Britain to Kitemark Electronic Devices After Cyber Attacks
Britain to Kitemark electronic devices in the wake of cyber attacks – that’s the headline grabbing everyone’s attention! Recent high-profile cyberattacks have shaken the UK, exposing vulnerabilities in our electronic devices and highlighting the urgent need for stronger cybersecurity measures. This new Kitemark scheme aims to change all that, promising a boost in consumer confidence and a more secure digital landscape.
But will it really work? Let’s dive in and explore the details.
The proposed Kitemark will act as a trusted seal of approval, assuring consumers that a device meets specific security standards. This means manufacturers will have to jump through some serious hoops to get certified, leading to potentially higher production costs and possibly even affecting the price of devices on the shelves. However, the long-term benefits could outweigh the initial costs, leading to a more secure and resilient digital ecosystem for everyone.
We’ll look at the pros and cons for both consumers and manufacturers, examining potential obstacles and comparing the scheme to similar initiatives in other countries.
The Current State of Cyber Security in Britain’s Electronics Sector: Britain To Kitemark Electronic Devices In The Wake Of Cyber Attacks
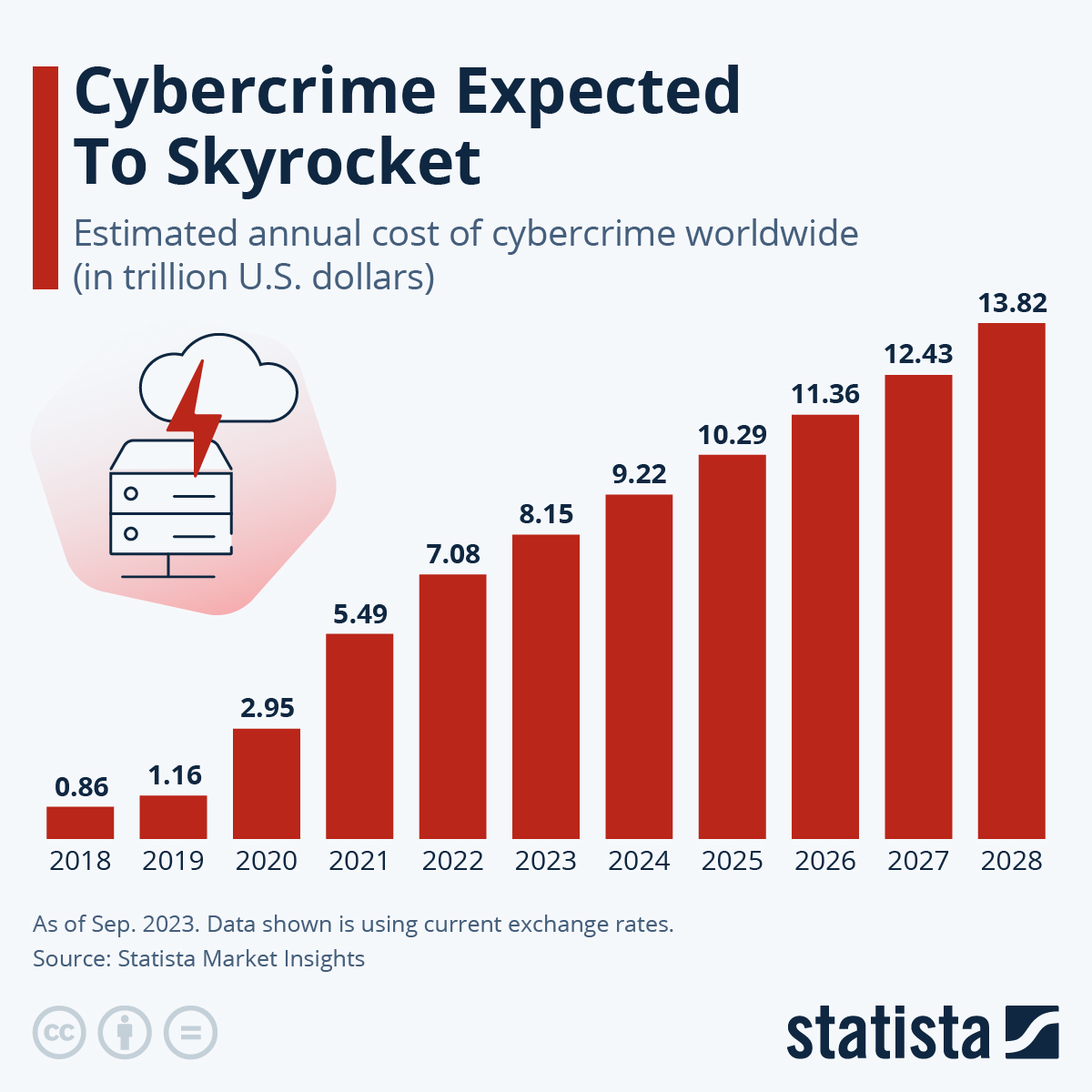
Britain’s electronics sector faces a constantly evolving landscape of cyber threats, impacting everything from critical national infrastructure to individual consumers. The increasing reliance on interconnected devices and the growing sophistication of cyberattacks present a significant challenge to national security and economic prosperity. The consequences of successful attacks can be severe, ranging from financial losses to reputational damage and disruption of essential services.The Current Cyber Threat Landscape in BritainThe UK is a prime target for cyberattacks due to its advanced technological infrastructure and its position as a global financial and economic hub.
Threat actors range from state-sponsored groups to organized crime syndicates and individual hackers, each with different motives and capabilities. These threats exploit vulnerabilities in hardware, software, and human processes, aiming to steal data, disrupt operations, or gain unauthorized access to systems. Recent attacks have highlighted the need for stronger cybersecurity measures across all sectors.
