A National Response to Ransomware Attacks
A National Response to Ransomware Attacks: Imagine a world where a single cyberattack could cripple essential services across an entire nation. That’s the chilling reality we face with ransomware, and the need for a robust national response is more urgent than ever. This isn’t just about protecting businesses; it’s about safeguarding our hospitals, power grids, and the very fabric of our digital lives.
This post dives deep into what a comprehensive national strategy should look like, exploring everything from prevention and mitigation to international collaboration and resource allocation.
We’ll unpack the critical infrastructure sectors most vulnerable to these attacks – think healthcare, finance, and energy – and examine the legal frameworks needed to effectively combat this growing threat. We’ll also explore the creation of a national coordination center, its structure, and the crucial role of public-private partnerships. Get ready to explore the complexities of ransomware response and the crucial steps needed to build a more resilient nation in the face of this ever-evolving threat.
Defining the Scope of a National Response
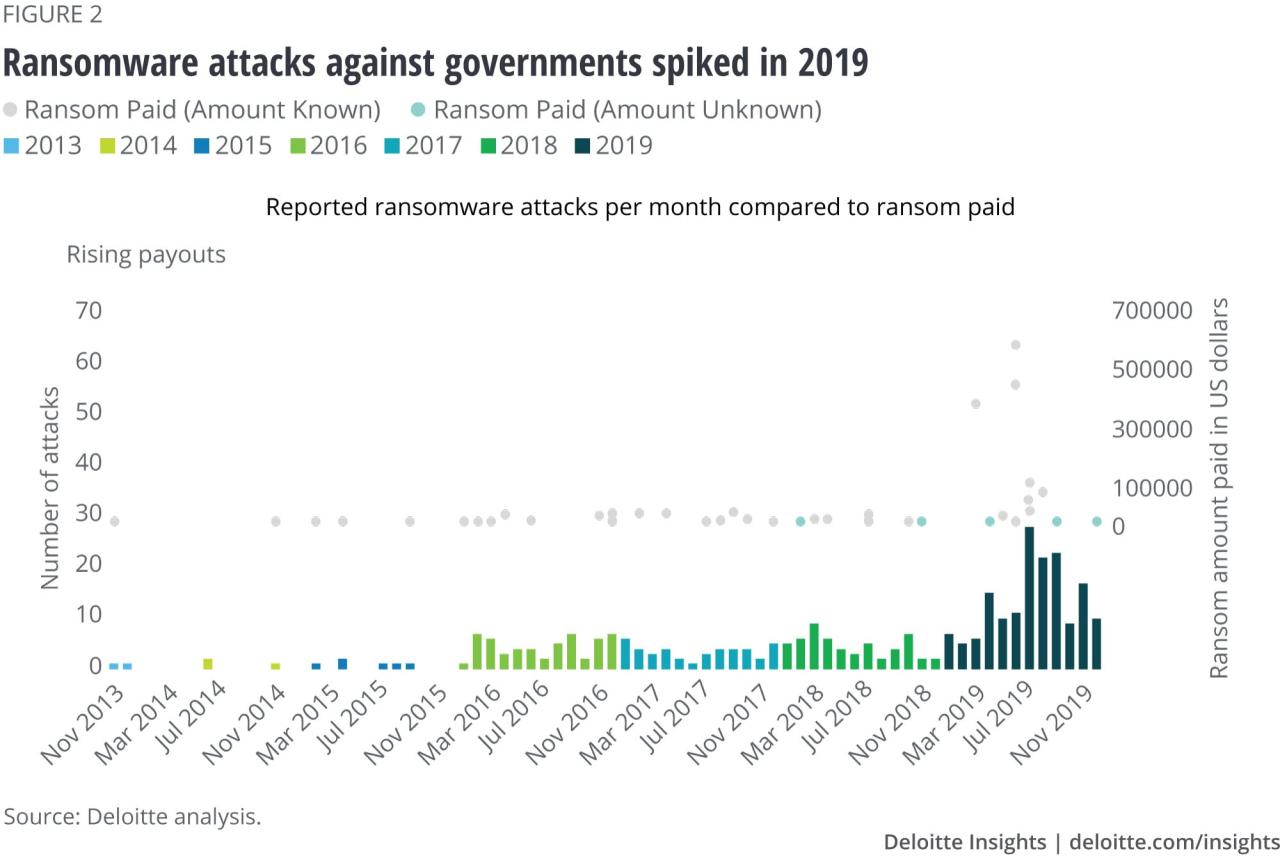
A national ransomware response strategy requires a multifaceted approach, moving beyond reactive measures to proactive prevention and robust mitigation. Success hinges on collaboration between government agencies, private sector entities, and international partners, fostering a shared responsibility model for cybersecurity. This collaborative effort needs to be underpinned by a clear understanding of vulnerabilities and a commitment to continuous improvement.A successful national ransomware response strategy is characterized by several key elements.
