Britain to Take a Call on Computer Misuse Act
Britain to take a call on Computer Misuse Act: Is the UK’s outdated cybercrime legislation finally getting an overhaul? For years, the Computer Misuse Act has struggled to keep pace with the ever-evolving landscape of online crime. This post dives into the current state of the Act, exploring its strengths and weaknesses, examining proposed amendments, and considering the impact on businesses and individuals alike.
We’ll look at real-world cases, public perception, and what the future might hold for cybercrime legislation in the UK.
From the challenges of enforcing the Act against sophisticated cyberattacks to the potential for stricter penalties and updated definitions of cyber offenses, the debate surrounding the Computer Misuse Act is far from over. We’ll unpack the key arguments, examining the potential benefits and drawbacks of proposed changes, and exploring how the UK can best protect itself from the growing threat of cybercrime in the digital age.
The Current State of the Computer Misuse Act in Britain

The Computer Misuse Act 1990 (CMA) is the primary legislation in the UK addressing cybercrime. While it has been amended several times, its core provisions remain relevant, though increasingly challenged by the evolving nature of digital technology and online threats. Its effectiveness in tackling modern cybercrime is a subject of ongoing debate.
Key Provisions of the Computer Misuse Act
The CMA defines three main offenses, each carrying different penalties. Section 1 covers unauthorized access to computer material, essentially hacking. Section 2 covers unauthorized access with intent to commit further offenses, such as data theft or system disruption. Section 3 deals with unauthorized modification of computer material, encompassing acts like data deletion or malware deployment. These offenses are graded in severity, reflecting the intent and impact of the actions.
The Act also considers the means of access, with sophisticated methods attracting harsher penalties.
Penalties for Violating the Act
Penalties under the CMA range significantly depending on the offense and the severity of the consequences. Section 1 offenses (unauthorized access) can result in up to six months imprisonment and/or an unlimited fine. Sections 2 and 3 offenses carry much steeper penalties, with potential sentences reaching up to ten years imprisonment and/or an unlimited fine. The courts consider factors such as the scale of the breach, the financial losses incurred, and the potential damage to reputation when determining sentencing.
For instance, a large-scale data breach targeting a financial institution would likely result in a far more severe sentence than unauthorized access to a personal online account.
Comparison with Similar Legislation in Other Countries
The CMA shares similarities with cybercrime legislation in other countries, such as the Computer Fraud and Abuse Act (CFAA) in the United States. Both Acts address unauthorized access, modification, and use of computer systems. However, there are key differences in their scope and enforcement mechanisms. For example, the CFAA’s definition of “computer” is broader than the CMA’s, leading to differences in jurisdiction and applicability.
The European Union’s approach to cybercrime is also relevant, with the establishment of the European Cybercrime Centre working towards harmonizing legislation across member states. These differences often complicate international investigations and prosecutions.
Challenges in Enforcing the Computer Misuse Act
Enforcing the CMA presents significant challenges. The rapid evolution of technology, including the rise of sophisticated hacking techniques and the use of encrypted communication channels, makes detection and prosecution difficult. Furthermore, establishing jurisdiction can be complex, particularly in cases involving cross-border cybercrime. The skills gap among law enforcement agencies also presents a challenge, with a need for specialized expertise in digital forensics and cybersecurity.
Finally, the ambiguity surrounding certain aspects of the Act, such as the definition of “unauthorized access,” can create legal uncertainties.
Types of Computer Misuse Offenses Under the Act
| Offense | Section | Description | Maximum Penalty |
|---|---|---|---|
| Unauthorized access to computer material | 1 | Accessing computer material without authorization. | 6 months imprisonment and/or unlimited fine |
| Unauthorized access with intent to commit further offenses | 2 | Accessing computer material without authorization with the intent to commit a further offense (e.g., data theft, system disruption). | 10 years imprisonment and/or unlimited fine |
| Unauthorized modification of computer material | 3 | Unauthorized alteration or deletion of computer material. | 10 years imprisonment and/or unlimited fine |
Proposed Changes and Amendments to the Act
The Computer Misuse Act 1990, while groundbreaking for its time, is increasingly struggling to keep pace with the rapidly evolving landscape of cybercrime. Its limitations are becoming more apparent as sophisticated attacks exploit loopholes and ambiguities within the existing legislation. Proposed amendments aim to modernize the Act, bolstering its effectiveness in prosecuting offenders and protecting businesses and individuals from the ever-growing threat of online crime.The need for updating the Act is paramount.