Vulnerabilities Exploited in Recent High-Profile Cyber Attacks
Recent high-profile cyberattacks in Britain have exposed several key vulnerabilities. For instance, attacks targeting supply chains have shown the weakness of relying on compromised components in electronic devices. Exploiting vulnerabilities in software updates and outdated systems has also been a common tactic, allowing attackers to gain control of networks and steal sensitive information. Furthermore, human error, such as phishing scams and weak password practices, continues to be a significant vulnerability, enabling attackers to gain initial access to systems.
The 2020 attack on the National Health Service (NHS) is a stark example of the devastating consequences of such vulnerabilities, demonstrating the significant impact on healthcare services and patient data.
Britain’s plan to kitemark electronic devices is a smart move given the recent surge in cyber attacks. This increased focus on device security highlights the need for robust cloud security measures, which is where solutions like bitglass and the rise of cloud security posture management become crucial. Ultimately, a multi-layered approach, encompassing both hardware certification and strong cloud security, is vital to protecting against future threats.
The kitemark initiative could be a powerful step in improving overall digital safety.
Economic and Social Impact of Cyber Attacks, Britain to kitemark electronic devices in the wake of cyber attacks
The economic impact of cyberattacks on Britain’s electronics sector is substantial. Data breaches can lead to significant financial losses through fines, legal fees, and damage to reputation. Disruption of services can halt production, affect supply chains, and cause considerable economic damage. For example, a successful ransomware attack on a manufacturing company could lead to production downtime, lost orders, and significant financial losses.
The social impact is equally significant. Data breaches can lead to identity theft, financial fraud, and loss of personal information, causing significant distress and harm to individuals. The disruption of essential services, such as healthcare or transportation, can have widespread consequences for the general public.
