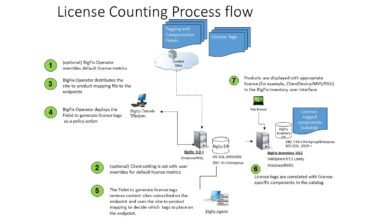
BigFix Extended Patch Expands Remediation to Hundreds of Third-Party Apps
Bigfix extended patch expands remediation content to hundreds of third party software titles – BigFix Extended Patch expands remediation content to hundreds of third-party software titles – that’s the headline, and it’s a game-changer. Imagine effortlessly patching vulnerabilities across your entire software ecosystem, including those pesky third-party apps that often slip through the cracks of traditional patch management. This isn’t just about saving time; it’s about significantly bolstering your organization’s security posture. This post dives deep into how BigFix Extended Patch achieves this, exploring its functionality, security implications, and the overall benefits it offers.
We’ll cover everything from the technical architecture that allows it to handle hundreds of third-party applications to practical deployment strategies and troubleshooting tips. Get ready to discover how BigFix Extended Patch can streamline your patch management process and significantly reduce your attack surface. We’ll also explore the cost-benefit analysis, so you can see how this powerful tool can deliver a strong return on investment.
BigFix Extended Patch Functionality
BigFix Extended Patch represents a significant advancement in patch management, moving beyond traditional solutions focused primarily on operating system updates. It empowers IT administrators to efficiently manage patches for hundreds of third-party applications, dramatically improving security posture and reducing the risk of vulnerabilities. This capability is crucial in today’s complex IT environments where reliance on diverse software is the norm.BigFix Extended Patch’s core functionality lies in its ability to automatically discover, assess, and remediate vulnerabilities across a wide range of third-party software.
Unlike standard patch management solutions that often rely on manual processes or limited vendor integrations, BigFix leverages a robust agent-based architecture and a comprehensive knowledge base of software updates to streamline the entire patch management lifecycle. This automation minimizes manual intervention, accelerates remediation, and reduces the overall time and resources required for patch management.
BigFix Extended Patch Architecture
The architecture of BigFix Extended Patch is designed for scalability and efficiency, enabling it to handle the complexities of managing updates for hundreds of third-party software titles. At its core is a centralized server that houses the patch catalog, containing detailed information about available updates for each supported application. This catalog is continuously updated, ensuring that the latest patches are readily available.
BigFix clients, deployed on managed endpoints, regularly communicate with the server to check for applicable updates. The communication uses a reliable, secure protocol. The client’s ability to handle numerous third-party applications is facilitated by the use of a flexible and extensible plugin architecture. These plugins provide the necessary logic to identify, download, and install updates for specific applications, ensuring compatibility across different operating systems and software versions.
This modular design allows for easy addition of support for new applications without requiring major changes to the core system. The entire process is carefully orchestrated, prioritizing patch deployment based on factors such as criticality and risk level.
Integrating BigFix Extended Patch
Integrating BigFix Extended Patch into an existing IT infrastructure is a relatively straightforward process, though the specific steps may vary slightly depending on the operating system and existing infrastructure. The process generally involves several key phases: installation of the BigFix server, deployment of BigFix clients to managed endpoints, configuration of patch management policies, and testing of the deployment process.
| Step | Windows | macOS | Linux |
|---|---|---|---|
| 1. Server Installation | Install the BigFix server software on a Windows server, configuring database and network settings. | Install the BigFix server software on a supported Linux server, configuring database and network settings. | Install the BigFix server software on a supported Linux server, configuring database and network settings. |
| 2. Client Deployment | Deploy the BigFix client agent to Windows endpoints using standard deployment mechanisms (e.g., Group Policy, SCCM). | Deploy the BigFix client agent to macOS endpoints using standard deployment mechanisms (e.g., JAMF, Munki). | Deploy the BigFix client agent to Linux endpoints using standard deployment mechanisms (e.g., Ansible, Puppet). |
| 3. Policy Configuration | Configure patch management policies within the BigFix console to specify which applications to patch, update schedules, and remediation actions. | Configure patch management policies within the BigFix console to specify which applications to patch, update schedules, and remediation actions. | Configure patch management policies within the BigFix console to specify which applications to patch, update schedules, and remediation actions. |
| 4. Testing and Validation | Test the patch deployment process on a small group of endpoints to ensure proper functionality and identify any potential issues. | Test the patch deployment process on a small group of endpoints to ensure proper functionality and identify any potential issues. | Test the patch deployment process on a small group of endpoints to ensure proper functionality and identify any potential issues. |
Security Implications and Best Practices
Expanding BigFix’s patching capabilities to encompass hundreds of third-party applications significantly increases the attack surface. While this broadens the scope of vulnerability remediation, it also introduces new security challenges that require careful consideration and proactive mitigation strategies. Failing to address these security concerns could lead to compromised systems and data breaches.Implementing BigFix Extended Patch requires a robust security posture to prevent unauthorized access and ensure the integrity of the patching process.
