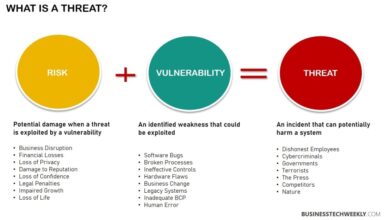
Apple iOS 12 Best Mobile Security Ever
Apple iOS 12 has the best mobile security features ever, a bold claim, but one backed by significant advancements in data protection, app security, and hardware enhancements. This wasn’t just an incremental update; iOS 12 represented a substantial leap forward in safeguarding user information and privacy. We’ll delve into the specifics, exploring how Apple significantly improved upon previous versions and outpaced competitors in securing the mobile landscape.
From enhanced encryption methods to a refined app permission model and the powerful Secure Enclave, iOS 12 offered a comprehensive security architecture. This post will dissect the key features, compare them to Android counterparts and previous iOS iterations, and highlight the innovative approaches Apple took to address emerging threats and bolster user privacy.
iOS 12 Security Features Overview

iOS 12 represented a significant leap forward in mobile security, building upon the strong foundation laid by its predecessors. While boasting many incremental improvements, several key features solidified its position as a leader in mobile device protection at the time of its release. This overview will detail those core features and highlight the advancements compared to earlier iOS versions.
Core Security Features in iOS 12
iOS 12 incorporated several crucial security enhancements. These included strengthened data encryption, improved protection against phishing attacks, and enhanced app sandboxing. The operating system leveraged hardware-level security features to protect user data, ensuring that even if a device was compromised, sensitive information remained relatively secure. Furthermore, iOS 12 refined its existing mechanisms for managing user permissions, giving users more granular control over which apps could access specific data like location services, contacts, and photos.
This granular control minimized the potential impact of compromised or malicious applications.
Improvements Compared to Previous iOS Versions
iOS 12 built upon the security architecture of previous versions, refining existing features and introducing new ones. For example, improvements to the built-in anti-phishing capabilities were substantial. iOS 12’s more robust detection algorithms and improved warning mechanisms provided users with better protection against sophisticated phishing attempts. Additionally, the system’s app sandboxing was further enhanced, limiting the potential damage from compromised apps by restricting their access to other parts of the system.
Previous iOS versions had strong security, but iOS 12 focused on making these protections more intelligent and proactive, responding more effectively to evolving threats.
Comparison of iOS 12 and Contemporary Android Versions
The following table compares the security features of iOS 12 with those of contemporary Android versions (around the same release period). It’s important to note that security landscapes are constantly evolving, and direct feature-to-feature comparisons can be complex. This table offers a high-level overview for illustrative purposes.
| Feature | iOS 12 | Android (e.g., Android 9 Pie) |
|---|---|---|
| Data Encryption | Hardware-level encryption at rest and in transit; strong key management. | Full-disk encryption available, but implementation varied across devices and manufacturers; key management complexities. |
| App Sandboxing | Robust app sandboxing with strict limitations on inter-app communication and access to system resources. | App sandboxing implemented, but enforcement and consistency varied across Android versions and device manufacturers. |
| Phishing Protection | Improved phishing detection algorithms and warning mechanisms integrated into Safari and system-wide. | Relied on individual browser and app-level protections, with varying levels of effectiveness across different platforms. |
| Security Updates | Regular, over-the-air security updates directly from Apple, ensuring timely patching of vulnerabilities. | Update schedules varied significantly depending on the device manufacturer and carrier. |
Data Protection in iOS 12
iOS 12 represented a significant leap forward in mobile security, boasting robust data protection mechanisms both for data at rest and data in transit. This enhanced security aimed to safeguard user information from unauthorized access and breaches, building upon the already strong security foundation of previous iOS versions. The implementation of various encryption techniques and security protocols provided a multi-layered defense against potential threats.Data encryption in iOS 12 was a core component of its security architecture.
This involved the use of strong encryption algorithms to scramble user data, making it unreadable without the correct decryption key. This protection applied not only to data stored on the device itself (data at rest) but also to data transmitted to and from the device (data in transit). This dual approach ensured a comprehensive level of protection throughout the data lifecycle.