Firstly, it must establish a clear chain of command and communication protocols to ensure swift and coordinated action during an attack. Secondly, it necessitates the development and implementation of comprehensive threat intelligence sharing mechanisms, allowing for rapid identification and response to emerging threats. Thirdly, a robust incident response capability, including skilled personnel and advanced technological tools, is essential for effective containment and recovery.
Finally, a strong focus on prevention through proactive security measures, education and awareness campaigns, and robust cybersecurity infrastructure is crucial.
Critical Infrastructure Sectors Most Vulnerable to Ransomware Attacks
Several critical infrastructure sectors exhibit heightened vulnerability to ransomware attacks due to their interconnected nature, reliance on legacy systems, and the potential for widespread disruption. The healthcare sector, for example, relies heavily on digital systems for patient records, medical devices, and operational efficiency. A ransomware attack could compromise patient data, disrupt medical services, and even endanger lives. Similarly, the energy sector, with its complex control systems and reliance on real-time data, faces significant risks from ransomware, potentially leading to power outages and disruptions to essential services.
The financial sector, with its vast amounts of sensitive financial data, is also a prime target, as a successful attack could result in significant financial losses and damage to reputation. Finally, transportation systems, including air traffic control and rail networks, are increasingly reliant on digital systems, making them susceptible to disruptions caused by ransomware attacks. The consequences of a successful ransomware attack on any of these sectors can be catastrophic, highlighting the need for robust cybersecurity measures.
Comparison of National Approaches to Cybersecurity and Ransomware Mitigation
Different nations adopt diverse approaches to cybersecurity and ransomware mitigation, reflecting their unique geopolitical contexts, technological capabilities, and legal frameworks. Some countries, like the United States, favor a largely market-driven approach, relying on private sector initiatives and industry best practices, supplemented by government guidance and regulations. Others, such as certain European nations, adopt a more regulatory-centric approach, with stringent data protection laws and cybersecurity standards imposed on businesses.
Israel, for instance, has a strong emphasis on national cybersecurity preparedness through proactive intelligence gathering and rapid response capabilities, often driven by the country’s unique security challenges. These contrasting approaches highlight the complexities of creating a universally effective national response strategy. Each approach presents advantages and disadvantages, and the optimal strategy often involves a blend of market-driven and regulatory approaches tailored to a nation’s specific needs and resources.
Legal and Regulatory Frameworks Supporting National Ransomware Response
A robust legal and regulatory framework is essential for supporting a national ransomware response. This framework should clarify responsibilities, establish reporting requirements, and provide legal recourse for victims. It needs to address issues such as data breach notification, liability for organizations affected by ransomware attacks, and the permissibility of certain response actions, such as paying ransoms. Furthermore, strong legislation is required to deter ransomware actors and facilitate international cooperation in investigations and prosecutions.
Existing laws, such as the GDPR in Europe and the CCPA in California, offer some protection, but a comprehensive national framework specifically tailored to address the unique challenges of ransomware attacks is needed. This framework should provide a clear legal basis for government intervention in critical infrastructure incidents and establish mechanisms for coordinating national and international responses. The framework also needs to consider the ethical and legal implications of using advanced technologies, such as AI and machine learning, in ransomware detection and response.
