Center Identity Launches Patented Passwordless Authentication Solution
Center Identity launches patented passwordless authentication solution—a game-changer in online security! Tired of endless password resets and the constant threat of breaches? This innovative technology promises a smoother, more secure login experience, eliminating the need for passwords altogether. Imagine a world where accessing your accounts is as simple and secure as using your fingerprint or a unique code sent directly to your device.
That’s the future Center Identity is building, and it’s more accessible than you think.
This revolutionary approach utilizes cutting-edge cryptography and biometrics to verify user identity, offering unparalleled protection against phishing, brute-force attacks, and other common security threats. We’ll delve into the specifics of how it works, its competitive advantages, and its potential to reshape the digital landscape. Get ready to say goodbye to password fatigue and hello to a new era of online security.
Center Identity’s Patented Solution
Center Identity’s passwordless authentication solution represents a significant leap forward in online security. It moves beyond the limitations of traditional password-based systems, offering a more secure and user-friendly experience. This innovative approach leverages a unique combination of technologies to provide robust protection against unauthorized access while simplifying the login process for end-users.The core functionality revolves around a proprietary cryptographic protocol that links user devices to their accounts without relying on passwords.
Instead of remembering and entering passwords, users authenticate through a combination of device-specific cryptographic keys and time-sensitive, one-time codes generated by the system. This eliminates the vulnerabilities associated with password reuse, phishing attacks, and brute-force attempts.
Technical Architecture
The patented technology employs a multi-layered architecture. At its heart lies a distributed, fault-tolerant key management system that securely generates and manages cryptographic keys for each registered user. These keys are never transmitted in plain text, instead, they are used to derive unique authentication tokens. The system utilizes elliptic curve cryptography (ECC) for its high security and efficiency, and incorporates advanced techniques to protect against side-channel attacks.
User devices interact with the system via a secure API, ensuring all communication channels are encrypted using industry-standard protocols like TLS 1.3. The backend utilizes a robust database system with advanced access controls to safeguard user data. This robust infrastructure ensures the solution scales effectively to handle large numbers of users and transactions.
Security Mechanisms
Center Identity’s solution incorporates multiple layers of security to protect user data and prevent unauthorized access. Beyond the ECC-based cryptographic protocols, the system incorporates multi-factor authentication (MFA) options, allowing users to add an extra layer of security using methods such as biometric authentication (fingerprint or facial recognition) or hardware security keys. Regular security audits and penetration testing are conducted to identify and address potential vulnerabilities proactively.
Center Identity’s patented passwordless authentication solution is a game-changer, addressing a major vulnerability in traditional security. This innovative approach is particularly relevant in light of the increasing complexity of cloud security, as highlighted by the rise of Cloud Security Posture Management (CSPM) solutions like Bitglass – check out this insightful article on bitglass and the rise of cloud security posture management to learn more.
Ultimately, Center Identity’s solution helps bolster the overall security posture, even within the increasingly complex cloud environments.
The system also employs advanced threat detection mechanisms to monitor for suspicious activity and automatically block potentially malicious attempts. Data is encrypted both in transit and at rest, adhering to stringent industry best practices. Furthermore, the system incorporates robust logging and auditing capabilities to maintain a comprehensive record of all authentication events.
Comparison with Other Passwordless Methods
While other passwordless authentication methods exist, such as FIDO2 and magic links, Center Identity’s solution offers several key advantages. Unlike magic links, which are susceptible to email interception or phishing, Center Identity’s solution relies on device-specific keys and cryptographic tokens, making it significantly more resistant to these attacks. Compared to FIDO2, Center Identity’s approach provides a more seamless and user-friendly experience, requiring minimal user interaction beyond initial device registration.
The patented technology offers a more comprehensive and robust solution, addressing some of the limitations inherent in existing passwordless approaches. For instance, the system’s distributed architecture ensures high availability and resilience to attacks targeting a single point of failure, unlike some centralized passwordless solutions.
Market Positioning and Competitive Advantages
Center Identity’s passwordless authentication solution is poised to disrupt the current landscape of digital security. By eliminating the vulnerabilities inherent in password-based systems, we offer a significantly more secure and user-friendly alternative for a wide range of applications. This positions us for substantial growth in a market increasingly concerned with both security and user experience.The target audience for our solution is broad, encompassing individuals and organizations seeking enhanced security and streamlined authentication processes.
