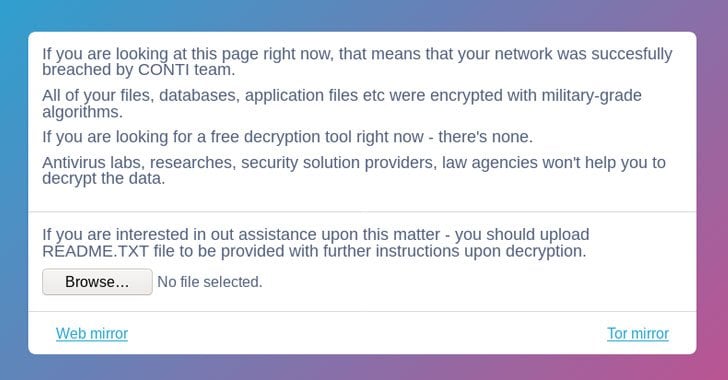
Conti Ransomware Targets Wind Turbine Giant Nordex
Conti ransomware targets wind turbine giant Nordex – a chilling headline that throws a spotlight on the increasingly vulnerable nature of critical infrastructure. Imagine the impact: a standstill of clean energy production, potentially impacting millions, all because of a sophisticated cyberattack. This isn’t just another ransomware story; it’s a wake-up call about the interconnectedness of our digital world and the real-world consequences of cybercrime.
This post delves into the details of this attack, exploring the vulnerabilities exploited, the damage inflicted, and the crucial lessons learned for the future of cybersecurity in the energy sector.
We’ll examine Nordex’s operational technology (OT) infrastructure, pinpoint potential weaknesses Conti exploited, and analyze the financial and reputational fallout. We’ll also investigate Conti’s tactics, from initial access to data exfiltration and encryption, and explore how this attack compares to other significant ransomware incidents targeting critical infrastructure. Get ready for a deep dive into the digital battlefield where clean energy meets cybercrime.
Nordex’s Vulnerability
The Conti ransomware attack on Nordex, a leading wind turbine manufacturer, highlighted significant vulnerabilities within the company’s operational technology (OT) infrastructure. While the specifics of the attack remain partially undisclosed, the incident underscores the growing threat landscape facing the energy sector and the critical need for robust cybersecurity measures in industrial control systems (ICS). This analysis delves into the potential weaknesses exploited and the resulting impact on Nordex’s operations.Nordex’s operational technology (OT) infrastructure, like many industrial companies, likely consists of a complex network of systems managing and monitoring the wind turbines themselves.
This includes Supervisory Control and Data Acquisition (SCADA) systems, Programmable Logic Controllers (PLCs), and various sensors and actuators distributed across geographically dispersed wind farms. These systems, often running legacy software and lacking robust security features, represent attractive targets for ransomware operators. Conti likely exploited vulnerabilities in these OT networks, potentially gaining access through phishing campaigns targeting employees, exploiting unpatched software vulnerabilities, or leveraging compromised remote access points.
Impact of the Ransomware Attack on Wind Turbine Operations
A successful ransomware attack on Nordex’s OT infrastructure could have had severe consequences. The immediate impact would likely have been downtime for affected wind turbines. This translates directly into lost energy generation, impacting Nordex’s revenue and potentially disrupting electricity supply to the grid. Beyond the immediate loss of production, the attack could have resulted in significant repair costs.
Restoring systems, verifying data integrity, and implementing enhanced security measures would have required substantial financial investment and time. The potential for physical damage to turbines due to malfunctions resulting from the attack also cannot be ruled out. For example, a ransomware attack disrupting control systems could lead to turbine overspeed or component failure, requiring costly repairs and potentially delaying project completion.
The reputational damage caused by such an event could further impact Nordex’s business.
