BigFix Extended Patch for RHEL Streamlining Updates
BigFix Extended Patch for RHEL: Ever felt the headache of managing patches across your Red Hat Enterprise Linux servers? I know I have! This powerful tool promises a smoother, more efficient patching process, minimizing downtime and maximizing security. Let’s dive into how it works, its benefits, and why it might be the solution you’ve been searching for to tame your RHEL patching beast.
This post will cover everything from basic setup and deployment strategies to advanced customization and troubleshooting tips. We’ll explore best practices for minimizing disruption, ensuring compliance, and maximizing the security of your RHEL infrastructure. I’ll even share some real-world examples and lessons learned from my own experiences implementing BigFix.
BigFix Extended Patch for RHEL
BigFix Extended Patch for Red Hat Enterprise Linux (RHEL) offers a powerful and efficient solution for managing system updates across your RHEL infrastructure. It goes beyond basic patching capabilities, providing comprehensive control and automation to streamline the entire patch management lifecycle. This deep dive explores its features, benefits, and workflow.
Core Features of BigFix Extended Patch for RHEL
BigFix Extended Patch for RHEL leverages the robust BigFix platform to deliver automated patch deployment, remediation, and reporting. Key features include automated patch discovery and classification, targeted deployment to specific groups of systems, robust reporting and auditing capabilities, and integration with existing IT infrastructure. It supports various patch sources, allowing administrators to manage updates from Red Hat Satellite, local repositories, or other approved sources.
The system offers granular control over patch deployment, enabling administrators to schedule updates, approve or reject patches individually, and even roll back deployments if necessary. This level of control minimizes downtime and reduces the risk of deployment failures.
Benefits Compared to Standard Patching Methods
Standard patching methods, often involving manual processes or basic scripting, are prone to errors and inconsistencies. BigFix Extended Patch for RHEL provides several key advantages. Firstly, automation significantly reduces the time and effort required for patching, freeing up IT staff for other critical tasks. Secondly, its centralized management capabilities ensure consistent patch levels across the entire RHEL environment, improving overall system security.
Thirdly, the detailed reporting and auditing features offer comprehensive visibility into the patching process, aiding in compliance and troubleshooting. Finally, the ability to target specific systems or groups allows for more controlled and efficient deployments, reducing the risk of disrupting critical services.
Comparison with Other Patch Management Solutions
Compared to other patch management solutions, BigFix Extended Patch for RHEL distinguishes itself through its highly scalable architecture and robust agentless capabilities. While other solutions may rely on agents that consume significant system resources or require complex configurations, BigFix leverages its existing agent infrastructure for a lightweight and efficient approach. This minimizes the impact on system performance and simplifies deployment.
Furthermore, its deep integration with the BigFix platform allows for seamless integration with other IT management tools, creating a unified and streamlined management experience. For instance, unlike some solutions that may require separate tools for inventory management, BigFix provides a complete picture of your RHEL infrastructure, facilitating better decision-making.
Typical Patch Deployment Workflow
A typical patch deployment using BigFix Extended Patch for RHEL follows a structured workflow. First, the system scans for available patches based on configured repositories. Then, administrators review and approve the patches, selecting the target systems or groups for deployment. Next, the deployment is scheduled, with options for immediate or delayed rollout. BigFix then distributes the patches to the target systems, initiating the update process.
During deployment, BigFix monitors the progress and provides real-time feedback. Finally, the system generates comprehensive reports detailing the success or failure of each patch installation, allowing for efficient troubleshooting and remediation of any issues. This entire process is logged and audited, ensuring compliance and providing a detailed history of all patching activities.
Patch Deployment Process and Best Practices
Successfully deploying patches across your RHEL infrastructure using BigFix Extended Patch is crucial for maintaining system security and stability. This requires a well-defined process and adherence to best practices to minimize disruption and maximize efficiency. This section Artikels a robust approach to patch deployment, encompassing configuration, deployment strategies, and pre- and post-deployment checks.
BigFix Extended Patch for RHEL Configuration
Configuring BigFix Extended Patch for RHEL involves several key steps. First, ensure your BigFix infrastructure is correctly set up and functioning. This includes verifying the connection between your BigFix server and the RHEL clients. Next, you’ll need to create relevant patch deployment targets. This might involve grouping clients based on operating system versions, roles, or criticality.
The next critical step is to define your patch baseline. This specifies which patches should be deployed, and potentially, the order of deployment. Finally, schedule your patch deployments. Consider deploying patches outside of peak business hours to minimize disruption. Remember to thoroughly test your deployment process in a non-production environment before applying it to your live systems.