Establishing a National Coordination Center
A robust national response to ransomware attacks necessitates a centralized, well-structured coordination center. This center will act as the central hub for information sharing, resource allocation, and strategic decision-making during ransomware incidents, ensuring a unified and effective national response. Its establishment is crucial for minimizing damage, accelerating recovery, and deterring future attacks.The National Ransomware Coordination Center (NRCC) will operate as a collaborative effort between various government agencies, private sector entities, and cybersecurity experts.
Its effectiveness hinges on clear lines of communication, well-defined roles, and access to advanced technological capabilities.
NRCC Structure and Key Stakeholders
The NRCC will adopt a tiered structure, mirroring the complexity of ransomware incidents. A central executive committee, composed of high-ranking officials from relevant government agencies (such as the Department of Homeland Security (DHS), the FBI, and the National Security Agency (NSA)), will oversee strategic direction and policy. Below this, specialized working groups will focus on specific areas like incident response, threat intelligence, victim support, and legal and policy matters.
Private sector participation will be vital, with representatives from major technology companies, critical infrastructure operators, and cybersecurity firms contributing expertise and resources. This collaborative approach ensures a holistic response leveraging the strengths of all stakeholders.
Roles and Responsibilities of Key Stakeholders
The NRCC’s success depends on clearly defined roles and responsibilities. The executive committee will be responsible for overall strategy, resource allocation, and communication with the public and international partners. Working groups will tackle specific tasks: the incident response team will handle immediate remediation efforts; the threat intelligence group will analyze attacks and identify emerging threats; the victim support group will assist individuals and organizations affected by ransomware; and the legal and policy team will ensure all actions are compliant with existing laws and regulations.
Private sector representatives will provide technical expertise, share threat intelligence, and contribute to incident response efforts. Clear communication channels and regularly scheduled meetings will ensure coordination across all groups.
Communication Protocol for Ransomware Incidents
Effective communication is paramount during a ransomware incident. The NRCC will establish a secure communication platform for information sharing among stakeholders. This will include secure messaging systems, video conferencing capabilities, and a centralized repository for incident reports and threat intelligence. A standardized reporting procedure will be implemented to ensure consistent and timely information flow. Regular briefings will be provided to the executive committee, and public communications will be managed through designated spokespeople to maintain a unified message and avoid confusion.
This structured approach will ensure transparency and coordinated action.
Technological Infrastructure of the NRCC
The NRCC will require a robust technological infrastructure to support its operations. This includes secure network infrastructure, advanced threat detection and analysis tools, data storage and management systems, and secure communication platforms. The center will need access to cutting-edge cybersecurity technologies, including sandboxing environments for malware analysis, threat intelligence platforms, and incident response tools. Data analytics capabilities will be crucial for identifying patterns and trends in ransomware attacks, informing preventative measures and strategic decision-making.
Redundancy and fail-safe mechanisms will be built into the system to ensure continuous operation even during major incidents. Regular security audits and penetration testing will be conducted to maintain the highest levels of security.
Prevention and Mitigation Strategies

Ransomware attacks represent a significant threat to individuals and organizations alike, demanding a proactive and multi-faceted approach to prevention and mitigation. A robust national response must incorporate strong preventative measures alongside effective mitigation strategies to minimize the impact of successful attacks. This section details best practices, successful national-level programs, the role of public-private partnerships, and a plan for effective public awareness campaigns.
