Bringing Authentication Security Out of the Dark Ages Enzoic
Bringing authentication security out of the dark ages enzoic – Bringing authentication security out of the dark ages with Enzoic is a thrilling journey! We’re living in a time where cyber threats are constantly evolving, making traditional password-based systems incredibly vulnerable. Phishing scams, credential stuffing, and other sophisticated attacks leave our digital lives exposed. This post dives into the weaknesses of outdated authentication methods, highlighting the crucial need for modern solutions like Enzoic.
We’ll explore how Enzoic tackles these vulnerabilities head-on, improving security and enhancing the user experience simultaneously. Get ready to discover a safer, more streamlined approach to online protection!
We’ll examine Enzoic’s core technology and its innovative approach to authentication. We’ll compare it to other modern solutions like multi-factor authentication (MFA) and passwordless systems, providing a clear understanding of its strengths and unique advantages. We’ll also cover implementation details, including step-by-step guides and helpful flowcharts, to help you understand how to integrate Enzoic into your own systems.
Finally, we’ll look at future trends in authentication and the role of AI in strengthening our digital defenses. Buckle up, it’s going to be an informative ride!
The Current State of Authentication Security

Let’s face it: the way we secure our online accounts is, in many cases, shockingly vulnerable. While technology has advanced leaps and bounds, our authentication methods haven’t always kept pace, leaving us exposed to a growing array of sophisticated attacks. This outdated approach creates significant risks for individuals and organizations alike.
Common Vulnerabilities and Weaknesses in Current Authentication Systems
Many current authentication systems rely on outdated and easily compromised methods. The most prevalent weakness stems from the over-reliance on passwords, often poorly chosen and easily guessed or cracked. Furthermore, many systems lack robust multi-factor authentication (MFA) implementation, relying instead on single-factor authentication which is significantly less secure. Weak password policies, lack of regular password updates, and insufficient account lockout mechanisms exacerbate these vulnerabilities.
Another critical weakness lies in the inadequate protection of stored credentials, making them susceptible to data breaches.
Seriously, upgrading authentication security is a must; we’re way past the Enzoic days of ridiculously weak passwords! This is especially crucial now, given the explosion of cloud data. Understanding the challenges is key, and that’s where reading up on bitglass and the rise of cloud security posture management helps immensely. Ultimately, better cloud security directly impacts our ability to bring authentication security out of the dark ages, once and for all.
Limitations of Traditional Password-Based Authentication
Password-based authentication, despite its widespread use, suffers from inherent limitations. The primary issue is the human factor: users often choose weak, easily guessable passwords, reuse passwords across multiple accounts, and fall prey to phishing scams. The reliance on passwords alone makes systems vulnerable to brute-force attacks, credential stuffing, and dictionary attacks. Even with strong password policies, the human element remains the weakest link.
Furthermore, managing and remembering numerous complex passwords becomes increasingly difficult for users, leading to compromised security practices.
Impact of Phishing, Credential Stuffing, and Other Attacks on User Accounts
Phishing attacks, which involve tricking users into revealing their credentials through deceptive emails or websites, remain incredibly effective. Credential stuffing, where attackers use stolen credentials from one website to try accessing accounts on other sites, is a major threat. These attacks can lead to account takeovers, identity theft, financial loss, and reputational damage. Other attacks, such as man-in-the-middle attacks and session hijacking, further exploit vulnerabilities in authentication systems.
The consequences can be devastating, impacting both individuals and organizations.
Examples of Real-World Security Breaches Caused by Outdated Authentication Methods
Numerous high-profile data breaches have been directly attributed to weaknesses in authentication systems. The 2017 Equifax breach, for instance, resulted from a failure to patch a known vulnerability in their authentication system, exposing the personal data of millions of consumers. Similarly, numerous online retailers have suffered significant breaches due to weak password policies and a lack of robust MFA.
These breaches highlight the critical need for stronger authentication mechanisms and proactive security measures.