This includes careful consideration of access controls, vulnerability management, and ongoing monitoring. A well-defined security policy is crucial for successful deployment and maintenance.
Potential Security Vulnerabilities and Mitigation Strategies
The extended reach of BigFix Extended Patch increases the potential for vulnerabilities. For example, compromised patch packages could introduce malware onto managed systems, while insecure configuration of the BigFix server itself could allow attackers to manipulate the patching process. Therefore, a multi-layered approach to security is vital.
- Vulnerability in Patch Packages: Malicious actors could potentially tamper with patch packages before they are deployed through BigFix. Mitigation involves rigorous verification of patch source integrity using digital signatures and checksum verification before deployment. Employing a secure repository for storing and managing patch packages is also critical.
- Insecure BigFix Server Configuration: Weak passwords, open ports, and lack of proper authentication mechanisms on the BigFix server create significant security risks. Mitigation requires implementing strong password policies, restricting network access to the server using firewalls and access control lists, and regularly updating the BigFix server software to address known vulnerabilities.
- Unauthorized Access to BigFix Console: Unauthorized access to the BigFix console could allow attackers to manipulate patch deployments, disable security features, or gain control of managed systems. Mitigation involves implementing role-based access control (RBAC) to limit access based on user roles and responsibilities, along with multi-factor authentication (MFA) for enhanced security.
Best Practices for Securing the BigFix Extended Patch System
Securing the BigFix Extended Patch system requires a proactive and multi-faceted approach. This includes regularly reviewing and updating security policies, conducting security audits, and establishing incident response procedures.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in the BigFix infrastructure and patch deployment processes. This includes reviewing access logs, analyzing security events, and verifying the effectiveness of security controls.
- Vulnerability Management: Implement a robust vulnerability management program that includes regular scanning for vulnerabilities in both the BigFix server and the managed endpoints. Prioritize patching critical vulnerabilities promptly.
- Strong Authentication and Authorization: Enforce strong password policies, implement multi-factor authentication (MFA), and leverage role-based access control (RBAC) to restrict access to the BigFix console and sensitive data.
- Network Security: Restrict network access to the BigFix server using firewalls and access control lists. Utilize secure network protocols and encrypt all communication between the BigFix server and managed endpoints.
- Regular Software Updates: Keep the BigFix server and all managed endpoints updated with the latest security patches and software updates to address known vulnerabilities.
BigFix Extended Patch Security Policy
A comprehensive security policy is essential for governing the use and management of BigFix Extended Patch within an organization. This policy should clearly define roles, responsibilities, and security controls.
“This policy Artikels the security requirements for the use and management of BigFix Extended Patch within [Organization Name]. All users and administrators are expected to adhere to these guidelines to ensure the security and integrity of our systems.”
The policy should cover aspects like: access control, patch management procedures, incident response plans, security awareness training, and regular security audits. It should also include procedures for handling security incidents and reporting vulnerabilities. Regular reviews and updates to the policy are essential to adapt to evolving threats and best practices. The policy should be readily available to all relevant personnel and enforced consistently.
Deployment and Management Strategies
Rolling out BigFix Extended Patch across your organization requires careful planning and execution. A phased approach, coupled with thorough user training and ongoing monitoring, is key to a successful implementation and sustained effectiveness. Ignoring these aspects can lead to deployment failures, security vulnerabilities, and ultimately, a diminished return on investment.Successfully deploying BigFix Extended Patch involves a multi-stage process.
This includes not only the technical aspects of software installation and configuration but also the crucial element of user preparedness and ongoing maintenance. A well-defined plan minimizes disruption and maximizes the benefits of this powerful patching solution.
