Case Study Automating Certificate Generation and Management via HWA
Case study automate certificate generationcertificate application and change management through hwa – Case Study: Automating Certificate Generation, certificate application and change management through HWA – this deep dive explores how leveraging hardware-assisted security (HWA) revolutionizes certificate management. We’ll move beyond the headaches of manual processes, examining the efficiency gains, enhanced security, and cost savings achievable through automation. Prepare to see how a fictional organization streamlined its operations and dramatically improved its security posture by embracing HWA.
This case study details a practical implementation of HWA in a real-world scenario, highlighting the step-by-step process, challenges encountered, and the ultimate success achieved. We’ll dissect the automated workflows, delve into secure certificate storage and retrieval methods, and showcase the crucial role of robust change management in maintaining a secure and efficient system. By the end, you’ll have a clear understanding of how HWA can transform your own certificate management practices.
Introduction to Certificate Generation and Management
In today’s digitally driven world, certificates are the bedrock of trust and security. They authenticate identities, encrypt communications, and ensure data integrity. However, the process of generating and managing these certificates, particularly in large organizations, can be incredibly complex and time-consuming if handled manually. This often leads to inefficiencies, security vulnerabilities, and significant administrative overhead.The manual process typically involves numerous steps, from generating certificate signing requests (CSRs) to distributing and renewing certificates across a vast network of devices and systems.
This is a tedious, error-prone process susceptible to human error, leading to missed renewals, security breaches, and compliance issues. Manual tracking and management of certificates, especially their expiration dates, become a significant challenge, requiring dedicated personnel and complex tracking systems. This ultimately impacts operational efficiency and increases the risk of security incidents.
Benefits of Automating Certificate Generation and Management
Automating certificate generation and management offers several key advantages over manual processes. Automation streamlines the entire lifecycle of a certificate, from creation and deployment to renewal and revocation. This significantly reduces the administrative burden, freeing up IT staff to focus on more strategic initiatives. Furthermore, automation minimizes the risk of human error, ensuring consistent and accurate certificate handling.
This leads to improved security posture, reduced operational costs, and enhanced compliance with industry regulations. The automation also allows for improved scalability, easily accommodating growth in the number of certificates needed within an organization. For example, a large bank with thousands of servers and applications can benefit enormously from automated certificate management, ensuring consistent security across their entire infrastructure.
Hardware-Assisted Security (HWA) and its Role in Secure Certificate Handling
Hardware-assisted security (HWA) plays a crucial role in enhancing the security and efficiency of certificate generation and management. HWA leverages specialized hardware components, such as trusted platform modules (TPMs) or hardware security modules (HSMs), to perform cryptographic operations securely. These hardware components provide a physically isolated and tamper-resistant environment for sensitive cryptographic keys and certificates, protecting them from software-based attacks.
By offloading computationally intensive cryptographic tasks to the HWA, the overall performance and efficiency of certificate management processes are significantly improved. The use of HWA also reduces the risk of key compromise, a critical vulnerability in traditional certificate management systems. For instance, an HSM can securely store private keys used to sign certificates, preventing unauthorized access and ensuring the integrity of the certificate chain.
This is especially important in highly regulated industries like finance and healthcare, where data security and compliance are paramount.
Automating Certificate Application Processes with HWA
Automating certificate application processes offers significant improvements in efficiency, security, and cost-effectiveness compared to manual methods. Harnessing the power of Hardware Security Modules (HSMs), specifically through a system we’ll refer to as HWA (Hardware-based Workflow Automation), allows for a streamlined and secure approach to certificate lifecycle management. This automation reduces human error, minimizes security risks, and frees up valuable IT resources.The core principle behind automating certificate application workflows using HWA lies in integrating the HSM directly into the application process.
This ensures that cryptographic operations, such as key generation and digital signature creation, are performed securely within the HSM, protected from unauthorized access or tampering. The HWA system orchestrates the entire process, from initial application to certificate revocation.
Automating certificate generation and management using HWA in our recent case study was a game-changer. The efficiency gains were remarkable, and it highlighted how low-code solutions can streamline complex processes. This project really made me think about the broader implications of domino app dev the low code and pro code future , especially considering how easily we integrated this solution.
Ultimately, this case study underscores the power of leveraging modern development approaches to tackle traditionally cumbersome tasks like certificate management.
