California Passes a Bill to Ban Traditional Passwords
California passes a bill to ban traditional passwords – can you believe it? This groundbreaking legislation is poised to reshape online security in the Golden State, potentially sparking a nationwide shift away from the passwords we’ve all grown to love (or hate). It’s a huge step, and the implications are far-reaching, impacting everything from how we log into our bank accounts to the security measures businesses must implement.
Get ready for a deep dive into the world of passwordless authentication!
The bill Artikels a phased approach, giving businesses time to adapt. But the real question is: are we ready for a password-free future? This post will explore the pros and cons, the technological hurdles, and the potential impact on both individual users and the broader economy. We’ll also look at alternative authentication methods, the security implications, and the public’s reaction to this bold move.
Buckle up!
Bill Overview and Implications
California’s groundbreaking legislation, aiming to phase out traditional passwords, represents a significant shift in online security and user experience. While the specifics are still unfolding, the bill’s core aim is to enhance data protection and reduce the vulnerability of Californians to cyberattacks. This move reflects a growing global concern over password-based security’s inherent weaknesses.The bill, once fully enacted, will mandate that businesses operating in California transition away from password-based authentication for their users.
This doesn’t necessarily mean an immediate ban, but rather a phased approach encouraging the adoption of more robust authentication methods. The exact details regarding the timeline and acceptable alternatives are still being finalized, but it’s likely to involve a period of transition, allowing businesses time to adapt their systems and user interfaces.
Timeline for Implementation
The exact timeline for implementation remains uncertain, as the bill is still undergoing the final stages of legislative review and approval. However, based on similar legislation in other jurisdictions, we can anticipate a phased rollout. This might involve a grace period of several years, starting with larger businesses and gradually extending to smaller organizations. Initial phases might focus on education and awareness campaigns for both businesses and consumers, followed by stricter enforcement down the line.
Expect regular updates and announcements from the California state government regarding the precise dates and milestones.
Economic Impacts on California Businesses
The transition to passwordless authentication will undoubtedly carry economic implications for businesses operating in California. Upgrading systems, training employees, and integrating new authentication technologies will require significant investment. Smaller businesses, in particular, may face challenges in affording these upgrades. However, the long-term benefits of enhanced security and reduced liability from data breaches could outweigh the initial costs.
For example, companies like LastPass, specializing in password management, might see a decrease in demand, while firms providing biometric authentication or multi-factor authentication solutions are likely to experience increased business. The overall economic impact will depend heavily on the pace of implementation and the level of government support offered to assist businesses during the transition.
Comparison with Similar Initiatives
California’s initiative is not an isolated case. Several other states and countries are exploring or implementing similar legislation aimed at enhancing online security. For example, the European Union’s General Data Protection Regulation (GDPR) indirectly encourages stronger authentication methods, although it doesn’t explicitly ban passwords. Similarly, some countries are already pushing for the widespread adoption of digital identity systems that rely on less vulnerable authentication techniques.
While the specific approaches vary, the common thread is a growing recognition of the limitations of traditional passwords and a concerted effort to move towards more secure alternatives.
Effects on User Experience and Online Security
The shift away from passwords has the potential to significantly improve user experience and enhance online security. Password fatigue and the risk of phishing attacks are major concerns with traditional password systems. Passwordless authentication methods, such as biometric authentication (fingerprint, facial recognition) or multi-factor authentication (using a combination of methods), offer a more convenient and secure alternative. While some users might initially be resistant to change, the long-term benefits of increased security and reduced frustration from forgotten or compromised passwords should outweigh the initial learning curve.
However, careful consideration must be given to accessibility issues to ensure that all users can benefit from these new systems. For example, users with disabilities might require alternative authentication methods to be fully included.
Alternative Authentication Methods: California Passes A Bill To Ban Traditional Passwords
California’s move towards a password-free future necessitates a closer look at the authentication methods poised to replace them. This shift promises enhanced security and user experience, but also presents significant challenges in implementation and adoption. Exploring the various alternatives, their strengths and weaknesses, is crucial to understanding the implications of this landmark legislation.
