our familiarity with genuine system updates to lower our guard.Deceptive updates frequently leverage familiar visual elements to blend in seamlessly. Subtle variations in design, wording, and overall presentation are key to their success.
By understanding these differences, you can significantly improve your ability to identify and avoid potentially harmful updates.
Visual Characteristics of Deceptive Updates
Malicious updates often mimic the appearance of legitimate updates, but closer inspection reveals key differences. For example, the update icon might be slightly altered, perhaps a subtly different shade of the official Android logo, or a slightly less sharp image. The update description might use slightly incorrect grammar or wording, or might include unusually enthusiastic or urgent language, such as “Critical Security Update! Install Immediately!” when a less dramatic tone is usually employed by legitimate updates.
The size and placement of buttons can also be manipulated, with a “Download” or “Install” button made unusually prominent. Furthermore, the source of the update might be subtly misrepresented; a legitimate update would typically originate from Google Play or a trusted source, while a malicious one might originate from an unfamiliar or slightly misspelled domain.
Comparison of Legitimate and Malicious Update Notifications
Imagine two update notifications side-by-side. The legitimate notification from Google Play shows the standard Android logo, a concise description stating “Android System Update – Version 13.0.1,” with clear, simple language explaining the update’s purpose (e.g., “Security and performance improvements”). The “Install” button is appropriately sized and clearly labelled. In contrast, the malicious notification might use a slightly altered Android logo, perhaps with a less crisp image or a slightly different shade of green.
The description might read something like “Android System Update! Critical Security Patch! Download Now!!!” The use of multiple exclamation points and the aggressive language are immediate red flags. The “Download” button might be larger and more prominently positioned than in the legitimate notification. The source might be listed as something like “googleplay.com.update,” subtly different from the genuine address.
These small, seemingly insignificant differences are precisely what malicious actors exploit to deceive users.
Examples of Deceptive Design Elements
A common tactic involves using a similar color scheme and font to the legitimate update notification. The malicious update might even use the correct Android logo, but at a slightly lower resolution or with subtle distortions. Another tactic is to create a sense of urgency by using alarming language and overly bold text. For example, instead of stating “Security update available,” a deceptive update might proclaim “Urgent security threat detected! Update immediately!” This creates a sense of panic, encouraging users to ignore their caution and install the update without proper scrutiny.
The use of unusual capitalization, punctuation, or grammatical errors is another telltale sign. Legitimate updates are usually meticulously proofread. A malicious update might contain misspelled words or incorrect sentence structure, indicating its illegitimate origin.
Conclusive Thoughts
In the ever-evolving landscape of mobile threats, staying vigilant against malicious Android system updates is crucial. Remember, a little caution can go a long way in protecting your personal data and device security. By carefully examining update notifications, verifying sources, and understanding the potential risks, you can significantly reduce your vulnerability. Stay informed, stay safe, and keep your Android device running smoothly – without the unwelcome surprises of malicious software.
Questions and Answers
What happens if I install a malicious update?
Installing a malicious update can lead to data theft (passwords, photos, financial info), device hijacking (remote control by attackers), and the installation of further malware, potentially crippling your phone.
Can I recover my data if my phone is infected?
Data recovery depends on the extent of the damage. Backing up your data regularly is crucial. If infected, try a factory reset (after backing up what you can), but professional data recovery services might be necessary in severe cases.
How often should I check for updates?
Check for updates regularly, but don’t rush into installing them. Always verify the source and legitimacy before proceeding.
What should I do if I see a suspicious update notification?
Don’t install it! Immediately investigate the source. Compare it to known legitimate sources. If you’re unsure, contact your device manufacturer or carrier for verification.