Business Email Compromise Simple, Destructive, Preventable
Business email compromise bec attacks are deceptively simple and destructive protecting your business – Business email compromise (BEC) attacks are deceptively simple and destructive, yet protecting your business from them is entirely possible. These attacks, often involving sophisticated social engineering, prey on human trust and organizational weaknesses to extract significant financial losses. Think of it like a digital heist, where the thieves are incredibly cunning and your employees might unknowingly become their accomplices.
This post dives into understanding BEC attacks, identifying red flags, implementing preventative measures, and responding effectively to an incident. We’ll explore the technical aspects, the human element, and the crucial role of proactive security strategies in safeguarding your business from this increasingly prevalent threat.
Understanding Business Email Compromise (BEC) Attacks: Business Email Compromise Bec Attacks Are Deceptively Simple And Destructive Protecting Your Business
Business Email Compromise (BEC) attacks are a sophisticated form of cybercrime that targets organizations by exploiting their internal communication systems. These attacks leverage social engineering techniques to trick employees into transferring funds or revealing sensitive information, resulting in significant financial losses and reputational damage. Understanding the mechanics of these attacks is crucial for developing effective preventative measures.BEC attacks typically unfold in a series of stages.
Business Email Compromise (BEC) attacks are terrifyingly easy to fall for, causing massive damage. Strengthening your defenses is crucial, and a key part of that involves securing your cloud infrastructure. Understanding the importance of cloud security is paramount, which is why I recommend checking out this article on bitglass and the rise of cloud security posture management to see how it helps protect against sophisticated threats like BEC.
Ultimately, a strong cloud security posture is your first line of defense against these deceptively simple, yet devastating attacks.
Initially, attackers conduct extensive reconnaissance, gathering information about the target organization and its employees through publicly available sources or social media. This information is then used to craft highly convincing phishing emails or spoofed communications that appear to originate from legitimate sources within the organization or trusted external partners.
BEC Attack Vectors
The success of a BEC attack hinges on the attacker’s ability to convincingly impersonate a trusted individual or entity. Several common attack vectors are employed:
- Phishing Emails: These emails often mimic legitimate requests, such as invoices, payment reminders, or urgent requests for wire transfers. They contain malicious links or attachments designed to install malware or steal credentials.
- Spoofed Emails: Attackers forge email headers to make it appear as though the email originates from a known and trusted sender, such as a senior executive or a business partner. This technique leverages the recipient’s trust in the apparent sender.
- Compromised Accounts: In some cases, attackers gain unauthorized access to legitimate email accounts within the target organization. This allows them to send fraudulent communications directly from the compromised account, making the attack even more difficult to detect.
Real-World Case Studies, Business email compromise bec attacks are deceptively simple and destructive protecting your business
Numerous real-world examples highlight the devastating impact of BEC attacks. One notable case involved a large manufacturing company that lost millions of dollars after an employee transferred funds to an account controlled by attackers who had successfully impersonated a senior executive via email. Another example saw a law firm fall victim to a BEC attack, resulting in the theft of confidential client information and significant legal repercussions.
These incidents demonstrate the potential for severe financial and reputational consequences.
Comparison of BEC Attack Types
The following table compares different types of BEC attacks, their success rates (estimated based on industry reports and publicly available data), and potential prevention strategies. Note that success rates are difficult to precisely quantify due to underreporting and the evolving nature of these attacks.
| Attack Type | Method | Success Rate (Estimate) | Prevention Strategies |
|---|---|---|---|
| Invoice Fraud | Spoofed email mimicking a vendor invoice | 15-25% | Verify invoices through multiple channels, implement strong authentication |
| CEO Fraud | Email impersonating a CEO requesting urgent wire transfer | 10-20% | Implement multi-factor authentication, establish verification protocols |
| Account Takeover | Compromised email account used to send fraudulent requests | 5-15% | Strong password policies, regular security awareness training |
| Fake Payment Request | Email requesting payment to a fraudulent account | 20-30% | Use secure payment platforms, verify payment details independently |
Identifying and Preventing BEC Attacks
Business Email Compromise (BEC) attacks are sophisticated scams that exploit trust and organizational processes. They’re incredibly damaging, often resulting in significant financial losses and reputational harm. Understanding the subtle signs of a BEC email and implementing robust preventative measures are crucial for protecting your business. This section will detail how to identify these attacks and build a stronger defense.
