Beyond Awareness Cultivating Securitys Human Side
Beyond awareness how to cultivate the human side of security – Beyond Awareness: How to Cultivate the Human Side of Security – it’s a phrase that speaks volumes. We all know that strong passwords and firewalls are crucial, but what about the biggest security vulnerability? Us. Humans are inherently fallible, prone to errors, and susceptible to manipulation. This isn’t about blaming individuals; it’s about understanding how our psychology impacts security and building a system that acknowledges and mitigates those risks.
This post dives into practical strategies to foster a truly secure environment, one that prioritizes human factors alongside technology.
We’ll explore how social engineering works, why training alone isn’t enough, and the importance of building a culture of trust and open communication around security. We’ll look at how to address human error and bias, moving beyond simply meeting compliance requirements to proactive, human-centric security measures. Get ready to rethink your approach to security – it’s time to put the “human” back in the equation.
Understanding the Human Element in Security: Beyond Awareness How To Cultivate The Human Side Of Security
We live in a world increasingly reliant on technology, yet our reliance on technology often creates vulnerabilities. While robust technical security measures are crucial, they are only part of the equation. Ignoring the human element—the individuals who interact with and manage these systems—leaves organizations significantly exposed to risk. A purely technical approach overlooks the inherent fallibility and susceptibility to manipulation present in all humans, creating a significant weakness in any security strategy.
Limitations of Purely Technical Security Measures
Technical security measures, such as firewalls, intrusion detection systems, and encryption, are essential for a robust security posture. However, they are not foolproof. These systems can be bypassed, compromised, or simply ineffective against sophisticated attacks that exploit human weaknesses. For instance, a highly secure network can be compromised if an employee falls victim to a phishing scam and reveals their credentials.
Furthermore, technical solutions are often expensive to implement and maintain, requiring specialized expertise and ongoing updates to stay ahead of evolving threats. The reliance on solely technical measures neglects the most vulnerable component of any system: the human user.
Human Factors Contributing to Security Breaches
Human error is a leading cause of security breaches. This includes accidental actions like clicking malicious links, losing or misplacing devices containing sensitive information, or failing to update software with critical security patches. Beyond accidental errors, intentional actions such as insider threats, where employees intentionally compromise security for personal gain or malicious intent, also pose significant risks. Negligence, lack of training, and insufficient awareness of security best practices further amplify the human element’s impact on security vulnerabilities.
The combination of human fallibility and the sophistication of modern cyberattacks creates a potent threat landscape.
Examples of Social Engineering Attacks and Their Impact
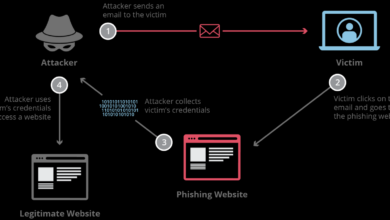
Social engineering attacks exploit human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. Phishing emails, posing as legitimate organizations, are a common example, often tricking users into clicking malicious links or revealing login credentials. Baiting, where attackers offer enticing rewards or information to gain access, is another effective technique. Pretexting involves creating a believable scenario to gain trust and information.
The impact of successful social engineering attacks can be devastating, leading to data breaches, financial losses, reputational damage, and legal repercussions. For example, a successful phishing attack targeting a company’s financial department could result in significant financial losses due to fraudulent transactions.
Psychological Principles Exploited in Successful Attacks, Beyond awareness how to cultivate the human side of security
Successful social engineering attacks often leverage fundamental psychological principles. These include exploiting trust, playing on emotions like fear or urgency, leveraging authority figures, and using reciprocity (the feeling of obligation to repay a favor). Attackers often employ techniques of persuasion and manipulation to bypass critical thinking and security protocols. The principle of scarcity (limited-time offers) or the desire for social acceptance can also be effectively used to manipulate individuals into making hasty decisions, neglecting their security awareness.
Understanding these psychological principles is crucial in developing effective countermeasures.