Deployment Plan
A robust deployment plan for BigFix Extended Patch should consider several key factors. First, assess your network infrastructure’s capacity to handle the increased data traffic during patch deployment. A phased rollout, starting with a pilot group of machines, allows for identification and resolution of any unforeseen issues before a full-scale deployment. This pilot program provides valuable feedback on potential bottlenecks and allows for adjustments to the deployment strategy.
Secondly, comprehensive user training is paramount. Users need to understand the importance of patching, the process involved, and how to report any issues encountered. This training should be tailored to different user groups based on their technical expertise. Finally, create a detailed timeline outlining each stage of the deployment, from initial planning to post-deployment monitoring. This timeline should include specific milestones and deadlines to ensure the project stays on track.
For example, a phased rollout might begin with a small, well-defined test group (e.g., 10% of endpoints) followed by expanding to larger segments (e.g., 25%, 50%, then 100%) over several weeks or months, depending on the scale of the organization. This allows for monitoring the impact of the patches and addressing any issues before wider deployment.
Management Checklist
Effective management of BigFix Extended Patch is crucial for maintaining its effectiveness and ensuring the ongoing security of your systems. Regular maintenance and updates are essential to keep the system running smoothly and to address any vulnerabilities that may arise. The following checklist Artikels key tasks for managing BigFix Extended Patch:
- Regular Software Updates: Ensure BigFix itself is updated to the latest version to benefit from performance improvements, bug fixes, and new features.
- Patch Catalog Maintenance: Regularly review and update the patch catalog to ensure it contains the latest patches for all supported software. This includes adding new titles and removing obsolete ones.
- Scheduled Patch Deployments: Implement a schedule for deploying patches, considering factors such as system usage patterns and potential downtime.
- Reporting and Analysis: Regularly review reports on patch deployment success rates, identifying and addressing any issues that prevent successful patching.
- Security Audits: Conduct regular security audits to identify potential vulnerabilities and ensure that the patching process is effective.
- Compliance Monitoring: Monitor compliance with patch management policies and take corrective action where necessary.
- Log Management: Maintain detailed logs of all patch deployments and related activities for troubleshooting and auditing purposes.
Performance and Effectiveness Monitoring, Bigfix extended patch expands remediation content to hundreds of third party software titles
Monitoring the performance and effectiveness of BigFix Extended Patch involves several methods. Analyzing patch deployment success rates provides immediate insights into the efficiency of the process. This data can be used to identify and address any bottlenecks or issues that may be hindering successful patching. Furthermore, regular reporting on the number of vulnerabilities remediated allows for a quantitative assessment of the effectiveness of the patching strategy.
For example, if the number of critical vulnerabilities remains high despite frequent patching, it may indicate a need for adjustments to the patching strategy or the patch catalog itself. Beyond simple metrics, advanced analysis can reveal trends and patterns in patch deployment, helping to predict future patching needs and optimize the process. Real-time monitoring of patch deployment progress allows for immediate intervention if any issues arise.
This proactive approach minimizes downtime and ensures that the patching process remains efficient and effective. A well-designed dashboard that visualizes key metrics, such as patch deployment success rates and the number of vulnerabilities remediated, is essential for effective monitoring. This allows for quick identification of potential problems and facilitates timely intervention.
Integration with Other Systems: Bigfix Extended Patch Expands Remediation Content To Hundreds Of Third Party Software Titles

BigFix Extended Patch doesn’t exist in a vacuum; its true power unfolds when integrated with other IT management tools. Effective patching requires a holistic approach, and seamless integration streamlines workflows, enhances visibility, and improves overall security. This section explores how BigFix Extended Patch collaborates with other systems, automates patch deployment, and strengthens organizational security.
The strength of BigFix Extended Patch lies in its ability to connect with existing IT infrastructure, minimizing disruption and maximizing efficiency. By integrating with various systems, you gain a unified view of your patch management landscape, reducing the complexity and potential for errors.