This includes enterprises needing robust security for sensitive data, government agencies prioritizing secure access control, and consumers demanding a simpler, more secure online experience. We also target developers seeking easy integration into their applications and platforms, reducing development time and security risks.
Competitive Landscape Analysis and Unique Selling Propositions
Center Identity differentiates itself through a combination of superior security, ease of use, and cost-effectiveness. Unlike many competitors relying on less secure methods, our patented technology utilizes advanced cryptographic techniques to provide unparalleled protection against various threats, including phishing and credential stuffing attacks. Furthermore, our solution’s seamless integration into existing systems minimizes disruption and simplifies the user onboarding process.
The intuitive design makes it accessible to a broader range of users, regardless of their technical proficiency. Finally, our flexible pricing model caters to the diverse needs and budgets of our clients.
Market Impact and Growth Opportunities
The global market for passwordless authentication is experiencing exponential growth, driven by increasing cyber threats and the rising demand for improved user experience. Center Identity is strategically positioned to capitalize on this trend. The adoption of our solution by major enterprises and government agencies will create a significant network effect, further accelerating market penetration. Growth opportunities exist in various sectors, including finance, healthcare, and e-commerce, where secure and user-friendly authentication is paramount.
For example, the increasing adoption of mobile banking and online healthcare services necessitates robust and secure authentication systems, creating a strong demand for our technology. We anticipate significant market share growth within the next three to five years, based on current market trends and our strong product-market fit.
Competitive Comparison Table
The following table compares Center Identity’s solution with three key competitors:
| Solution Name | Key Features | Security Protocols | Pricing Model |
|---|---|---|---|
| Center Identity | Passwordless authentication, multi-factor authentication (MFA) options, seamless integration, user-friendly interface, customizable branding. | Advanced cryptographic algorithms, biometric authentication support, regular security audits and updates. | Subscription-based, tiered pricing based on user count and features. |
| Competitor A | Passwordless authentication, limited MFA options, complex integration process, less intuitive interface. | Standard cryptographic algorithms, limited biometric support. | Per-user licensing, high upfront costs. |
| Competitor B | Passwordless authentication primarily through email verification, limited MFA options, basic integration. | Standard cryptographic algorithms, vulnerable to phishing attacks. | Freemium model with limited features in the free tier. |
| Competitor C | Passwordless authentication using one-time codes, limited MFA options, integration challenges, complex user interface. | Standard cryptographic algorithms, susceptible to code interception. | Per-user licensing, high ongoing maintenance costs. |
Implementation and User Experience

Integrating Center Identity’s passwordless authentication solution is designed for seamless deployment, minimizing disruption to existing workflows. The process focuses on ease of integration and a user-friendly experience, ensuring a smooth transition for both administrators and end-users. This allows for a rapid return on investment and immediate improvement in security.The implementation process involves several key steps, each designed to be straightforward and well-documented.
Our support team provides comprehensive guidance and assistance throughout the entire integration process, from initial assessment to final deployment.
Integration Steps
The integration of Center Identity’s solution typically involves these steps: API integration, user provisioning, and configuration of authentication policies. These steps are detailed below to provide a clear understanding of the process.
- API Integration: Our robust and well-documented APIs allow for quick and easy integration with existing systems. The process involves connecting your system to our platform using standard RESTful APIs. This allows for secure communication and data exchange between the two systems.
- User Provisioning: Center Identity offers flexible user provisioning methods. You can either integrate with your existing user directory or use our built-in user management system. This allows for centralized management of user accounts and simplifies the process of adding or removing users.
- Configuration of Authentication Policies: Administrators can configure various authentication policies, such as multi-factor authentication (MFA) options, to suit their specific security requirements. This granular control allows organizations to tailor their security posture to their specific needs and risk tolerance.
User Experience
From registration to authentication, the user experience is designed to be intuitive and secure. Users will find the process straightforward and efficient, requiring minimal effort while significantly enhancing security. This is achieved through a combination of streamlined workflows and clear, concise instructions.
- Registration: New users register using their existing email address or phone number. They receive a verification code via their chosen method. Once verified, they are ready to access the system.