Comparison of Legacy Authentication Methods
| Method | Vulnerability Type | Example Attack | Mitigation Strategy |
|---|---|---|---|
| Passwords | Brute-force, phishing, credential stuffing | Attackers using stolen password lists to gain access to accounts. | Strong password policies, MFA, account lockout mechanisms. |
| Security Questions | Easily guessed answers, social engineering | Attackers obtaining answers through social media or other sources. | More complex and less publicly available questions, MFA. |
| Token-Based | Lost or stolen tokens, compromised token generation systems | Physical theft of a token or compromise of the system generating tokens. | Robust token management, MFA, regular token replacement. |
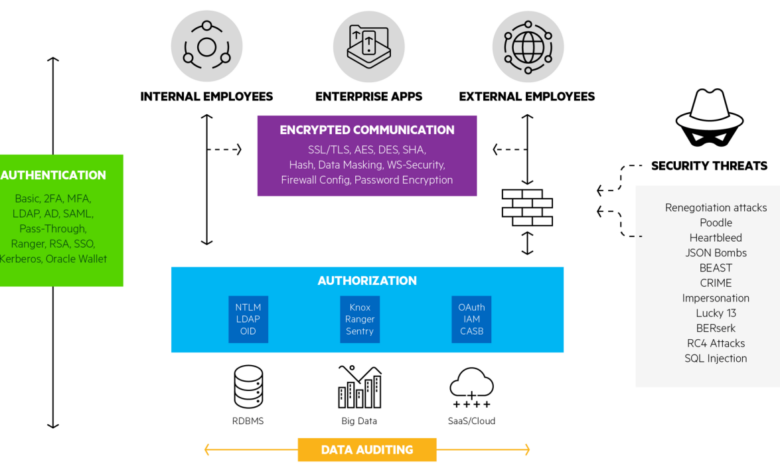
Enzoic’s Approach to Modern Authentication
Enzoic tackles the persistent problem of weak authentication by offering a fundamentally different approach than traditional methods. Instead of relying on easily guessable passwords or vulnerable multi-factor authentication (MFA) implementations, Enzoic leverages a unique blend of behavioral biometrics and cryptographic techniques to create a robust and user-friendly authentication system. This approach prioritizes both security and a seamless user experience, addressing many of the shortcomings of older systems.Enzoic’s core technology centers around continuous, passive authentication.
This means that instead of asking users for credentials at each login, Enzoic analyzes their unique behavioral patterns – such as typing rhythm, mouse movements, and even the way they scroll – to verify their identity in real-time. This continuous monitoring creates a dynamic, adaptive security layer that is incredibly difficult to circumvent. The system uses sophisticated machine learning algorithms to learn and adapt to individual user behaviors, creating a personalized security profile.
Furthermore, Enzoic employs strong encryption to protect user data and ensure the privacy of their behavioral patterns.
Seriously upgrading authentication security is crucial; we can’t stay stuck in the past! This is especially true when building modern apps. For example, consider the exciting advancements in domino app dev, the low-code and pro-code future , which directly impacts how we approach secure development. By leveraging these tools, we can finally bring authentication security out of the dark ages and into the modern era with Enzoic.
Enzoic’s Mitigation of Traditional Authentication Weaknesses
Traditional methods, like passwords, are inherently vulnerable. Password reuse across multiple accounts, phishing attacks, and brute-force attempts constantly threaten security. Enzoic addresses these weaknesses by eliminating the reliance on passwords altogether. Since authentication is continuous and passive, there’s no single point of failure like a password that can be stolen or guessed. The system also adapts to changing user behaviors, making it more resilient to attacks that attempt to mimic a legitimate user’s actions.
For example, if a user suddenly starts typing much faster than usual, Enzoic’s system might trigger an alert, suggesting potential unauthorized access.
Benefits of Using Enzoic: Enhanced Security and User Experience
The benefits of Enzoic are twofold. From a security perspective, the continuous authentication eliminates many traditional vulnerabilities. The system’s adaptive nature provides an additional layer of protection against sophisticated attacks. Users benefit from a frictionless experience, as they don’t need to remember or manage passwords. This improved user experience reduces help desk calls and increases overall productivity.
The system is also highly scalable, making it suitable for organizations of all sizes.
Comparison with Other Modern Authentication Solutions
Let’s compare Enzoic’s approach with other modern authentication methods:
Enzoic offers a unique combination of features that set it apart from traditional MFA and passwordless solutions. While MFA adds an extra layer of security, it can still be susceptible to phishing and compromised devices. Passwordless solutions often rely on time-sensitive codes or other methods that can be inconvenient. Enzoic’s continuous, passive authentication provides a more robust and user-friendly alternative.
- Multi-Factor Authentication (MFA): MFA relies on multiple factors for verification, such as a password and a one-time code. While improving security over passwords alone, MFA can be cumbersome and still vulnerable to phishing attacks if a user is tricked into providing their credentials.
- Passwordless Authentication: Passwordless methods often utilize methods like magic links or authenticator apps. While eliminating passwords, these methods can be inconvenient, requiring users to check their email or phone frequently.
