Cybersecurity
-

Hackers Cyberattack Amazon Cloud to Mine Bitcoins
Hackers cyber attack amazon cloud to mine bitcoins, a disturbing trend, highlights the vulnerability of cloud services like Amazon Web…
Read More » -

Hackers Cyberattack US Power Firms New Malware Threat
Hackers cyber attack us power firms with a new malware, raising serious concerns about the resilience of our critical infrastructure.…
Read More » -

Hackers Are Turning Webcam Users Into Slaves A Deep Dive
Hackers are turning webcam users into slaves, leveraging various methods to gain control and exploit vulnerable individuals. This insidious practice…
Read More » -

Hackers Are Launching Fileless Cyber Attacks
Hackers are launching fileless cyber attacks, a sophisticated and insidious threat that bypasses traditional security measures. This new form of…
Read More » -

Hacker Destroys 18-Year Data of VFEmail
Hacker destroys 18 years old data of vfemail via cyber attack, leaving an 18-year-old victim reeling from the devastating loss…
Read More » -
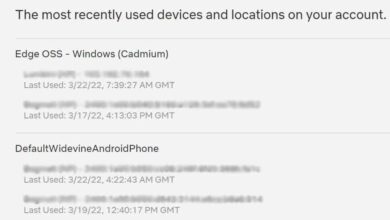
Hacked Houseparty App Netflix & Spotify Breach
Hacked houseparty app infiltrates netflix and spotify accounts, leaving a trail of compromised user data and raising serious concerns about…
Read More » -

Finlands Government Sites Hit by DDoS Attack
Government websites in Finland suffer DDoS cyber attack, highlighting a concerning trend of digital assaults on critical infrastructure globally. This…
Read More » -

Saudi Agencies Warned on Shamoon Attacks
Government agencies in Saudi Arabia warned against Shamoon cyber attacks, highlighting the escalating threat landscape in the region. These sophisticated…
Read More » -

Global Cyber Threats Government Action Plan
Government cybersecurity is a global problem heres how agencies can address it. The digital age has brought unprecedented opportunities, but…
Read More »