- Authentication: Upon logging in, users are prompted to verify their identity using their preferred method, such as a one-time password (OTP) sent via SMS or email, or a biometric authentication method (if configured). This eliminates the need for remembering complex passwords.
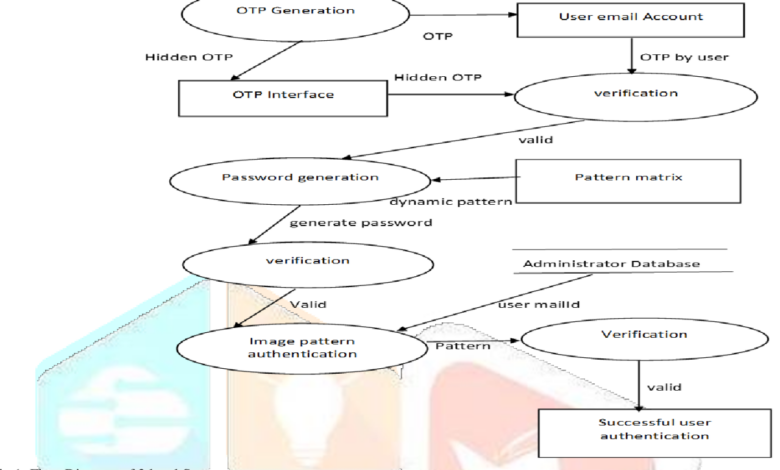
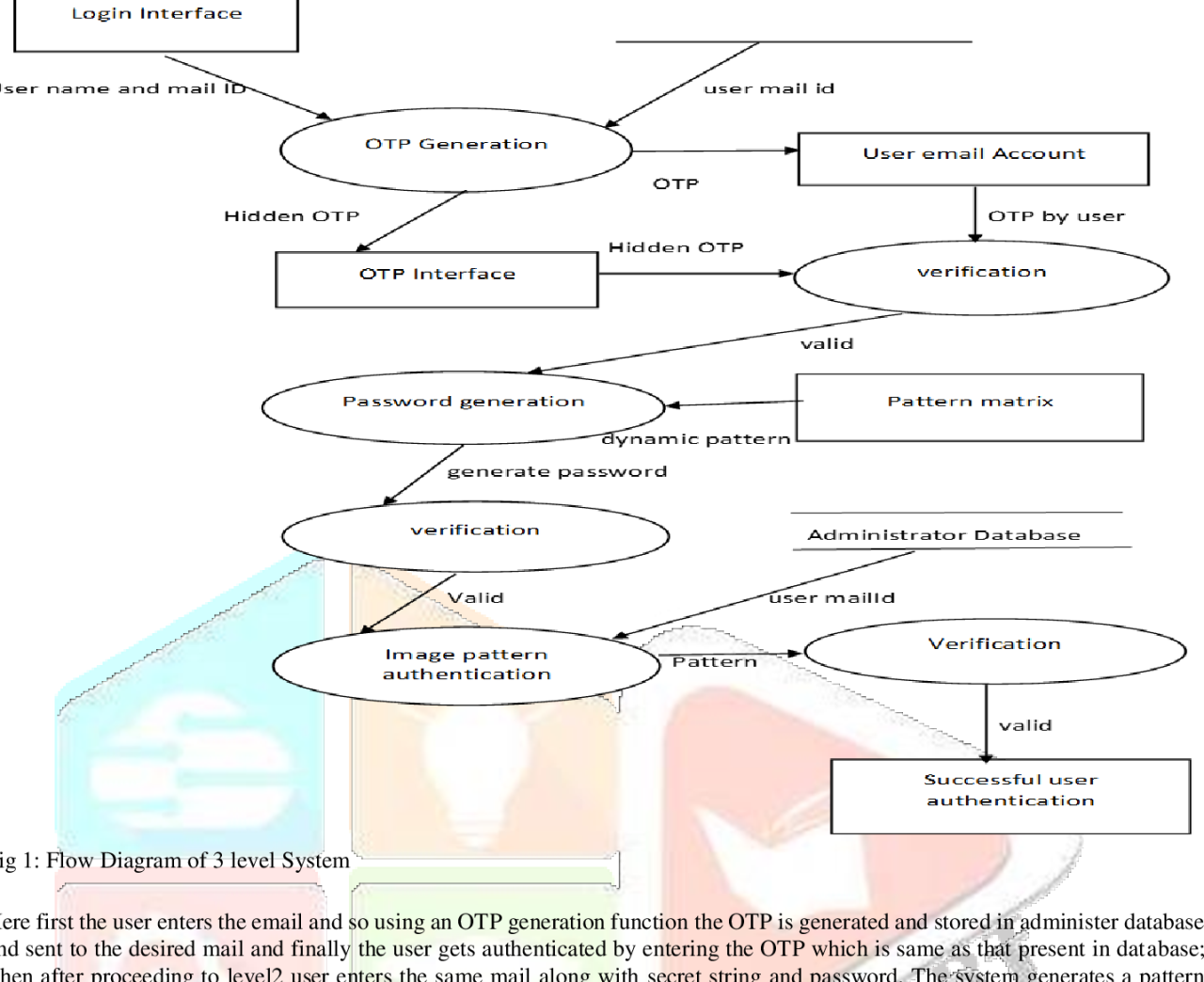
Authentication Process User Flow Diagram
Imagine a simple diagram. The process begins with the user attempting to access a protected resource. This triggers a request to Center Identity’s authentication server. The server then sends a verification code to the user’s registered device (phone or email). The user enters this code into the application.