Data Encryption at Rest and in Transit
iOS 12 employed advanced encryption standards to protect user data. Data at rest, meaning data stored on the device’s internal storage, was encrypted using hardware-level AES-256 encryption. This means the encryption process was handled by a dedicated security chip within the device, offering a high level of protection against physical attacks. For data in transit, iOS 12 utilized TLS 1.2 (or later) to secure communication between the device and Apple’s servers, as well as other secure servers.
This protocol encrypts data during transmission, preventing eavesdropping and data interception. The combination of strong encryption at both rest and in transit significantly reduced the risk of data compromise.
Examples of iOS 12 Data Protection
Imagine a scenario where an iPhone running iOS 12 is lost or stolen. Even if a malicious actor gains physical access to the device, the data remains encrypted. Without the correct passcode or biometric authentication, the attacker cannot access the encrypted data. Similarly, when a user accesses their email or banking app, the data transmitted between the device and the server is encrypted using TLS, preventing interception by third parties.
This dual-layered approach, protecting both stored and transmitted data, forms the bedrock of iOS 12’s security.
Types of Data Protected and Their Methods
The importance of understanding the different types of data protected by iOS 12 and the methods employed cannot be overstated. A comprehensive approach is crucial for effective security.
- Passwords and Passcodes: Protected by Secure Enclave, a dedicated hardware component resistant to software attacks. The Secure Enclave handles cryptographic operations and key management, preventing unauthorized access to stored credentials.
- Health Data: Encrypted both at rest and in transit using AES-256. Users can further enhance security by enabling a passcode or biometric authentication to access the Health app.
- Photos and Videos: Encrypted at rest using AES-256. iCloud Photo Library, if enabled, offers additional layers of encryption during cloud storage and transmission.
- Messages: End-to-end encryption for iMessages, protecting the content from being read by Apple or third parties. This means only the sender and recipient can access the message content.
- Location Data: Precise location data is not constantly transmitted; instead, location services utilize differential privacy techniques to aggregate location information while protecting individual user privacy.
App Security and Permissions in iOS 12

iOS 12 significantly enhanced app security by refining its permission model and strengthening app sandboxing. This resulted in a more robust system for protecting user data and preventing malicious software from wreaking havoc. The improvements focused on providing users with greater control over what data apps could access and limiting the potential damage from compromised applications.
The app permission model in iOS 12 operates on a principle of least privilege. This means that apps only receive access to the specific data they require to function, and only when explicitly granted permission by the user. This contrasts with earlier systems where apps might request broad access rights, potentially allowing them to collect and misuse more data than necessary.
iOS 12’s refined approach dramatically reduced the attack surface for malicious apps, making data breaches significantly less likely.
App Sandboxing Enhancements, Apple ios 12 has the best mobile security features ever
iOS 12 built upon the existing app sandboxing architecture, making it even more effective at containing malicious app behavior. Sandboxing isolates each app within its own controlled environment, preventing it from accessing the resources or data of other apps, or the underlying operating system. Key improvements in iOS 12 included more stringent restrictions on inter-process communication and enhanced monitoring for suspicious activity.
For example, attempts by an app to access files outside its designated sandbox would be immediately blocked, and the operating system would alert the user. This proactive approach minimizes the impact of compromised apps, preventing widespread system compromise.
Granting and Revoking App Permissions
The process of granting and revoking app permissions in iOS 12 was streamlined for user clarity and control. When an app requests access to sensitive data, such as location services, contacts, or photos, the user receives a clear and concise prompt explaining exactly what data the app is requesting and why. Users could then choose to grant or deny access.
Furthermore, users could easily review and modify previously granted permissions at any time through the Settings app. This allows users to maintain complete control over their data and revoke access from apps that are no longer trusted or needed. For instance, if a user discovers an app is using location services unnecessarily, they can quickly disable this permission, preventing further location tracking.