Comparison of Nordex’s Cybersecurity Posture to Industry Best Practices
Assessing Nordex’s cybersecurity posture before the attack requires careful consideration, as complete details are not publicly available. However, based on the occurrence of the attack and industry trends, we can infer some aspects of their security measures and compare them to best practices.
| Measure | Nordex’s Approach (Inferred) | Industry Best Practice | Gap Analysis |
|---|---|---|---|
| Network Segmentation | Likely insufficient segmentation between IT and OT networks, allowing lateral movement. | Strict network segmentation between IT and OT, with strong access controls and monitoring. Air-gapping where possible. | Significant gap; lack of proper segmentation increased attack surface. |
| Patch Management | Possibly inadequate or delayed patching of vulnerabilities in OT systems. | Regular and timely patching of all systems, including OT devices, with automated vulnerability scanning. | Significant gap; outdated software represents a major vulnerability. |
| Access Control | Potentially weak authentication and authorization mechanisms. | Strong multi-factor authentication (MFA) for all users, role-based access control (RBAC), and regular access reviews. | Significant gap; weak access control facilitated unauthorized access. |
| Security Awareness Training | Possibly insufficient training for employees on phishing and social engineering tactics. | Regular and comprehensive security awareness training for all employees, including simulated phishing campaigns. | Potential gap; successful phishing attacks suggest a lack of adequate training. |
| Incident Response Plan | Likely lacked a comprehensive and tested incident response plan specific to ransomware attacks. | Well-defined incident response plan with established procedures for detection, containment, eradication, recovery, and post-incident activity. Regular drills and testing. | Significant gap; a robust plan is crucial for minimizing damage. |
Conti’s Tactics, Techniques, and Procedures (TTPs): Conti Ransomware Targets Wind Turbine Giant Nordex
The Conti ransomware group, known for its sophisticated attacks targeting large organizations, likely employed a multi-stage approach to compromise Nordex’s systems. Understanding their TTPs is crucial for improving cybersecurity defenses against future attacks. This analysis focuses on the probable methods used, considering Conti’s established modus operandi and the nature of the Nordex incident.Conti’s methods are notoriously adaptable, leveraging a combination of initial access vectors and advanced techniques to achieve their objectives.
They often exploit vulnerabilities in widely used software or rely on social engineering to gain a foothold within a target’s network. Once inside, they move laterally to identify and exfiltrate valuable data before deploying their ransomware payload.
Initial Access Vectors
Conti’s initial access is often achieved through various means. While the specific vulnerability exploited in the Nordex case has been addressed, we can speculate on likely methods based on Conti’s past campaigns. These include phishing emails containing malicious attachments or links, exploiting known vulnerabilities in unpatched software (particularly in industrial control systems given Nordex’s industry), or leveraging compromised credentials obtained through previous breaches.
The use of a zero-day exploit, while less probable due to the higher resource investment, remains a possibility. The success of these methods hinges on the target’s security posture, with inadequate patching and employee training representing significant weaknesses.
Ransomware Variant and Capabilities
Identifying the precise Conti ransomware variant used in the Nordex attack is challenging without official confirmation. However, Conti’s ransomware is known for its advanced capabilities, including data encryption, data exfiltration, and double extortion tactics. The ransomware likely employed strong encryption algorithms, making decryption without the decryption key extremely difficult. Furthermore, the variant probably included features for disabling security software and deleting shadow copies to hinder recovery efforts.
The sophistication of Conti’s ransomware makes recovery extremely difficult without paying the ransom or having a robust backup and recovery plan in place.
Data Exfiltration Techniques
Data exfiltration is a critical phase in Conti’s attack chain, enabling the group to leverage the double extortion tactic. Before deploying the ransomware, Conti likely employed several methods to steal sensitive data. The selection of methods would depend on the network’s architecture and security controls.
The following is a list of potential data exfiltration methods employed:
- Compromised Credentials: Using stolen credentials, Conti could have accessed file shares, databases, and other sensitive data repositories directly.
- Remote Access Tools (RATs): Installing RATs on compromised machines allowed for remote access and data transfer.
- Command and Control (C2) Servers: Data could have been exfiltrated via encrypted channels to the group’s C2 servers.
- Data Transfer via Cloud Storage: Data could have been uploaded to cloud storage services, either compromised accounts or newly created ones.
- File Transfer Protocol (FTP): Conti may have used FTP to transfer data to external servers.