Comparison of Technical and Human-Centric Security Approaches
| Aspect | Technical Approach | Human-Centric Approach | Notes |
|---|---|---|---|
| Cost | High initial investment, ongoing maintenance costs | Relatively lower initial cost, ongoing training and awareness costs | Technical solutions often require significant upfront investment and continuous updates. Human-centric approaches require less upfront cost but ongoing investment in training and awareness. |
| Effectiveness | Highly effective against automated threats, less effective against sophisticated social engineering | Addresses the root cause of many breaches – human error | While technical measures are effective at blocking many threats, they are often ineffective against attacks that exploit human vulnerabilities. |
| Implementation | Requires technical expertise and infrastructure | Requires training, awareness programs, and clear security policies | Technical implementation requires specialized skills, while human-centric approaches focus on education and behavior change. |
| Maintenance | Requires ongoing updates, patching, and monitoring | Requires ongoing training, updates to policies, and reinforcement of security best practices | Both approaches require ongoing maintenance, but the nature of the maintenance differs significantly. |
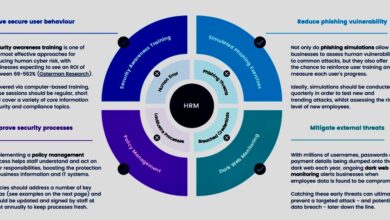
Cultivating a Security-Conscious Culture

Building a security-conscious culture isn’t just about implementing technical safeguards; it’s about fostering a mindset where security is everyone’s responsibility. A proactive approach, where employees actively participate in protecting company assets, is far more effective than relying solely on reactive measures. This requires a multi-faceted strategy encompassing robust training, clear communication, and strong leadership.
Strategies for Fostering a Proactive Security Mindset
Creating a proactive security mindset requires a shift in organizational culture. It’s about moving from a position where security is seen as an IT problem to one where it’s understood as a shared responsibility, integral to the success of the entire organization. This shift necessitates consistent reinforcement of security best practices, regular communication, and recognition of employees’ contributions to security.
Beyond awareness in security means fostering a culture of responsibility. It’s not just about policies, but about empowering individuals. This is where efficient development plays a crucial role; check out this article on domino app dev the low code and pro code future to see how streamlined processes can free up time for security training and awareness initiatives.
Ultimately, cultivating the human side of security requires a holistic approach, combining technology and people.
Regular security awareness campaigns, coupled with clear communication channels for reporting security incidents, are vital. Gamification and reward systems can further incentivize proactive security behavior. For example, a company could implement a points-based system where employees earn rewards for reporting security vulnerabilities or participating in security training.
Improving Employee Awareness and Training
Effective employee awareness and training go beyond simple compliance. It should be engaging, relevant, and tailored to the specific roles and responsibilities of employees. Using diverse learning methods, such as interactive modules, simulations, and real-world case studies, ensures information is retained and applied effectively. Regular refresher training, ideally incorporating new threats and vulnerabilities, is crucial to maintain a high level of awareness.
For example, a training program could include interactive scenarios simulating phishing attacks, allowing employees to practice identifying and reporting suspicious emails. This hands-on approach significantly improves knowledge retention compared to passive methods like reading lengthy manuals.
A Comprehensive Security Awareness Program
A successful security awareness program needs to be comprehensive, addressing diverse learning styles. It should combine various methods to cater to visual, auditory, and kinesthetic learners. This could involve videos, podcasts, interactive quizzes, hands-on workshops, and even gamified challenges. The program should also be regularly updated to reflect the ever-evolving threat landscape. Consider incorporating real-world examples of security breaches and their consequences to emphasize the importance of security best practices.
Regular feedback mechanisms, such as surveys and focus groups, are important to gauge the effectiveness of the program and make necessary adjustments.
The Role of Leadership in Promoting a Security-Conscious Culture
Leadership plays a pivotal role in establishing and maintaining a security-conscious culture. Leaders must actively champion security initiatives, demonstrating their commitment through visible support and participation. This includes setting a clear example by adhering to security policies and actively promoting security awareness among their teams. Regular communication from leadership, emphasizing the importance of security and acknowledging employee contributions, is crucial.