Types of Cyber Threats and Their Impact
Understanding the different types of cyber threats and their potential impact is crucial for effective mitigation. The following table summarizes some common threats and their consequences:
| Threat Type | Target | Impact | Mitigation Strategy |
|---|---|---|---|
| Ransomware | Data and systems | Data loss, operational disruption, financial losses | Regular backups, robust security software, employee training |
| Phishing | Individuals, organizations | Data breaches, malware infections, financial losses | Security awareness training, multi-factor authentication, email filtering |
| Denial-of-Service (DoS) | Websites, online services | Service disruption, loss of revenue, reputational damage | Network security measures, DDoS mitigation services |
| Supply Chain Attacks | Hardware, software components | Compromised devices, data breaches, widespread disruption | Secure supply chain management, rigorous vendor vetting |
The Proposed Kitemark Scheme

The recent surge in sophisticated cyberattacks targeting electronic devices in Britain has highlighted a critical need for enhanced security measures. To address this vulnerability and restore consumer confidence, a comprehensive Kitemark scheme for electronic devices is being proposed. This scheme aims to provide a clear and easily identifiable mark of assurance, signifying that a device has met rigorous security standards.The rationale behind introducing a Kitemark scheme is multifaceted.
It seeks to create a level playing field for manufacturers, rewarding those who prioritize cybersecurity and penalizing those who don’t. Furthermore, it provides consumers with a simple and trustworthy method for identifying secure devices, reducing their risk of cyberattacks and data breaches. Finally, it aims to strengthen Britain’s position as a global leader in cybersecurity innovation and best practices.
Security Standards and Criteria
Devices seeking Kitemark certification will need to meet a comprehensive set of security standards and criteria. These will cover various aspects of device security, including secure boot processes, robust encryption protocols, regular software updates, and secure data handling practices. Specific standards will likely align with internationally recognized frameworks such as NIST Cybersecurity Framework and ISO 27001, adapting them to the specific context of consumer and business electronic devices.
Independent testing and audits will be required to verify compliance, ensuring the integrity and reliability of the Kitemark. Failure to meet these standards will result in denial of certification.
Key Stakeholders Involved
The development and implementation of the Kitemark scheme involve a diverse range of stakeholders, each playing a crucial role. The UK government is providing strategic direction and potentially funding for the initiative. Industry bodies representing electronics manufacturers will be actively involved in defining the standards and ensuring the scheme is practical and achievable. Independent certification bodies will conduct the testing and auditing of devices.
Finally, consumer advocacy groups will contribute to ensuring the scheme effectively protects consumer interests and provides transparency. Collaboration among these stakeholders is essential for the scheme’s success.
Anticipated Benefits for Consumers and Businesses
The Kitemark scheme is anticipated to bring significant benefits to both consumers and businesses. For consumers, the Kitemark will provide a clear and simple indicator of a device’s security, empowering them to make informed purchasing decisions and reduce their vulnerability to cyber threats. Businesses will benefit from improved supply chain security, reduced liability from security breaches, and enhanced brand reputation.
The scheme could also stimulate innovation in cybersecurity, driving the development of more secure and resilient electronic devices. For example, a company offering a Kitemarked smart home system would be likely to attract more customers than a competitor offering a similar product without the certification, demonstrating a clear market advantage.
Implementation and Enforcement of the Kitemark
The success of the proposed Kitemark scheme hinges not only on its design but also on its effective implementation and enforcement. A robust and transparent process for certification, coupled with rigorous monitoring and penalties for non-compliance, will be crucial in building consumer trust and driving industry adoption. This section Artikels the key aspects of this vital phase.
The Kitemark Certification Process
Manufacturers seeking the Kitemark will need to undergo a rigorous assessment process. This will likely involve a multi-stage approach, beginning with a self-assessment to identify potential vulnerabilities and areas needing improvement. This self-assessment would be followed by an independent audit conducted by a designated certification body accredited by a relevant UK authority, such as the UK Accreditation Service (UKAS).