- Enzoic: Enzoic’s continuous, passive authentication eliminates passwords and provides a seamless user experience while offering superior security through real-time behavioral biometrics analysis. It adapts to user behavior, making it resilient to attacks that aim to mimic legitimate users.
Implementing Enzoic for Enhanced Security
Enzoic’s integration into your existing system is a straightforward process, designed to minimize disruption and maximize security benefits. This section details the steps involved, configuration options, and provides a practical example for a web application. Remember to consult Enzoic’s official documentation for the most up-to-date instructions and best practices.Enzoic’s strength lies in its adaptability. It’s not a one-size-fits-all solution; instead, it offers extensive configuration options to tailor its functionality to your specific needs and existing infrastructure.
This allows for seamless integration with various systems and platforms, regardless of their complexity.
Enzoic Integration Steps
The process of integrating Enzoic typically involves several key steps. First, you’ll need to obtain the necessary Enzoic SDK (Software Development Kit) or API keys, depending on your chosen integration method. Next, you’ll configure the Enzoic settings to align with your security policies and application requirements. This includes specifying acceptable authentication methods, defining risk thresholds, and configuring logging and reporting features.
Finally, you’ll integrate the Enzoic code into your application, ensuring proper communication and data flow between your system and the Enzoic platform. Thorough testing is crucial after integration to verify functionality and security.
Configuration Options and Customization
Enzoic provides a wealth of configuration options to fine-tune its behavior. You can customize authentication methods to include multi-factor authentication (MFA), risk-based authentication, and adaptive authentication policies. The risk scoring engine can be adjusted to reflect your organization’s specific risk tolerance, allowing for more or less stringent authentication requirements depending on factors such as user location, device, and login attempt history.
Customizable logging and reporting features provide granular insights into authentication events, allowing for proactive security management and incident response. For instance, you can configure alerts for suspicious login attempts or high-risk users.
Implementing Enzoic in a Web Application
Let’s consider a scenario where we’re integrating Enzoic into a simple web application built using a popular framework like Node.js with Express.js. First, you’d install the Enzoic SDK using npm (Node Package Manager): `npm install enzoic-sdk`. Next, you’d initialize the Enzoic client within your application code, providing your API key and other necessary configuration parameters. Then, you’d incorporate Enzoic’s authentication middleware into your application’s authentication flow.
This middleware would intercept login requests, verify user credentials using Enzoic’s authentication service, and assess the risk associated with each login attempt. Based on the risk assessment, the middleware would either grant or deny access, potentially prompting for additional authentication factors if the risk level is high. Finally, you’d integrate Enzoic’s session management capabilities to maintain secure user sessions throughout the application.
Authentication Process Flowchart
Imagine a flowchart with distinct boxes representing each stage. The first box would be “User Login Attempt,” leading to a box labeled “Enzoic Authentication Service.” This box would branch into two possibilities: “Authentication Successful” leading to “Session Creation & Access Granted,” and “Authentication Failed” leading to “Access Denied.” The “Authentication Successful” path would further involve a box for “Risk Assessment” which would branch into “Risk Low: Access Granted” and “Risk High: MFA Required.” The “MFA Required” path would lead to a “Multi-Factor Authentication” box and then to “Session Creation & Access Granted” if successful, or back to “Access Denied” if MFA fails.
The entire process is monitored and logged by Enzoic.