Biometric Authentication: Advantages and Disadvantages
Biometric authentication, using unique biological traits for verification, offers a compelling alternative to passwords. Fingerprint scanning, facial recognition, and iris scanning are common examples. The advantages are clear: increased security (difficult to replicate biological traits), improved user experience (no need to remember complex passwords), and potentially reduced fraud. However, disadvantages exist. Privacy concerns surrounding the collection and storage of sensitive biometric data are paramount.
Accuracy can also be an issue, with potential for false positives or negatives leading to user frustration or security breaches. Furthermore, the cost of implementing robust biometric systems can be substantial, and accessibility issues arise for individuals with certain disabilities. For example, a system relying solely on fingerprint recognition would exclude individuals with damaged or missing fingerprints.
Examples of Passwordless Authentication Systems
Several passwordless systems are already available, offering various approaches to secure authentication. One prominent example is using a time-based one-time password (TOTP) generated by an authenticator app on a smartphone. These apps, like Google Authenticator or Authy, generate unique codes that change every few seconds, providing strong security. Another approach involves using a public key infrastructure (PKI) with digital certificates.
This method relies on cryptographic keys for authentication, eliminating the need for passwords entirely. WebAuthn, a standard for creating passwordless credentials, is another example, allowing users to authenticate using their hardware security keys or built-in biometric sensors on their devices. These methods, however, require users to have compatible devices and apps, which poses a challenge for widespread adoption.
Comparison of Multi-Factor Authentication (MFA) Methods
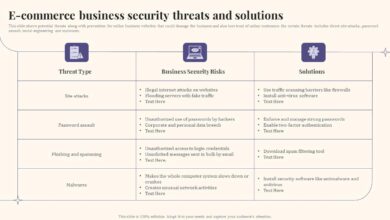
Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple forms of verification. The following table compares several common MFA methods:
| MFA Method | Factor 1 | Factor 2 | Advantages |
|---|---|---|---|
| Password + One-Time Code (OTP) | Something you know (password) | Something you have (OTP from authenticator app) | Widely available, relatively easy to implement |
| Password + Biometrics | Something you know (password) | Something you are (fingerprint, facial recognition) | Strong security, convenient user experience |
| Hardware Security Key | Something you have (security key) | Something you know (PIN or biometric) | High security, resistant to phishing |
| Passwordless with WebAuthn | Something you have (device with WebAuthn support) | Something you are (biometric authentication, if supported) | Strong security, no passwords needed |
Challenges in Widespread Adoption of Passwordless Systems
Despite the benefits, several challenges hinder the widespread adoption of passwordless systems. Firstly, there is a significant learning curve for users unfamiliar with these new technologies. Secondly, compatibility issues across different devices and platforms can create fragmentation and limit usability. Thirdly, the cost of implementing and maintaining secure passwordless infrastructure can be substantial, particularly for smaller organizations.
Finally, the need for user education and support is critical to ensure successful transition and address potential security concerns related to new authentication methods.
Factors Influencing Authentication Method Choice
The choice of authentication method depends on several factors, including the sensitivity of the data being protected, the technical capabilities of the organization, and the user experience requirements. For high-security applications, such as financial transactions, a multi-factor approach combining several authentication methods is often preferred. For less sensitive applications, a simpler method like a password combined with an OTP might suffice.
Cost considerations also play a role, as implementing advanced biometric systems or hardware security keys can be expensive. Finally, user experience should not be overlooked; a complex or inconvenient authentication process can lead to user frustration and ultimately compromise security through workarounds.
Security and Privacy Concerns
California’s ambitious move towards a passwordless future raises legitimate concerns about security and user privacy. While passwords have their own vulnerabilities, the shift to new authentication methods introduces a different set of risks that need careful consideration and robust mitigation strategies. The success of this legislation hinges on effectively addressing these challenges and ensuring a secure and private experience for all Californians.The transition to passwordless systems presents several potential security vulnerabilities.
For example, biometric authentication, while convenient, can be susceptible to spoofing attacks, where an attacker uses a forged biometric sample to gain unauthorized access. Similarly, relying heavily on mobile devices for authentication creates a single point of failure; if a device is lost or compromised, the user’s access is jeopardized. Furthermore, the security of any passwordless system ultimately depends on the security of the underlying infrastructure and the robustness of the authentication protocols used.