Strategies for Minimizing Downtime During Patch Deployment
Minimizing downtime is paramount during patch deployments. One effective strategy is to utilize phased rollouts. This involves deploying patches to a small subset of your systems initially, allowing you to monitor for any unexpected issues before deploying to the entire environment. Another crucial technique is to leverage BigFix’s capabilities for reboots. BigFix allows you to schedule reboots strategically, minimizing the impact on user productivity.
Careful selection of the patch deployment window is also essential; consider off-peak hours or weekends to minimize disruption. Employing robust monitoring and alerting is also vital. BigFix provides tools to monitor the deployment progress and send alerts in case of failures, enabling timely intervention. Finally, thorough testing of the patches in a staging environment before deploying to production is a critical step in minimizing the risk of downtime.
Pre- and Post-Deployment Checklist for BigFix Extended Patch for RHEL
A comprehensive checklist ensures a smooth and successful patch deployment.
Pre-Deployment Checklist:
- Verify BigFix server and client connectivity.
- Create appropriate client target groups.
- Define the patch baseline, including relevant patches and their deployment order.
- Test the deployment process in a non-production environment.
- Schedule the deployment outside of peak business hours.
- Communicate the deployment schedule to relevant stakeholders.
- Back up critical system data.
Post-Deployment Checklist:
- Verify the successful deployment of patches on all target systems.
- Monitor system logs for any errors or warnings.
- Check system performance metrics to ensure no degradation after the patch deployment.
- Document the deployment process and results.
- Review and update the patch management strategy based on the deployment results.
Security Considerations and Vulnerability Management
Keeping your RHEL systems patched is paramount for maintaining a secure environment. Outdated systems are vulnerable to a wide range of exploits, from simple data breaches to complete system compromises. BigFix Extended Patch for RHEL offers a powerful solution to address these risks, but understanding the security implications and implementing robust strategies is crucial.BigFix mitigates security risks associated with outdated RHEL patches by providing a centralized, automated patching process.
This eliminates the manual effort and potential human error associated with traditional patching methods, ensuring consistent and timely updates across your entire infrastructure. By identifying vulnerable systems and deploying patches automatically, BigFix minimizes the window of vulnerability, reducing the likelihood of successful attacks. Furthermore, BigFix’s reporting capabilities allow administrators to track patching progress, identify gaps in coverage, and proactively address potential security issues.
Potential Security Risks of Outdated RHEL Patches
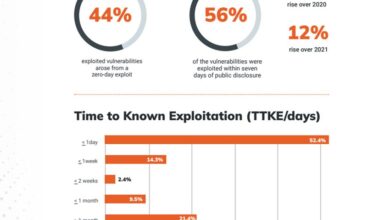
Outdated RHEL patches expose systems to a variety of known vulnerabilities. These vulnerabilities can be exploited by malicious actors to gain unauthorized access, steal sensitive data, disrupt services, or even take complete control of the affected systems. The severity of these risks varies depending on the specific vulnerabilities involved, but the consequences can be significant, ranging from minor inconveniences to substantial financial losses and reputational damage.
Examples include the Heartbleed vulnerability (CVE-2014-0160), which allowed attackers to steal sensitive data from affected systems, and Shellshock (CVE-2014-6271), which enabled remote code execution. The timely application of patches is therefore crucial to mitigate these risks.
Implementing Robust Security Measures with BigFix Extended Patch for RHEL
Beyond simply deploying patches, a comprehensive security strategy is necessary. This involves implementing strong access controls, regularly auditing system configurations, and maintaining robust network security measures. BigFix Extended Patch for RHEL integrates well with other security tools and practices. For example, combining BigFix with intrusion detection and prevention systems (IDPS) provides a layered security approach. BigFix ensures systems are patched, while the IDPS monitors for malicious activity, providing a more comprehensive security posture.
Regular security assessments and penetration testing are also recommended to identify and address potential vulnerabilities that may not be covered by standard patching.
BigFix Extended Patch for RHEL’s Role in Vulnerability Management
BigFix Extended Patch for RHEL plays a central role in vulnerability management by automating the patch deployment process. It identifies vulnerable systems, downloads the necessary patches, and deploys them according to pre-defined schedules or policies. This proactive approach minimizes the window of vulnerability, significantly reducing the risk of exploitation. Furthermore, BigFix provides detailed reporting and analytics, enabling administrators to track the patching status of their systems, identify any outstanding vulnerabilities, and measure the effectiveness of their vulnerability management program.