The audit would assess the manufacturer’s security practices, including their software development lifecycle (SDLC), supply chain management, and physical security measures. The specific requirements will depend on the type of electronic device, with stricter standards applied to devices with greater security implications (e.g., smart home hubs compared to simple kitchen timers). Successful completion of the audit would result in the granting of the Kitemark license, allowing the manufacturer to display the Kitemark on their products.
Regular reassessments and audits would be required to maintain certification, ensuring ongoing compliance with the evolving security landscape.
Mechanisms for Monitoring and Enforcement
Maintaining the integrity of the Kitemark requires robust monitoring and enforcement mechanisms. This would involve post-market surveillance, including testing of devices available to consumers, to verify that they continue to meet the specified security standards. The certification body would play a key role in this, conducting periodic checks and responding to consumer complaints or reports of security breaches.
Penalties for non-compliance should be significant enough to deter manufacturers from cutting corners, potentially including fines, suspension or revocation of the Kitemark license, and even legal action. Public transparency in reporting enforcement actions will be critical to maintain credibility and accountability. The government might also establish a dedicated task force or agency to oversee the scheme’s implementation and enforcement, providing additional oversight and support.
Challenges in Implementation and Enforcement Across Different Sectors
Implementing the Kitemark scheme uniformly across diverse sectors will present significant challenges. The security requirements for a simple electronic toy will differ greatly from those of a critical infrastructure device. Therefore, a tiered approach to certification, tailored to the specific risk profiles of different product categories, might be necessary. Ensuring consistent enforcement across all sectors will also be a challenge, requiring close collaboration between government agencies, certification bodies, and industry stakeholders.
Another challenge will be adapting the scheme to the rapid pace of technological innovation. The security landscape is constantly evolving, necessitating regular updates to the Kitemark standards to reflect the latest threats and best practices.
Potential Obstacles to Widespread Adoption
The successful adoption of the Kitemark will depend on overcoming several potential obstacles:
- Cost of Certification: The cost of obtaining and maintaining the Kitemark could be a significant barrier for smaller manufacturers, particularly those operating on tight margins.
- Complexity of Standards: The technical complexity of the security standards might make it difficult for some manufacturers to meet them, requiring substantial investment in expertise and resources.
- Lack of Awareness: Consumers need to be made aware of the Kitemark and its significance in ensuring the security of their electronic devices. A comprehensive public awareness campaign will be essential.
- International Harmonization: Ensuring the Kitemark is recognized internationally would be beneficial to UK manufacturers exporting their products. Achieving international harmonization of security standards will be a significant undertaking.
- Resistance from Manufacturers: Some manufacturers might resist adopting the Kitemark, either due to cost concerns or a reluctance to undergo the rigorous certification process.
Impact on Manufacturers and Consumers
The introduction of a Kitemark for electronic devices in Britain, designed to bolster cybersecurity, will undoubtedly have a significant impact on both manufacturers and consumers. The ripple effects will be felt across the supply chain, from component sourcing to retail pricing, and ultimately influence consumer choices and trust in the digital marketplace. Understanding these impacts is crucial for navigating the transition to a more secure digital landscape.The proposed Kitemark scheme will likely increase the cost of manufacturing electronic devices.
Manufacturers will need to invest in new testing procedures, implement enhanced security measures during the design and manufacturing process, and potentially redesign existing products to meet the Kitemark’s stringent criteria. These added costs could translate to higher prices for consumers, potentially impacting the affordability and accessibility of certain devices, especially for budget-conscious buyers. The increased complexity of certification might also lead to longer lead times for product launches, potentially affecting market competitiveness.
Cost and Availability of Electronic Devices
The increased costs associated with achieving Kitemark certification will inevitably impact the pricing of electronic devices. Smaller manufacturers, particularly those with limited resources, may struggle to absorb these additional costs, potentially leading to reduced competition and a smaller selection of products available to consumers. Larger manufacturers with greater financial resources are more likely to absorb the costs, although this might still lead to slightly higher prices across the board.
