Cybersecurity
-

Indian Cybercrime Alert Job Scams
Indian government issues cyber crime alert in view of job offers, highlighting the rising tide of online job scams targeting…
Read More » -

Imperva Cloud Firewall Hack Data Exposed
Imperva announces that data of its cloud firewall was exposed to hackers, sparking immediate concern about the security of sensitive…
Read More » -

Immutable Data Storage Ransomwares Last Stand
Immutable data storage is last line of defense against ransomware – Immutable data storage is the last line of defense…
Read More » -
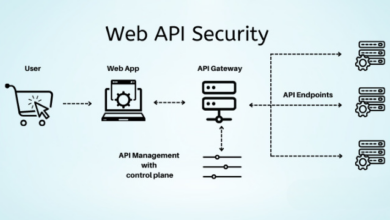
API Security Risks Graylogs Solution
If your business is not vulnerable to api security risks then you are not paying attention graylog – If your…
Read More » -
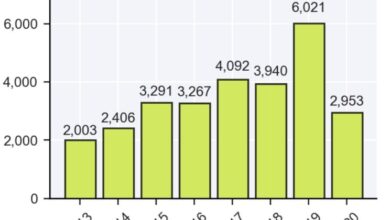
Massive Data Leak 8.5 Billion Records Compromised
Ibm says more than 8 5 billion records were leaked in cyber attacks – IBM says more than 8.5 billion…
Read More » -