Best Practices for Ransomware Prevention
Implementing strong security practices is the cornerstone of ransomware prevention. The following table Artikels key preventative measures, their implementation costs, and their effectiveness. Note that costs can vary widely depending on the size and complexity of an organization’s IT infrastructure. Effectiveness is also relative and depends on proper implementation and ongoing maintenance.
| Practice | Description | Implementation Cost | Effectiveness |
|---|---|---|---|
| Regular Software Updates | Keeping operating systems, applications, and antivirus software up-to-date patches vulnerabilities exploited by ransomware. | Low to Moderate (depending on automation) | High |
| Strong Password Policies | Enforcing complex, unique passwords and multi-factor authentication (MFA) significantly reduces the risk of unauthorized access. | Low to Moderate (depending on MFA implementation) | High |
| Data Backups | Regularly backing up critical data to offline or cloud storage allows for quick recovery in case of an attack. The 3-2-1 backup rule (3 copies of data, on 2 different media, with 1 offsite copy) is recommended. | Moderate to High (depending on storage solution) | High |
| Employee Security Training | Educating employees about phishing scams, malicious attachments, and other social engineering tactics is crucial in preventing initial infection. | Low to Moderate (depending on training method) | High |
| Network Segmentation | Dividing the network into smaller, isolated segments limits the impact of a ransomware infection. | Moderate to High (depending on network complexity) | High |
| Intrusion Detection/Prevention Systems (IDS/IPS) | These systems monitor network traffic for malicious activity and can block or alert on suspicious behavior. | Moderate to High | Moderate to High |
| Regular Security Audits and Penetration Testing | Periodic assessments identify vulnerabilities and weaknesses in security posture. | Moderate to High | High |
Examples of Successful Ransomware Prevention Programs
While specific details of national-level ransomware prevention programs are often kept confidential for security reasons, successful strategies generally involve a combination of the best practices listed above, coupled with strong public-private partnerships and robust incident response capabilities. For example, many countries have implemented national cybersecurity awareness campaigns, similar to those run by the UK’s National Cyber Security Centre (NCSC) or the US Cybersecurity and Infrastructure Security Agency (CISA), which aim to educate citizens and businesses about ransomware threats and best practices.
These campaigns often involve public service announcements, online resources, and workshops. Furthermore, many countries have established CERTs (Computer Emergency Response Teams) that provide incident response support and guidance to organizations affected by ransomware attacks. These teams play a vital role in containing the spread of ransomware and assisting with recovery efforts.
The Role of Public-Private Partnerships in National Prevention Strategies
Effective ransomware prevention requires collaboration between government agencies, private sector organizations, and research institutions. Public-private partnerships (PPPs) facilitate the sharing of threat intelligence, the development of best practices, and the implementation of national-level prevention strategies. PPPs can also help to coordinate responses to ransomware attacks, ensuring a swift and effective response. For example, a PPP might involve government agencies sharing threat intelligence with private sector organizations, enabling them to proactively defend against emerging threats.
Conversely, private sector organizations can contribute their expertise and resources to help government agencies develop and implement effective prevention strategies.
Public Awareness Campaigns to Educate Citizens About Ransomware
A comprehensive public awareness campaign is crucial in educating citizens about ransomware threats and preventative measures. The campaign should utilize multiple channels, including:
- Public Service Announcements (PSAs): Short, impactful videos and radio ads broadcast across various media platforms.
- Online Resources: A dedicated website and social media channels providing information, best practices, and FAQs.
- Educational Workshops and Seminars: Targeted workshops for specific demographics, such as small businesses and senior citizens.
- School Programs: Integrating cybersecurity education into school curricula to build awareness from a young age.
- Community Outreach Programs: Collaborating with local organizations and community leaders to reach wider audiences.
The campaign should emphasize the importance of strong passwords, regular software updates, and caution when opening emails and attachments. It should also provide clear instructions on what to do if a ransomware attack occurs, including reporting the incident to the appropriate authorities. Regular updates and adjustments to the campaign based on emerging threats are also essential.
Incident Response and Recovery
A national ransomware response requires a robust and well-defined incident response plan. This plan must be capable of handling attacks of varying scales, from localized incidents to widespread, crippling events impacting critical infrastructure. Effective response hinges on speed, coordination, and a clear understanding of the attacker’s methods.
A comprehensive national strategy needs to account for the diverse range of potential targets and attack vectors. This includes everything from government agencies and financial institutions to healthcare providers and private businesses. The speed and effectiveness of the response directly impacts the extent of damage and the overall recovery time.