BigFix Extended Patch Integrations
Below is a table illustrating how BigFix Extended Patch integrates with several common IT management systems. The integration methods vary, offering flexibility depending on your existing environment and requirements.
| System Name | Integration Method | Benefits |
|---|---|---|
| ServiceNow | API Integration | Automated ticket creation and updates for patch failures; centralized visibility of patch status within the ServiceNow platform. This allows for streamlined incident management and improved collaboration between IT and other departments. |
| SCCM (System Center Configuration Manager) | Data Synchronization (e.g., via custom scripts or third-party tools) | Consolidated reporting on patch compliance across both BigFix and SCCM managed devices; potential for reduced redundancy in patch management infrastructure. This can lead to cost savings and simplified management. |
| Jira | API Integration | Automated creation of Jira issues for critical patch failures, facilitating efficient tracking and resolution of patching problems. This provides better visibility and accountability for addressing vulnerabilities. |
| Active Directory | Group Policy integration (indirectly via BigFix’s ability to leverage AD groups for targeting) | Targeted patch deployment to specific organizational units or groups within Active Directory, enhancing control and precision in patch management. This allows for more granular control over the deployment process. |
Automating Patch Deployment with Scripting
Automating patch deployment using BigFix Extended Patch and scripting languages like PowerShell or Bash significantly improves efficiency and reduces the risk of human error. This allows for consistent and reliable patch application across a large number of systems.
For example, a PowerShell script could be used to query BigFix for systems requiring a specific patch, then trigger the deployment using BigFix actions. This script could also incorporate error handling and reporting mechanisms, providing detailed logs and alerts.
Similarly, a Bash script could perform similar functions within a Linux environment, leveraging BigFix’s cross-platform capabilities. This ensures consistent automation across heterogeneous IT infrastructures.
Improving Organizational Security Posture
BigFix Extended Patch contributes to improved security by automating the patching process, reducing the window of vulnerability, and providing detailed reporting on patch compliance. This proactive approach helps mitigate the risk of successful cyberattacks exploiting known vulnerabilities.
For instance, by automatically deploying critical security patches within hours of release, organizations can significantly reduce their attack surface and minimize the impact of potential breaches. The detailed reporting capabilities of BigFix allow security teams to identify and address systems that are not compliant with patching policies, proactively mitigating risk.
Furthermore, the integration with other systems, such as SIEM (Security Information and Event Management) solutions, allows for correlation of patch status with security events, providing valuable insights into the effectiveness of security measures and identifying potential weaknesses.
Cost and Return on Investment (ROI)
BigFix Extended Patch offers significant potential cost savings, but understanding the true return on investment requires a careful analysis of both costs and benefits. This involves calculating the total cost of ownership (TCO) and then comparing it to the avoided costs and increased efficiency resulting from the implementation.Calculating the TCO and ROI for BigFix Extended Patch requires a multi-faceted approach.
We need to consider not only the initial licensing fees but also the ongoing maintenance, support, and the resources dedicated to deployment and management. On the benefit side, we need to quantify the reduction in security vulnerabilities, the minimized downtime due to patching failures, and the improved compliance posture.
Total Cost of Ownership (TCO) Calculation
The TCO of BigFix Extended Patch includes several key components. Firstly, there’s the initial software license cost, which varies depending on the number of managed endpoints. Secondly, annual maintenance and support fees contribute significantly. Thirdly, consider the internal resources dedicated to deployment, configuration, and ongoing management – this includes the time spent by IT staff on tasks like patch deployment, troubleshooting, and reporting.
Finally, potential training costs for staff members responsible for managing the system should be factored in. A realistic TCO calculation should account for all these aspects over a projected timeframe, say three to five years. For example, a company with 5,000 endpoints might expect an initial license cost of $X, annual maintenance of $Y, and internal resource costs (salaries, benefits, etc.) of $Z per year.
Adding these costs over a five-year period gives a comprehensive TCO.
Return on Investment (ROI) Assessment
Assessing the ROI involves comparing the TCO with the benefits achieved. Key benefits include reduced vulnerability to security breaches, minimizing downtime caused by unpatched systems, improved compliance with industry regulations (like PCI DSS or HIPAA), and increased productivity due to less time spent on manual patching. Quantifying these benefits requires careful analysis. For instance, a security breach could cost a company millions of dollars in remediation, legal fees, and reputational damage.
BigFix Extended Patch helps mitigate this risk. Similarly, downtime due to system failures can significantly impact productivity and revenue. By reducing downtime, BigFix Extended Patch directly contributes to cost savings. To calculate ROI, we can use a simple formula:
ROI = (Total Benefits – Total Costs) / Total Costs
. Let’s say that by implementing BigFix Extended Patch, a company avoids a potential $1 million security breach and reduces downtime costs by $50,000 annually over five years. If the TCO is $200,000 over the same period, the ROI would be calculated as follows:
ROI = ($1,000,000 + ($50,000
- 5)
- $200,000) / $200,000 = 3.75 or 375%
. This illustrates a significant return on investment.