The availability of some lower-cost devices might decrease as manufacturers decide the added cost of certification isn’t economically viable. This could disproportionately affect consumers in lower income brackets. We might see a shift towards a tiered market, with Kitemark-certified devices at a premium price point and uncertified devices remaining at lower price points but with a corresponding security risk.
Manufacturer Response to Certification Requirements
Manufacturers’ responses will vary depending on their size, financial capabilities, and existing security practices. Larger companies with established cybersecurity teams are likely to adapt more quickly, viewing the Kitemark as an opportunity to demonstrate their commitment to security and gain a competitive advantage. They may proactively invest in new technologies and processes to meet the certification requirements. Smaller manufacturers may face greater challenges, potentially requiring government support or collaboration to meet the new standards.
Some manufacturers might choose to focus on specific product lines for certification, prioritizing those with higher security needs or market value. Others might even decide to exit the market if the costs of certification prove insurmountable. This could lead to market consolidation, with fewer, larger players dominating the landscape.
Benefits and Drawbacks of the Kitemark for Consumers
The Kitemark offers consumers a clear and easily identifiable indication of a device’s enhanced cybersecurity features. This transparency allows consumers to make informed purchasing decisions based on their individual security needs and risk tolerance. The increased trust and confidence in the security of Kitemark-certified devices could lead to reduced instances of cyberattacks and data breaches. However, the higher cost of Kitemark-certified devices presents a significant drawback, particularly for budget-conscious consumers.
The scheme’s effectiveness also depends on the rigor of the certification process and its enforcement. If the certification process is weak or poorly enforced, the Kitemark’s value as a security indicator diminishes. There is also a risk of “Kitemark fatigue,” where consumers become desensitized to the mark’s significance.
Scenario: Consumer Benefit from a Kitemark-Certified Device
Imagine Sarah, a freelance journalist, who relies heavily on her laptop for work. She stores sensitive client information and financial data on her device. After reading about the Kitemark scheme, Sarah decides to purchase a Kitemark-certified laptop. This provides her with peace of mind, knowing that the device has undergone rigorous testing to ensure its cybersecurity capabilities. When a recent cyberattack targets unprotected devices, Sarah’s Kitemark-certified laptop remains secure, protecting her valuable data and avoiding the significant financial and reputational damage that could have resulted from a data breach.
This scenario highlights the tangible benefits of purchasing a Kitemark-certified device, especially for individuals and businesses handling sensitive information.
International Comparisons and Best Practices
Britain’s proposed Kitemark scheme for electronic devices aims to bolster cybersecurity, but how does it stack up against similar initiatives globally? Examining international best practices and comparing different approaches can help refine the scheme and ensure its effectiveness. This analysis will highlight successful strategies and identify areas where the British scheme can learn from others.
Several countries have implemented or are developing cybersecurity certification schemes for electronic devices. These schemes vary significantly in scope, implementation, and enforcement. Understanding these differences is crucial to crafting a robust and effective Kitemark scheme. We will examine key features, focusing on their strengths and weaknesses, to identify potential improvements for the UK’s initiative.
Cybersecurity Certification Schemes in Other Countries
The European Union’s Cybersecurity Act, for instance, establishes a framework for cybersecurity certification schemes, including a scheme for IoT devices. This framework emphasizes interoperability and mutual recognition of certifications across member states. In contrast, the United States relies more on voluntary industry standards and government guidance, with initiatives like the NIST Cybersecurity Framework playing a significant role. Other countries, such as Singapore and Japan, have implemented specific cybersecurity labeling programs focusing on particular device types or sectors.
These diverse approaches reflect differing regulatory environments and national priorities.
Best Practices from International Cybersecurity Initiatives
A key best practice observed in successful schemes is the involvement of industry stakeholders throughout the development process. This ensures the scheme is practical, adaptable, and widely accepted by manufacturers. For example, the development of the German GS mark (Geprüfte Sicherheit) involved extensive consultation with industry experts, resulting in a scheme that is both rigorous and relevant to market needs.