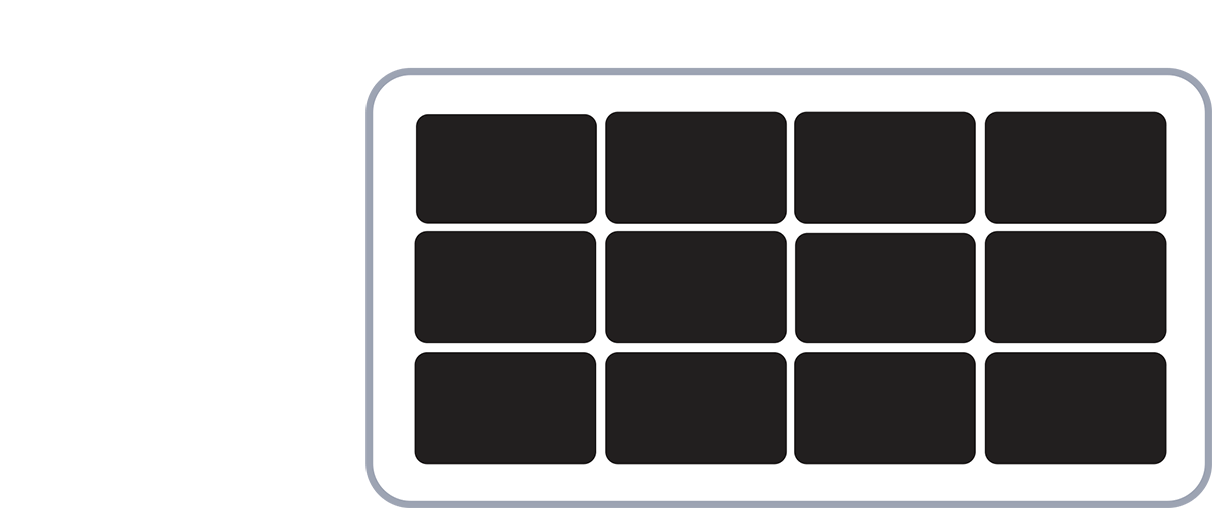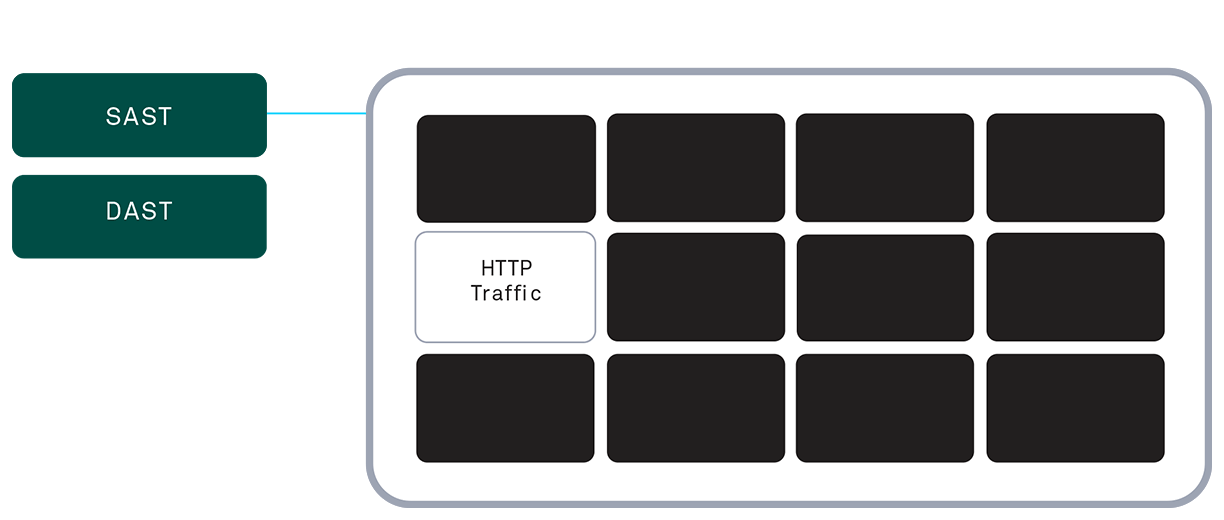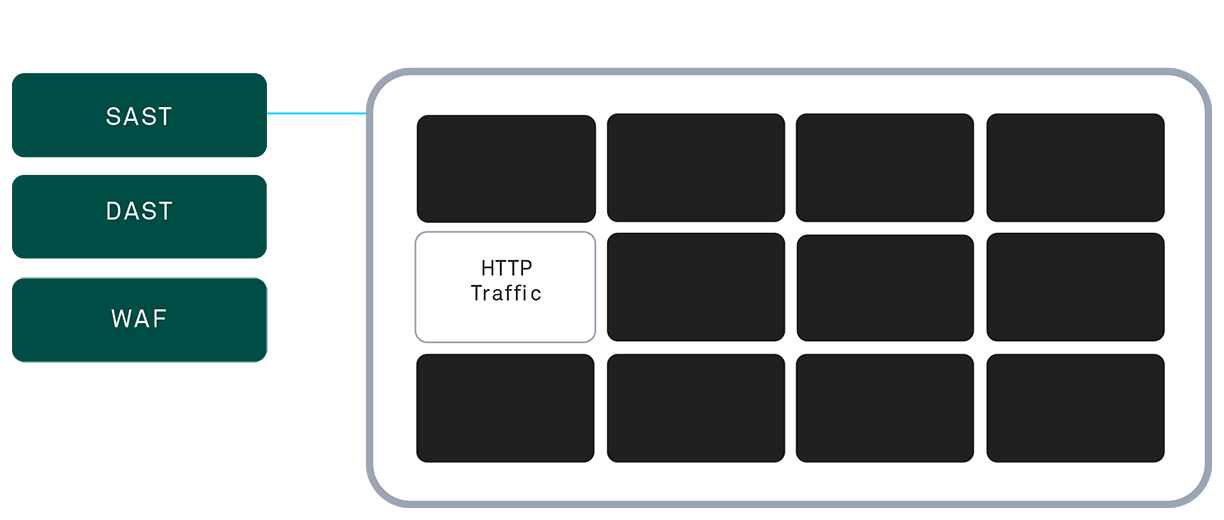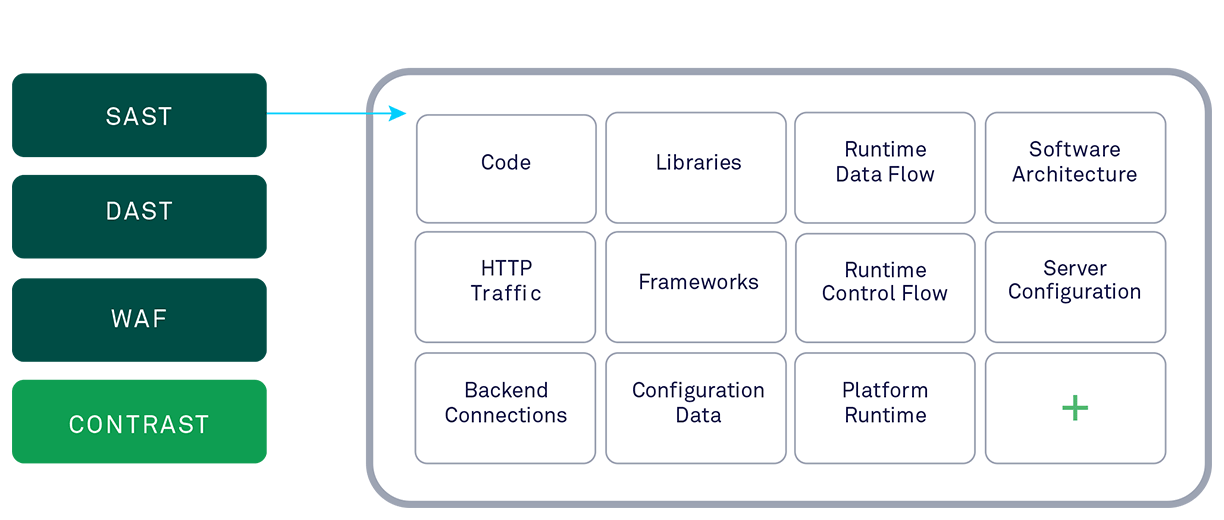
IAST, RASP, and Runtime Instrumentation Securing Apps
Iast rasp and runtime instrumentation – IAST, RASP, and runtime instrumentation are crucial for securing applications. This exploration delves into…
Read More » -
Classifying Malware Using Deep Learning A Deep Dive
Classifying malware using deep learning is revolutionizing cybersecurity. Traditional methods struggle with the ever-evolving nature of malicious software. Deep learning,…
Read More » -

How to Use Asset Management Software for Cyber Risk Reduction
How to use your asset management software to reduce cyber risks is crucial in today’s digital landscape. Protecting your valuable…
Read More » -
How to Track Ransomware Attacks A Guide
How to track ransomware attacks a comprehensive guide sets the stage for this detailed exploration of a critical cybersecurity concern.…
Read More »