A strong national response to ransomware attacks needs robust, secure systems. This is where efficient development comes in; check out this article on domino app dev the low code and pro code future to see how streamlined development can improve security. Ultimately, quicker development cycles and more secure code contribute to a more resilient national infrastructure against these cyber threats.
Step-by-Step Procedure for Responding to a Large-Scale Ransomware Attack
Responding to a large-scale ransomware attack demands a systematic and coordinated approach. A clear, pre-defined procedure is crucial for minimizing damage and facilitating a swift recovery. This involves isolating affected systems, containing the spread of the ransomware, and ultimately restoring affected data and services.
- Immediate Containment: Isolate affected systems from the network to prevent further spread of the ransomware. This might involve disconnecting infected machines from the internet and internal network segments.
- Incident Assessment: Determine the extent of the breach, identifying all affected systems and data. This includes assessing the type of ransomware, its entry point, and the scope of data encryption.
- Evidence Collection and Preservation: Gather forensic evidence from infected systems, preserving system logs, network traffic data, and any other relevant information. This is crucial for identifying the attackers and building a case for prosecution.
- Notification and Coordination: Notify relevant stakeholders, including law enforcement, affected organizations, and potentially the public. Establish a national coordination center to centralize response efforts and facilitate communication.
- Ransom Negotiation (Conditional): Consider whether to negotiate with the attackers. This is a highly complex decision, requiring careful assessment of the risks and potential benefits. Many experts advise against paying ransoms due to the risk of emboldening attackers and the lack of guarantee of decryption.
- Data Recovery: Utilize backups to restore encrypted data. This underscores the critical importance of having a robust and regularly tested backup and recovery plan.
- System Restoration: Restore affected systems to a clean state using backups or re-imaging. Implement security patches and updates to prevent future attacks.
- Post-Incident Analysis: Conduct a thorough post-incident analysis to identify vulnerabilities, improve security practices, and refine the incident response plan.
Importance of Data Backups and Recovery Plans in a National Ransomware Response Strategy
Data backups and recovery plans are not merely optional components; they are fundamental pillars of any effective national ransomware response strategy. Without robust backups, organizations face potentially catastrophic data loss, severely hindering their ability to recover from an attack and potentially leading to irreversible damage.
A comprehensive strategy includes regular, automated backups stored offline or in geographically separate locations. These backups should be regularly tested to ensure their integrity and recoverability. The plan should also detail the procedures for restoring data, including system configurations and applications.
The 2017 NotPetya ransomware attack highlighted the devastating consequences of inadequate backup strategies. The malware spread rapidly, crippling numerous organizations worldwide, partly because many lacked effective backups or had backups that were also compromised.
Comparison of Ransomware Decryption Methods and Their Effectiveness
Several methods exist for decrypting ransomware-encrypted data, each with varying degrees of effectiveness. The success of decryption often depends on factors such as the specific ransomware variant, the encryption method used, and the availability of decryption tools.
| Decryption Method | Effectiveness | Limitations |
|---|---|---|
| Ransom Payment | Potentially High (but unreliable) | Supports criminal activity, no guarantee of decryption, may not be legal in all jurisdictions. |
| Decryption Tools | Varies depending on ransomware variant | Requires availability of a working tool, may not be effective against newer or sophisticated ransomware. |
| Data Recovery from Backups | High, if backups are available and intact | Requires a robust and tested backup strategy, backups may be outdated or corrupted. |
| Manual Decryption (Expert Level) | Potentially High (but extremely difficult) | Requires specialized skills and knowledge, time-consuming, may not always be successful. |
Process for Investigating Ransomware Attacks to Identify Perpetrators and Gather Evidence
Investigating ransomware attacks to identify perpetrators requires a systematic and thorough approach, combining digital forensics with traditional investigative techniques. The goal is to gather sufficient evidence to prosecute the attackers and prevent future attacks.
