Breaking AppSec News I Finally Got IAST!
Breaking appsec news i finally got what iast for – Breaking AppSec news: I finally got what IAST is all about! For months, I’ve been hearing whispers, seeing acronyms, and feeling completely lost in the world of application security testing. IAST – Interactive Application Security Testing – sounded like some kind of secret code only elite hackers understood. But now, after diving deep into the nitty-gritty, I’m ready to share my newfound knowledge and demystify this crucial aspect of AppSec.
This isn’t just another tech blog post; it’s my personal journey of understanding IAST, from complete confusion to confident comprehension.
This post will cover everything from the basics of IAST and how it differs from SAST and DAST, to the latest breakthroughs driven by AI and machine learning. I’ll share some real-world examples, discuss the challenges of implementation, and even peek into the future of IAST. Get ready for a deep dive into the world of application security – it’s more exciting than you might think!
Understanding IAST
Interactive Application Security Testing (IAST) has emerged as a powerful tool in the AppSec arsenal, offering a unique approach to identifying vulnerabilities within running applications. Unlike static or dynamic testing methods, IAST provides real-time insights into application behavior, pinpointing security flaws as they occur. This allows for faster remediation and a more efficient security process.IAST’s core functionality revolves around instrumenting the application under test.
This instrumentation, typically achieved through agents embedded within the application, monitors the application’s runtime behavior, analyzing data flow and control flow to identify vulnerabilities. This analysis happens during the actual execution of the application, providing a highly accurate representation of potential security risks. The agent collects data on requests, responses, and internal application events, correlating this information to detect exploitable weaknesses.
The results are then presented in a user-friendly report, highlighting the location and severity of identified vulnerabilities.
IAST versus SAST
Static Application Security Testing (SAST) analyzes application code without actually running it. This means SAST can identify vulnerabilities early in the development lifecycle, but it might miss vulnerabilities that only manifest during runtime. IAST, on the other hand, analyzes the application in its runtime environment, providing a more accurate picture of actual vulnerabilities. SAST is generally faster for initial scans but can generate a higher number of false positives.
IAST offers a lower false positive rate because it only flags vulnerabilities that are actually reachable and exploitable within the application’s runtime context.
Examples of Vulnerabilities Detected by IAST
IAST excels at detecting vulnerabilities that are difficult or impossible to find with SAST or DAST. For example, IAST can effectively identify SQL injection vulnerabilities by analyzing the interaction between the application and the database during runtime. It can also pinpoint cross-site scripting (XSS) vulnerabilities by tracking how user inputs are handled and rendered in the application’s output. Other vulnerabilities effectively detected by IAST include insecure deserialization, command injection, and path traversal flaws.
Imagine a scenario where a developer inadvertently introduces a vulnerability allowing a user to manipulate file paths; IAST would instantly identify this during testing by observing the application’s interaction with the file system.
IAST versus DAST
Dynamic Application Security Testing (DAST) analyzes the application from the outside, simulating attacks to identify vulnerabilities. While DAST is effective at finding externally accessible vulnerabilities, it often struggles to pinpoint internal flaws or vulnerabilities within complex application logic. IAST complements DAST by providing insights into the application’s internal workings, thereby offering a more complete picture of its security posture. DAST can detect vulnerabilities like insecure configurations or exposed sensitive data, while IAST excels at detecting vulnerabilities that stem from the application’s internal logic.
Combining both DAST and IAST provides a comprehensive approach to application security testing.