Common Indicators of BEC Emails
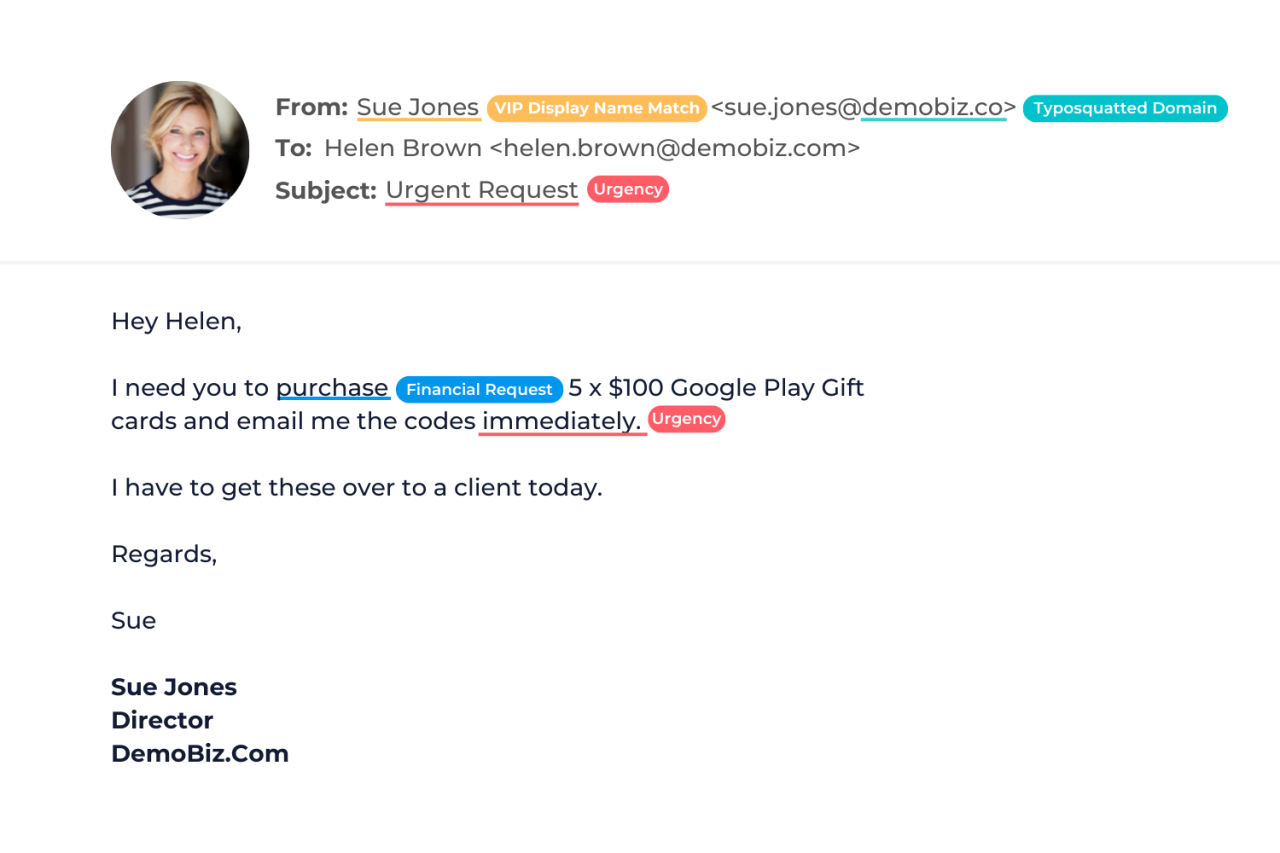
BEC emails are designed to appear legitimate, making detection challenging. However, careful scrutiny can reveal subtle clues. Look for inconsistencies in email addresses, slightly altered company logos or branding, unusual urgency in requests, and grammatical errors or inconsistencies in tone. For example, a fraudulent email might use a similar-looking email address to a legitimate one, such as “[email protected]” instead of “[email protected],” or a slightly misspelled company name in the sender’s display name.
A sense of urgency, often involving immediate payment or wire transfers, is another major red flag. Finally, inconsistencies in language and tone—a formal email suddenly switching to casual language, for instance—can also be a warning sign. Always verify requests independently, even if they seem to come from a trusted source.
Email Authentication Protocols: SPF, DKIM, and DMARC
Implementing email authentication protocols is a critical step in preventing BEC attacks. These protocols help verify the sender’s identity and prevent spoofing. SPF (Sender Policy Framework) verifies that the sender’s email address is authorized to send emails on behalf of the domain. DKIM (DomainKeys Identified Mail) uses digital signatures to authenticate emails, ensuring they haven’t been tampered with.