Okay, so Apple iOS 12 boasted some seriously impressive security features – I still think it’s up there with the best. Building secure apps is crucial, and that’s where understanding the development landscape comes in. Check out this article on domino app dev the low code and pro code future to see how developers are tackling this.
Ultimately, robust security, like iOS 12 offered, needs to be a priority from the ground up in app development.
Hardware Security Enhancements in iOS 12
iOS 12 built upon the strong security foundation of its predecessors, incorporating significant hardware-level enhancements to bolster its defenses against both software and physical attacks. These improvements, largely centered around the Secure Enclave and other specialized hardware components, ensured a more robust and tamper-resistant environment for user data and sensitive operations.The Secure Enclave plays a pivotal role in safeguarding sensitive information.
This dedicated hardware component, isolated from the main processor, provides a trusted execution environment for cryptographic operations, key management, and other security-critical tasks. In iOS 12, the Secure Enclave’s capabilities were further refined to enhance protection against sophisticated attacks, including those targeting the device’s software or attempting to extract cryptographic keys. This isolation prevents malicious software from accessing sensitive data even if the main system is compromised.
Secure Enclave Functionality in iOS 12
The Secure Enclave in iOS 12 devices handled several crucial security functions. It protected Touch ID and Face ID biometric data, ensuring that these sensitive authentication factors remained inaccessible to unauthorized parties, even in the event of a jailbreak or other system compromise. Furthermore, it managed encryption keys used to protect user data stored on the device, preventing unauthorized access to sensitive information like messages, photos, and other personal files.
The Secure Enclave’s isolated and tamper-resistant nature made it a critical component in the overall security architecture of iOS 12.
Hardware-Level Protections Against Physical Attacks
iOS 12 devices implemented various hardware-level measures to deter physical attacks. These included features designed to make it extremely difficult for attackers to extract data through physical manipulation or unauthorized access. For example, the devices employed advanced memory encryption techniques to protect data at rest and in transit, even if the device was physically compromised. This meant that even if an attacker gained physical access, retrieving the encrypted data would be computationally infeasible without the correct decryption keys, securely stored within the Secure Enclave.
Additionally, specialized hardware sensors detected attempts at tampering or unauthorized access, triggering security protocols such as data erasure to prevent data theft.
Comparison of Hardware Security Features
A direct comparison of iOS 12’s hardware security features with competing platforms at the time reveals some key distinctions. While precise details about competitor implementations are often proprietary, a general comparison based on publicly available information can be made.
| Feature | iOS 12 | Android (circa 2018) | Windows Mobile (circa 2018) |
|---|---|---|---|
| Secure Enclave/TEE | Dedicated, isolated hardware for cryptographic operations and key management. | TEE implementation varied widely across manufacturers and devices, often less robustly isolated. | Limited TEE capabilities; security largely reliant on software solutions. |
| Memory Encryption | Full-disk encryption with hardware-accelerated AES encryption. | Varied across manufacturers and devices; often relied on software encryption with hardware acceleration varying. | Hardware-assisted encryption available but implementation details varied significantly. |
| Tamper Detection | Hardware sensors detected physical tampering attempts. | Tamper detection varied greatly across manufacturers; some devices had basic features, others lacked robust hardware-based detection. | Limited hardware-based tamper detection; primarily relied on software-based methods. |
iOS 12’s Response to Emerging Threats: Apple Ios 12 Has The Best Mobile Security Features Ever
iOS 12, released in September 2018, faced a landscape of evolving cyber threats. Its security improvements weren’t just incremental; they actively addressed vulnerabilities discovered in previous iOS versions and anticipated emerging attack vectors. This proactive approach was crucial in maintaining a strong security posture against increasingly sophisticated malicious actors.The development and deployment of iOS 12 security updates reflected Apple’s commitment to rapid response and continuous improvement.
Addressing vulnerabilities promptly minimized the window of opportunity for exploitation, protecting users from potential data breaches and system compromises. This involved a multi-pronged approach including regular software updates, enhanced detection mechanisms, and improvements to existing security features.