Comparison of IAST, SAST, and DAST
| Feature | IAST | SAST | DAST |
|---|---|---|---|
| Testing Method | Runtime analysis | Static code analysis | Black-box testing |
| Accuracy | High, fewer false positives | Moderate, higher false positives | Moderate, higher false positives |
| Coverage | Limited to runtime behavior | Comprehensive code coverage | Limited to externally accessible vulnerabilities |
| Speed | Moderate | Fast | Moderate to Slow |
| Cost | Moderate | Low to Moderate | Low to Moderate |
Breaking News in IAST: Breaking Appsec News I Finally Got What Iast For
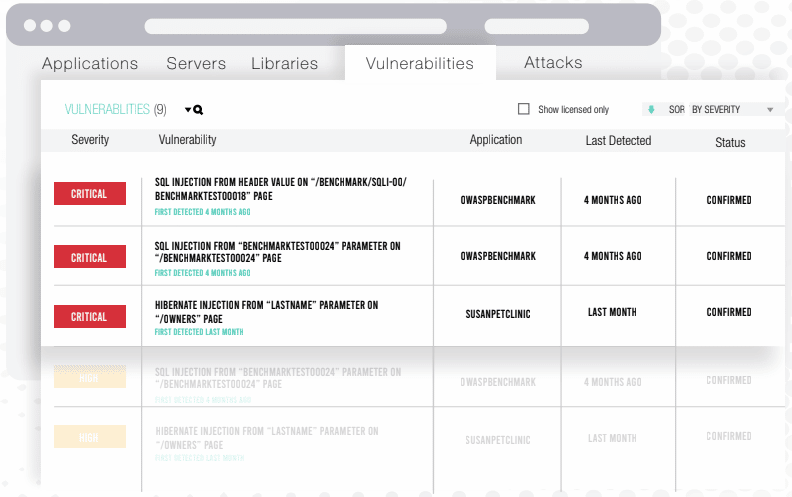
The world of application security is constantly evolving, and Interactive Application Security Testing (IAST) is no exception. Recent advancements in IAST technology are dramatically improving the speed, accuracy, and efficiency of identifying and remediating vulnerabilities within applications. This post will delve into some of the most exciting recent developments, explore the impact of AI and machine learning, and discuss emerging trends and challenges in IAST adoption.
Recent Advancements in IAST Technology, Breaking appsec news i finally got what iast for
Several recent publications highlight significant progress in IAST capabilities. One article, published by a leading security research firm, detailed the development of a new IAST engine that utilizes advanced static analysis techniques to significantly reduce false positives. This engine leverages a novel algorithm to more accurately identify true vulnerabilities within the application’s codebase, resulting in a more streamlined vulnerability management process for security teams.
Another blog post from a major IAST vendor showcased the integration of their platform with a popular DevOps pipeline, enabling automated vulnerability detection and remediation throughout the software development lifecycle (SDLC). This seamless integration reduces manual intervention and accelerates the overall security process. Finally, an independent security researcher’s report demonstrated the effectiveness of a novel IAST approach that uses machine learning to prioritize vulnerabilities based on their potential impact.
This approach allows security teams to focus their efforts on the most critical vulnerabilities first.
The Impact of AI and Machine Learning on IAST Tools
The integration of AI and machine learning is revolutionizing IAST. These technologies are used to improve the accuracy of vulnerability detection, reduce false positives, and automate the analysis of vast amounts of data generated by applications. For example, machine learning algorithms can identify patterns in application behavior that indicate the presence of vulnerabilities, even those not explicitly defined in traditional vulnerability databases.
This capability allows IAST tools to detect zero-day vulnerabilities and previously unknown attack vectors. Furthermore, AI-powered IAST solutions can automatically prioritize vulnerabilities based on their severity and potential impact, allowing security teams to focus their resources effectively. The result is a more efficient and comprehensive security posture.
Emerging Trends in IAST Adoption and Implementation
Three significant trends are shaping the future of IAST adoption: Firstly, the increasing demand for IAST solutions within DevOps and DevSecOps environments is driving innovation in areas like seamless integration with CI/CD pipelines and automated remediation workflows. Secondly, the growing adoption of cloud-native applications is leading to the development of IAST solutions specifically designed for cloud environments, addressing the unique security challenges posed by cloud infrastructure.
Thirdly, the rise of serverless computing is prompting the development of IAST tools capable of analyzing serverless functions and identifying vulnerabilities within this rapidly evolving architectural paradigm.
Challenges in Implementing IAST Solutions
Organizations face several challenges when implementing IAST solutions. One significant challenge is the potential for high false positive rates, which can overwhelm security teams and lead to alert fatigue. Careful configuration and tuning of IAST tools are crucial to mitigate this issue. Another challenge is the need for skilled personnel to effectively interpret IAST results and guide remediation efforts.
Organizations may need to invest in training or hire specialized security professionals to maximize the value of their IAST investment. Finally, integrating IAST into existing security workflows and toolchains can be complex and require significant effort. Careful planning and a phased approach are essential for successful integration.