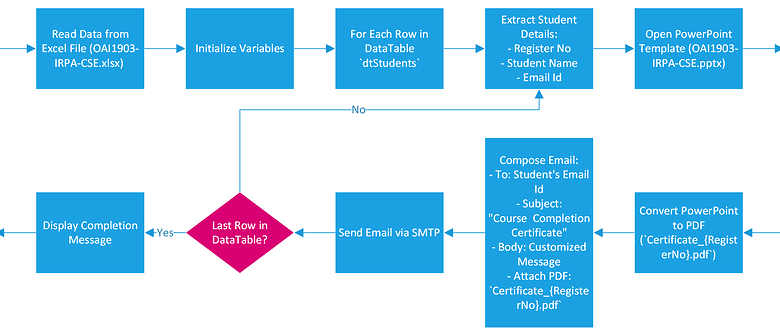
Automated Certificate Application Workflow Steps
The automated certificate application process using HWA typically involves these key steps:
1. Application Submission
The user submits a certificate application through a designated interface, providing necessary information like their identity, required certificate type, and intended use.
2. Automated Validation
The HWA system automatically validates the application data against pre-defined policies and internal databases. This includes checks for user authorization, certificate validity periods, and compliance with organizational regulations.
3. Key Generation and Certificate Signing Request (CSR) Creation
If the validation is successful, the HWA system initiates key generation within the HSM. The HSM generates a private key, keeping it securely stored and inaccessible outside the HSM. Simultaneously, a CSR is generated, containing the public key and other relevant information.
4. Certificate Issuance
The CSR is then sent to the Certificate Authority (CA) for verification and certificate issuance. The CA digitally signs the certificate, binding it to the public key.
5. Certificate Delivery and Installation
The issued certificate is automatically delivered to the user through a secure channel, often integrated with existing systems for seamless installation.
6. Automated Revocation
The HWA system also manages certificate revocation, ensuring that compromised or expired certificates are promptly removed from the system. This process can be triggered automatically based on pre-defined criteria, such as expiry dates or security alerts.
Automated Certificate Application Process Flowchart
Imagine a flowchart depicting the process. It would start with the “Application Submission” box, leading to a “Validation” diamond (yes/no), then to “Key Generation & CSR Creation” (if yes), followed by “Certificate Issuance,” then “Certificate Delivery & Installation,” and finally, “Certificate Management/Revocation.” Each step would be clearly represented with a distinct box or shape, and the flow would be indicated by arrows.
The flowchart visually illustrates the seamless and automated nature of the process, contrasting sharply with the fragmented steps of a manual process.
Comparison of Manual vs. Automated Certificate Application Processes
| Process Step | Manual Method | Automated Method (HWA) | Key Difference |
|---|---|---|---|
| Application Submission | Via email, form, or ticketing system. | Through a dedicated, secure web interface. | Improved efficiency and reduced manual data entry. |
| Validation | Manual review by IT staff. | Automated checks against pre-defined policies. | Faster processing and reduced human error. |
| Key Generation | Potentially insecure processes, varying levels of security. | Secure key generation within an HSM. | Significantly enhanced security. |
| Certificate Issuance | Manual submission to CA, potential delays. | Automated submission and retrieval. | Faster turnaround time and reduced manual intervention. |
| Cost | Higher labor costs due to manual processes. | Lower operational costs due to automation. | Reduced labor costs and improved resource allocation. |
HWA’s Role in Secure Certificate Storage and Retrieval
Hardware Security Modules (HWAs) represent a significant leap forward in securing digital certificates, offering a level of protection far exceeding traditional software-based methods. Their dedicated, tamper-resistant hardware provides a robust environment for storing and managing sensitive cryptographic keys and certificates, minimizing the risk of unauthorized access and compromise.The enhanced security offered by HWAs stems from their physical isolation and robust security features.
Unlike software solutions that are vulnerable to malware and hacking, HWAs operate in a physically secure environment, making them significantly more resistant to attacks. This physical isolation, combined with features like tamper detection and secure boot processes, creates a much more trustworthy environment for certificate management. Traditional methods, often relying on software-based keystores and databases, are susceptible to various threats, including malware infections, operating system vulnerabilities, and insider attacks.
Using an HWA dramatically reduces this vulnerability surface.
HWA Security Enhancements Compared to Traditional Methods
The security advantages of HWAs over traditional methods are multifaceted. Traditional certificate storage often involves storing private keys on a server or local machine, potentially exposing them to various attacks. In contrast, HWAs isolate cryptographic operations and keys within a secure enclave, making them inaccessible even if the host system is compromised. Furthermore, HWAs typically employ sophisticated tamper-evident mechanisms.