DMARC (Domain-based Message Authentication, Reporting & Conformance) builds on SPF and DKIM by providing instructions on how to handle emails that fail authentication, such as quarantining or rejecting them. By implementing all three protocols, businesses significantly reduce their vulnerability to BEC attacks. These protocols act as a multi-layered security system, checking multiple points of origin and integrity to confirm the authenticity of an email.
Security Measures to Prevent BEC Attacks
Implementing a comprehensive security strategy is essential to protect against BEC attacks. This requires a multi-faceted approach, including technical safeguards and employee training.
- Strong Password Policies: Enforce strong, unique passwords for all accounts and encourage regular password changes.
- Multi-Factor Authentication (MFA): Implement MFA for all email accounts and other critical systems to add an extra layer of security.
- Email Security Solutions: Utilize advanced email security solutions that can detect and block phishing attempts and malicious attachments.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure that security measures are up-to-date and effective.
- Employee Training: Conduct regular employee training to raise awareness of BEC attacks and best practices for email security.
- Verification Procedures: Establish clear procedures for verifying email requests, especially those involving financial transactions. Never rely solely on email communication for sensitive information.
Employee Training Modules on BEC Awareness
Effective employee training is crucial in combating BEC attacks. A comprehensive training program should include:
- Phishing Simulations: Regularly conduct phishing simulations to test employees’ ability to identify and report suspicious emails.
- BEC Awareness Training: Provide training on identifying common characteristics of BEC emails, including subtle cues and red flags.
- Best Practices for Email Security: Educate employees on secure email practices, such as verifying sender identities and avoiding clicking on suspicious links or attachments.
- Reporting Procedures: Establish clear procedures for reporting suspicious emails and incidents.
- Reinforcement and Updates: Regularly reinforce training with updates and reminders to maintain vigilance against evolving threats.
Responding to a BEC Attack
A Business Email Compromise (BEC) attack can inflict significant financial and reputational damage. Swift and decisive action is crucial to minimize losses and prevent further compromise. This section Artikels the critical steps to take when facing a suspected or confirmed BEC attack.
The initial response to a BEC attack needs to be both rapid and methodical. Panicking will only hinder effective action. Instead, focus on immediate containment and preservation of evidence. Remember, the longer the attack goes undetected, the greater the potential damage.
Immediate Actions Upon Suspecting a BEC Attack
The first few hours are critical. Immediately quarantine all potentially compromised email accounts and systems. This prevents further unauthorized access and data exfiltration. Simultaneously, initiate a thorough review of recent financial transactions, looking for any unusual or unauthorized payments. Document everything meticulously, including screenshots and email headers.
This documentation will be essential for both internal investigation and reporting to law enforcement. Consider freezing any accounts suspected of being compromised to prevent further financial losses.
Reporting a BEC Attack to Law Enforcement and Relevant Authorities
Reporting is a vital step in mitigating damage and potentially recovering lost funds. Contact your local FBI field office (in the US) or your country’s equivalent cybercrime unit. Provide them with all the documentation you’ve gathered: compromised emails, transaction records, and any other relevant information. They can guide you through the investigation process and may be able to assist in recovering funds.
Business Email Compromise (BEC) attacks are terrifyingly effective because they’re so simple; a cleverly crafted email can wipe out your finances. Strengthening your defenses requires a multi-pronged approach, including robust security training and reliable systems. This is where streamlined development comes in; exploring options like those detailed in this article on domino app dev the low code and pro code future can help you build more secure, efficient internal processes, making your business less vulnerable to BEC scams.
Ultimately, protecting your business from BEC requires vigilance and smart technology choices.
Additionally, inform your financial institutions about the attack, providing them with details to help them identify and block fraudulent transactions. Depending on the scale and impact of the attack, you may also need to notify your insurance provider and any relevant regulatory bodies.
A step-by-step procedure might look like this:
- Gather all relevant documentation (emails, transaction records, etc.).
- Contact your local FBI field office (or equivalent agency in your country).
- Provide the agency with all gathered documentation and answer their questions thoroughly.
- Contact your financial institutions to report the fraudulent transactions.
- Notify your insurance provider and any relevant regulatory bodies as needed.
- Maintain detailed records of all communication and actions taken.