Successful IAST Implementation Scenario
Imagine a large financial institution deploying a new mobile banking application. To ensure robust security, they integrate an IAST solution early in the SDLC. The IAST tool continuously monitors the application during development and testing, identifying and reporting vulnerabilities in real-time. The automated vulnerability prioritization feature focuses the security team’s attention on critical SQL injection flaws, enabling immediate remediation.
The seamless integration with the CI/CD pipeline ensures that newly discovered vulnerabilities are addressed before deployment. The result is a secure and reliable mobile banking application launched without significant security breaches. The IAST solution significantly reduces the time and resources needed for vulnerability management, allowing the security team to focus on more strategic security initiatives.
Practical Applications of IAST
Interactive Application Security Testing (IAST) is no longer a futuristic concept; it’s a powerful tool actively shaping modern application security. Its ability to pinpoint vulnerabilities within the application’s runtime environment offers unparalleled precision and efficiency, significantly reducing the time and resources needed for effective security testing. This section delves into practical applications, showcasing IAST’s real-world impact.
IAST Identifying and Resolving a Critical Vulnerability
Imagine a large e-commerce platform processing thousands of transactions daily. An IAST solution, integrated into the application’s runtime environment, detects a critical SQL injection vulnerability during a routine user interaction. The IAST tool identifies the precise location of the vulnerable code within a specific payment processing function – a line of code accepting user input without proper sanitization. The detailed vulnerability report provides the exact line number, the type of vulnerability (SQL injection), and even suggests potential remediation strategies.
Developers can immediately address the issue, preventing malicious actors from potentially accessing sensitive customer data or disrupting financial transactions. The speed and precision of this identification, compared to traditional penetration testing, dramatically reduces the risk window.
IAST Integration into a CI/CD Pipeline
Seamless integration with a CI/CD pipeline is crucial for maximizing IAST’s effectiveness. The process typically involves embedding the IAST agent within the application build process. Once the application is deployed to a testing environment, the IAST agent begins monitoring application behavior. Each build triggers an automated security scan. If vulnerabilities are detected, the CI/CD pipeline is halted, preventing the deployment of insecure code.
This automated approach ensures continuous security monitoring throughout the development lifecycle, transforming security from a separate phase to an integral part of the development process. Automated reports and alerts further streamline the remediation process, allowing developers to address vulnerabilities promptly and efficiently.
Using IAST in a Software Development Project: A Step-by-Step Guide
1. Selection and Integration
Choose an IAST solution compatible with your technology stack and integrate its agent into your application. This often involves adding a few lines of code or configuring your build system.
2. Configuration
Configure the IAST tool to target specific areas of the application or to focus on certain types of vulnerabilities.
3. Testing
Run your application under normal operating conditions. The IAST agent will monitor the application’s runtime behavior, detecting vulnerabilities.
4. Analysis
Review the IAST reports, which pinpoint vulnerabilities with detailed information.
5. Remediation
Address identified vulnerabilities, using the provided information and guidance.
6. Retesting
After remediation, re-run the IAST scan to verify the effectiveness of the fixes. This iterative process ensures complete vulnerability elimination.
Case Study: Acme Corp’s Successful IAST Implementation
Acme Corp, a financial services company, faced increasing pressure to enhance its application security posture. After implementing an IAST solution, they discovered and remediated over 150 vulnerabilities within their core banking application within the first three months. These included critical vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure direct object references (IDORs). The IAST tool’s precision significantly reduced the time spent on manual code review and penetration testing, freeing up security engineers to focus on other critical security initiatives.
Furthermore, the integration into their CI/CD pipeline ensured that newly introduced vulnerabilities were identified and addressed promptly, preventing them from reaching production. This proactive approach significantly reduced their overall risk exposure and improved their compliance posture.
Benefits of IAST Across Different Development Methodologies
The benefits of IAST extend across various development methodologies. The advantages are particularly pronounced in Agile environments where rapid iterations are common.
- Agile: IAST’s continuous monitoring capabilities seamlessly integrate with the iterative nature of Agile development. Early vulnerability detection minimizes rework and accelerates the release cycle.
- Waterfall: Even in the more structured Waterfall approach, IAST provides a comprehensive security assessment during the testing phase, ensuring a more secure final product.