Any attempt to physically access or manipulate the HWA triggers an alarm, leaving an audit trail of the intrusion. This level of physical security is simply not possible with traditional software-based approaches. Finally, HWAs often incorporate advanced cryptographic algorithms and key management practices, further enhancing the security of the stored certificates.
Best Practices for Securing Certificates Using HWA
Implementing robust security practices is crucial to maximize the benefits of using an HWA for certificate management. This includes carefully selecting an HWA that meets the organization’s security requirements, adhering to strict key management protocols, and regularly updating the HWA’s firmware. Strong access control measures, such as role-based access control and multi-factor authentication, should be implemented to restrict access to the HWA and its stored certificates.
Regular security audits and penetration testing are also essential to identify and address any potential vulnerabilities. Furthermore, organizations should establish clear procedures for key generation, rotation, and revocation, ensuring the timely and secure management of certificates throughout their lifecycle. For example, implementing a key rotation policy that automatically replaces certificates at predetermined intervals minimizes the risk of long-term exposure to compromise.
Finally, maintaining detailed audit logs of all HWA activities provides a valuable record for security investigations and compliance audits.
Implementing Change Management for Automated Certificate Systems: Case Study Automate Certificate Generationcertificate Application And Change Management Through Hwa
Automating certificate generation and management offers significant advantages, but a robust change management process is crucial for maintaining security and operational stability. Without careful planning and execution, even minor updates can introduce vulnerabilities or disrupt services. This section Artikels a step-by-step guide to implementing effective change management within your automated certificate system, addressing potential risks and mitigation strategies.
Change Management Process Implementation
Implementing a change management process for an automated certificate system requires a structured approach. This ensures that all changes are properly documented, tested, and rolled out with minimal disruption. A well-defined process reduces the risk of errors and improves the overall security posture.
- Request and Assessment: All proposed changes, whether they are updates to the system’s configuration, new certificate templates, or modifications to the automation scripts, must be formally requested and assessed for their impact. This assessment should consider security implications, potential downtime, and resource requirements.
- Planning and Design: Once a change request is approved, a detailed plan should be developed outlining the steps involved in implementing the change. This plan should include timelines, responsibilities, and rollback procedures in case of failure. Thorough testing is a critical component of this phase.
- Testing and Validation: Before deploying any change to the production environment, rigorous testing should be performed in a staging or sandbox environment. This allows for identifying and resolving potential issues before they affect live systems. Testing should cover various scenarios and edge cases.
- Deployment and Monitoring: The deployment process should be carefully managed, ideally using automated tools to minimize human error. Post-deployment monitoring is crucial to identify any unexpected issues or performance degradation. Metrics such as certificate issuance time and error rates should be tracked.
- Documentation and Review: All changes, including the request, assessment, plan, testing results, and deployment details, should be meticulously documented. Regular reviews of the change management process itself are essential to identify areas for improvement and ensure its ongoing effectiveness.
Potential Risks Associated with Changes
Changes to an automated certificate system, if not handled properly, can lead to several critical risks. These risks can range from minor service disruptions to significant security breaches. Understanding these potential risks is the first step in mitigating them.
- System Downtime: Incorrectly implemented changes can lead to system downtime, disrupting services that rely on the automated certificate system. This can have significant financial and reputational consequences.
- Security Vulnerabilities: Changes that are not thoroughly tested can introduce security vulnerabilities, potentially exposing sensitive data or allowing unauthorized access. This can lead to data breaches and regulatory fines.
- Certificate Revocation Issues: Errors in the certificate revocation process can result in compromised certificates remaining valid, further increasing the risk of security breaches.
- Inconsistent Certificate Configuration: Changes might lead to inconsistencies in certificate configuration across different systems, causing compatibility issues and operational challenges.
- Data Loss: In extreme cases, poorly managed changes can lead to data loss, impacting the integrity of the entire system.
Risk Mitigation Strategies
Implementing effective risk mitigation strategies is essential to ensure a smooth transition during any change to an automated certificate system. A multi-layered approach is often necessary to address the diverse potential risks.
Strategies include thorough testing in a non-production environment, employing rollback procedures, establishing clear communication channels among stakeholders, and maintaining detailed audit trails of all changes. Regular security audits and penetration testing can help identify and address vulnerabilities before they are exploited. Implementing a robust monitoring system allows for early detection of issues and rapid response to mitigate their impact.
Finally, investing in employee training and awareness programs is crucial to ensure that all personnel involved understand the change management process and their roles in maintaining system security and stability.