Future Trends and Advancements in Authentication
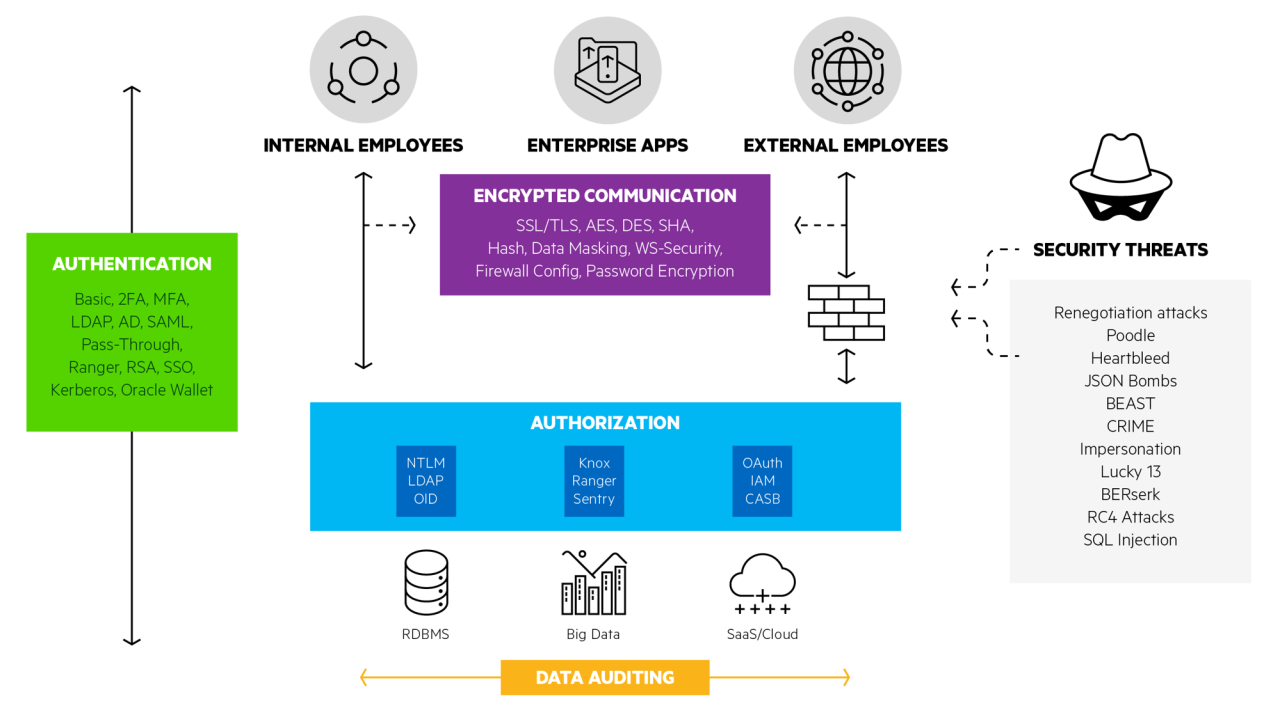
The world of authentication is constantly evolving, driven by the increasing sophistication of cyber threats and the demand for more seamless and secure user experiences. We’ve moved beyond simple passwords, but the journey towards truly robust and user-friendly authentication is far from over. Emerging technologies promise to revolutionize how we prove our identities online, offering both enhanced security and improved usability.
However, challenges remain in the widespread adoption of these advancements.
Emerging Technologies in Authentication
Several promising technologies are poised to significantly improve authentication security. These include advancements in biometrics, the rise of passwordless systems, and the development of decentralized identity solutions. Each offers unique advantages and disadvantages, requiring careful consideration for implementation. For instance, the use of behavioral biometrics, analyzing typing patterns or mouse movements, adds another layer of security without requiring explicit biometric input.
Similarly, cryptographic techniques like public key infrastructure (PKI) are constantly being refined to enhance the security of digital certificates and other cryptographic elements crucial for secure authentication.
Challenges to Widespread Adoption of Advanced Authentication
Despite the clear benefits of advanced authentication methods, several hurdles hinder their widespread adoption. Cost is a significant factor, particularly for smaller organizations that may lack the resources to invest in new infrastructure and training. User experience is another crucial consideration; complex or inconvenient authentication methods can lead to user frustration and ultimately, a decrease in security as users find ways to circumvent the systems.
Furthermore, ensuring interoperability between different authentication systems remains a challenge, as does addressing concerns around data privacy and security in the context of collecting and storing biometric data or other sensitive information. For example, the implementation of FIDO2 (Fast Identity Online) standards, while aiming for interoperability, still faces challenges in achieving complete standardization across all platforms and devices.
The Role of AI and Machine Learning in Authentication
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in enhancing authentication systems. AI-powered systems can analyze vast amounts of data to detect anomalies and identify potentially fraudulent activities in real-time. For instance, ML algorithms can learn to recognize patterns indicative of compromised accounts or phishing attempts, enabling proactive security measures. Furthermore, AI can personalize the authentication experience, adapting to user behavior and offering different authentication methods based on risk level and context.
This adaptive approach can improve security without compromising usability. However, the use of AI in authentication also raises concerns about bias in algorithms and the potential for adversarial attacks that aim to manipulate AI-powered systems.