The server verifies the code. If valid, access is granted; otherwise, access is denied. This entire process is seamless and happens within seconds.
User Roles and Interactions
Different user roles interact with the system in different ways. Administrators have full control over system settings and user management, while end-users primarily interact with the authentication process.
| User Role | Interaction with System |
|---|---|
| Administrator | Configures authentication policies, manages users, monitors system logs, and integrates with other systems. |
| End-User | Registers an account, authenticates using their chosen method, and accesses protected resources. |
Security and Privacy Considerations
Passwordless authentication, while offering a superior user experience, necessitates a robust security architecture to mitigate potential vulnerabilities. Center Identity’s solution prioritizes user privacy and data protection, adhering to stringent security protocols and relevant regulations. This section details our approach to ensuring the security and privacy of our users’ data.
Potential Security Vulnerabilities and Mitigation Strategies
Our passwordless system employs a multi-layered security approach to address potential vulnerabilities. One potential risk is unauthorized access through compromised devices. To mitigate this, we utilize multi-factor authentication (MFA) incorporating methods like biometric verification and one-time passwords (OTPs) sent to registered devices. Furthermore, we employ robust encryption techniques, both in transit and at rest, to protect user data from interception or unauthorized access.
Regular security audits and penetration testing identify and address any weaknesses before they can be exploited. We also maintain a vigilant monitoring system to detect and respond to suspicious activities in real-time. For instance, unusual login attempts from unfamiliar geographic locations trigger immediate alerts and potential account lockouts.
Privacy Implications and User Data Protection
User privacy is paramount. We collect only the minimum necessary data to provide our passwordless authentication service. This typically includes user identifiers, device information for security purposes, and authentication logs for security monitoring. All data is anonymized where possible and handled in accordance with our strict privacy policy. We utilize robust data encryption methods to protect user data from unauthorized access, both during transmission and storage.
Center Identity’s patented passwordless authentication solution is a game-changer for security, and its implications are huge. Thinking about how this impacts app development, it’s exciting to consider how this integrates with the evolving landscape of domino app dev, the low-code and pro-code future , making secure, streamlined applications even easier to build. Ultimately, this passwordless tech from Center Identity promises a smoother, safer user experience across the board.
Access to user data is strictly controlled and limited to authorized personnel on a need-to-know basis. We do not sell or share user data with third parties for marketing or other non-essential purposes.
Compliance with Data Privacy Regulations
Center Identity’s passwordless solution is designed to comply with all relevant data privacy regulations, including the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). We maintain comprehensive data processing agreements with our partners and adhere to strict data retention policies, ensuring compliance with all legal requirements. Our internal processes and procedures are regularly audited to confirm our ongoing compliance with these regulations.
For example, we provide users with clear and accessible mechanisms to exercise their data rights, such as the right to access, rectify, and erase their personal data.
Security Audit Process and Results
We conduct regular, independent security audits of our system and infrastructure. These audits involve penetration testing, vulnerability assessments, and code reviews performed by certified security experts. The most recent audit, conducted in [Month, Year] by [Auditing Firm Name], revealed no critical vulnerabilities. The audit report highlighted several minor issues, all of which were promptly addressed and remediated. These audits ensure the ongoing security and integrity of our passwordless authentication solution and provide us with continuous improvement opportunities.