Specific Vulnerabilities Addressed in iOS 12 Updates
iOS 12’s security updates tackled a range of vulnerabilities, many of which were publicly disclosed through responsible disclosure programs or discovered internally by Apple’s security teams. These vulnerabilities spanned various aspects of the iOS ecosystem, including kernel exploits, web browser flaws, and issues related to third-party applications. For example, several updates patched vulnerabilities that could allow malicious apps to bypass security restrictions and gain unauthorized access to user data or system resources.
Another key focus was on addressing vulnerabilities in the WebKit engine, the rendering engine used by Safari, to prevent exploitation through malicious websites.
Examples of iOS 12 Security Updates and Their Impact
One significant example is iOS 12.1.1, released in January 2019, which addressed several critical vulnerabilities, including one that could have allowed a malicious application to execute arbitrary code with kernel privileges. This update significantly reduced the risk of a complete system compromise. Similarly, iOS 12.1.2 and subsequent updates continued to patch vulnerabilities, improving the overall resilience of the operating system against known exploits.
The impact of these updates was a noticeable reduction in the number of successful attacks reported against iOS devices running iOS 12, although precise figures are difficult to obtain due to the private nature of many security incidents.
Timeline of Significant iOS 12 Security Patches
The following timeline illustrates the release of key iOS 12 security updates and the types of threats they addressed. It’s important to note that this is not an exhaustive list, as numerous smaller updates also contributed to the overall security posture.
| Date | iOS Version | Vulnerabilities Addressed |
|---|---|---|
| September 2018 | iOS 12.0 | Initial release with numerous security enhancements, laying the groundwork for future updates. Addressed vulnerabilities present in previous iOS versions. |
| October 2018 | iOS 12.0.1 | Addressed several minor vulnerabilities, improving stability and security. |
| January 2019 | iOS 12.1.1 | Addressed critical kernel vulnerabilities that could allow arbitrary code execution. |
| February 2019 | iOS 12.1.2 | Addressed additional vulnerabilities related to WebKit and other system components. |
| March 2019 | iOS 12.1.4 | Focused on further enhancements to system security and stability. Specific vulnerability details often remain undisclosed for security reasons. |
User Privacy in iOS 12
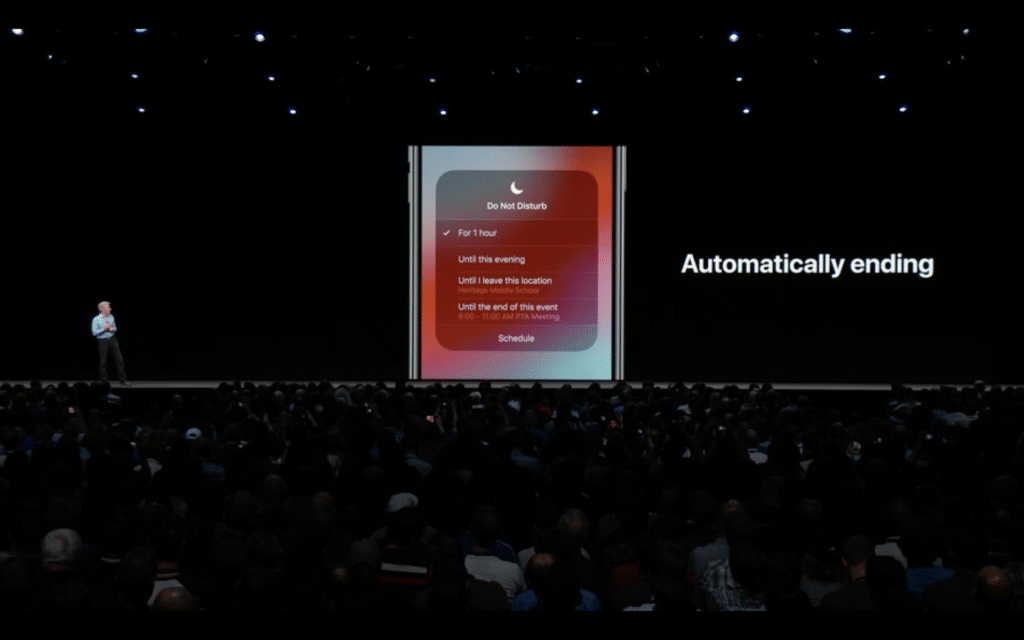
iOS 12 represented a significant leap forward in Apple’s commitment to user privacy. Building on previous iterations, iOS 12 introduced several refinements and new features designed to give users greater control over their data and limit the collection of personal information without explicit consent. This wasn’t just about adding checkboxes; it was about fundamentally altering how apps interacted with sensitive user data.