Modern cybercrime often transcends national borders, involving complex networks of perpetrators and sophisticated techniques that the current legislation isn’t fully equipped to handle. Furthermore, the rise of new technologies, such as cloud computing and the Internet of Things (IoT), has created new vulnerabilities and attack vectors that weren’t considered when the Act was first drafted. Addressing these gaps is crucial for maintaining a robust and effective cybersecurity framework.
Britain’s review of the Computer Misuse Act is crucial, especially considering the rapid advancements in tech. This makes the future of app development, like what’s discussed in this insightful article on domino app dev the low code and pro code future , even more relevant. Understanding these evolving development methods is key to navigating the complexities of cybersecurity legislation and ensuring the Act remains effective in the face of new technologies.
Impact of Proposed Amendments on Businesses
Proposed amendments could significantly impact businesses, both positively and negatively. On the positive side, strengthened legislation could lead to increased confidence in online transactions and data security, potentially attracting more investment and fostering economic growth. Clearer legal definitions and increased penalties for cybercrimes could act as a strong deterrent, reducing the risk of attacks and the associated financial losses.
However, businesses may also face increased compliance costs associated with implementing stronger cybersecurity measures to meet the updated legal requirements. This could particularly affect smaller businesses with limited resources. For example, increased requirements for data breach notification and incident reporting could necessitate investment in new technologies and expertise.
Strengthening Cybersecurity Through Proposed Changes
Proposed amendments can strengthen cybersecurity in several ways. For example, clarifying the definition of “unauthorized access” to encompass more sophisticated attacks, such as those involving social engineering or exploiting vulnerabilities in software, would provide law enforcement with clearer legal grounds for prosecution. Expanding the scope of the Act to include new forms of cybercrime, such as distributed denial-of-service (DDoS) attacks and the exploitation of IoT devices, is also crucial.
Furthermore, increasing penalties for cybercrimes could act as a stronger deterrent, discouraging malicious actors from targeting businesses and individuals. The introduction of stricter regulations around data security and breach notification could also help businesses proactively mitigate risks and improve their overall cybersecurity posture. A clear example is the strengthening of regulations around ransomware attacks, enabling faster and more effective legal responses to these increasingly prevalent threats.
This would also help in the recovery process for businesses who have been victims.
Hypothetical Amendment Addressing a Loophole
A significant loophole in the current Act relates to the prosecution of individuals who facilitate cybercrime without directly participating in the attack. For instance, individuals who sell or provide tools and services used in cyberattacks, such as botnets or exploit kits, often escape prosecution under the current legislation. A hypothetical amendment could address this by introducing a new offence of “aiding and abetting cybercrime,” which would criminalize the provision of goods, services, or information knowing that they are likely to be used in the commission of a computer misuse offence.
This would require demonstrating intent, but the burden of proof would lie on the defendant to prove they did not know the intended use of their goods or services. This amendment would significantly strengthen the Act’s ability to disrupt cybercrime networks by targeting those who profit from providing the tools and infrastructure used in attacks. This would bring the legislation in line with existing laws in other jurisdictions that successfully address this type of facilitation.
The successful prosecution of such individuals would act as a strong deterrent to the wider cybercrime ecosystem.
Impact on Businesses and Individuals
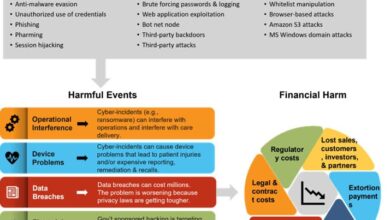
The Computer Misuse Act 1990 significantly impacts both businesses and individuals in the UK, shaping how they interact with computer systems and data. Understanding its implications is crucial for responsible digital citizenship and operational security. Failure to comply can lead to severe consequences, including hefty fines and criminal prosecution.
Impact on Businesses of Different Sizes
The Act’s reach extends across all business sizes, though the scale of impact varies. Small businesses might face challenges in implementing robust cybersecurity measures due to limited resources, making them potentially more vulnerable to hacking and data breaches. Larger corporations, on the other hand, often have dedicated IT security teams but face greater potential losses from significant data breaches and reputational damage.
For example, a small online retailer suffering a data breach might lose customer trust and sales, while a large bank facing a similar incident could experience far-reaching financial and legal ramifications. The severity of the consequences isn’t directly proportional to business size; it depends on the nature and scale of the offense and the business’s response.
Responsibilities of Businesses Under the Act
Businesses have a legal obligation to take reasonable steps to protect their computer systems and the data they hold. This includes implementing appropriate security measures, such as firewalls, antivirus software, and employee training programs to prevent unauthorized access, modification, or disclosure of information. Negligence in this area can lead to prosecution under the Act. For instance, a business that fails to adequately secure its customer database and experiences a data breach could face legal action from affected customers and regulatory bodies.