Financial Model Illustrating Cost Savings
A simple financial model can project potential cost savings. Consider a scenario where a company spends $100,000 annually on manual patching, experiences an average of 10 hours of downtime per month due to patching issues (at a cost of $5,000 per hour), and faces a 10% risk of a security breach costing $500, By implementing BigFix Extended Patch, let’s assume that downtime is reduced by 80%, and the risk of a security breach is lowered by 50%.
The table below illustrates the potential savings:
| Item | Annual Cost Before BigFix | Annual Cost After BigFix | Annual Savings |
|---|---|---|---|
| Manual Patching | $100,000 | $0 | $100,000 |
| Downtime | $600,000 (10 hours/month
|
$120,000 (20% of original downtime cost) | $480,000 |
| Security Breach Risk | $50,000 (10% – $500,000) | $25,000 (5% – $500,000) | $25,000 |
| Total Annual Savings | $605,000 |
This model demonstrates that even with the initial investment in BigFix Extended Patch, significant cost savings can be realized within a relatively short period. Remember that these figures are illustrative; actual savings will vary depending on the specific circumstances of each organization.
Troubleshooting and Support
BigFix Extended Patch, while powerful, can sometimes present challenges. This section provides guidance on resolving common issues and accessing support resources to ensure a smooth patching experience. Understanding potential problems and their solutions will minimize downtime and maximize the effectiveness of your patching strategy.
Common BigFix Extended Patch Issues and Resolutions
Troubleshooting BigFix Extended Patch often involves examining logs, verifying configurations, and checking network connectivity. Below are some common issues and their corresponding solutions.
- Patch Deployment Failures: Failures can stem from various sources, including network connectivity problems, insufficient permissions on target machines, or issues with the patch packages themselves. First, review the BigFix console logs for error messages indicating the specific reason for failure. Check network connectivity between the BigFix server and the target machines. Ensure the BigFix client is running and has the necessary permissions to install software.
If the problem persists, verify the integrity of the patch packages and try re-deploying them.
- Slow Patch Deployment: Slow deployments might be due to network bandwidth limitations, a large number of target machines, or poorly optimized patch packages. Optimize your network for BigFix traffic, prioritize patch deployments during off-peak hours, and consider breaking down large deployments into smaller, more manageable batches. Analyze the size and structure of the patch packages to identify potential areas for optimization.
- Patch Conflicts: Conflicts can arise when multiple patches attempt to modify the same system files. Careful planning and testing are crucial to prevent this. Utilize BigFix’s dependency analysis features to identify potential conflicts before deployment. Consider the order of patch deployment to mitigate conflicts. Always test patch deployments in a non-production environment before rolling them out to production systems.
- Client Communication Issues: If BigFix clients are unable to communicate with the server, check for firewall rules blocking communication on the necessary ports. Ensure that the BigFix client service is running on the target machines and that the server’s address is correctly configured in the client settings. Verify that DNS resolution is working correctly.
Frequently Asked Questions (FAQ)
This section addresses frequently asked questions concerning BigFix Extended Patch implementation and usage.
- Q: How do I integrate BigFix Extended Patch with our existing IT infrastructure? A: Integration depends on your existing systems. Common methods include using APIs for data exchange with other systems, such as ServiceNow or other ticketing systems, or integrating with existing monitoring tools. Careful planning is required to map your current systems to the BigFix Extended Patch workflow.
- Q: What security measures should I implement when using BigFix Extended Patch? A: Implement robust authentication and authorization mechanisms to control access to the BigFix console and manage user permissions. Regularly update the BigFix server and clients with the latest security patches. Employ strong passwords and enable multi-factor authentication where possible. Monitor for any unauthorized access attempts.
- Q: How can I track the progress of patch deployments? A: BigFix provides comprehensive reporting and monitoring capabilities. Use the BigFix console to monitor the progress of deployments in real-time, track the number of successful and failed deployments, and generate reports on patch deployment statistics. This allows for proactive management and troubleshooting.
- Q: What are the best practices for managing BigFix Extended Patch? A: Establish a clear patching schedule, prioritize critical patches, and thoroughly test patches in a non-production environment before deploying them to production. Regularly review and update your patch deployment strategies to adapt to changing needs and security threats. Implement proper change management procedures to ensure a smooth and controlled patching process.