Containing the Damage and Mitigating Further Financial Losses
Once the immediate response is underway, the focus shifts to damage control. This involves assessing the extent of the breach, identifying affected systems and accounts, and implementing measures to prevent further compromise. This may include password resets for all affected accounts, updating security software, and reviewing and strengthening internal security policies. Engage cybersecurity professionals to conduct a thorough forensic investigation to identify vulnerabilities and prevent future attacks.
They can also help recover lost data if possible. Closely monitor financial accounts for any further unauthorized activity.
Incident Response Plan
A well-defined incident response plan is crucial for effectively handling a BEC attack. This plan should Artikel roles, responsibilities, and communication protocols.
Here’s an example of an incident response plan:
- Incident Response Team: This team should include representatives from IT, finance, legal, and communications departments.
- Communication Protocol: Establish clear communication channels and protocols to ensure timely and efficient information sharing among team members and external stakeholders (law enforcement, etc.).
- Incident Reporting Procedures: Define clear steps for reporting suspected BEC attacks, including contact information for relevant personnel and authorities.
- Containment Procedures: Artikel steps for isolating affected systems and accounts to prevent further damage.
- Recovery Procedures: Detail steps for restoring affected systems and data, including data backups and recovery plans.
- Post-Incident Activities: Define procedures for conducting a post-incident review to identify lessons learned and improve future response efforts.
The Role of Technology in BEC Prevention

Business Email Compromise (BEC) attacks are sophisticated and increasingly prevalent, making technological defenses crucial for mitigating risk. While employee training is vital, technology provides the first line of defense, automatically identifying and blocking many threats before they even reach human eyes. A layered approach, combining various technologies, offers the strongest protection.Advanced threat detection systems play a critical role in identifying and neutralizing BEC attacks.
These systems utilize machine learning algorithms and behavioral analysis to detect anomalies in email traffic that are indicative of malicious activity. They can identify suspicious email patterns, such as unusual sender addresses, unexpected attachments, or unusual language in the body of the email, flagging them for further review or automatically blocking them. This proactive approach significantly reduces the chances of a successful BEC attack.
Advanced Threat Detection Systems
Advanced threat detection systems leverage several techniques to identify BEC attempts. For example, they analyze email headers for inconsistencies, such as discrepancies between the displayed sender name and the actual email address. They also look for unusual communication patterns, such as sudden changes in communication frequency or subject matter with a known contact. Furthermore, these systems often incorporate sandboxing technology, which analyzes suspicious attachments in a safe, isolated environment to detect malicious code before it can execute.
The speed and automation of these systems are key to their effectiveness, enabling immediate responses to threats. For instance, a system might automatically quarantine an email exhibiting multiple suspicious characteristics, preventing it from reaching the intended recipient.
Email Security Solutions Comparison
Several email security solutions exist, each with its strengths and weaknesses. Traditional spam filters, while effective against basic spam, often struggle with sophisticated BEC attacks that mimic legitimate communications. More advanced solutions incorporate techniques like DMARC (Domain-based Message Authentication, Reporting & Conformance), SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) to authenticate email sender identities, helping to prevent spoofing.
Cloud-based email security solutions offer scalability and often include features such as data loss prevention (DLP) and advanced threat protection, providing a comprehensive approach. On-premise solutions offer greater control but require more significant investment in infrastructure and maintenance. The best solution depends on an organization’s size, budget, and technical expertise.
Anti-Phishing Software and Email Filtering Systems
Effective anti-phishing software and email filtering systems go beyond basic spam filtering. Key features include URL analysis to detect malicious links, heuristic analysis to identify suspicious email content based on patterns and language, and real-time threat intelligence feeds to stay ahead of emerging threats. These systems often incorporate machine learning to adapt to evolving phishing techniques and improve their accuracy over time.
A crucial element is the ability to train the system with organization-specific data, enabling it to identify patterns and anomalies unique to the company’s communication patterns. For example, a system trained on typical internal email communication styles will be better equipped to detect deviations that might indicate a BEC attempt.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) significantly reduces the risk of BEC attacks by adding an extra layer of security beyond passwords. Even if an attacker obtains an employee’s login credentials through phishing, they will still need access to a second factor, such as a one-time code sent to a mobile phone or a security token, to gain access to the account.
This significantly increases the difficulty for attackers and makes successful BEC attempts much less likely. The widespread adoption of MFA across all organizational systems is a crucial step in bolstering security against BEC and other cyber threats. Organizations should prioritize implementing MFA for all employees with access to sensitive information and financial systems.