Impact Assessment and Response

The Conti ransomware attack on Nordex, a significant player in the wind energy sector, presents a complex scenario with potentially devastating financial and reputational consequences. Assessing the full impact requires considering both immediate, direct costs and the longer-term, indirect effects that ripple through the company’s operations and market standing. The scale of the damage depends heavily on the extent of data breach, the disruption to operations, and the effectiveness of Nordex’s response.The financial losses incurred by Nordex can be substantial.
Direct costs include the expenses associated with incident response – hiring cybersecurity experts, engaging forensic investigators, paying ransoms (if any were paid), and recovering and restoring systems. Indirect costs are far more challenging to quantify but could be even more significant. These include lost revenue due to operational downtime, the cost of rebuilding damaged systems and data, the expense of notifying affected customers and regulatory bodies, and potential legal fees related to data breach litigation.
For example, a similar attack on a smaller energy company might cost millions in direct costs alone, and indirect losses from lost contracts and reputational damage could easily multiply that figure several times over. The size and complexity of Nordex’s operations suggest the potential for losses to reach tens or even hundreds of millions of Euros.
Financial Losses
The financial impact extends beyond immediate costs. Disruption to project timelines due to compromised systems could lead to significant penalties for missed deadlines in wind farm construction contracts. Furthermore, the loss of sensitive data, such as intellectual property related to turbine design or customer information, could lead to competitive disadvantage and erode trust with clients. This could result in the loss of future contracts and damage Nordex’s long-term profitability.
The Conti ransomware attack on Nordex, a major wind turbine manufacturer, highlights the vulnerability of critical infrastructure. This incident underscores the need for robust, adaptable security systems, and that’s where the future of application development comes in. Learning more about efficient development through domino app dev, the low-code and pro-code future , could help companies like Nordex build more resilient systems against future cyberattacks.
Ultimately, stronger security measures are crucial to protecting our energy grid from these kinds of devastating ransomware attacks.
The overall financial impact is a complex interplay of direct costs, lost revenue, and potential future losses stemming from compromised reputation and diminished market share. Accurate estimation would require a detailed forensic analysis of the attack’s scope and impact.
Reputational Damage and Investor Confidence
A ransomware attack on a company of Nordex’s stature carries significant reputational risks. News of the breach can damage investor confidence, leading to a decline in stock price and making it more expensive to secure future funding. Customers may question the company’s security practices and reliability, potentially leading to contract cancellations or reluctance to engage in new business.
The impact on Nordex’s brand reputation could be long-lasting, especially within the highly regulated energy sector. This damage to reputation is hard to quantify directly but can have a significant and prolonged impact on the company’s valuation and future growth prospects. Similar incidents in other sectors have demonstrated how swiftly a negative reputation can spread and how difficult it is to regain lost trust.
Hypothetical Incident Response Plan
A comprehensive incident response plan is crucial for mitigating the impact of a ransomware attack on a wind energy company. The plan should be tailored to the specific vulnerabilities of the organization and its critical infrastructure. The plan should detail steps to contain the attack, eradicate the malware, recover data, and communicate with stakeholders. Key elements include a robust cybersecurity infrastructure with strong access controls, regular backups, and employee security awareness training.
The plan should also Artikel procedures for collaborating with law enforcement and cybersecurity specialists, and for notifying affected parties, including customers, regulators, and investors. Furthermore, a post-incident review should be conducted to identify weaknesses in the existing security posture and implement improvements to prevent future attacks. The plan should include detailed contact lists, communication protocols, and a pre-approved budget for incident response activities.
Regular testing and updates are crucial to ensure the plan remains effective in the face of evolving threats.
Lessons Learned and Mitigation Strategies

The Conti ransomware attack on Nordex serves as a stark reminder of the vulnerability of industrial control systems (ICS) within the wind energy sector. This incident highlights the critical need for robust cybersecurity measures tailored to the specific challenges of this industry, moving beyond generic IT security practices. Failing to address these vulnerabilities leaves wind farms exposed to significant financial losses, operational disruptions, and potential safety hazards.
A proactive and layered approach is crucial for effective mitigation.