Future of IAST

The field of Interactive Application Security Testing (IAST) is rapidly evolving, driven by the increasing complexity of software architectures and the ever-changing threat landscape. As applications become more distributed and leverage cloud-native technologies, IAST tools must adapt to remain effective. This section explores the predicted trajectory of IAST, considering the impact of emerging technologies and the features likely to shape its future.
IAST in Serverless Architectures
Serverless computing presents unique challenges for IAST. Traditional IAST agents rely on instrumenting application servers, a concept less clearly defined in a serverless environment where functions execute ephemerally. Future IAST solutions will need to incorporate mechanisms for dynamically attaching agents to functions at runtime, potentially leveraging containerization technologies or integrating directly with serverless platforms’ APIs to gain visibility into function execution and identify vulnerabilities.
This might involve analyzing function code before deployment, leveraging function logs, and integrating with runtime metrics to detect anomalous behavior indicative of exploits. A successful strategy will require a shift from agent-based instrumentation to a more event-driven, context-aware approach.
IAST for Cloud-Native Applications
Cloud-native applications, built using microservices and containerized deployments, introduce significant complexity for security testing. Traditional IAST struggles with the distributed nature of these applications, often failing to provide a holistic view of security vulnerabilities across multiple services. Future IAST tools will need to incorporate advanced techniques like distributed tracing to correlate events across microservices and provide a unified view of the application’s security posture.
This will require sophisticated integration with cloud-native monitoring and logging tools, as well as the ability to analyze traffic flowing between microservices to identify vulnerabilities that might only be apparent in the interaction between different components. The ability to automatically map application dependencies and understand data flow across services will be critical.
Key Features of Future IAST Solutions
Three key features will likely define future IAST solutions:
First, AI-powered vulnerability analysis will become increasingly important. Machine learning algorithms can be used to analyze vast amounts of runtime data to identify subtle vulnerabilities that might be missed by traditional rule-based approaches. This will include analyzing patterns in application behavior to detect anomalies indicative of attacks and prioritizing vulnerabilities based on their potential impact. For example, an AI-powered IAST could learn to identify subtle timing attacks or resource exhaustion vulnerabilities that might be difficult for a human analyst to spot.
Second, improved integration with DevSecOps pipelines is crucial. IAST needs to seamlessly integrate with CI/CD pipelines to provide continuous security feedback throughout the software development lifecycle. This will involve improved reporting, automation of remediation tasks, and better integration with other security tools. For example, automated remediation suggestions generated by IAST could be directly integrated into a developer’s IDE, improving workflow and reducing response times.
Third, support for diverse application architectures is essential. Future IAST solutions will need to support a wider range of application technologies, including serverless functions, microservices, and legacy applications. This requires adaptable agents and analysis techniques that can work effectively across different environments. For example, the same IAST solution should be able to analyze a traditional Java web application as well as a serverless function written in Python.
IAST in Five Years
Currently, IAST primarily focuses on identifying vulnerabilities during runtime. In five years, we can expect IAST to significantly enhance its capabilities. It will likely move beyond simple vulnerability detection to offer more comprehensive security insights, including automated remediation suggestions, predictive risk assessment, and proactive threat detection. Instead of just flagging vulnerabilities, it will integrate with other security tools to provide a holistic security posture management solution.
Imagine an IAST system that not only identifies a SQL injection vulnerability but also automatically suggests code changes to fix it and verifies the effectiveness of the fix in real-time. This level of automation will significantly reduce the time and resources required to secure applications.
A Futuristic Application of IAST
Imagine a future where IAST is integrated directly into the fabric of the application itself. An application could dynamically adjust its security posture based on real-time risk assessments provided by embedded IAST agents. This could involve dynamically applying security controls, such as input sanitization or rate limiting, in response to detected threats. This proactive approach to security would provide a level of protection not currently achievable with traditional security testing methods.
This self-healing application, constantly monitoring and adapting to threats, represents a significant step towards a more secure and resilient software ecosystem.
IAST Tools and Technologies

Interactive Application Security Testing (IAST) tools have become indispensable for modern software development, offering a dynamic approach to vulnerability detection that complements static and dynamic analysis methods. This section delves into a comparative analysis of commercially available IAST tools, exploring their features, limitations, and practical applications.