Furthermore, leaders should allocate the necessary resources to support security initiatives, including training and awareness programs. For instance, a CEO publicly endorsing a new security awareness program and highlighting its importance during a company-wide meeting sends a strong message to all employees.
Actionable Steps for Implementing a Robust Security Awareness Program
Implementing a robust security awareness program requires a structured approach. The following steps provide a framework for success:
- Conduct a thorough risk assessment to identify vulnerabilities and tailor the program accordingly.
- Develop a comprehensive training curriculum that addresses various learning styles and incorporates interactive elements.
- Establish clear communication channels for reporting security incidents and providing feedback.
- Implement a system for tracking employee participation and measuring the effectiveness of the program.
- Regularly update the program to reflect evolving threats and vulnerabilities.
- Recognize and reward employees for their contributions to security.
- Secure buy-in from leadership to ensure consistent support and resources.
- Conduct regular phishing simulations and other security awareness exercises to test employee knowledge and preparedness.
- Integrate security awareness training into new employee onboarding.
- Create a culture of open communication and feedback regarding security concerns.
Building Trust and Collaboration
Building a strong security posture isn’t just about technology; it’s fundamentally about people. A security program, no matter how sophisticated, will falter without the trust and collaboration of everyone within an organization. Open communication, shared responsibility, and a culture of psychological safety are crucial for creating a truly effective security framework.Open communication and feedback are the cornerstones of a successful security program.
When employees feel comfortable voicing concerns, reporting vulnerabilities, and offering suggestions, the organization gains valuable insights that can prevent costly breaches. Conversely, a culture of silence or fear can lead to undetected weaknesses and a higher risk of successful attacks.
Open Communication and Feedback Mechanisms
Effective communication regarding security risks requires multiple channels and consistent reinforcement. Regular security awareness training sessions, coupled with easily accessible reporting mechanisms (like anonymous online forms or dedicated hotlines), ensure employees know how to communicate concerns. Feedback mechanisms, such as post-incident surveys or regular employee pulse checks on security-related matters, allow the security team to gauge effectiveness and identify areas for improvement.
For instance, a company could implement a system where employees can anonymously submit security concerns via a dedicated email address or a secure online platform. The security team would then acknowledge receipt of the report and provide updates on the investigation and resolution. This demonstrates transparency and builds confidence in the process.
Barriers to Effective Security Communication
Several factors can hinder effective communication about security risks. These include a lack of trust in security teams, fear of retribution for reporting incidents, unclear communication channels, and a perception that security concerns are not taken seriously. For example, if employees have experienced disciplinary action in the past for reporting minor security issues, they may be hesitant to report future incidents, even if serious.
Similarly, if communication from the security team is technical, jargon-laden, or infrequent, employees may feel disconnected and less likely to engage.
Building Trust Between Security Teams and Employees
Building trust requires consistent effort and transparency. Security teams should demonstrate competence, fairness, and empathy. Regular communication, including updates on security initiatives and responses to reported incidents, is crucial. This could involve newsletters, town hall meetings, or even informal chats to build rapport and demonstrate that the security team values employee input. Furthermore, actively soliciting feedback and demonstrating a willingness to adapt based on employee input fosters a sense of collaboration and mutual respect.
For example, regularly scheduled feedback sessions with department heads could provide valuable insights into employee perceptions and concerns regarding security practices.
Encouraging Secure Incident Reporting
A crucial element in fostering a security-conscious culture is creating a safe space for employees to report security incidents without fear of reprisal. This requires clear policies that guarantee confidentiality and protect against retaliation. Anonymous reporting mechanisms should be readily available, and the process for investigating and resolving incidents should be transparent and fair. It’s essential to emphasize that reporting, even minor issues, is not only acceptable but encouraged, and that the focus is on improvement, not blame.