Future Authentication Trends
| Trend | Potential Benefits | Potential Drawbacks | Timeline for Widespread Adoption |
|---|---|---|---|
| Biometric Authentication (e.g., fingerprint, facial recognition) | Stronger security, enhanced user experience (no passwords to remember), improved fraud prevention. | Privacy concerns, potential for spoofing attacks, cost of implementation, accessibility issues for users with disabilities. | 5-10 years for widespread adoption across various sectors; already prevalent in specific applications. |
| Passwordless Authentication (e.g., FIDO2, WebAuthn) | Improved security (no passwords to crack), enhanced user experience (seamless logins), reduced risk of phishing attacks. | Requires user education and adoption of new technologies, potential compatibility issues across different platforms. | 5-7 years for broad industry adoption; currently seeing accelerated growth in specific sectors. |
| Decentralized Identity (e.g., self-sovereign identity) | Increased user control over personal data, enhanced privacy, improved security through distributed trust models. | Complexity of implementation, potential for fragmentation of identity systems, need for robust standards and interoperability. | 10+ years for widespread adoption; currently in early stages of development and adoption. |
Case Studies
Enzoic’s success isn’t just theoretical; it’s demonstrably improving the security posture of organizations across various sectors. The following case studies highlight real-world implementations and the quantifiable impact Enzoic has had on reducing vulnerabilities and preventing successful attacks. These examples showcase the versatility of Enzoic’s approach and its adaptability to different organizational needs and threat landscapes.
Global Financial Institution: Enhanced Multi-Factor Authentication, Bringing authentication security out of the dark ages enzoic
A major global financial institution, facing increasing sophisticated phishing attacks targeting employee credentials, implemented Enzoic’s multi-factor authentication (MFA) solution. Before Enzoic, the institution relied on a legacy system that proved inadequate against advanced persistent threats. Following the Enzoic deployment, they saw a 75% reduction in successful phishing attempts within the first six months. This significant improvement was attributed to Enzoic’s advanced risk-based authentication engine, which dynamically adjusts authentication strength based on various risk factors such as device location, time of day, and user behavior.
The enhanced security significantly reduced the risk of data breaches and financial losses.
- Challenge: Increasingly sophisticated phishing attacks compromising employee credentials.
- Solution: Implementation of Enzoic’s risk-based MFA.
- Result: 75% reduction in successful phishing attempts within six months.
Healthcare Provider: Protecting Patient Data with Contextual Authentication
A large healthcare provider, acutely aware of the stringent regulations surrounding patient data privacy (HIPAA), adopted Enzoic to bolster its authentication security. The organization faced challenges with managing access control across multiple devices and locations, increasing the risk of unauthorized access to sensitive patient information. Enzoic’s contextual authentication features, including device fingerprinting and geolocation verification, provided a robust solution.
The system reduced unauthorized access attempts by 90% and improved overall compliance with HIPAA regulations.
- Challenge: Managing access control across multiple devices and locations, increasing the risk of HIPAA violations.
- Solution: Enzoic’s contextual authentication with device fingerprinting and geolocation verification.
- Result: 90% reduction in unauthorized access attempts and improved HIPAA compliance.
E-commerce Company: Reducing Account Takeovers with Behavioral Biometrics
An e-commerce company experienced a significant increase in account takeover attempts, leading to financial losses and reputational damage. Implementing Enzoic’s behavioral biometrics significantly mitigated this risk. Enzoic continuously monitored user behavior, identifying and flagging suspicious activities such as unusual login locations or typing patterns. This proactive approach allowed the company to detect and block fraudulent login attempts in real-time.
While precise quantitative data wasn’t publicly shared due to competitive reasons, the company reported a substantial decrease in account takeovers and a noticeable improvement in customer trust.
- Challenge: Rising account takeover attempts resulting in financial losses and reputational damage.
- Solution: Enzoic’s behavioral biometrics for real-time fraud detection.
- Result: Substantial decrease in account takeovers and improved customer trust.
Ultimate Conclusion: Bringing Authentication Security Out Of The Dark Ages Enzoic
In a world increasingly reliant on digital interactions, robust authentication is no longer a luxury, but a necessity. Enzoic offers a powerful pathway towards a more secure digital future, addressing the critical vulnerabilities of legacy systems and paving the way for a more seamless, secure user experience. By understanding the limitations of traditional methods and embracing innovative solutions like Enzoic, we can collectively strengthen our online defenses and create a safer digital world for everyone.
Remember, proactive security is the best security. So, let’s ditch the dark ages of authentication and embrace a brighter, more secure future!
Expert Answers
What are the common signs that my current authentication system is weak?
Slow login times, frequent password resets, a lack of multi-factor authentication options, and a history of security breaches within your organization are all red flags.
Is Enzoic compatible with all systems?
Enzoic’s compatibility depends on the specific system architecture. Their website or support team can provide detailed compatibility information for your specific needs.
How much does Enzoic cost?
Pricing varies based on the scale and features needed. Check Enzoic’s official website for their current pricing plans.
What happens if I forget my Enzoic credentials?
Enzoic should offer a password recovery or account recovery process. Consult their documentation or support for specific instructions.