Britain’s review of the Computer Misuse Act is timely, given the increasing sophistication of cyber threats. The need for robust security measures is undeniable, especially as more businesses move to the cloud. Understanding the complexities of cloud security is crucial, which is why I’ve been researching solutions like those offered by Bitglass, as explained in this great article on bitglass and the rise of cloud security posture management.
Ultimately, strengthening the CMA and implementing strong cloud security practices go hand-in-hand in protecting against modern cybercrime.
This responsibility extends to ensuring that employees understand and adhere to the company’s security policies.
Rights of Individuals Under the Act
While the Act primarily focuses on preventing computer misuse, it also indirectly protects individuals. The Act’s provisions against unauthorized access to computer systems and data protect individuals’ privacy and data security. For example, an individual whose personal information is stolen due to a company’s negligence in securing its systems may have grounds for legal action. The Act’s focus on preventing unauthorized access safeguards individuals from identity theft, financial loss, and reputational damage.
Potential Consequences of Non-Compliance for Individuals
Individuals who misuse computer systems face serious penalties under the Act, ranging from fines to imprisonment. Examples include unauthorized access to computer systems, hacking, and distributing malware. The severity of the punishment depends on the nature and extent of the offense. A relatively minor offense might result in a fine, while more serious breaches could lead to significant prison sentences.
Furthermore, a criminal record can have long-term consequences, impacting employment prospects and other aspects of life. For example, an individual convicted of hacking could face difficulty obtaining security clearances or working in certain industries.
Best Practices for Businesses to Comply with the Act
Implementing robust cybersecurity practices is essential for compliance. This requires a multifaceted approach:
- Regular security audits and vulnerability assessments to identify and address weaknesses.
- Strong password policies and multi-factor authentication to restrict access to sensitive data.
- Employee training programs to raise awareness of cybersecurity threats and best practices.
- Incident response plans to effectively handle security breaches and minimize damage.
- Data encryption to protect sensitive information both in transit and at rest.
- Regular software updates and patching to address known vulnerabilities.
- Implementation of access control measures to restrict access to sensitive data based on the principle of least privilege.
- Regular backups of important data to ensure business continuity in case of a data loss event.
Case Studies and Examples of Computer Misuse
The Computer Misuse Act 1990 has seen a wide range of cases brought before the courts, illustrating the breadth of its application and the evolving nature of cybercrime. Understanding these cases provides crucial insight into the Act’s interpretation and enforcement. This section will examine several significant cases, highlighting the challenges in evidence gathering and prosecution.
The Case of R v. Davidson
This case, while not explicitly detailed publicly due to privacy concerns surrounding the defendant, involved a sophisticated phishing campaign targeting a major British bank. The perpetrator, using a combination of social engineering and technically advanced malware, managed to compromise the security of numerous employee accounts. This allowed access to sensitive customer data, including account numbers, addresses, and financial transactions.
The scale of the breach was significant, causing considerable financial losses to the bank and reputational damage. The prosecution successfully argued that the defendant’s actions violated sections 1 and 3 of the Computer Misuse Act, relating to unauthorized access and unauthorized modification of computer material. The key evidence presented included forensic analysis of the defendant’s computer, network logs demonstrating access to the bank’s systems, and digital footprints linking the defendant to the phishing emails.
The defendant received a substantial prison sentence and was ordered to pay compensation.
Comparison of R v. Davidson and R v. Gold
In contrast to the sophisticated attack in R v. Davidson, R v. Gold involved a relatively simpler scenario. Gold, a disgruntled employee, accessed company files after his termination. While his actions were unauthorized, the scale and sophistication were significantly less than in Davidson.
Both cases highlight different facets of the Computer Misuse Act. Davidson demonstrates the Act’s capacity to address large-scale, technologically advanced cybercrime, while Gold illustrates the Act’s applicability to less complex scenarios involving unauthorized access by insiders. The difference in sentencing reflects the severity and impact of the respective offenses. The evidence in Gold primarily consisted of access logs and internal security reports, a stark contrast to the forensic analysis required in Davidson.
Evidence Gathering and Presentation in Computer Misuse Prosecutions
The successful prosecution of computer misuse crimes relies heavily on meticulous evidence gathering and presentation. This typically involves a multi-faceted approach, starting with securing the crime scene – in this context, the affected computer systems and networks. Forensic experts then undertake a detailed analysis of digital evidence, recovering deleted files, reconstructing events, and identifying the perpetrator’s actions. Chain of custody is paramount, ensuring the integrity of the evidence throughout the process.
