Beware of This Ratmilad Android Spying Malware
Beware of this Ratmilad Android spying malware! This insidious piece of software is silently lurking, ready to steal your personal data and compromise your privacy. It’s more dangerous than your average Android virus, going beyond simple data theft to potentially granting remote access to your entire device. Let’s dive into what makes Ratmilad so dangerous and how to protect yourself.
Ratmilad’s sneaky methods of infection, from disguised apps to cleverly crafted phishing scams, make it a serious threat. Once installed, it can access your contacts, messages, photos, location data, and even financial information. Understanding its capabilities is the first step in protecting yourself against this malicious malware.
Understanding Ratmilad Malware
Ratmilad is a particularly nasty piece of Android malware, designed to spy on unsuspecting users and exfiltrate sensitive data. It operates in the shadows, silently collecting information and sending it to malicious actors. Understanding its functionality, infection methods, and the data it targets is crucial for effective protection.
Ratmilad Malware Functionality
Ratmilad functions as a sophisticated Remote Access Trojan (RAT). Once installed on a device, it grants remote attackers complete control. This control allows them to perform a range of malicious actions, including accessing contacts, reading messages (SMS, WhatsApp, etc.), recording calls, tracking location, taking photos and videos, accessing files, and even remotely controlling the device’s functions. Essentially, it transforms the infected phone into a digital surveillance tool.
The malware’s persistence mechanisms ensure it remains active even after a device restart, making it exceptionally difficult to remove without specialized tools.
Methods of Access and Infection
Ratmilad typically spreads through deceptive means. Users might unknowingly download and install it through disguised apps on unofficial app stores or through phishing campaigns that lure victims into downloading malicious APK files. These APKs often masquerade as legitimate apps, such as games or productivity tools. Social engineering tactics, such as promising exclusive content or offering free premium services, are frequently employed to trick users into granting the necessary permissions for the malware to function.
Once installed, Ratmilad often requests extensive permissions, which, if granted, allow it to access a wide range of sensitive data and device functions. The malware might also exploit vulnerabilities in the Android operating system to gain root access, granting even more control.
Types of Data Stolen by Ratmilad
The data stolen by Ratmilad is extensive and potentially devastating. This includes: contact lists, call logs, SMS messages, location data (GPS coordinates), photos and videos stored on the device, files from various storage locations, and credentials stored in applications. The malware can also record audio from the device’s microphone, effectively turning it into a listening device. Essentially, any data accessible on the compromised Android device is at risk.
Ratmilad Versions and Variants
While specific information on distinct versions or variants of Ratmilad is limited publicly, the malware’s modular nature suggests the possibility of ongoing development and updates. New capabilities and evasion techniques could be added over time, making it more difficult to detect and remove. Threat actors are likely to adapt the malware’s code to bypass security measures and remain undetected for longer periods.
This underscores the importance of staying updated with the latest security patches and using robust anti-malware solutions.
Comparison of Ratmilad with Other Android Malware
The following table compares Ratmilad to other known Android malware families. Note that the detection difficulty can vary depending on the specific anti-malware solution used and the sophistication of the malware’s evasion techniques.
| Malware Name | Data Stolen | Infection Method | Detection Difficulty |
|---|---|---|---|
| Ratmilad | Contacts, messages, location, photos, videos, files, audio recordings, credentials | Deceptive apps, phishing, exploit vulnerabilities | Moderate to High |
| Cerberus | Similar to Ratmilad, plus banking credentials | Similar to Ratmilad | High |
| Anubis | Similar to Ratmilad, often targets financial apps | Similar to Ratmilad | High |
| FakeInstaller | Various data depending on the disguised app | Disguised as legitimate app installers | Moderate |
Identifying Ratmilad Infection

Spotting Ratmilad, like any sneaky malware, requires vigilance. It doesn’t announce its presence with flashing lights and sirens; instead, it works silently in the background, subtly impacting your device’s performance and potentially stealing your data. Understanding the signs of infection is crucial for swift removal and minimizing damage.This section will detail the indicators of compromise (IOCs) associated with Ratmilad, the observable symptoms on your Android device, the performance impact, and provide a checklist to help you assess your device’s health.
We’ll also look at how Ratmilad might disguise itself.
Indicators of Compromise (IOCs)
Identifying Ratmilad requires looking for unusual activity on your device. These indicators might include the presence of unknown files or processes, unusual network traffic, or unexpected changes in system settings. Specific IOCs might include the detection of Ratmilad’s command-and-control (C&C) server IP addresses or domain names by security software, or the presence of unique file hashes associated with the malware itself.
These IOCs are typically identified by security professionals using specialized tools and analysis. Finding these indicators requires technical expertise and access to security software.