Available Support Resources
Several resources are available to assist BigFix Extended Patch users.
- IBM Support: IBM provides comprehensive support options, including online documentation, knowledge bases, and direct technical support through various channels. These resources offer troubleshooting assistance, best practice guidance, and access to expert engineers.
- Online Communities: Engage with other BigFix users in online communities and forums to share experiences, ask questions, and find solutions to common problems. These communities provide a valuable resource for collaborative problem-solving and knowledge sharing.
- Third-Party Support: Many third-party vendors offer consulting and support services specifically for BigFix Extended Patch. These services can provide tailored assistance for complex deployments or specialized requirements.
Future Developments and Enhancements
BigFix Extended Patch has already proven its value in streamlining patch management for a wide range of third-party software. However, the ever-evolving landscape of technology demands continuous innovation. Looking ahead, several key areas present opportunities for significant enhancements and expansion of its capabilities. These enhancements would not only improve efficiency but also address emerging security challenges and better integrate with future IT infrastructures.The future of BigFix Extended Patch hinges on its ability to adapt to the rapid pace of technological change and the increasing complexity of modern IT environments.
This requires a proactive approach to development, focusing on areas such as improved automation, enhanced security features, and a more intuitive user experience. This will ensure that BigFix remains a leading solution in the ever-competitive patch management market.
Automated Patch Prioritization and Remediation
Intelligent automation is key to maximizing the efficiency of patch management. Future versions of BigFix Extended Patch could incorporate machine learning algorithms to prioritize patches based on vulnerability severity, software criticality, and potential impact on business operations. This would allow administrators to focus on the most pressing issues first, minimizing downtime and risk. For example, the system could automatically identify and remediate critical vulnerabilities in production systems before less critical updates on development servers.
This level of intelligent automation would drastically reduce manual intervention and improve overall responsiveness to security threats.
Support for Emerging Technologies and Software
The rapid growth of cloud-native applications, containerization (like Docker and Kubernetes), and serverless architectures necessitates that BigFix Extended Patch adapt to manage patches within these environments. This requires expanding its capabilities to identify and deploy patches for cloud-based services and containerized applications, seamlessly integrating with cloud platforms like AWS, Azure, and GCP. For instance, future development should include support for automatically updating container images with the latest security patches before deployment, enhancing the security posture of microservices.
Enhanced User Interface and User Experience
A streamlined and intuitive user interface is crucial for improving user adoption and maximizing the effectiveness of BigFix Extended Patch. Future improvements could include a modernized dashboard with improved visualization of patch deployment status, more robust reporting capabilities, and enhanced search functionality. A more user-friendly interface with clear, concise information presented in an accessible format will significantly reduce the learning curve for administrators, allowing them to manage patches more efficiently.
For example, a visual representation of patch deployment progress across different systems, with color-coded indicators for success and failure, would provide at-a-glance insight into the overall health of the system.
Conclusion
BigFix Extended Patch isn’t just another patch management tool; it’s a comprehensive solution designed to tackle the complexities of modern IT environments. By expanding remediation capabilities to hundreds of third-party applications, it offers unparalleled control and security. The ability to automate patching, integrate with other systems, and proactively mitigate vulnerabilities makes BigFix Extended Patch a must-have for organizations serious about their security.
This deep dive hopefully provides you with the information you need to evaluate and implement this powerful tool for your own organization. Ready to streamline your patching process and boost your security? Let’s get started!
FAQs
What types of third-party software does BigFix Extended Patch support?
BigFix Extended Patch supports a wide range of third-party software titles, encompassing various categories like productivity suites, enterprise resource planning (ERP) systems, and more. The specific list is constantly expanding.
How does BigFix Extended Patch handle updates for different operating systems?
It uses OS-specific agents to deliver and apply patches appropriately, ensuring compatibility and seamless integration across various platforms.
Is there a free trial or demo available for BigFix Extended Patch?
Contact IBM or your BigFix reseller to inquire about trial options and demos. Availability may vary depending on your region and licensing agreements.
What kind of reporting and analytics does BigFix Extended Patch offer?
BigFix Extended Patch provides detailed reporting and analytics on patch deployment, compliance, and remediation efforts, helping you track progress and identify areas for improvement.