Another best practice is the establishment of clear and accessible criteria, making it easy for manufacturers to understand the requirements for certification. Finally, robust enforcement mechanisms are crucial for ensuring the effectiveness of any cybersecurity certification scheme. This could include regular audits, penalties for non-compliance, and public reporting of certification status.
Examples of Successful Cybersecurity Initiatives
Singapore’s Cyber Security Agency (CSA) has implemented a successful cybersecurity labeling scheme for IoT devices. The scheme focuses on specific vulnerabilities and requires manufacturers to meet minimum security requirements before receiving the label. This has helped raise awareness among consumers about cybersecurity risks and encouraged manufacturers to improve the security of their products. Similarly, Germany’s GS mark, while not exclusively focused on cybersecurity, has been effective in promoting product safety and reliability, including aspects related to cybersecurity.
The scheme’s success is largely attributed to its rigorous testing procedures and strong enforcement mechanisms.
Comparative Table of National Cybersecurity Schemes
| Country | Scheme Name | Key Features | Effectiveness (Qualitative Assessment) |
|---|---|---|---|
| United States | NIST Cybersecurity Framework (primarily guidance, not certification) | Voluntary framework; focuses on risk management; widely adopted by industry | Moderately Effective – widespread adoption but relies on self-assessment |
| European Union | EU Cybersecurity Act (framework for certification schemes) | Mandates cybersecurity certification for certain products; promotes interoperability | Developing – implementation and effectiveness vary across member states |
| Singapore | Cybersecurity Labelling Scheme (IoT devices) | Mandatory labelling for certain IoT devices; clear security requirements; public awareness campaign | Highly Effective – significant improvement in IoT device security |
| Germany | GS Mark (Geprüfte Sicherheit) | Covers various product categories, including aspects related to cybersecurity; rigorous testing | Highly Effective – strong reputation for product safety and reliability |
| Japan | Various sector-specific initiatives | Focus on specific industries and device types; often involves government-industry collaboration | Moderately Effective – effectiveness varies depending on specific initiative |
Future of Cybersecurity in the UK Electronics Market
The introduction of a Kitemark scheme for electronic devices signifies a significant step towards bolstering cybersecurity in the UK. Its long-term impact will be multifaceted, affecting not only manufacturers and consumers but also shaping the future landscape of cybersecurity research, development, and innovation within the UK electronics market. The success of the scheme hinges on its adaptability and responsiveness to the ever-evolving threat landscape.The Kitemark scheme’s long-term impact will be a gradual but significant improvement in the overall security posture of electronic devices sold in the UK.
We can expect to see a reduction in vulnerabilities exploited by cybercriminals, leading to fewer successful attacks and a decrease in associated financial and reputational losses for both businesses and individuals. This will foster greater consumer trust and potentially lead to increased competitiveness for UK manufacturers who meet the Kitemark standard, as they can showcase a higher level of security assurance compared to their competitors.
However, the scheme’s effectiveness will depend on consistent enforcement and regular updates to its standards.
Long-Term Impact of the Kitemark Scheme
The Kitemark scheme’s success will depend on its ability to adapt to the ever-changing threat landscape. A notable example is the rapid evolution of IoT devices and the associated security challenges they pose. The initial standards might not adequately address future threats from sophisticated AI-driven attacks or quantum computing advancements. Therefore, ongoing review and updates to the Kitemark standards are crucial to maintaining its relevance and effectiveness.
Regular audits and revisions will be necessary to incorporate the latest best practices and address emerging vulnerabilities, ensuring the Kitemark remains a robust indicator of security compliance. This iterative process will necessitate collaboration between industry experts, government agencies, and cybersecurity researchers. For example, following a major vulnerability discovery in a specific type of device, the Kitemark scheme would need to be updated to address that weakness, mandating manufacturers to implement the necessary security patches and improvements to retain their Kitemark certification.