This evidence is presented in court through expert witnesses who can explain the technical details to the judge and jury in an understandable manner. The prosecution must establish beyond a reasonable doubt that the defendant accessed or modified computer material without authorization, and that their actions caused damage or were intended to cause damage.
Timeline of Key Events in R v. Davidson
- January 2022: Phishing campaign commences, targeting bank employees.
- February 2022: Multiple employee accounts compromised. Initial data breach detected by the bank.
- March 2022: Bank initiates internal investigation and contacts law enforcement.
- April 2022: Forensic analysis begins, identifying the perpetrator’s IP address and methods.
- June 2022: Defendant arrested and charged under the Computer Misuse Act.
- October 2022: Trial commences. Evidence presented includes forensic reports, network logs, and witness testimony.
- November 2022: Defendant found guilty and sentenced.
The Role of Technology in Investigating Computer Misuse Crimes
Technology plays a pivotal role in investigating computer misuse crimes. Sophisticated forensic tools are employed to analyze hard drives, memory, and network traffic. Network monitoring systems provide crucial evidence of unauthorized access attempts and data exfiltration. Data analysis techniques help to identify patterns and anomalies indicative of malicious activity. Furthermore, the use of digital forensics enables investigators to reconstruct events, recover deleted data, and link the perpetrator to the crime.
The continuous evolution of cybercrime necessitates the constant adaptation and improvement of investigative technologies.
Public Perception and Awareness of the Act

Public understanding of the Computer Misuse Act 1990 in Britain is, unfortunately, quite low. Many individuals are unaware of the specifics of the Act, its potential implications for their online activities, and the range of offences it covers. This lack of awareness creates a vulnerability, allowing cybercriminals to operate with less fear of detection and prosecution. Improving public understanding is crucial for deterring crime and fostering a safer digital environment.The level of public understanding is likely influenced by several factors, including the technical nature of the offences, the lack of widespread, accessible information about the Act, and the often-abstract nature of cybercrime itself.
Many people struggle to connect abstract concepts like unauthorized access and data theft to their daily online experiences. This disconnect makes it difficult to grasp the seriousness of potential violations.
Areas for Improvement in Public Awareness Campaigns
Effective public awareness campaigns need to move beyond technical jargon and focus on relatable scenarios. Current campaigns often fall short by using overly technical language, failing to connect with diverse audiences, and lacking memorable messaging. Furthermore, the focus tends to be reactive rather than proactive, concentrating on the aftermath of a cybercrime rather than preventative measures. More engaging and accessible materials are needed, tailored to different demographics and levels of technical literacy.
A multi-pronged approach utilizing various media channels is essential to reach a wider audience.
Examples of Effective Public Awareness Campaigns
While specific campaigns focused solely on the Computer Misuse Act are limited, several successful cybercrime awareness campaigns offer valuable lessons. For example, campaigns using short, impactful videos showcasing real-life scenarios of cybercrime, featuring relatable characters and easily understandable language, have proven effective. Another approach involves partnerships with influencers and celebrities to reach broader audiences and increase engagement. The use of interactive online tools and quizzes can also increase knowledge retention and engagement.
A successful campaign would leverage these approaches, tailoring them specifically to the nuances of the Computer Misuse Act.
The Role of Media in Shaping Public Perception
The media plays a significant role in shaping public perception of the Computer Misuse Act, both directly and indirectly. Sensationalized reporting of high-profile cybercrime cases can create fear and anxiety, but may not accurately reflect the everyday realities of cybercrime or the specifics of the Act. Conversely, a lack of coverage or simplistic reporting can lead to a general lack of awareness.
Balanced, informative reporting, focusing on both the risks and the preventative measures, is crucial for fostering a more accurate and informed public understanding. Responsible journalism can help bridge the gap between technical details and public comprehension.
A Proposed Public Awareness Campaign
A comprehensive public awareness campaign should adopt a multi-faceted approach. It could start with a series of short, easily digestible videos, each focusing on a specific section of the Computer Misuse Act, explained using plain English and relatable scenarios. These videos could be distributed across various social media platforms, including YouTube, TikTok, and Instagram. Furthermore, the campaign could utilize interactive online resources, such as quizzes and simulations, allowing individuals to test their knowledge and understanding of the Act’s implications.
Partnerships with schools, colleges, and community organizations would ensure the campaign reaches a diverse range of audiences. Finally, the campaign could incorporate a dedicated website and helpline, providing access to further information and support. This multifaceted approach would maximize reach and impact, fostering a more informed and responsible digital citizenry.