The core philosophy behind iOS 12’s privacy enhancements was transparency and user empowerment. Apple aimed to make it clear what data was being accessed, by whom, and why, giving users the agency to decide whether that access was acceptable. This involved not only providing granular control over settings but also actively working to prevent data collection through clever design and technological safeguards.
Location Services Management
iOS 12 provided significantly improved management of location services. Users could now choose to grant apps access to their location only while using the app (“While Using the App”), rather than always (“Always”). This reduced the potential for apps to track user movements even when not actively in use. Furthermore, iOS 12 introduced more precise controls, allowing users to specify location access on a per-app basis, and to easily review which apps had recently requested location data.
This level of granularity allowed users to tailor their privacy settings to their comfort levels with each individual application.
Ad Tracking Limitations
iOS 12 strengthened its limitations on ad tracking. While previous versions had already implemented measures to restrict cross-app tracking, iOS 12 further refined these mechanisms, making it more difficult for advertisers to build detailed profiles of users’ online behavior across different apps and websites. This involved limiting the sharing of unique device identifiers and strengthening the restrictions on the use of cookies and other tracking technologies.
The result was a more private browsing experience, reducing the potential for targeted advertising based on sensitive personal data.
Control of Data Privacy Settings
iOS 12 consolidated and simplified access to privacy settings. The Settings app offered a centralized location for managing various privacy aspects, including location services, contacts, photos, microphone access, and more. This made it easier for users to understand and adjust their privacy preferences without having to navigate through multiple menus. Furthermore, clear and concise descriptions accompanied each setting, ensuring users understood the implications of their choices.
The simplified interface aimed to empower even less tech-savvy users to take control of their data privacy.
Preventing Data Collection Without User Consent
iOS 12 employed several mechanisms to prevent unauthorized data collection. Enhanced restrictions on background processes minimized the opportunity for apps to collect data without user knowledge or consent. The system also actively monitored app behavior, flagging suspicious activity that might indicate unauthorized data access. This proactive approach, combined with the granular control offered to users, significantly reduced the risk of data breaches and privacy violations.
Apple’s commitment to privacy wasn’t merely reactive; it was proactive, anticipating potential threats and building defenses into the operating system itself.
Comparative Analysis of iOS 12 Security (vs. other iOS versions and Android)
iOS 12 represented a significant step forward in mobile security, building upon the strengths of its predecessors while addressing some lingering weaknesses. Comparing it to both earlier iOS versions and contemporary Android releases reveals its unique position in the mobile OS security landscape. This analysis highlights key improvements and remaining challenges.
Direct comparison between operating systems is complex due to the constantly evolving threat landscape and the inherent differences in their architectures. However, focusing on specific security features allows for a more meaningful assessment.