This process typically involves analyzing infected systems, network logs, and other digital evidence to identify the attack vector, the ransomware variant, and any communication with the attackers. This information can then be used to trace the attackers back to their origin, identifying their infrastructure and potentially their identities.
Collaboration with law enforcement agencies is essential, leveraging their expertise in criminal investigations and international cooperation. Information sharing and coordination between organizations and national agencies is vital to effectively track and prosecute ransomware gangs.
International Cooperation and Information Sharing
Ransomware attacks transcend national borders, making international cooperation crucial for effective response and prevention. The interconnected nature of global infrastructure and data flow means that a successful attack in one country can quickly ripple outwards, impacting others. Sharing information and coordinating efforts across international boundaries is therefore not just beneficial, but essential for minimizing damage and disrupting ransomware operations.International collaboration allows for the pooling of resources and expertise, enhancing our collective ability to combat ransomware.
By sharing threat intelligence, best practices, and incident response strategies, nations can strengthen their individual defenses and collectively weaken the capabilities of ransomware actors. This collaborative approach significantly improves the effectiveness of national ransomware response strategies, reducing response times and minimizing the overall impact of attacks.
Key International Organizations Involved in Cybersecurity
Several key international organizations play vital roles in coordinating the global response to ransomware. These organizations provide platforms for information sharing, collaborative research, and the development of international standards and best practices. Their contributions are invaluable in building a cohesive global defense against ransomware threats.
- INTERPOL: INTERPOL facilitates international police cooperation, including the sharing of intelligence on cybercrime, and assists member states in investigating and prosecuting ransomware actors.
- Europol: Europol, the European Union’s law enforcement agency, plays a similar role within the EU, focusing on coordinating investigations and disrupting ransomware gangs operating within Europe.
- The Cybersecurity and Infrastructure Security Agency (CISA) (USA): While a national agency, CISA actively participates in international collaborations and shares threat intelligence globally, contributing significantly to the collective effort.
- The National Cyber Security Centre (NCSC) (UK): Similar to CISA, the NCSC plays a key role in international information sharing and collaboration, particularly within the Five Eyes intelligence alliance.
- United Nations Office on Drugs and Crime (UNODC): The UNODC works to develop international norms and standards related to cybercrime, including ransomware, and provides assistance to countries in strengthening their cybersecurity capabilities.
Framework for Secure Information Sharing
A robust framework for secure information sharing is crucial for effective international cooperation against ransomware. This framework should prioritize the protection of sensitive information while ensuring the timely and efficient exchange of critical threat intelligence. This involves several key components.
- Establish Secure Communication Channels: Dedicated, encrypted channels are necessary for the secure exchange of sensitive information between nations. This could involve the use of secure messaging platforms, dedicated data exchange networks, or other secure communication technologies.
- Develop Standardized Data Formats: Adopting standardized data formats for sharing threat intelligence ensures interoperability between different national systems and facilitates faster analysis and response.
- Implement Data Privacy and Security Protocols: Strict protocols are needed to protect the privacy and security of shared information, adhering to relevant national and international laws and regulations.
- Establish Clear Legal Frameworks: International legal frameworks are essential to govern the sharing of information and ensure that data is handled appropriately and legally across borders.
- Foster Trust and Transparency: Building trust and transparency among participating nations is paramount for the success of any information-sharing initiative. This requires open communication and a commitment to mutual benefit.
Improving Effectiveness of National Strategies Through Collaboration
International collaboration directly improves the effectiveness of national ransomware response strategies in several ways. For example, coordinated takedowns of ransomware infrastructure, facilitated through international cooperation, can significantly disrupt criminal operations. The sharing of threat intelligence allows nations to proactively defend against emerging threats, improving their preparedness and response capabilities. Joint exercises and training programs can enhance the skills and coordination of national response teams.
Finally, collaborative research and development can lead to the creation of new technologies and strategies for combating ransomware. The collective intelligence and resources harnessed through international cooperation represent a powerful force against this global threat.