Observable Signs of Ratmilad Infection
While technical IOCs require specialized tools, several signs are readily apparent to the average user. These include unexpected battery drain, unexplained data usage, overheating, slow performance, and apps crashing frequently. You might also notice pop-up ads appearing even when you’re not using any ad-supported applications, or persistent notifications from unknown sources. Furthermore, unusual permissions requested by apps, particularly those related to accessing contacts, location, or microphone, should raise suspicion.
Seriously, folks, be wary of Ratmilad – that Android spying malware is nasty. Building secure apps is crucial, which is why I’ve been diving into the world of app development lately, particularly exploring the exciting advancements discussed in this article on domino app dev: the low-code and pro-code future. Understanding these new development methods is key to creating robust apps that are resistant to threats like Ratmilad.
So, stay safe out there and build smart!
If your device seems to be behaving strangely without a clear explanation, Ratmilad might be the culprit.
Performance Impact of Ratmilad
Ratmilad’s malicious activities consume system resources, leading to noticeable performance degradation. This can manifest as slower processing speeds, increased battery drain, and apps freezing or crashing more frequently. The severity of the performance impact depends on factors such as the device’s hardware capabilities and the extent of Ratmilad’s activity. For example, a powerful device might experience only minor slowdowns, while an older or less powerful device could suffer significantly, becoming practically unusable.
High data usage, even when you’re not actively using data-intensive applications, is another clear indicator of the malware’s background activities.
Checklist for Ratmilad Assessment
To assess your device for Ratmilad, consider the following steps:
- Check for unusual apps or processes running in the background.
- Monitor your data usage and battery consumption for unexpected spikes.
- Examine app permissions and revoke any suspicious ones.
- Scan your device with a reputable antivirus or anti-malware application.
- Review your device’s network activity for unusual connections.
- Look for any unauthorized changes to your device’s settings.
This checklist offers a proactive approach to identifying potential infections.
Applications or System Processes Mimicked by Ratmilad
Ratmilad, like other malware, often attempts to blend in by disguising itself as legitimate system processes or applications. It might mimic the names of common system utilities or even popular apps to avoid detection. Examples might include disguising itself as a system update process, a battery optimization tool, or even a seemingly harmless game. This makes visual identification difficult; therefore, relying solely on visual inspection is not sufficient.
Always verify the authenticity of any process or application using reputable sources before taking any action. Security software with advanced threat detection capabilities is essential for identifying such masquerades.
Preventing Ratmilad Infection: Beware Of This Ratmilad Android Spying Malware
Protecting your Android device from malware like Ratmilad requires a proactive approach encompassing several key security measures. Failing to take these precautions leaves your personal data, financial information, and device functionality vulnerable to serious compromise. This section details the essential steps to safeguard your Android phone or tablet.
Ratmilad, and similar Android malware, often exploits vulnerabilities in the operating system or uses social engineering tactics to gain access to your device. Understanding these potential entry points is crucial for effective prevention.
App Store Selection and Permission Verification
Choosing your app sources carefully is paramount. Downloading apps from unofficial app stores significantly increases your risk of encountering malware like Ratmilad. These unofficial stores often lack the security checks and vetting processes of established marketplaces. Always download apps from the official Google Play Store. Before installing any app, meticulously review its permissions.
If an app requests access to functionalities that seem unnecessary for its stated purpose (e.g., a flashlight app requesting access to your contacts), it’s a strong indication of potentially malicious behavior. Rejecting such requests can prevent Ratmilad and similar threats from gaining unwarranted access to your sensitive data.
Securing an Android Device Against Ratmilad and Similar Threats
A multi-layered approach is the most effective way to protect your device. Follow these steps to enhance your security:
- Install a reputable antivirus app: A good antivirus application will scan downloaded apps and files for malware before they can execute harmful code. Regular scans can help detect and remove existing infections.
- Enable automatic updates: Keep your Android operating system and all your apps updated to the latest versions. These updates often include security patches that address known vulnerabilities exploited by malware.
- Avoid clicking suspicious links: Be wary of links received through text messages, emails, or social media from unknown sources. These links can lead to malicious websites designed to install malware on your device.
- Enable screen lock and strong password: Use a strong password or biometric authentication (fingerprint or facial recognition) to prevent unauthorized access to your device. This adds an extra layer of protection, even if malware manages to partially compromise your system.
- Regularly review app permissions: Periodically check the permissions granted to your installed apps. Revoke permissions that seem unnecessary or suspicious. This can prevent malicious apps from accessing sensitive data.
- Back up your data: Regularly back up your important data to a cloud service or external storage. This allows you to restore your data in case of a malware infection or device failure.