iOS 12 Security Enhancements Compared to iOS 11 and Android
| Feature | iOS 12 | iOS 11 | Android (Contemporary Versions) |
|---|---|---|---|
| Improved App Sandboxing | Further refined app isolation, limiting data access and preventing unauthorized communication between apps. | Strong sandboxing, but with some identified vulnerabilities exploited in previous versions. | Sandboxing implemented, but with a history of vulnerabilities depending on the specific Android version and device manufacturer’s implementation. Consistency is a challenge. |
| Enhanced Data Protection | Strengthened encryption algorithms and key management for data at rest and in transit. Improved handling of sensitive data like biometric information. | Good data protection, but iOS 12 offered improvements in encryption strength and key management practices. | Varied levels of data protection across different Android versions and device manufacturers. Encryption is often dependent on device settings and user choices. |
| Hardware Security Enhancements | Further integration of Secure Enclave for enhanced key protection and cryptographic operations. Improved tamper detection mechanisms. | Secure Enclave present, but iOS 12 included architectural improvements to enhance its resilience against attacks. | Hardware security varies greatly depending on the device manufacturer and the specific chipsets used. Generally less standardized than iOS. |
| Improved Threat Detection and Response | More proactive threat detection and mitigation through improved machine learning and updated security updates. | Reactive threat response, improvements in iOS 12 made it more proactive. | Android’s threat detection and response mechanisms rely heavily on Google Play Protect and individual device manufacturers’ security solutions. Effectiveness varies significantly. |
Limitations and Weaknesses in iOS 12 Security
While iOS 12 represented a significant advancement, it wasn’t without limitations. One area of ongoing concern is the reliance on user behavior and awareness. Phishing attacks and social engineering remain effective regardless of the underlying operating system security. Furthermore, while the Secure Enclave provides robust protection, vulnerabilities in other parts of the system could still be exploited to compromise the overall security.
Another limitation stems from the relatively closed ecosystem of iOS. While this limits the potential attack surface in some ways, it also restricts independent security audits and the rapid dissemination of security patches compared to the more open nature of Android. This makes the discovery and patching of zero-day vulnerabilities a potentially slower process.
Illustrative Example of iOS 12 Security Mechanism
Let’s consider a scenario involving Sarah, a busy professional who uses her iPhone extensively for both personal and work communications. She relies heavily on email, messaging apps, and cloud storage for accessing sensitive documents. This scenario will highlight how iOS 12’s App-Specific Passwords protected her data from a potential breach.Sarah uses a password manager to generate and store strong, unique passwords for all her online accounts.
However, she also uses several different apps that access her cloud storage. One day, Sarah receives a phishing email seemingly from her bank. The email contains a link to a fraudulent website designed to mimic her bank’s login page.
App-Specific Passwords Preventing Account Compromise
The phishing email aims to steal Sarah’s banking credentials. If she had used her main bank password across multiple apps, including the fraudulent one, the attacker would have gained access to her account. However, iOS 12’s App-Specific Passwords feature comes into play. Through her password manager, Sarah has set up unique, automatically generated passwords for each app accessing her cloud storage, including her banking app.
When she attempted to log in to the fraudulent website, even though it looked authentic, the unique password generated for her legitimate banking app wouldn’t work. The fraudulent website would not have access to the correct password, preventing the attacker from gaining access to her banking information. This is because the password generated for the fraudulent app (which she did not authorize) is different from the one generated for the legitimate app.
This prevents a single point of failure where compromising one password could compromise all her accounts. The iOS 12 security feature effectively blocked the attacker’s attempt, preserving the integrity of Sarah’s banking information and demonstrating the effectiveness of App-Specific Passwords in preventing unauthorized access.
Ultimate Conclusion
In conclusion, while no system is perfectly impenetrable, iOS 12 undeniably set a new standard for mobile security. Its layered approach, combining software and hardware enhancements with a user-centric privacy focus, provided a level of protection rarely seen before. While subsequent iOS versions have built upon this foundation, iOS 12 remains a landmark achievement in mobile security, showcasing Apple’s commitment to user safety and data privacy.
Key Questions Answered
Was iOS 12’s security truly better than Android’s at the time?
While direct comparisons are complex, iOS 12 generally received higher marks for its overall security architecture and user-centric privacy features compared to contemporary Android versions. Android’s fragmented ecosystem presented more challenges in consistent security updates and patching.
Did iOS 12 completely eliminate vulnerabilities?
No operating system is completely invulnerable. iOS 12, while significantly improved, still had vulnerabilities discovered and addressed through security updates. The speed and frequency of these updates, however, contributed to its strong security posture.
How did iOS 12 improve upon iOS 11?
iOS 12 built upon iOS 11’s foundation with enhanced encryption, stricter app permissions, improvements to the Secure Enclave, and more robust mechanisms to prevent data tracking and unauthorized access.