A poorly designed or implemented system could be vulnerable to various attacks, including phishing, man-in-the-middle attacks, and sophisticated data breaches.
Vulnerabilities of Alternative Authentication Methods
Biometric authentication, while offering a user-friendly experience, is not without its vulnerabilities. Spoofing attacks, where an attacker uses a fake fingerprint or facial scan, represent a significant threat. For instance, high-resolution photos or 3D-printed fingerprints could potentially bypass some biometric systems. Additionally, the accuracy and reliability of biometric technologies can vary depending on factors like environmental conditions (lighting, temperature) and individual user characteristics.
Similarly, relying on devices for authentication (like smartphones or smartwatches) introduces the risk of device loss or theft. If a device is compromised, an attacker gains access to all associated accounts, making robust device security measures crucial. Finally, the security of any passwordless system rests on the security of the underlying infrastructure. If the servers storing authentication data are breached, user accounts will be compromised regardless of the authentication method used.
Data Protection Measures in a Passwordless Environment
Protecting user data in a passwordless environment requires a multi-layered approach. Robust encryption, both in transit and at rest, is essential to safeguard sensitive authentication data. This includes encrypting biometric templates and other authentication factors before storage. Regular security audits and penetration testing are crucial to identify and address potential vulnerabilities proactively. Furthermore, implementing strong access controls and multi-factor authentication (even within a passwordless system, additional layers of verification can be used) adds an extra layer of security.
Data minimization is also vital; only the necessary data should be collected and stored. The California bill should mandate strict data retention policies and procedures for data deletion to limit the potential damage in case of a breach. Finally, robust incident response plans are essential to quickly contain and mitigate the impact of any security incidents.
Addressing User Privacy Concerns
The California law should explicitly address user privacy concerns by outlining clear guidelines for data collection, storage, and usage. It needs to specify what data is collected, how it’s used, and for how long it’s retained. The principle of data minimization should be central – only essential data should be collected for authentication purposes. Transparency is crucial; users should be clearly informed about what data is being collected and how it’s being used.
The law should also provide mechanisms for users to access, correct, and delete their data. Furthermore, robust data security measures, as described earlier, are essential to prevent unauthorized access or disclosure of personal information. Regular audits and independent reviews of the data handling practices should be mandated to ensure compliance with the law and to maintain public trust.
Privacy Implications: Passwords vs. Passwordless Systems
Traditional passwords, while convenient, are vulnerable to various attacks like phishing and credential stuffing. Password managers, while helpful, can introduce a single point of failure. Passwordless systems, however, shift the focus from memorizing secrets to possessing unique identifiers and relying on devices or biometrics. While this mitigates some risks, it introduces new concerns, particularly around data security and the potential for surveillance.
For instance, the use of biometrics raises questions about data privacy and potential misuse. A well-designed passwordless system with robust security and privacy protections, however, can potentially offer a higher level of security than passwords, reducing the risk of credential theft. The privacy implications of each method must be carefully weighed against the potential benefits. Ultimately, the privacy impact depends on how the system is designed, implemented, and regulated.
Best Practices for Securing Passwordless Authentication Systems
Implementing robust security measures is crucial for a successful transition to passwordless systems. Here are some best practices:
- Employ strong encryption for all authentication data, both in transit and at rest.
- Implement multi-factor authentication (MFA) even within a passwordless framework, adding additional verification layers.
- Regularly conduct security audits and penetration testing to identify and address vulnerabilities.
- Adhere to the principle of data minimization, collecting only the necessary data for authentication.
- Establish clear data retention policies and procedures for secure data deletion.
- Develop comprehensive incident response plans to effectively manage security breaches.
- Ensure compliance with relevant data privacy regulations, such as GDPR and CCPA.
- Provide users with clear and transparent information about data collection and usage practices.
- Offer users control over their data, allowing them to access, correct, and delete their information.
Public Reaction and Debate
California’s proposed password ban has ignited a firestorm of debate, revealing a complex interplay of anxieties and expectations surrounding digital security and user experience. The bill, while aiming for enhanced security, has encountered significant pushback from various stakeholders, highlighting the challenges of transitioning away from a system deeply ingrained in our digital lives.The arguments for and against the ban are sharply defined, often reflecting differing priorities.