A well-defined incident response plan that includes clear communication protocols and guarantees of confidentiality will greatly enhance the willingness of employees to report security breaches.
Cultivating a Culture of Shared Responsibility
Security should not be solely the responsibility of the security team; it’s a collective effort. This requires fostering a culture where everyone understands their role in maintaining security. Regular training, clear guidelines, and consistent reinforcement of security best practices are essential. Furthermore, recognizing and rewarding employees who demonstrate exemplary security practices can further solidify the message that security is a shared responsibility.
For example, implementing a peer-recognition program where employees can nominate colleagues who have demonstrated strong security awareness could reinforce positive behaviors and encourage proactive participation.
Addressing Human Error and Bias
Human error and cognitive biases are significant contributors to security vulnerabilities. Understanding these factors is crucial for building robust security systems that account for the inherent limitations of human judgment and decision-making. Ignoring the human element leads to preventable breaches and significant financial and reputational damage. This section explores common types of human error, the influence of cognitive biases, and strategies for mitigation.
Common Types of Human Error in Security
Human error manifests in various ways, often leading to security breaches. These errors range from simple mistakes like forgetting passwords to more complex issues involving misconfigurations or social engineering susceptibility. For example, using easily guessable passwords, clicking on malicious links in phishing emails, or failing to update software are all common examples of human error that can compromise security.
Furthermore, inadequate training, poor security awareness, and time pressure can significantly exacerbate the likelihood of errors.
The Influence of Cognitive Biases on Security Decisions
Cognitive biases are systematic patterns of deviation from norm or rationality in judgment. These biases significantly influence how we perceive and process information, impacting our security decisions. For example, confirmation bias—the tendency to favor information confirming pre-existing beliefs—can lead to overlooking critical security threats that contradict our assumptions. Similarly, anchoring bias—over-reliance on the first piece of information received—can lead to flawed risk assessments.
The availability heuristic, where we overestimate the likelihood of events easily recalled, can also skew security priorities, leading to disproportionate focus on easily remembered threats while neglecting less salient but potentially more dangerous ones.
Strategies for Mitigating Human Error and Bias in Security Practices
Mitigating human error and bias requires a multi-faceted approach. Effective security awareness training is paramount, educating users about common threats and best practices. This training should be engaging, regularly updated, and tailored to the specific risks faced by the organization. Implementing strong authentication mechanisms, such as multi-factor authentication, reduces reliance on easily compromised passwords. Furthermore, designing user-friendly security systems minimizes the potential for errors stemming from complex or confusing interfaces.
Regular security audits and penetration testing can help identify vulnerabilities and assess the effectiveness of security controls. Finally, fostering a culture of security awareness where reporting errors is encouraged and not punished is crucial.
Examples of Successful Interventions to Reduce Human-Caused Security Incidents
Many organizations have successfully implemented strategies to reduce human-caused security incidents. For instance, implementing mandatory security awareness training programs with regular assessments and phishing simulations has demonstrably improved employee behavior and reduced the number of successful phishing attacks. Similarly, the introduction of simplified password management systems and multi-factor authentication has significantly reduced the number of compromised accounts. The use of security information and event management (SIEM) systems allows for proactive monitoring and detection of suspicious activities, alerting security teams to potential breaches before significant damage is done.
Cognitive Biases and Their Impact on Security
| Cognitive Bias | Impact on Security |
|---|---|
| Confirmation Bias | Ignoring contradictory evidence, leading to overlooked vulnerabilities. |
| Anchoring Bias | Over-reliance on initial assessments, leading to inaccurate risk prioritization. |
| Availability Heuristic | Overestimating the likelihood of easily recalled threats, neglecting less salient but potentially more dangerous ones. |
| Overconfidence Bias | Underestimating risks and vulnerabilities, leading to inadequate security measures. |
| Bandwagon Effect | Following the crowd’s security practices without critical evaluation, leading to vulnerabilities. |
Beyond Compliance

Compliance-based security, while crucial for meeting legal and regulatory requirements, often falls short in protecting against the ever-evolving landscape of modern threats. Relying solely on ticking boxes and meeting minimum standards leaves organizations vulnerable to sophisticated attacks that exploit human vulnerabilities and unforeseen circumstances. A proactive approach is essential to truly secure an organization’s assets and maintain a robust security posture.Proactive security measures go beyond simply reacting to threats or addressing vulnerabilities after they’ve been exploited.