The Importance of Software Updates and Security Patches
Regular software updates are essential for maintaining a secure Android device. These updates frequently include security patches that address vulnerabilities exploited by malware like Ratmilad. By keeping your operating system and apps up-to-date, you significantly reduce the risk of successful malware infections. Neglecting updates leaves your device vulnerable to known exploits, increasing the likelihood of a successful attack.
For example, a vulnerability patched in Android 12 might have been actively exploited by Ratmilad in earlier versions. Therefore, timely updates are a critical element in a comprehensive security strategy.
Responding to Ratmilad Infection
Discovering your Android device is infected with Ratmilad malware is a serious situation requiring immediate action. The longer the malware remains on your device, the greater the risk of data theft, financial loss, and identity compromise. This section details the crucial steps you must take to mitigate the damage and regain control of your device.
Immediate Actions Upon Suspecting Ratmilad Infection
The first step is to disconnect your device from all networks – Wi-Fi and mobile data. This prevents the malware from communicating with its command-and-control server and potentially exfiltrating more data. Next, put your device into Airplane mode to ensure complete network isolation. Immediately power down your device if possible, as this will halt any malicious activity.
Removing Ratmilad from an Infected Device
Removing Ratmilad requires a multi-pronged approach. First, perform a factory reset. This will wipe all data from your device, including the malware. However, it’s crucial to understand that a factory reset alone might not completely eliminate deeply rooted malware. Therefore, consider using a reputable anti-malware application after the factory reset.
Ensure the application is updated to the latest version before scanning your device. If the malware persists after a factory reset and anti-malware scan, professional assistance from a cybersecurity expert may be necessary. They possess specialized tools and techniques to identify and remove persistent threats.
Securing Online Accounts After Ratmilad Infection
Ratmilad’s access to your device likely compromises your online accounts. Change all your passwords immediately, including those for email, banking, social media, and other sensitive accounts. Use strong, unique passwords for each account. Consider enabling two-factor authentication (2FA) wherever possible to add an extra layer of security. It is also advisable to monitor your accounts for any suspicious activity, such as unauthorized transactions or login attempts from unfamiliar locations.
If you notice any irregularities, contact the respective service providers immediately.
Reporting Ratmilad Infections
Reporting Ratmilad infections is crucial for several reasons. First, it helps security researchers understand the malware’s capabilities and distribution methods, allowing them to develop better defenses. Second, reporting helps law enforcement agencies track down and prosecute the perpetrators. You can report the infection to your mobile carrier, the Android operating system provider (Google), and relevant cybersecurity authorities or companies such as the FBI’s Internet Crime Complaint Center (IC3) or your national cybersecurity agency.
Providing details about the infection, including how you believe you contracted the malware, will aid in their investigations.
Ratmilad Infection Response Flowchart, Beware of this ratmilad android spying malware
The following flowchart illustrates the steps to take if you suspect a Ratmilad infection:
[Diagram description: A flowchart would be visually represented here. It would begin with a diamond shape labeled “Suspected Ratmilad Infection?”. A “Yes” branch would lead to a rectangle labeled “Disconnect from all networks (Wi-Fi, Mobile Data) and put device in Airplane mode”. This would lead to another rectangle labeled “Power down device if possible”. This then leads to a rectangle labeled “Factory Reset Device”. Following this would be a rectangle labeled “Install and run updated anti-malware software”. Then a diamond labeled “Malware removed?”. A “Yes” branch would lead to a rectangle labeled “Change all passwords and enable 2FA”. A “No” branch would lead to a rectangle labeled “Seek professional cybersecurity assistance”. A “No” branch from the initial diamond would lead to a rectangle labeled “Monitor device for suspicious activity”. All paths would ultimately converge to a rectangle labeled “Report infection to relevant authorities.”]
Technical Analysis of Ratmilad
Ratmilad, a sophisticated Android spying malware, presents a complex technical landscape for analysis. Understanding its architecture, communication methods, and evasion techniques is crucial for effective detection and mitigation. This section delves into the technical intricacies of Ratmilad, providing insights into its inner workings.