Resource Allocation and Funding
The fight against ransomware demands a significant and sustained investment. A robust national response requires a multi-faceted approach encompassing human expertise, cutting-edge technology, and substantial financial resources. Failing to adequately fund this effort risks leaving the nation vulnerable to increasingly sophisticated and costly attacks.The economic impact of ransomware is staggering, extending far beyond the immediate financial losses suffered by victims.
Disruptions to critical infrastructure, loss of intellectual property, reputational damage, and the costs associated with recovery all contribute to a substantial overall economic burden. Adequate resource allocation is not simply a matter of expense; it’s a critical investment in national security and economic stability.
Key Resources Required for a National Ransomware Response
A comprehensive national ransomware response requires a strategic allocation of resources across several key areas. These resources are interconnected and mutually supportive, requiring a coordinated and holistic approach.
- Human Resources: This includes cybersecurity experts, incident responders, investigators, legal professionals, and communication specialists. A national program should invest in training and development to build a skilled workforce capable of handling the complexities of ransomware attacks. The number of personnel required will depend on the size and complexity of the program but should include specialists in areas like digital forensics, malware analysis, and threat intelligence.
- Technological Resources: This encompasses advanced threat detection systems, incident response tools, data recovery solutions, secure communication channels, and a robust national cybersecurity infrastructure. Investment in research and development of new technologies to combat ransomware is also crucial. Examples include advanced sandboxing capabilities for malware analysis and automated threat hunting tools.
- Financial Resources: Funding is essential for all aspects of a national ransomware response, from personnel salaries and training to the acquisition of advanced technologies and the development of prevention and mitigation strategies. A robust budget is needed to support ongoing operations, research, and emergency response efforts. This includes funding for public awareness campaigns and victim support programs.
Funding Model for a National Ransomware Response Program
Several funding models could be employed to support a national ransomware response program. A multi-pronged approach is likely the most effective.
- Government Funding: Direct allocation of funds from national budgets is crucial to provide a stable and reliable source of funding. This funding should be allocated across different government agencies responsible for cybersecurity and law enforcement.
- Public-Private Partnerships: Collaboration between government agencies and private sector companies is essential. This could involve shared funding, joint research initiatives, and the development of industry standards. Examples include government grants to encourage private sector investment in cybersecurity research and development.
- Insurance Programs: Cybersecurity insurance can play a significant role in mitigating the financial impact of ransomware attacks. Government incentives could encourage wider adoption of these insurance programs and ensure they provide adequate coverage. This could include tax incentives for businesses that invest in robust cybersecurity measures and obtain cyber insurance.
Economic Impact of Ransomware Attacks and Justification for Resource Allocation
The economic impact of ransomware is far-reaching and devastating. Consider the 2017 NotPetya attack, estimated to have caused over $10 billion in global damages. This included direct costs from paying ransoms, indirect costs from business disruptions, and the cost of recovery efforts. The Colonial Pipeline ransomware attack in 2021 resulted in fuel shortages and significant economic disruption.
These examples illustrate the need for proactive and well-funded national response programs. The cost of inaction far outweighs the cost of investing in prevention, mitigation, and response capabilities.
Cost Breakdown of Prevention, Response, and Recovery Efforts
Precise cost estimations are challenging due to the variability of attacks and the specific needs of different organizations. However, a general breakdown can illustrate the significant financial commitment required.
| Activity | Cost Factors | Estimated Cost Range (USD) |
|---|---|---|
| Prevention | Software licenses, security training, vulnerability assessments, security awareness campaigns | $100,000 – $10,000,000+ (depending on organization size and complexity) |
| Response | Incident response team deployment, forensic analysis, data recovery, legal fees, ransom payments (though discouraged) | $50,000 – $5,000,000+ (depending on attack severity and complexity) |
| Recovery | System restoration, data recovery, business continuity planning implementation, reputational damage mitigation | $100,000 – $10,000,000+ (depending on data loss and business disruption) |
Measuring Effectiveness and Continuous Improvement
A robust national ransomware response strategy isn’t just about reacting to attacks; it’s about proactively improving our defenses and measuring the success of our efforts. Continuous improvement is key to staying ahead of ever-evolving threats, and that requires a comprehensive system for tracking performance and identifying areas needing attention. This involves establishing clear metrics, regularly evaluating our response mechanisms, and using data-driven insights to refine our approach.Regular evaluation and improvement of the national response mechanisms are crucial for maintaining effectiveness against the dynamic threat landscape of ransomware attacks.