Businesses, for example, are concerned about the costs and logistical hurdles of implementing new authentication methods across their systems. Consumers, on the other hand, are grappling with the learning curve associated with passwordless technologies and expressing concerns about potential privacy implications. Security experts, while generally supportive of the move towards passwordless systems, are voicing cautions about the potential vulnerabilities of new technologies and the need for robust security standards.
Stakeholder Perspectives on the Password Ban
Businesses, particularly small and medium-sized enterprises (SMEs), fear the financial burden of upgrading their infrastructure to accommodate passwordless systems. The cost of implementing new authentication methods, training employees, and addressing potential compatibility issues could be substantial, potentially impacting their competitiveness. Larger corporations, while possessing greater resources, also face challenges in migrating their existing systems and ensuring seamless integration with third-party applications.
Consumers, meanwhile, are wary of unfamiliar technologies. Many are accustomed to the (albeit flawed) familiarity of passwords and might resist adopting new authentication methods unless they are demonstrably user-friendly and secure. Security experts acknowledge the inherent weaknesses of passwords, but emphasize the importance of rigorous testing and standardization of passwordless technologies to prevent the emergence of new vulnerabilities.
They also highlight the need for public education to build trust and understanding.
Arguments For and Against the Password Ban
Proponents of the ban argue that passwords are inherently insecure, susceptible to phishing attacks, brute-force attempts, and data breaches. The shift to passwordless systems, they contend, offers a significant leap forward in cybersecurity, reducing the risk of data theft and identity fraud. Opponents, however, raise concerns about the usability and accessibility of passwordless systems, particularly for individuals with limited technical skills or those relying on older devices.
They also highlight the potential for new vulnerabilities and the need for careful consideration of privacy implications. The debate centers around finding a balance between enhanced security and practical usability. For example, the reliance on biometric authentication raises concerns about data privacy and potential biases in biometric recognition systems.
Public Understanding and the Bill’s Success, California passes a bill to ban traditional passwords
The success of the California bill hinges significantly on public understanding and acceptance of passwordless systems. Widespread adoption requires a concerted effort to educate the public about the benefits and limitations of these systems, dispelling common misconceptions and building trust. A lack of understanding could lead to resistance, hindering the transition and potentially jeopardizing the bill’s effectiveness. For example, if the public perceives passwordless systems as more complicated or less secure than passwords, they may be reluctant to adopt them, ultimately undermining the bill’s objectives.
Public Education Campaigns
Successful implementation requires a multi-pronged public education campaign. This could involve: simplified explanations of passwordless technologies, readily available tutorials and support materials, and proactive outreach to vulnerable populations (elderly, low-tech users). Collaborations between government agencies, technology companies, and cybersecurity experts are crucial in creating effective and trustworthy educational resources. Government-sponsored workshops and online resources could significantly improve public understanding and encourage adoption.
Furthermore, highlighting real-world examples of data breaches caused by password vulnerabilities could underscore the urgency of the transition.
Common Misconceptions about Passwordless Authentication
A common misconception is that passwordless systems are inherently more complex than passwords. While some methods might require a learning curve, many passwordless systems are designed to be more intuitive and user-friendly than remembering and managing complex passwords. Another misconception is that passwordless systems are less secure. In fact, properly implemented passwordless systems offer stronger security than passwords, as they are less vulnerable to common attacks like phishing and credential stuffing.
Finally, some fear that passwordless systems will compromise their privacy. However, many systems utilize privacy-preserving techniques and adhere to strict data protection regulations, ensuring that user data is handled responsibly.
Technological Considerations

California’s ambitious move to ban traditional passwords necessitates a significant technological overhaul. The transition requires careful planning and substantial investment in infrastructure, impacting various sectors and demanding a collaborative effort between the government, private companies, and technology providers. Success hinges on addressing the challenges of integrating new systems with existing infrastructure while ensuring robust security and user-friendliness.The technological infrastructure needed to support a passwordless California is multifaceted.
It demands widespread adoption of robust authentication methods like biometrics, multi-factor authentication (MFA), and potentially decentralized identity solutions. This includes upgrading existing systems to accommodate these new methods, developing compatible software and hardware, and establishing secure communication channels for transmitting authentication data. The sheer scale of this undertaking across all sectors of California’s economy is a significant challenge.