The Need for Future Updates and Revisions
The dynamic nature of cybersecurity threats necessitates continuous evolution of the Kitemark standards. Future revisions should consider several factors: the increasing sophistication of cyberattacks, the emergence of new technologies (e.g., 5G, AI, quantum computing), and the expansion of the Internet of Things (IoT). Regular audits and independent testing will ensure that the Kitemark remains a reliable indicator of security.
For instance, initial standards might focus on basic software security, but future updates could incorporate hardware-level security features, supply chain security assessments, and robust incident response plans. The scheme’s adaptability will be vital in maintaining consumer trust and driving innovation in secure device development. A robust feedback mechanism involving manufacturers, consumers, and cybersecurity experts is essential for identifying areas for improvement and incorporating the latest research findings.
The Role of Ongoing Research and Development
Ongoing research and development are pivotal in enhancing cybersecurity and maintaining the relevance of the Kitemark scheme. Investment in areas such as advanced threat detection, AI-driven security solutions, and post-quantum cryptography is crucial. Universities and research institutions play a key role in developing new techniques and technologies that can be incorporated into future Kitemark standards. Collaboration between academia and industry is essential to translate research findings into practical security solutions that can be implemented by manufacturers.
Britain’s plan to kitemark electronic devices, a response to escalating cyberattacks, highlights the urgent need for robust security. This increased focus on secure development practices ties directly into the advancements in application building, like those explored in this article on domino app dev the low code and pro code future , where faster development doesn’t have to mean sacrificing security.
Ultimately, safer devices depend on secure coding practices from the outset, influencing everything from IoT devices to critical infrastructure.
For example, research into zero-trust architectures could inform future Kitemark standards, leading to more secure device designs. Similarly, advancements in blockchain technology could enhance supply chain security, contributing to more robust verification processes for the Kitemark.
Influence of the Kitemark Scheme on New Cybersecurity Technologies
The Kitemark scheme has the potential to significantly influence the development of new cybersecurity technologies within the UK electronics market. By setting a high standard for security, it creates a strong incentive for manufacturers to invest in and adopt cutting-edge security solutions. This demand-driven approach could accelerate the development and adoption of innovative technologies, such as hardware-based security modules, advanced encryption techniques, and robust intrusion detection systems.
Furthermore, the Kitemark could act as a catalyst for collaboration between manufacturers and cybersecurity companies, fostering innovation through shared expertise and resources. For example, a manufacturer seeking Kitemark certification might collaborate with a cybersecurity firm to develop a novel security feature, benefiting both parties and advancing the overall state of cybersecurity. This creates a positive feedback loop where the demand for Kitemark compliance drives innovation, leading to further improvements in the scheme’s standards and overall cybersecurity posture.
Ending Remarks
The UK’s decision to introduce a Kitemark for electronic devices in response to escalating cyber threats is a significant step towards enhancing national cybersecurity. While challenges remain in implementation and enforcement, the potential benefits for consumers and businesses, along with the increased focus on robust security standards, make this a crucial initiative. The success of the Kitemark will depend on the level of industry adoption, consumer awareness, and the ongoing evolution of cybersecurity best practices.
It’s a game-changer, and we’ll be watching closely to see how it unfolds.
Answers to Common Questions
What specific security standards will devices need to meet for the Kitemark?
The exact standards are still being finalized but are expected to cover areas like software updates, secure boot processes, and data encryption.
How will the Kitemark scheme be enforced?
Enforcement will likely involve a combination of audits, testing, and penalties for non-compliance.
Will the Kitemark increase the price of electronic devices?
It’s possible, as manufacturers will need to invest in meeting the new security standards. However, the long-term benefits of increased security may offset this cost.
What happens if a Kitemark-certified device is compromised?
While the Kitemark aims to minimize risks, no system is foolproof. A compromised device would likely trigger an investigation into whether the certification was correctly awarded.