IT Security
-

Glass Class Mitigating Risk Before Shadow It
Glass class mitigating risk before shadow it – Glass Class: Mitigating Risk Before Shadow It – sounds like a sci-fi…
Read More » -
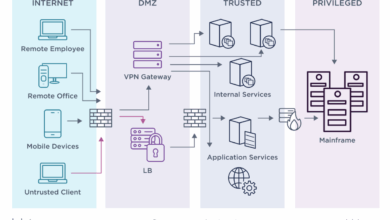
Enterprise Information Networks and the Threat Environment
Enterprise information networks and the threat environment are more intertwined than ever. Think about it – your company’s entire digital…
Read More » -

Ensuring Data Security in Slack
Ensuring data security in Slack isn’t just about ticking boxes; it’s about building a robust, secure environment for your team’s…
Read More » -

Dangerous Flaws Found in Cisco, Microsoft, Citrix, and IBM Remote Access Devices
Dangerous flaws found in cisco microsoft citrix and ibm remote work access and perimeter devices – Dangerous flaws found in…
Read More » -

Creating a Culture of Cybersecurity 2 A Deeper Dive
Creating a Culture of Cybersecurity 2 isn’t just about installing software; it’s about fundamentally shifting how your organization thinks about…
Read More » -

Citrix App Protection Helps Secure Remote Workers
Citrix App Protection helps secure remote workers, a critical need in today’s increasingly distributed workforce. This powerful solution safeguards sensitive…
Read More » -

Businesses Shift Toward Compliance as Code
Businesses shift toward compliance as code – it sounds like a techy buzzword, right? But it’s actually a game-changer for…
Read More » -

Be Cybersmart 4 ERP Security Best Practices
Be cybersmart 4 erp best practices to prioritize security – Be Cybersmart: 4 ERP Security Best Practices – that’s the…
Read More » -

A Guide to Handling SAP Security Breaches
A Guide to Handling SAP Security Breaches: Think your SAP system is impenetrable? Think again! This isn’t your grandpappy’s accounting…
Read More »