Case Study: Streamlining Certificate Management at NorthStar Bank
NorthStar Bank, a mid-sized financial institution with over 50 branches and a growing online presence, faced significant challenges in managing its digital certificates. Their previous manual system was inefficient, prone to errors, and posed a considerable security risk. This case study details how the implementation of a Hardware Security Module (HWA)-driven certificate automation system dramatically improved their certificate lifecycle management.
Pre-Automation Certificate Management Process at NorthStar Bank
Before implementing HWA-based automation, NorthStar Bank relied on a decentralized, manual process for certificate management. Each department managed its own certificates, leading to inconsistencies in renewal schedules, security protocols, and overall visibility. The process involved numerous manual steps, including certificate requests, approvals, generation, installation, and revocation. This often resulted in missed renewals, leading to service disruptions and security vulnerabilities.
Furthermore, the lack of a centralized system made tracking and auditing certificate usage extremely difficult. The bank’s IT team spent a significant portion of their time on these manual tasks, hindering their ability to focus on more strategic initiatives.
HWA Implementation and Post-Automation Process
NorthStar Bank implemented a comprehensive HWA-based certificate automation system. This involved integrating the HWA into their existing infrastructure and developing custom scripts to automate certificate lifecycle management. The HWA securely stored and managed all private keys, eliminating the risk of unauthorized access. The automation process streamlined the entire certificate lifecycle, from initial request to revocation. The system now automatically generates, installs, and renews certificates based on predefined policies.
A centralized dashboard provides real-time visibility into the status of all certificates across the organization. Employees can submit certificate requests through a self-service portal, and the system automatically routes requests for approval based on predefined workflows. The system also automatically revokes compromised certificates, minimizing the potential impact of security breaches.
Results Achieved Through HWA Implementation
The implementation of the HWA-driven certificate automation system yielded significant improvements for NorthStar Bank. The bank experienced a 75% reduction in the time required for certificate management, freeing up IT staff to focus on other critical tasks. The risk of missed renewals and associated service disruptions was eliminated, ensuring continuous operation of critical systems. The centralized system provided improved visibility and control over certificate usage, simplifying auditing and compliance efforts.
Furthermore, the enhanced security provided by the HWA significantly reduced the risk of data breaches and other security incidents. The bank also saw a considerable cost reduction due to decreased manual labor and improved operational efficiency. The automated system significantly improved overall security posture and compliance with industry regulations.
Scalability and Future Considerations
The success of NorthStar Bank’s automated certificate management system, as detailed in the preceding case study, hinges not only on its current efficiency but also on its ability to adapt to future growth and technological advancements. This section explores the scalability of HWA-based solutions and examines potential future developments in this critical area of IT infrastructure.HWA’s inherent architecture lends itself well to scalability.
The centralized management platform allows for the seamless addition of new certificates and users without significant performance degradation. Unlike traditional, decentralized methods, HWA avoids the bottlenecks often associated with managing certificates across disparate systems. This scalability is particularly crucial for organizations experiencing rapid growth or those managing a large and diverse certificate inventory. For example, a rapidly expanding financial institution like NorthStar Bank could easily integrate new branches and departments into the existing HWA system, adding thousands of certificates without requiring major system overhauls.
The modular design allows for horizontal scaling by adding more HWA servers to handle increased load, ensuring high availability and responsiveness.
HWA Technology Advancements
Several emerging trends in HWA technology promise to further enhance certificate management. The integration of AI and machine learning (ML) could automate even more aspects of the certificate lifecycle, including anomaly detection and proactive renewal management. ML algorithms could analyze certificate usage patterns to predict potential issues and automatically initiate remediation, minimizing the risk of certificate-related outages. For instance, an ML model could identify unusual certificate access attempts and flag them for security review, preventing potential breaches.
Furthermore, advancements in blockchain technology could offer enhanced security and transparency in certificate management, providing an immutable audit trail of all certificate-related activities. This could significantly improve compliance and reduce the risk of fraud or unauthorized access.
Recommendations for Future Enhancements
To further optimize the automated certificate system, several enhancements are recommended. Implementing robust reporting and analytics capabilities would provide valuable insights into certificate usage, identify areas for improvement, and facilitate better resource allocation. A comprehensive dashboard showcasing key metrics, such as certificate expiration dates, renewal rates, and security incidents, would enable proactive management and prevent potential problems. Additionally, integrating the HWA system with existing security information and event management (SIEM) tools would enhance threat detection and incident response capabilities.