Securing ICS in the wind energy sector requires a multi-faceted strategy that addresses the unique characteristics of these systems. These systems often involve a mix of legacy and modern technologies, making them particularly susceptible to attacks. Furthermore, the geographically dispersed nature of wind farms and the reliance on remote monitoring and control present additional challenges. A robust cybersecurity strategy must encompass all aspects of the system, from the turbines themselves to the supervisory control and data acquisition (SCADA) systems and network infrastructure.
Best Practices for Securing Industrial Control Systems (ICS) in the Wind Energy Sector
Implementing strong cybersecurity measures within the wind energy sector requires a holistic approach that goes beyond simple antivirus software. This involves a combination of technological solutions, operational procedures, and employee training. A layered security approach is essential, focusing on multiple points of defense to prevent, detect, and respond to cyber threats. This includes robust network segmentation, intrusion detection systems, and regular security assessments to identify and address vulnerabilities before they can be exploited.
Furthermore, rigorous access control measures and employee training on cybersecurity best practices are vital to minimizing human error, a frequent factor in successful cyberattacks.
Preventative Measures Against Ransomware Attacks
A proactive approach to cybersecurity is paramount in preventing ransomware attacks. This involves implementing a layered security strategy that combines technical safeguards with robust security policies and employee training. The following table Artikels key preventative measures, their implementation costs, and effectiveness:
| Threat Vector | Mitigation Strategy | Implementation Cost | Effectiveness |
|---|---|---|---|
| Phishing Emails | Security Awareness Training, Email Filtering, Multi-Factor Authentication | Medium – High (depending on training scope and email filtering solution) | High |
| Exploiting Software Vulnerabilities | Regular Patching and Vulnerability Scanning, Software Inventory Management | Medium | High |
| Weak Passwords | Password Management Policies, Multi-Factor Authentication, Password Managers | Low – Medium | High |
| Malware Infections | Antivirus Software, Endpoint Detection and Response (EDR), Network Segmentation | Medium – High | Medium – High |
| Unpatched or Outdated Systems | Regular Software Updates, Automated Patch Management | Medium | High |
| Insider Threats | Access Control Policies, Background Checks, Regular Security Audits | Medium – High | Medium – High |
| Remote Access Vulnerabilities | Secure Remote Access Solutions (VPN with MFA), Regular Security Audits of Remote Access Points | Medium – High | High |
Implementing Multi-Factor Authentication and Regular Security Audits
Multi-factor authentication (MFA) significantly enhances security by requiring multiple forms of verification to access systems. This can include something you know (password), something you have (security token), and something you are (biometrics). Implementing MFA across all systems, particularly those with access to ICS, is a critical step in preventing unauthorized access. Regular security audits provide a systematic review of security controls, identifying vulnerabilities and weaknesses.
These audits should encompass all aspects of the ICS infrastructure, including network security, access control, and software configurations. They should be conducted by qualified professionals with expertise in ICS security.
The Broader Context
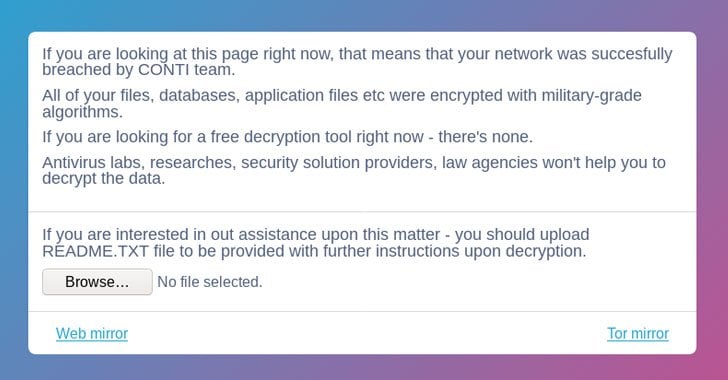
The Conti ransomware attack on Nordex, a significant player in the wind turbine industry, highlights a growing threat: the targeting of critical infrastructure by sophisticated ransomware gangs. This isn’t an isolated incident; it represents a worrying trend with potentially devastating consequences for energy security and the global economy. Understanding this attack within the larger context of ransomware attacks on critical infrastructure is crucial for developing effective mitigation strategies.The attack on Nordex shares similarities with other high-profile incidents, such as the Colonial Pipeline attack in 2021 and the attack on the Oldsmar, Florida water treatment plant in 2021.