This allows for continuous improvement and proactive risk mitigation.
Comparison of BigFix Extended Patch for RHEL with Other Security Solutions
Compared to other security solutions, BigFix Extended Patch for RHEL offers a unique combination of automation, scalability, and centralized management. While other solutions might focus on specific aspects of security, such as antivirus or firewall management, BigFix provides a comprehensive patching solution specifically tailored for RHEL systems. This centralized approach simplifies the management of updates across large and complex IT infrastructures, which can be challenging with standalone or disparate security tools.
The ability to create and enforce custom patch deployment policies further strengthens its position as a robust and adaptable vulnerability management tool.
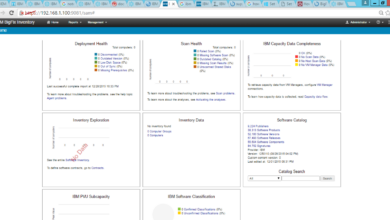
Integration and Reporting Capabilities

BigFix Extended Patch for RHEL offers robust integration capabilities, allowing seamless interaction with your existing IT infrastructure and providing comprehensive reporting on patch deployment status. This integration streamlines your patching workflow and enhances visibility into your security posture. Effective reporting is crucial for compliance auditing and proactive vulnerability management.Integrating BigFix with other IT management tools significantly improves efficiency and reduces manual effort.
This integration allows for centralized monitoring and management of your entire IT environment, fostering a more streamlined and proactive approach to system maintenance and security.
BigFix Integration with Other IT Management Tools
BigFix’s open architecture allows for integration with a variety of IT management tools through APIs and custom scripts. For example, it can integrate with ServiceNow for incident management, integrating patch deployment status directly into your ticketing system. This enables automated updates on ticket resolution, streamlining communication and tracking. Another example is integration with monitoring tools like Nagios or Zabbix, where BigFix can provide real-time patch deployment data, enriching the overall system health monitoring.
This allows administrators to proactively identify potential issues related to patching and address them before they escalate. Custom scripts can further extend these integrations to meet specific organizational needs.
Custom Reporting for Patch Deployment Status
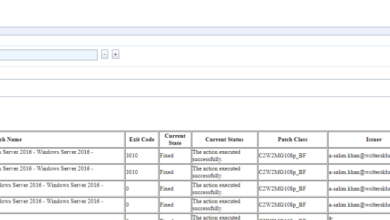
BigFix offers powerful reporting capabilities, allowing administrators to create custom reports tailored to their specific needs. To monitor patch deployment status, reports can be created to show the number of systems patched, the number of systems requiring patching, and the overall patch deployment success rate. These reports can be scheduled to run automatically and distributed to relevant stakeholders.
For instance, a report could show the percentage of systems that have successfully installed a specific security patch within a defined timeframe. Another report might highlight systems that have failed to install patches, along with the reasons for failure. This level of granular detail is invaluable for identifying and resolving deployment issues.
Key BigFix Extended Patch for RHEL Reporting Metrics
The following table summarizes key reporting metrics provided by BigFix Extended Patch for RHEL:
| Metric | Description | Data Type | Example Value |
|---|---|---|---|
| Patches Deployed | Number of patches successfully deployed | Integer | 150 |
| Systems Patched | Number of systems that have received the patches | Integer | 200 |
| Patch Deployment Success Rate | Percentage of successful patch deployments | Percentage | 95% |
| Average Patch Deployment Time | Average time taken to deploy a patch | Time (e.g., HH:MM:SS) | 00:15:30 |
BigFix Reporting for Compliance Auditing
BigFix reporting features are invaluable for compliance auditing. By generating reports on patch compliance, organizations can demonstrate their adherence to industry standards and regulatory requirements. Reports can show which systems are compliant with specific patch policies, highlighting any non-compliant systems and the reasons for non-compliance. This information is crucial for demonstrating compliance to auditors and for proactively addressing any vulnerabilities that might put the organization at risk.
For example, a report could be generated showing compliance with PCI DSS standards by demonstrating that all systems handling sensitive payment information have the required security patches installed. This provides verifiable evidence for audits and helps organizations maintain a strong security posture.
Troubleshooting and Common Issues
Deploying BigFix Extended Patch for RHEL can sometimes present challenges. This section Artikels common problems encountered during deployment and offers practical solutions to get your patching process back on track. Understanding these potential issues and their solutions is crucial for maintaining a secure and up-to-date system environment.