Instead, they focus on anticipating potential risks, implementing preventative measures, and fostering a security-conscious culture within the organization. This shift from reactive to proactive security is a fundamental change in mindset, requiring a strategic investment in people, processes, and technology.
Proactive Security Measures
Implementing proactive security involves a multi-faceted approach. It’s not enough to simply install firewalls and antivirus software; organizations must also invest in employee training, security awareness programs, and robust incident response planning. Regular security audits and penetration testing can identify vulnerabilities before attackers do, allowing for timely remediation. Furthermore, implementing robust access control measures, data loss prevention (DLP) tools, and multi-factor authentication (MFA) are crucial steps in building a layered security defense.
Examples of Proactive Security Initiatives
Several initiatives exemplify a proactive approach. For instance, implementing a bug bounty program encourages ethical hackers to identify vulnerabilities before malicious actors. Regular security awareness training, incorporating simulated phishing attacks and interactive modules, can significantly improve employee vigilance and reduce the likelihood of successful social engineering attempts. Conducting regular tabletop exercises to simulate real-world security incidents allows teams to practice their response and refine their procedures, ensuring smoother and more effective responses in the event of a breach.
Benefits of Security Awareness and Training
Investing in security awareness and training is a highly effective proactive measure. Employees are often the weakest link in the security chain, and comprehensive training can equip them with the knowledge and skills to identify and report potential threats. This includes understanding phishing scams, recognizing malware, and following secure password practices. Regular training sessions, coupled with engaging materials and reinforcement activities, maintain a high level of security awareness and build a culture of security within the organization.
The benefits extend beyond incident prevention, fostering a more security-conscious workforce and reducing the overall risk profile of the organization.
Visual Representation: Reactive vs. Proactive Security
Imagine two diagrams. The first, representing reactive security, depicts a castle under siege. Arrows (representing cyberattacks) are hitting the castle walls. The defenders are scrambling to repair the damageafter* the attacks occur. They are constantly reacting to the incoming threats, patching holes as they appear, but never addressing the underlying vulnerabilities.
The castle is constantly under attack, and resources are perpetually focused on damage control.The second diagram, representing proactive security, shows the same castle, but with a strong moat (representing preventative measures like MFA and strong access controls), sturdy walls (representing robust infrastructure and security technologies), and vigilant guards (representing trained and security-aware employees) patrolling the perimeter. Arrows still fly, but many are deflected by the moat and walls.
The guards identify and neutralize potential threats before they can breach the defenses. The focus is on prevention and preparedness, ensuring a strong and resilient security posture. This illustration clearly shows the difference between reacting to threats and proactively preventing them.
Measuring the Effectiveness of Human-Centric Security
Implementing human-centric security isn’t just about feeling good; it needs to demonstrate tangible results. Measuring its effectiveness requires a multifaceted approach, tracking key metrics to show a clear return on investment and improved security posture. This isn’t just about ticking boxes; it’s about proving the value of investing in your people.
Key Metrics for Evaluating Human-Centric Security Initiatives
Effective measurement requires focusing on specific, measurable, achievable, relevant, and time-bound (SMART) goals. We need to move beyond simple completion rates and delve into the actual impact on security. For example, instead of just measuring the percentage of employees who completed a training module, we should track the reduction in phishing click rates among those employees post-training.
- Phishing Click Rates: A significant indicator of employee susceptibility to social engineering attacks. A decrease shows the effectiveness of awareness training.