Ratmilad Architecture
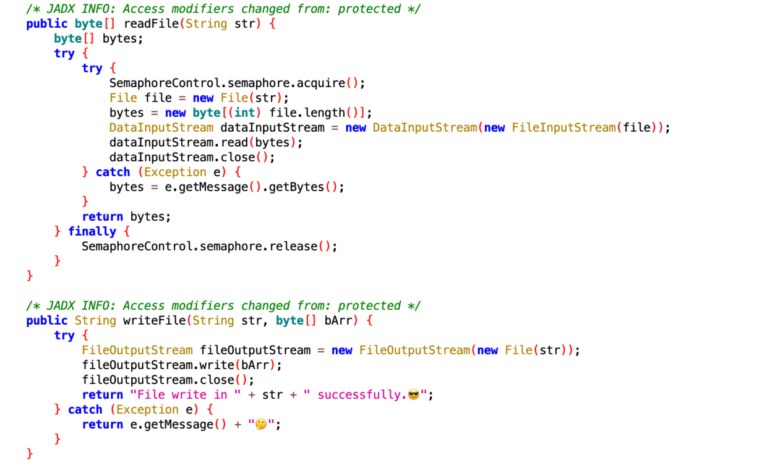
Ratmilad’s architecture is modular, allowing for flexibility and adaptability. It typically consists of several core components: a command-and-control (C&C) server, a client-side Android application (the malware itself), and potentially various plugins or modules that extend its functionality. The client application acts as an interface between the user’s device and the C&C server, relaying stolen data and receiving instructions. This modular design allows developers to easily update or add functionalities without needing to completely rewrite the entire malware.
The separation of components also increases the malware’s resilience against analysis and removal.
Command-and-Control (C&C) Infrastructure
Ratmilad utilizes a centralized C&C infrastructure for communication and control. The specific location and configuration of this infrastructure are constantly evolving to evade detection. However, past analysis has shown that Ratmilad often employs techniques like domain generation algorithms (DGAs) to generate a large pool of potential C&C server addresses, making it harder to track and block. Furthermore, the malware might use encrypted communication channels to hinder reverse engineering efforts and obfuscate the transmitted data.
The C&C server is responsible for distributing commands, receiving stolen data, and managing the infected devices.
Persistence and Evasion Techniques
Ratmilad employs various techniques to ensure persistence and evade detection on infected devices. These include:
- Device Administration Privileges: Ratmilad often attempts to gain device administrator privileges, making it extremely difficult to uninstall without specialized tools or knowledge. This elevated privilege allows it to survive reboots and resist removal attempts by the user.
- Rootkit Capabilities: Some variants of Ratmilad exhibit rootkit-like behavior, hiding their presence from the user and standard security applications. This involves techniques like concealing files, processes, and network connections.
- Anti-Analysis Techniques: Ratmilad incorporates anti-analysis techniques to hinder reverse engineering and malware analysis. This can involve code obfuscation, packing, and the use of anti-debugging measures. These techniques make it significantly more challenging to understand the malware’s functionality.
- Dynamic Code Loading: The malware may load parts of its functionality dynamically, making it harder to statically analyze its complete feature set. This technique helps avoid signature-based detection.
Comparison to Other Malware Samples
Ratmilad shares similarities with other Android banking Trojans and spyware families, particularly in its use of modular architecture, C&C communication, and persistence mechanisms. However, specific techniques used for data exfiltration, encryption, and anti-analysis differ, showcasing its unique design and ongoing evolution. While it borrows from established techniques, Ratmilad incorporates enough unique elements to distinguish it from other known malware.
The specific similarities and differences would need to be assessed through detailed comparative analysis of its codebase against other samples.
Communication Protocols
Ratmilad’s communication with its C&C server typically involves the use of several protocols, often layered to enhance security and obfuscation.
- HTTP/HTTPS: The most commonly observed protocol, used for command and control communication and data exfiltration. HTTPS provides encryption, obscuring the transmitted data.
- Custom Binary Protocols: Ratmilad often employs custom binary protocols to further enhance its stealth. These protocols are typically undocumented and require reverse engineering to understand their structure and functionality. This allows the malware to communicate in a way that’s less easily detected by network monitoring tools.
Conclusion
Ratmilad isn’t just another Android malware; it’s a sophisticated threat that demands our attention. By understanding its tactics and implementing robust security measures, we can significantly reduce our vulnerability. Remember to stay vigilant, keep your software updated, and only download apps from trusted sources. Your digital security depends on it!
General Inquiries
Can Ratmilad be removed completely?
Yes, but it often requires a factory reset of your device to ensure complete removal. Professional help might be necessary in some cases.
How can I tell if my device is slow because of Ratmilad?
Ratmilad’s performance impact can be subtle. Look for unusual battery drain, excessive data usage, or apps running in the background that you don’t recognize.
What if I’ve already been infected?
Immediately back up any essential data you can, then perform a factory reset. Change all your passwords and contact your bank and other relevant services to report potential fraud.
Is Ratmilad only targeting specific devices?
While some malware targets specific devices or operating systems, Ratmilad’s reach is broad. Any Android device can be vulnerable if proper security measures aren’t in place.