These attacks all involved the exploitation of vulnerabilities in operational technology (OT) systems, causing significant disruption to essential services. While the specific vulnerabilities and techniques varied, the common thread is the exploitation of weaknesses in cybersecurity defenses to achieve a high-impact outcome. The disruption caused by these attacks, measured in financial losses and the impact on public services, underscores the severity of the threat.
Unlike attacks targeting financial institutions, which primarily aim for financial gain, attacks on critical infrastructure often have broader societal consequences, including potential threats to public health and safety.
Comparison of Ransomware Attacks Targeting Critical Infrastructure
The Nordex attack, while significant due to its impact on the renewable energy sector, differs from the Colonial Pipeline attack in its target. Colonial Pipeline’s attack disrupted fuel distribution across a large portion of the eastern United States, resulting in fuel shortages and price hikes. The Nordex attack, while potentially causing delays in wind turbine production and maintenance, did not result in a similarly widespread immediate disruption to energy supply.
However, the long-term implications for the renewable energy sector, which is vital for addressing climate change, are substantial. Both attacks, however, highlight the vulnerability of critical infrastructure to ransomware attacks, regardless of the specific industry. The Oldsmar water treatment plant attack, while smaller in scale, demonstrates the potential for even more catastrophic consequences – in this case, the potential contamination of drinking water.
The common factor across all three is the significant disruption caused by exploiting relatively minor security flaws.
Implications for Energy Security and the Broader Economy, Conti ransomware targets wind turbine giant nordex
Ransomware attacks targeting critical infrastructure, such as energy providers, pose a significant threat to energy security. Disruptions to energy production, distribution, or consumption can lead to power outages, supply chain disruptions, and economic instability. The cost of recovery, including paying ransoms (though this is highly discouraged), hiring cybersecurity experts, and restoring systems, can be astronomical. Beyond the direct financial costs, there are indirect costs associated with reputational damage, loss of customer trust, and potential legal liabilities.
For example, the Colonial Pipeline attack cost the company millions of dollars, and the economic ripple effects extended far beyond the company itself. The impact on consumer confidence and the potential for increased energy prices are also significant considerations. The increasing reliance on interconnected digital systems within critical infrastructure magnifies the potential impact of ransomware attacks, making proactive cybersecurity measures essential.
Recommendations for Improving Resilience
The vulnerability of critical infrastructure to ransomware attacks necessitates a multi-pronged approach to improve resilience. This requires collaboration between government agencies, industry organizations, and individual companies.
A proactive strategy is essential, rather than simply reacting to incidents. This includes:
- Mandatory Cybersecurity Standards and Regulations: Governments should establish and enforce stricter cybersecurity standards and regulations specifically tailored to critical infrastructure sectors. This includes regular security audits and vulnerability assessments.
- Improved Information Sharing and Collaboration: Facilitating secure information sharing between industry players and government agencies is vital for rapid threat detection and response. This should include sharing of threat intelligence and best practices.
- Investment in Cybersecurity Infrastructure and Training: Significant investment in advanced cybersecurity technologies, such as intrusion detection systems and endpoint detection and response (EDR) solutions, is crucial. Equally important is investing in comprehensive cybersecurity training for personnel across all levels.
- Incident Response Planning and Exercises: Developing robust incident response plans and conducting regular simulations and exercises are essential for effective response to ransomware attacks. This includes having clearly defined roles, responsibilities, and communication protocols.
- Promoting Cybersecurity Awareness: Raising awareness among employees about phishing scams, social engineering attacks, and other common ransomware attack vectors is paramount. This includes regular security awareness training and phishing simulations.
- Strengthening Supply Chain Security: Ransomware attacks often exploit vulnerabilities in the supply chain. Therefore, strengthening the security posture of vendors and suppliers is critical. This includes conducting thorough due diligence on third-party vendors and implementing robust access controls.
