Cybersecurity
-

Company Asks Customers to Delete Credit Card Info After Data Breach
Company asks customers to delete credit card info after data breach – a headline that unfortunately rings too true these…
Read More » -

Companies Taking Cyber Insurance Are Vulnerable to Ransomware Attacks
Companies taking cyber insurance are vulnerable to ransomware attacks – a seemingly paradoxical statement, yet one supported by unsettling evidence.…
Read More » -
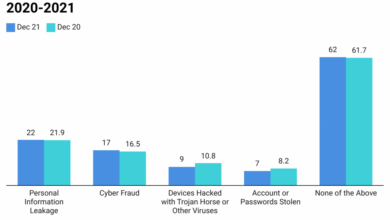
Companies in China Witness a Surge in Cyber Attacks
Companies in China witness a surge in cyber attacks – a chilling reality that’s shaking the foundations of the nation’s…
Read More » -

Common ISO 27001 Pitfalls and How to Avoid Them
Common iso iec 27001 pitfalls and how to avoid them – Common ISO 27001 pitfalls and how to avoid them…
Read More » -

Common Cybersecurity Challenges and Solutions
Common cybersecurity challenges and solutions are crucial for navigating the digital landscape. In today’s hyper-connected world, understanding the threats—from phishing…
Read More » -
Cloudsek Offers a Search Engine to Detect Malicious Apps
Cloudsek offers a search engine to detect malicious apps – a game-changer in the world of app security! Imagine a…
Read More » -

CloudPets Teddy Bears Leak Millions of Voice Recordings
CloudPets teddy bears leak millions of voice recordings to hackers – that’s the chilling reality that unfolded, exposing a massive…
Read More » -

Cloud Services Now Spreading Malware
Cloud services now spreading malware? It’s a chilling reality, isn’t it? We rely on cloud services for everything these days…
Read More » -

Cloud Security Breach Leaks 957,000 Patient Records
Cloud security breach leads to a leak of 957000 patient records – Cloud security breach leads to a leak of…
Read More » -

Cloud Security Beefed Up for IBM Blockchain
Cloud security beefed up for IBM Blockchain – that’s the exciting news! IBM’s recent enhancements to its blockchain platform are…
Read More »