Common Deployment Issues and Solutions
Several factors can hinder successful BigFix Extended Patch for RHEL deployment. These range from network connectivity problems to incorrect configuration settings. Addressing these issues proactively minimizes downtime and ensures efficient patch management.
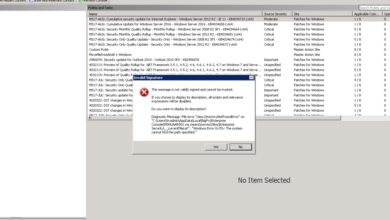
- Network Connectivity Problems: Insufficient network bandwidth or firewall restrictions can prevent BigFix clients from communicating with the server, hindering patch downloads and installations. Solutions involve verifying network connectivity, adjusting firewall rules to allow BigFix traffic (typically ports 52311 and 52312), and optimizing network bandwidth allocation. Consider using a dedicated network segment for BigFix communication if bandwidth is a major concern.
- Incorrect BigFix Configuration: Improperly configured BigFix actions or relevance statements can lead to patches failing to deploy to the intended target systems. Review the BigFix action scripts and relevance statements meticulously. Ensure they correctly identify the target systems and the specific patches to be installed. Utilize BigFix’s logging capabilities to identify the precise point of failure.
- Insufficient Disk Space: Insufficient disk space on the target RHEL systems can prevent patch installation. Regularly monitor disk space usage on managed systems. Implement automated alerts or proactive measures to address low disk space conditions before they impact patch deployments. Regularly cleaning up temporary files and unused packages can also help.
- Permission Issues: Lack of appropriate user permissions can block patch installation. Ensure the BigFix client runs with sufficient privileges to install software packages and modify system files. Review the user account and group memberships associated with the BigFix client.
- Patch Download Failures: Issues with the BigFix patch repository or corrupted patch files can cause download failures. Verify the integrity of the patch files in the repository. If necessary, re-download the patches to ensure they are not corrupted. Regularly check the health of the repository and implement error handling mechanisms in the BigFix actions to manage failed downloads gracefully.
Troubleshooting Patch Deployment Failures
Effective troubleshooting involves a systematic approach to identify the root cause of patch deployment failures. This involves analyzing BigFix logs, examining the system’s state, and systematically testing potential solutions.
- Review BigFix Logs: BigFix provides detailed logs that track patch deployment activities. Analyze these logs to pinpoint the exact point of failure. Look for error messages, warnings, and other relevant information. This detailed information provides invaluable clues for troubleshooting.
- Check System Logs: Examine the system logs on the affected RHEL systems (e.g., `/var/log/messages`, `/var/log/yum.log`) for additional error messages related to the patch installation process. These logs often contain clues that are not visible in the BigFix logs.
- Verify Network Connectivity: Ensure the affected RHEL system has proper network connectivity to the BigFix server and the internet (if patches are downloaded from an external source). Use tools like `ping` and `traceroute` to diagnose network issues.
- Test Patch Installation Manually: Attempt to manually install the problematic patch on an affected system to rule out BigFix-specific issues. This helps isolate whether the problem lies within BigFix or the patch itself.
- Isolate the Problem: Try deploying the patch to a smaller subset of systems to determine if the problem is isolated to specific systems or a broader issue. This helps to narrow down the scope of the problem and make it easier to resolve.
Troubleshooting Flowchart
A visual flowchart can greatly aid in systematic troubleshooting. While a visual representation cannot be included here, a textual representation of a flowchart follows:Start -> Check BigFix Logs -> Check System Logs -> Verify Network Connectivity -> Test Manual Patch Installation -> Isolate Problem -> Identify Root Cause -> Implement Solution -> Verify Solution -> End. Each step would ideally branch to appropriate actions based on the results.
For example, if network connectivity is an issue, the next steps might involve checking firewall rules, network cables, and DNS resolution.
Optimizing BigFix Extended Patch for RHEL Performance
Optimizing BigFix for RHEL patch deployment improves efficiency and reduces the impact on system resources.
- Schedule Patch Deployments: Avoid deploying patches during peak usage hours to minimize disruption. Schedule deployments for off-peak times to reduce the impact on system performance and user productivity. This can be easily managed within the BigFix console.
- Optimize Relevance Statements: Well-crafted relevance statements precisely target systems requiring patches, minimizing unnecessary scans and deployments. Carefully define the target systems to avoid unnecessary work and resource consumption.