The Human Element in BEC Attacks
Business Email Compromise (BEC) attacks aren’t just about sophisticated technology; they’re a masterclass in psychological manipulation, preying on human weaknesses and ingrained trust. Understanding these psychological tactics is crucial to building a robust defense against BEC, because ultimately, it’s the human element that makes these attacks successful. The attackers don’t rely solely on technical prowess; they leverage our natural tendencies to trust, to act quickly, and to follow instructions from perceived authority figures.BEC attacks thrive on exploiting common human vulnerabilities.
Attackers often employ urgency, leveraging fear of missing out (FOMO) or the threat of immediate negative consequences. They craft believable narratives, often impersonating executives or trusted business partners, to build confidence and elicit compliance. This carefully constructed narrative, combined with the pressure to act quickly, bypasses rational decision-making processes and triggers impulsive actions. The pressure of deadlines, coupled with the perceived authority of the sender, overrides critical thinking, making employees vulnerable to the attackers’ schemes.
Psychological Manipulation Techniques in BEC Attacks
BEC attackers utilize a range of psychological manipulation techniques to increase their success rate. These include creating a sense of urgency, leveraging authority figures, and employing social engineering tactics to gain trust. For example, an attacker might impersonate a CEO requesting an urgent wire transfer, emphasizing the dire consequences of delay. The use of official-looking email addresses and logos further enhances the credibility of the fraudulent request.
The pressure of a supposed deadline combined with the perceived authority of the sender significantly increases the likelihood of the employee complying without verification. This underscores the importance of fostering a culture of skepticism and verification within the organization.
The Importance of Employee Training and Awareness Programs
Robust employee training and awareness programs are the first line of defense against BEC attacks. These programs should go beyond simple awareness campaigns; they need to actively engage employees and equip them with the skills to identify and respond to suspicious emails. Training should cover common tactics used by attackers, including impersonation, urgency, and social engineering. Regular refresher courses and simulated phishing exercises are also crucial to maintaining vigilance and reinforcing learned behaviors.
A strong security culture that encourages employees to question requests and report suspicious activity is essential.
Scenario: A Successful BEC Attack and its Prevention
Imagine Sarah, a junior accountant at a mid-sized company. She receives an email seemingly from her CEO, requesting an urgent wire transfer of a substantial sum to a foreign account. The email is well-crafted, using the CEO’s name and company logo. It emphasizes the confidentiality of the transaction and the dire consequences of delay. Sarah, under pressure and trusting the sender, processes the wire transfer without verification.
The money is lost, and the company suffers significant financial damage.Had Sarah received thorough training on BEC attacks, she would have been aware of the common tactics used by attackers. She would have known to verify the request through an independent channel, such as a phone call to the CEO, before processing the transfer. This simple verification step could have prevented the entire incident.
The training would have also empowered her to report the suspicious email immediately, allowing the company to take preventative measures.
Effective Communication Strategies for BEC Awareness
Effective communication is paramount in educating employees about BEC threats. Regular security awareness newsletters, engaging training videos, and interactive workshops can significantly improve employee awareness. These materials should use real-world examples and case studies to illustrate the potential consequences of BEC attacks. The use of clear and concise language, avoiding technical jargon, is essential for effective communication.
Furthermore, establishing a clear reporting mechanism for suspicious emails and providing regular updates on emerging threats will encourage employee participation and enhance the overall security posture. A culture of open communication and collaboration is crucial in fostering a strong security environment.
Closing Notes
In the ever-evolving landscape of cyber threats, BEC attacks remain a significant concern for businesses of all sizes. While the methods may seem deceptively simple, the consequences can be devastating. By understanding the mechanics of these attacks, implementing robust security measures, and fostering a culture of cybersecurity awareness among employees, businesses can significantly reduce their vulnerability. Remember, vigilance, proactive security, and employee training are your strongest defenses against the insidious threat of BEC.
Don’t wait for an attack to happen; proactively protect your business today.
Common Queries
What is the average financial loss from a successful BEC attack?
The average loss varies greatly depending on the size of the business and the sophistication of the attack, but reports indicate losses can range from thousands to millions of dollars.
Can insurance cover BEC losses?
Some cyber insurance policies may cover losses resulting from BEC attacks, but coverage details vary widely. It’s crucial to review your policy carefully.
How often should employees receive BEC awareness training?
Regular, ongoing training is recommended, ideally including refresher courses at least annually and incorporating simulated phishing exercises.
Are there any free tools available to help detect BEC attempts?
While many sophisticated tools are paid, some email providers offer basic phishing detection features. There are also free resources and checklists available online to help businesses improve their email security posture.