The detailed audit report is available upon request to our enterprise clients.
Future Developments and Potential Applications
Center Identity’s passwordless authentication solution represents a significant leap forward in security and user experience. However, the potential for growth and application extends far beyond its current capabilities and target market. Future development will focus on enhancing its robustness, expanding its functionalities, and exploring new sectors where this technology can revolutionize access management.The core technology, while already highly secure and efficient, can be further refined and expanded to accommodate evolving technological landscapes and user needs.
This includes exploring integration with emerging technologies and enhancing its adaptability to diverse platforms and devices.
Potential Future Enhancements, Center identity launches patented passwordless authentication solution
Future enhancements will concentrate on improving scalability, optimizing performance for resource-constrained environments, and adding support for more authentication methods. This includes exploring the integration of biometric authentication, such as fingerprint or facial recognition, as an additional layer of security. We also plan to investigate advanced threat detection capabilities, leveraging machine learning to identify and mitigate potential security breaches in real-time.
Furthermore, improving the user interface and providing more customization options will be a key focus, ensuring seamless integration across various devices and platforms. The development of a comprehensive API will allow for seamless integration with existing systems and applications, fostering wider adoption.
Expansion Beyond the Current Target Market
Currently, our solution is targeted primarily at enterprise clients requiring robust security measures. However, the versatility of our passwordless authentication technology lends itself to a much broader application. By adapting the solution to meet the specific needs of various industries, we can significantly broaden its reach and impact.
Potential Industry Verticals
The inherent benefits of enhanced security and improved user experience make our solution attractive to a wide range of industries. Some key sectors that could greatly benefit from this technology include:
- Healthcare: Protecting sensitive patient data and streamlining access for authorized personnel.
- Finance: Securing online banking platforms and ensuring the integrity of financial transactions.
- Government: Improving the security of citizen portals and streamlining access to government services.
- Education: Simplifying student and faculty access to learning management systems and other educational resources.
- Retail: Enhancing the security of online shopping platforms and protecting customer data.
Hypothetical Scenario: Application in Healthcare
Imagine a large hospital system implementing Center Identity’s passwordless authentication solution. Physicians, nurses, and other healthcare professionals could access patient records and electronic health records (EHRs) securely using their mobile devices through biometric authentication, eliminating the need for passwords and reducing the risk of unauthorized access. This streamlined access improves efficiency, enhances patient care, and reduces the administrative burden associated with password management.
Furthermore, the system’s advanced threat detection capabilities could identify and prevent malicious attempts to access sensitive patient data, ensuring compliance with HIPAA regulations and maintaining patient privacy. This approach also significantly reduces the risk of phishing attacks, a common problem in the healthcare industry, as there are no passwords to steal or reset. The system’s inherent security features and the elimination of password-related vulnerabilities drastically reduce the hospital’s overall security risk profile.
Wrap-Up

Center Identity’s patented passwordless authentication solution isn’t just another security upgrade; it’s a paradigm shift. By eliminating passwords, the company tackles a major vulnerability in the current online ecosystem. The seamless user experience, robust security features, and potential for widespread adoption across various industries make this a technology worth watching. It’s a compelling solution to a persistent problem, and the implications for enhanced security and user convenience are significant.
The future of secure online access is here, and it’s passwordless.
Popular Questions: Center Identity Launches Patented Passwordless Authentication Solution
What types of devices are compatible with Center Identity’s solution?
The solution is designed to be highly adaptable and works across a range of devices, including smartphones, tablets, and laptops, supporting various operating systems.
How does Center Identity protect user data from unauthorized access?
Center Identity employs multi-layered security measures, including encryption, data anonymization, and robust access controls, to safeguard user data and comply with relevant privacy regulations.
What is the cost of implementing Center Identity’s passwordless authentication solution?
Pricing varies depending on the specific needs and scale of implementation. Contact Center Identity directly for a customized quote.
What happens if a user loses their authentication device?
Center Identity provides recovery mechanisms to ensure users can regain access to their accounts even if they lose their primary authentication device. These typically involve secondary verification methods.