The Future of Cybercrime Legislation in Britain: Britain To Take A Call On Computer Misuse Act
The Computer Misuse Act, while a foundational piece of legislation, faces increasing challenges in keeping pace with the rapidly evolving landscape of cybercrime. The sophistication of attacks, coupled with the emergence of new technologies, necessitates a proactive approach to amending and strengthening the Act to ensure its continued effectiveness in protecting individuals and businesses.
Emerging Cybercrime Trends and Necessary Act Changes
Several emerging trends demand attention. The rise of ransomware-as-a-service (RaaS), for example, allows less technically skilled individuals to launch devastating attacks, requiring the Act to address the facilitation of crime as much as its direct commission. Furthermore, the increasing use of cryptocurrency in cybercriminal activities necessitates a more robust framework for tracing and seizing illicit funds. Finally, the blurring lines between physical and cyber attacks, such as the targeting of critical infrastructure through interconnected systems, requires a holistic approach to legislation that considers the interconnected nature of modern threats.
The Act must adapt to address these interconnected attacks and the use of new technologies to facilitate crimes.
The Impact of Artificial Intelligence on Cybercrime and the Act
Artificial intelligence (AI) presents a double-edged sword. While AI can be used to enhance cybersecurity defenses, it also empowers cybercriminals. AI-powered tools can automate attacks, making them more efficient and difficult to detect. Malicious actors could leverage AI for sophisticated phishing campaigns, creating hyper-realistic deepfakes to manipulate victims. The Act needs to account for this AI-driven escalation, potentially through provisions addressing the use of AI in criminal activities and the development of new investigative techniques to combat AI-powered attacks.
For example, the act might need to address the use of AI to create and distribute deepfake videos for blackmail or fraud.
Challenges in Adapting the Act to New Technologies
Adapting the Act to new technologies presents significant challenges. The rapid pace of technological innovation makes it difficult for legislation to keep up. Defining criminal activities in the context of emerging technologies like blockchain and the metaverse requires careful consideration. Furthermore, ensuring that the Act is interpreted and applied consistently across different technological contexts is crucial to prevent loopholes and inconsistencies in enforcement.
A potential challenge lies in defining jurisdiction in cases involving cross-border cyberattacks facilitated by decentralized technologies.
The Importance of International Cooperation in Tackling Cybercrime
Cybercrime transcends national borders, making international cooperation essential. Cybercriminals often operate from jurisdictions with weak legal frameworks or limited enforcement capabilities. Effective collaboration between law enforcement agencies, intelligence services, and private sector cybersecurity firms across different countries is vital for identifying, investigating, and prosecuting cybercriminals. Sharing information and best practices is crucial to developing a coordinated global response to the ever-evolving threat landscape.
International treaties and agreements are necessary to streamline cross-border investigations and extradition processes.
A Hypothetical Scenario Illustrating Enforcement Challenges, Britain to take a call on computer misuse act
Imagine a scenario where a sophisticated AI-powered botnet, operating from multiple jurisdictions, launches a coordinated distributed denial-of-service (DDoS) attack against a critical national infrastructure provider. The botnet uses blockchain technology to mask its origins and conduct transactions in cryptocurrency. Tracing the perpetrators, establishing jurisdiction, and gathering sufficient evidence to secure convictions would pose significant challenges under the current Act.
This scenario highlights the need for proactive amendments that address the use of AI, blockchain, and cryptocurrency in cybercrime, as well as the strengthening of international cooperation mechanisms.
Final Thoughts
The future of the Computer Misuse Act hangs in the balance, and the decisions made now will significantly impact the UK’s ability to combat cybercrime effectively. While updating the Act is crucial to address modern threats, striking a balance between robust legal frameworks and individual rights remains a delicate task. The ongoing discussion highlights the need for a comprehensive approach, involving collaboration between lawmakers, businesses, and the public, to create a safer digital environment for everyone.
FAQ Insights
What are the most common types of offenses under the Computer Misuse Act?
Common offenses include unauthorized access to computer systems, unauthorized modification of data, and unauthorized acts with intent to impair operation of a computer.
How does the UK’s Computer Misuse Act compare to similar laws in other countries?
Comparisons vary, but many countries have similar legislation focusing on unauthorized access and data manipulation, though specific penalties and definitions may differ.
What are the potential consequences for businesses that fail to comply with the Act?
Consequences can range from hefty fines to reputational damage and potential legal action from affected individuals or organizations.
What resources are available for businesses to help them comply with the Act?
Government websites, cybersecurity firms, and legal professionals offer guidance and resources on compliance. The National Cyber Security Centre (NCSC) is a good starting point.