Comparison of Three Commercially Available IAST Tools
Three prominent IAST tools – Contrast Security, GitLab Security, and Acunetix – each offer unique strengths and weaknesses. Contrast Security is known for its comprehensive coverage, integrating seamlessly into the development pipeline and providing detailed vulnerability information. However, its pricing can be a barrier for smaller organizations. GitLab Security, being integrated into a popular DevOps platform, offers a streamlined workflow for developers, but its IAST capabilities may be less extensive than dedicated IAST solutions like Contrast.
Acunetix, while offering strong vulnerability detection, might require more manual configuration and integration efforts compared to the others. These tools differ in their approach to instrumentation, reporting, and overall integration with the software development lifecycle. Contrast, for example, uses lightweight agents that minimize performance overhead, while others might necessitate more significant modifications to the application’s codebase.
Types of Vulnerability Scans Offered by IAST Tools
IAST tools typically offer a range of vulnerability scans covering common web application vulnerabilities. These include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure deserialization, and insecure direct object references. Many tools also detect vulnerabilities related to authentication and authorization mechanisms, business logic flaws, and potentially sensitive data exposure. The specific vulnerabilities detected and the depth of analysis can vary depending on the tool and its configuration.
Some tools might also incorporate machine learning algorithms to identify emerging or less common vulnerabilities. The sophistication of these scans often directly impacts the accuracy and the volume of false positives.
Prioritizing Vulnerability Remediation with IAST Tools
IAST tools facilitate prioritization by providing context-rich vulnerability reports. This includes details such as the severity of the vulnerability, its location within the application code, and the potential impact on business operations. For example, a vulnerability allowing unauthorized access to sensitive customer data would be prioritized higher than a minor XSS vulnerability affecting a less critical section of the application.
Many tools incorporate risk scoring mechanisms, helping security teams focus on the most critical issues first. This approach is far more effective than simply addressing vulnerabilities in the order they are discovered.
Factors to Consider When Choosing an IAST Tool
Selecting the right IAST tool requires careful consideration of several factors. These include the specific needs of the application, the development environment, the level of integration required, the budget, and the technical expertise of the security team. Other crucial considerations include the tool’s ease of use, the quality of its reporting, its support for different programming languages and frameworks, and its ability to integrate with existing security tools and processes.
A thorough evaluation of these aspects is crucial to ensure the chosen IAST solution effectively addresses the organization’s security needs.
Pricing Models and Features of IAST Tools
| Tool | Pricing Model | Key Features | Limitations |
|---|---|---|---|
| Contrast Security | Subscription-based, tiered pricing | Comprehensive vulnerability detection, deep code analysis, seamless integration | Can be expensive for smaller organizations |
| GitLab Security | Included in GitLab Ultimate and Premium plans | Integrated into the GitLab DevOps platform, ease of use for developers | May have less extensive IAST capabilities than dedicated solutions |
| Acunetix | Subscription-based, tiered pricing | Strong vulnerability detection, wide range of supported technologies | May require more manual configuration and integration |
End of Discussion
So, there you have it – my epic journey into the world of IAST! From initial confusion to a confident grasp of its capabilities, I’ve learned that IAST is not just another security tool; it’s a game-changer. Its ability to detect vulnerabilities in real-time, integrate seamlessly into CI/CD pipelines, and leverage AI for enhanced accuracy makes it a must-have for any serious software development team.
While challenges remain, the future of IAST is bright, promising even more sophisticated and effective ways to protect our applications. I’m excited to see what innovations the future holds and how IAST will continue to evolve to meet the ever-changing landscape of cybersecurity.
Answers to Common Questions
What’s the biggest difference between IAST and DAST?
IAST analyzes application behavior from
-inside* the application, providing more precise vulnerability detection compared to DAST, which tests from the outside.
Is IAST suitable for all types of applications?
While IAST works well for many applications, its effectiveness can vary depending on the application’s architecture and complexity. Some highly customized or legacy systems might pose integration challenges.
How much does IAST software typically cost?
Pricing varies greatly depending on the vendor, features, and the number of users/applications. Expect a range from open-source options (free but requiring more technical expertise) to enterprise-level solutions with substantial licensing fees.
Can IAST replace SAST and DAST?
No, IAST complements SAST and DAST. Each approach offers unique advantages, and a combined strategy often yields the best results.