- Security Incident Reporting Rates: Increased reporting suggests employees are more comfortable and confident in reporting potential breaches, leading to faster responses.
- Time to Resolve Security Incidents: Faster resolution times indicate improved employee understanding of security protocols and procedures.
- Number of Security Policy Violations: A reduction demonstrates improved understanding and adherence to established security guidelines.
- Employee Satisfaction with Security Awareness Programs: High satisfaction suggests engagement and buy-in, crucial for long-term success. This can be measured through surveys and feedback mechanisms.
Tracking Employee Engagement in Security Awareness Programs
Measuring engagement goes beyond simple completion rates. We need to understand how employees are interacting with the training materials and applying their learning in their daily work.
- Quiz Scores and Knowledge Retention Tests: These assess understanding of key security concepts.
- Active Participation in Simulated Phishing Exercises: Measuring participation and successful identification of phishing attempts.
- Feedback Surveys and Focus Groups: Gathering qualitative data on employee perception and suggestions for improvement.
- Gamification Metrics: Tracking points earned, badges achieved, and leaderboard rankings in gamified training programs. Higher scores and engagement indicate greater learning and retention.
Measuring the Reduction in Security Incidents Due to Human Error
Attributing a reduction in security incidents solely to human-centric security initiatives is challenging. However, by analyzing incident reports and correlating them with training and awareness programs, we can identify trends.
For instance, a company might track the number of data breaches caused by phishing attacks before and after implementing a comprehensive security awareness program. A significant decrease in breaches attributed to phishing could be directly linked to the effectiveness of the program. Analyzing the root causes of incidents helps pinpoint areas where human-centric initiatives have made the most impact.
Demonstrating the Return on Investment (ROI) of Human-Centric Security Measures
Calculating the ROI of human-centric security requires quantifying both costs and benefits. Costs include training materials, employee time, and program management. Benefits include reduced incident response costs, avoided fines and legal fees, and improved brand reputation.
ROI = (Return – Investment) / Investment
For example, if a company invests $10,000 in a security awareness program and avoids a $50,000 data breach due to improved employee awareness, the ROI is 400%. This calculation requires careful estimation of potential losses and accurate tracking of program costs.
Reporting Framework for Security Awareness Programs
A robust reporting framework should provide regular updates on key metrics, highlighting successes and areas for improvement. The framework should include:
- Regular Reporting Cycle: Monthly or quarterly reports provide timely insights.
- Key Performance Indicators (KPIs): Focus on the metrics discussed above.
- Visualizations: Charts and graphs effectively communicate data.
- Trend Analysis: Tracking changes over time to identify patterns and measure progress.
- Actionable Recommendations: Suggesting improvements based on data analysis.
Summary
Ultimately, cultivating the human side of security isn’t just about ticking boxes; it’s about creating a culture of shared responsibility and proactive engagement. By understanding human psychology, fostering open communication, and implementing effective training programs, organizations can significantly reduce their vulnerability to security breaches. It’s about moving beyond reactive measures and embracing a proactive, human-centric approach that prioritizes trust, collaboration, and a shared commitment to security.
Remember, your strongest security asset is your people – empower them, and you empower your entire security posture.
Questions Often Asked
What’s the difference between reactive and proactive security?
Reactive security responds to threats
-after* they occur (e.g., patching vulnerabilities after an exploit). Proactive security anticipates and prevents threats
-before* they happen (e.g., security awareness training, robust incident response planning).
How can I measure the effectiveness of my security awareness training?
Track metrics like employee participation rates, phishing test results, reported security incidents, and employee feedback. Analyze trends over time to see if training is improving security behaviors.
What if my employees are resistant to security awareness training?
Make training engaging and relevant to their daily tasks. Offer incentives, tailor content to different learning styles, and demonstrate the value of security to them personally.
How do I build trust with employees regarding security reporting?
Guarantee anonymity for reporting, ensure no retribution for honest mistakes, and clearly communicate the importance of reporting incidents to improve overall security.