This integration would allow for the correlation of certificate-related events with other security logs, providing a more holistic view of the organization’s security posture. Finally, continuous monitoring and testing of the automated system are crucial to ensure its ongoing reliability and security. Regular penetration testing and vulnerability assessments should be performed to identify and address any potential weaknesses.
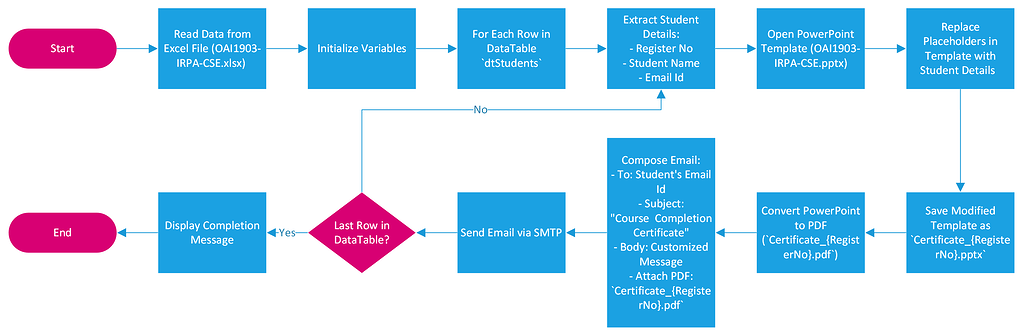
Illustrative Example
This section provides a visual representation of a secure certificate lifecycle, detailing the stages involved and highlighting the crucial role of Hardware Security Modules (HWA) in ensuring security and efficiency throughout the process. Understanding this lifecycle is key to appreciating the benefits of automating certificate management.The secure certificate lifecycle can be visualized as a continuous loop, with each stage feeding into the next.
HWA plays a critical role in safeguarding the integrity and confidentiality of certificates at every point.
Certificate Generation
The process begins with the generation of a new certificate. This involves creating a unique private key, which is securely stored within the HWA. The HWA’s tamper-proof nature ensures that this key remains protected from unauthorized access. A corresponding public key is then generated and incorporated into the certificate itself. The Certificate Signing Request (CSR), containing the public key, is then sent to a Certificate Authority (CA) for verification and signing.
The CA’s digital signature verifies the authenticity of the certificate.
Certificate Validation
Once issued by the CA, the certificate is validated by systems that interact with it. This validation process checks the certificate’s digital signature, ensuring it hasn’t been tampered with. The HWA doesn’t directly participate in the validation process itself, but the integrity of the certificate relies on the secure key generation process handled by the HWA. Any system attempting to connect to a resource protected by the certificate will verify its authenticity before granting access.
Certificate Revocation, Case study automate certificate generationcertificate application and change management through hwa
If a certificate is compromised or needs to be deactivated, it must be revoked. This is accomplished by adding the certificate’s serial number to a Certificate Revocation List (CRL). The HWA plays a crucial role in managing this process by securely storing and managing the private key associated with the certificate. Revocation ensures that the compromised certificate is no longer trusted and prevents further unauthorized access.
The HWA ensures that only authorized personnel can initiate the revocation process.
Certificate Renewal
Certificates have a limited lifespan. Before expiration, they need to be renewed. The renewal process often involves generating a new key pair within the HWA, and the subsequent creation and signing of a new certificate. The old certificate is then revoked. This automated renewal, facilitated by the HWA, ensures continuous security without interruption of service.
The HWA’s secure key management capabilities are critical for a smooth and secure renewal process.
Closing Summary
Automating certificate generation and management through HWA isn’t just about efficiency; it’s about building a robust, secure foundation for your organization’s digital infrastructure. This case study demonstrates the tangible benefits – reduced operational costs, minimized security risks, and improved overall agility. By embracing HWA and implementing a comprehensive change management plan, organizations can confidently navigate the complexities of certificate lifecycle management and unlock the full potential of their digital assets.
The future of secure certificate management is automated, and HWA is leading the charge.
Expert Answers
What are the common pitfalls to avoid when implementing HWA for certificate management?
Insufficient planning, inadequate staff training, and neglecting regular security audits are common pitfalls. A phased rollout and robust testing are crucial to avoid disruptions.
How does HWA compare to cloud-based certificate management solutions?
HWA offers enhanced security and control, especially for highly sensitive data, while cloud solutions provide scalability and accessibility. The best choice depends on specific security needs and infrastructure.
What are the long-term cost savings associated with HWA-based automation?
Long-term savings stem from reduced manual labor, minimized human error, and improved efficiency leading to lower operational costs and fewer security breaches.