Government Agency Roles in Facilitating Transition
Government agencies will play a crucial role in this transition, acting as both regulators and facilitators. They can provide funding for research and development of new authentication technologies, establish security standards and best practices, and offer educational resources to both businesses and individuals. Furthermore, government agencies can incentivize the adoption of passwordless systems through tax breaks or grants for businesses that comply with new regulations.
The California Department of Technology, for example, could lead the effort by developing model systems and providing technical support to other state agencies and local governments. Similar initiatives already exist in other states, serving as valuable models for California to emulate.
Challenges of Integrating New Authentication Systems with Legacy Systems
Integrating new authentication systems with existing legacy systems presents a considerable hurdle. Many businesses rely on outdated software and hardware that may not be compatible with modern authentication methods. The cost of upgrading these systems can be prohibitive for smaller companies, and the process itself can be complex and time-consuming. Furthermore, ensuring seamless integration between different systems across various industries will require careful planning and standardization.
California’s move to ban traditional passwords is a big deal, forcing a rethink of security protocols. This shift highlights the need for robust, secure authentication systems, and that’s where exploring the possibilities of modern development like what’s discussed in this article on domino app dev the low code and pro code future becomes crucial. Ultimately, the password ban pushes us towards more innovative, and hopefully more secure, solutions for the future.
This integration will necessitate the development of APIs and protocols that allow different systems to communicate securely and efficiently.
California’s move to ban traditional passwords is a big deal, forcing a shift towards more secure authentication methods. This heightened focus on security makes the advancements in cloud security even more critical, like what’s discussed in this article on bitglass and the rise of cloud security posture management , which highlights the importance of robust security solutions.
Ultimately, California’s ban underscores the need for innovative, passwordless security strategies to protect against increasingly sophisticated cyber threats.
Industry Adaptation to Passwordless Requirements
Different industries will adapt to the new requirements in diverse ways. The financial sector, for instance, may leverage biometric authentication combined with strong MFA for online banking and transactions. Healthcare providers might use digital signatures and secure messaging apps for patient record access. The education sector could implement single sign-on (SSO) systems with multi-factor authentication for students and faculty accessing online learning platforms.
The transition will require significant investment in training for employees and customers alike to ensure comfortable and secure usage of the new systems.
Visual Representation of Passwordless Authentication
Imagine a diagram illustrating the flow of information. A user initiates a login request (Step 1). Their device sends a biometric scan (fingerprint or facial recognition) (Step 2) to an authentication server. The server verifies the biometric data against a secure database (Step 3). If verified, the server issues a temporary access token (Step 4) which is sent back to the user’s device.
This token grants access to the requested service or application (Step 5). A second factor, such as a one-time code sent via SMS or an authenticator app, might be added for enhanced security (Step 6). The entire process is encrypted to ensure confidentiality and integrity. The temporary nature of the access token minimizes risk in case of compromise.
Closing Notes

California’s decision to ban traditional passwords is a bold experiment with potentially massive consequences. While the transition won’t be without its challenges – technological, economic, and even social – the potential benefits in terms of enhanced security and user experience are undeniable. The success of this initiative will depend heavily on public education, robust technological infrastructure, and a smooth transition for businesses.
Only time will tell if California’s lead will inspire similar legislation elsewhere, but one thing’s for sure: the age of the password is definitely drawing to a close.
FAQ Guide
What happens if a business in California doesn’t comply with the new law?
The bill likely includes penalties for non-compliance, potentially fines or other legal actions. The specifics would be detailed in the full text of the legislation.
Will this affect my personal accounts outside of California?
No, this law only directly affects businesses operating within California. However, the success of this initiative could influence similar legislation in other states or countries.
Are all passwordless systems equally secure?
No. The security of a passwordless system depends on its implementation and the specific technology used. Some methods are inherently more secure than others. Strong multi-factor authentication is crucial.
How will this affect small businesses in California?
Small businesses may face challenges adapting to new authentication systems, particularly those with limited IT resources. The bill may offer support or extended timelines for smaller companies.