Visual Representation of the Attack
Visualizing the Conti ransomware attack on Nordex requires understanding its likely progression, from initial compromise to data exfiltration and encryption. This involves considering the network architecture of a large multinational company like Nordex, which likely includes a complex mix of on-premise servers, cloud infrastructure, and remote industrial control systems (ICS). The attack likely exploited vulnerabilities in less secure parts of the network to gain a foothold and then moved laterally to more critical systems.The following diagram depicts a plausible attack scenario.
It’s important to remember this is a representation based on common Conti TTPs and general industrial network structures; the precise details of the Nordex attack remain confidential.
Network Topology and Attack Progression
Imagine a diagram showing a simplified Nordex network. We have several distinct zones: the external internet, a demilitarized zone (DMZ) containing publicly accessible servers, an internal network segment for corporate applications and data, and a separate, highly segmented network for ICS controlling the wind turbines. These zones are connected via firewalls and other security appliances.The attack likely began with an initial access vector – perhaps a phishing email targeting an employee in the corporate network, exploiting a vulnerability in their email client or a less-secure application.
Once inside the corporate network, the attacker leveraged compromised credentials or exploited vulnerabilities in software to move laterally, gaining access to more privileged accounts and systems. This lateral movement could involve exploiting known vulnerabilities in Windows servers, Active Directory, or other enterprise applications. The attackers then likely used tools to map the network and identify valuable data, including potentially sensitive engineering designs, customer data, or financial records.
Data Exfiltration and Encryption
Once the attackers had identified high-value targets, they would have exfiltrated the data using techniques such as command-and-control (C2) servers or compromised cloud storage accounts. The data exfiltration likely happened over a period of time, using techniques to avoid detection. After exfiltrating the data, the attackers would then deploy the Conti ransomware, encrypting critical files on the servers and potentially even extending into the ICS network, although this is less likely due to the higher level of segmentation typically found in such environments.
The encryption process would likely involve multiple stages and the use of sophisticated encryption algorithms. The final stage would be the deployment of a ransom note demanding payment in cryptocurrency for the decryption key.
Illustrative Diagram Description
The diagram would show four main sections: the internet, the DMZ, the corporate network, and the ICS network. Arrows would illustrate the attack path: from a phishing email (external) to a compromised workstation (corporate network), then lateral movement to a domain controller (corporate network), data exfiltration to a C2 server (internet), and finally, ransomware deployment across selected servers (corporate network, potentially limited to ICS network).
Each network segment would be represented by a distinct shape (e.g., rectangles for networks, circles for servers), with firewalls depicted as barriers between segments. The diagram would also include icons representing various security tools and technologies (e.g., antivirus, intrusion detection system), showing how these were potentially bypassed or circumvented by the attackers. The use of different colors to represent different network segments and the attack’s progression would enhance clarity.
Closing Notes
The Conti ransomware attack on Nordex serves as a stark reminder of the escalating threats facing critical infrastructure. The vulnerability of OT systems, coupled with the sophistication of modern ransomware groups, necessitates a proactive and comprehensive approach to cybersecurity. From strengthening defenses against initial access attempts to implementing robust incident response plans, the energy sector must prioritize security to ensure resilience against future attacks.
This isn’t just about protecting profits; it’s about safeguarding essential services and maintaining the stability of our energy supply. The lessons learned from this incident should propel us toward a more secure and resilient future.
Popular Questions
What specific type of data did Conti likely steal from Nordex?
Likely targets include intellectual property related to turbine design, maintenance records, customer data, and potentially even operational control system configurations.
How long was Nordex likely offline due to the attack?
The duration of downtime would depend on the extent of the encryption and the effectiveness of Nordex’s recovery plan. It could range from days to weeks, potentially longer.
Did Nordex pay the ransom?
Whether or not Nordex paid the ransom is usually not publicly disclosed for security and legal reasons. Paying ransoms is generally discouraged due to its encouragement of further attacks.
What are the long-term consequences for Nordex beyond immediate financial losses?
Long-term consequences could include damaged reputation, loss of investor confidence, difficulty securing future contracts, and increased insurance premiums.