This requires a structured process encompassing data collection, analysis, and feedback loops to inform strategic adjustments and resource allocation. The ultimate goal is to minimize the impact of ransomware attacks on critical infrastructure and the overall economy.
Key Performance Indicators (KPIs) for Ransomware Response
Effective measurement requires specific, measurable, achievable, relevant, and time-bound (SMART) KPIs. These KPIs should track various aspects of the response, from prevention to recovery. Examples include the average time to contain a ransomware attack, the percentage of attacks successfully prevented through proactive measures, the average recovery time for affected systems, and the overall financial losses associated with ransomware incidents.
Tracking these metrics provides a clear picture of the effectiveness of the national strategy and allows for identification of areas requiring immediate attention. For example, a consistently high average recovery time might indicate a need for improved incident response training or enhanced backup and recovery infrastructure.
Data Collection and Analysis Methods, A national response to ransomware attacks
Collecting and analyzing relevant data is the cornerstone of effective measurement. This involves establishing a centralized data repository to gather information from various sources, including government agencies, private sector organizations, and cybersecurity firms. Data points could include the number of ransomware attacks, their geographic distribution, the types of ransomware used, the methods of infection, the ransom demands, and the financial losses incurred.
Sophisticated data analysis techniques, such as statistical modeling and machine learning, can then be employed to identify trends, predict future attacks, and refine the national response strategy. For instance, analyzing attack vectors could reveal common vulnerabilities that can be addressed through targeted security awareness campaigns or software updates.
Post-Incident Review Process
Post-incident reviews (PIRs) are critical for learning from past experiences and preventing future incidents. A structured PIR process should be implemented, involving representatives from various agencies and organizations involved in the response. The PIR should focus on identifying the strengths and weaknesses of the response, determining the root causes of the incident, and recommending specific improvements to the national strategy.
A standardized PIR template should be used to ensure consistency and completeness of the reviews. The findings from these reviews should be documented and shared broadly to foster continuous improvement across all involved parties. For example, a PIR might reveal shortcomings in communication protocols, leading to recommendations for improved coordination and information sharing during future incidents.
Concluding Remarks
Ultimately, a successful national response to ransomware attacks requires a multi-faceted approach. It’s not just about reacting to incidents; it’s about proactively preventing them through robust security measures, public awareness campaigns, and strong international collaboration. Building a resilient nation against this threat demands a commitment to investing in the necessary resources, constantly evaluating our strategies, and fostering a culture of cybersecurity awareness across all sectors.
The fight against ransomware is far from over, but with a well-defined national strategy, we can significantly reduce its impact and protect our critical infrastructure and citizens.
Clarifying Questions: A National Response To Ransomware Attacks
What are the biggest challenges in implementing a national ransomware response?
Major challenges include securing sufficient funding, coordinating diverse stakeholders, overcoming jurisdictional issues, and adapting to the ever-evolving tactics of ransomware attackers. Balancing security with economic considerations also presents a significant hurdle.
How can individuals protect themselves from ransomware?
Individuals should practice good cybersecurity hygiene: regularly update software, use strong passwords, be wary of phishing emails and suspicious links, and maintain regular backups of important data.
What role does insurance play in a national ransomware response?
Cyber insurance can help organizations mitigate financial losses from ransomware attacks, but it’s not a complete solution. A comprehensive strategy must include prevention, response, and recovery measures, regardless of insurance coverage.
What is the difference between a national response and individual organizational response?
A national response provides overarching strategy, coordination, and resource allocation. Individual organizations are responsible for implementing specific security measures and responding to attacks within their own systems, often guided by national best practices and guidelines.