- Utilize Patch Remediation: Leverage BigFix’s built-in remediation capabilities to automatically fix issues discovered during patching, streamlining the process and reducing manual intervention. This automated approach significantly improves efficiency and reduces the potential for human error.
- Regularly Maintain the BigFix Server: Regular maintenance of the BigFix server, including updates and performance tuning, ensures optimal operation and efficient patch deployment. Regular server maintenance is crucial for ensuring reliability and optimal performance.
- Monitor Resource Usage: Regularly monitor the resource utilization (CPU, memory, disk I/O) of the BigFix server and clients to identify and address any performance bottlenecks. This proactive monitoring helps identify and resolve performance issues before they significantly impact patch deployment.
Advanced Usage and Customization: Bigfix Extended Patch For Rhel
BigFix Extended Patch for RHEL offers a powerful, yet flexible, patching solution. Beyond the basic deployment, significant customization is possible to align perfectly with your organization’s unique infrastructure and security policies. This section delves into advanced features and techniques to maximize its potential.
The core of this customization lies in leveraging BigFix’s robust scripting capabilities. By understanding the underlying architecture and available actions, administrators can tailor patching schedules, target specific systems based on complex criteria, and automate remediation processes that go beyond the standard patch deployment.
Customizing Patch Selection and Deployment
The default patch selection criteria might not always suffice. For example, you might need to exclude specific patches based on internal testing results or integrate with your change management system. BigFix allows you to refine the patch selection process using relevance statements and custom actions. These statements can filter patches based on various attributes such as severity level, release date, or even custom metadata added during your internal testing process.
This level of control prevents unwanted or untested patches from being deployed to production systems.
Advanced BigFix Scripting for Patch Management
BigFix scripting, using the Relevance language, allows for intricate automation. Imagine a scenario where a specific patch requires a reboot, but you want to schedule this reboot only during off-peak hours. A custom BigFix action can check the system time, compare it against your defined maintenance window, and then trigger the reboot only if the conditions are met.
This is far more sophisticated than relying solely on the default deployment settings.
Another example involves automatically creating detailed reports post-patch deployment. A script can gather information such as successful patch installations, failed installations, and any errors encountered. This information can then be formatted into a custom report, emailed to administrators, or integrated with your existing monitoring system. This enhances visibility and allows for proactive issue resolution.
Here’s a simplified example of a BigFix relevance statement to target only servers running a specific version of Apache:
exists version of it whose (name = "Apache" and version = "2.4.52")
This statement, when used within a fixlet, will only target systems meeting this criteria, allowing for precise and targeted patch deployment.
Scenario: Patch Management in a Complex IT Environment
Consider a large enterprise with a heterogeneous environment including physical servers, virtual machines, and cloud instances. BigFix Extended Patch for RHEL can manage patching across this entire landscape. Different groups of systems might have varying security policies and maintenance windows. Using BigFix’s capabilities, you can create separate target groups for each environment (e.g., production servers, development servers, cloud instances).
You can then define specific patch schedules and deployment strategies for each group. Furthermore, you can leverage custom actions to perform pre- and post-patch validation checks, ensuring system stability and data integrity.
For example, before deploying a critical security patch to production servers, a custom action could run a series of system checks (memory usage, disk space, network connectivity) to ensure the servers are in a healthy state. After the patch is applied, another action could verify the patch’s successful installation and perform additional system checks to confirm functionality.
Final Review
Managing RHEL patches doesn’t have to be a nightmare. BigFix Extended Patch offers a robust and efficient solution for streamlining the entire process, from initial configuration to ongoing maintenance. By leveraging its features and following best practices, you can significantly reduce your risk exposure, improve system stability, and free up valuable IT resources. Ready to ditch the manual patching headaches?
Let’s get started!
FAQ Resource
What is the difference between BigFix and other patch management solutions?
BigFix distinguishes itself through its agentless architecture, allowing for centralized management of a vast number of systems. Other solutions may rely on more complex or less scalable approaches.
How does BigFix handle patching for different RHEL versions?
BigFix is designed to handle patching across various RHEL versions, adapting its approach based on the specific OS version and its associated vulnerabilities.
Can BigFix integrate with our existing monitoring tools?
Yes, BigFix offers robust integration capabilities with various IT management and monitoring tools, allowing for centralized reporting and management.
What kind of reporting does BigFix provide?
BigFix provides detailed reports on patch deployment status, compliance levels, and other key metrics, helping you track progress and identify potential issues.