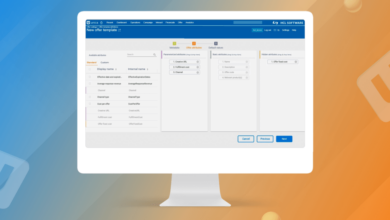
Unica Journey Dynamic Content, Decisions & Splits
Unica Journey handling dynamic content using decision and engagement splits is a powerful way to personalize user experiences. This involves leveraging Unica Journey’s architecture to deliver tailored content based on individual user profiles, behaviors, and real-time data. We’ll explore how decisioning engines and A/B testing (engagement splits) work within Unica Journey to optimize content delivery, leading to improved engagement and conversions.
This journey will cover best practices, implementation strategies, and the critical role of data quality in achieving impactful personalization.
We’ll delve into the technical aspects, including integrating external data sources and utilizing various personalization techniques. From setting up business rules to measuring campaign effectiveness using key performance indicators (KPIs), we’ll cover everything you need to know to harness the full potential of dynamic content within the Unica Journey platform. We’ll also touch upon advanced topics like machine learning and AI for enhanced personalization, alongside crucial security and privacy considerations.
Unica Journey’s Dynamic Content Capabilities: Unica Journey Handling Dynamic Content Using Decision And Engagement Split
Unica Journey, IBM’s marketing automation platform, boasts powerful capabilities for delivering personalized experiences through dynamic content. This allows marketers to tailor messaging and offers to individual customers based on their specific characteristics, behaviors, and interactions. The system goes beyond simple segmentation, offering a sophisticated approach to real-time personalization that enhances engagement and conversion rates.
Unica Journey’s Architecture for Handling Dynamic Content
Unica Journey’s architecture centers around a rules-based engine that processes customer data and applies predefined rules to select the most relevant content. This engine integrates with various data sources, including CRM systems, transactional databases, and external marketing data providers. The data is processed in real-time or near real-time, allowing for highly personalized content delivery across multiple channels, such as email, web, and mobile.
The system utilizes a combination of predefined templates and dynamic content blocks, allowing for flexible and scalable content creation and management. These blocks are populated with data from the customer profile and external sources, ensuring that each customer receives a unique experience.
Personalization Mechanisms in Unica Journey
Unica Journey employs several mechanisms to personalize user experiences. These include using customer attributes (demographics, purchase history, preferences), behavioral data (website activity, email opens, clicks), and contextual data (time of day, location) to dynamically populate content elements. For instance, a customer who frequently purchases sporting goods might receive an email promoting a new line of athletic apparel, while a customer who primarily buys books might receive recommendations for new releases.
The system also leverages predictive modeling to anticipate customer needs and proactively deliver relevant content. This predictive capability helps anticipate future purchases or interests, leading to more effective and targeted campaigns.
Integration with External Data Sources
Unica Journey seamlessly integrates with various external data sources to enhance personalization. This integration allows marketers to leverage a broader range of data points to create more refined customer segments and deliver more relevant content. Common data sources include CRM systems (Salesforce, SAP), marketing automation platforms, and external data providers that offer demographic, behavioral, and firmographic information. This integration is typically achieved through APIs or data connectors, enabling real-time or batch data updates.
For example, integrating with a CRM system allows marketers to access real-time customer information such as purchase history, support interactions, and account details, directly enriching the content within the Unica Journey campaigns.
Comparison of Content Personalization Techniques
The following table compares different content personalization techniques supported by Unica Journey:
| Technique | Description | Advantages | Disadvantages |
|---|---|---|---|
| Rule-based personalization | Using predefined rules to select content based on customer attributes and behaviors. | Simple to implement, easy to manage, cost-effective. | Can become complex with many rules, may not adapt well to changing customer behavior. |
| Recommendation engines | Suggesting products or content based on customer preferences and past behavior. | Highly effective at increasing engagement and sales, improves customer experience. | Requires significant data volume for accurate recommendations, can be computationally expensive. |
| AI-powered personalization | Utilizing machine learning algorithms to personalize content in real-time. | Highly adaptable to changing customer behavior, provides highly relevant content. | Requires significant technical expertise and data infrastructure, can be expensive. |
| A/B testing | Comparing different versions of content to determine which performs best. | Data-driven approach to optimization, improves campaign effectiveness. | Requires time and resources to conduct tests, results may not be generalizable. |
Decisioning and Engagement Split in Unica Journey
Unica Journey’s power lies in its ability to deliver personalized experiences. This is achieved through a sophisticated system of decisioning and engagement splits, allowing marketers to tailor content and offers based on individual customer profiles and behaviors. By dynamically adjusting the journey based on real-time data, Unica Journey maximizes engagement and conversion rates.
The Role of Decisioning in Dynamic Content Delivery
Decisioning in Unica Journey acts as the brain of the customer journey. It uses pre-defined rules and real-time data to determine which content or offer a specific customer receives at each touchpoint. This ensures that every interaction feels relevant and personalized, leading to improved customer engagement and ultimately, higher ROI. The system analyzes customer attributes, past interactions, and even real-time behavior to dynamically route the customer through different paths within the journey.
This ensures the right message reaches the right person at the right time.
Setting up A/B and Multivariate Testing with Engagement Splits
Engagement splits in Unica Journey facilitate A/B and multivariate testing, allowing marketers to compare different versions of content or offers to determine which performs best. Setting up an A/B test involves creating two or more variations of a specific element within the journey (e.g., different subject lines for an email). Unica Journey then automatically distributes traffic across these variations, allowing for a statistically significant comparison of their performance.
Multivariate testing expands upon this by testing multiple elements simultaneously, enabling a more comprehensive understanding of which combinations yield the best results. The system tracks key metrics such as open rates, click-through rates, and conversions to identify the winning variation.
Examples of Business Rules for Dynamic Content Delivery, Unica journey handling dynamic content using decision and engagement split
Business rules are the core of Unica Journey’s decisioning engine. These rules dictate how the system routes customers based on specific criteria. For instance, a rule might state: “If a customer is a high-value customer AND has recently viewed product X, then show them a personalized offer for product Y.” Another example could be: “If a customer has abandoned their shopping cart, send them a reminder email with a special discount.” These rules can be based on various data points, including demographics, purchase history, website activity, and even real-time behavior such as location or device.
Complex rules can be built using logical operators (AND, OR, NOT) to create highly targeted and personalized experiences.
Decisioning Process Flowchart: Personalized Product Recommendations
Imagine a customer browsing an e-commerce website. The following flowchart illustrates how Unica Journey’s decisioning engine might work to deliver personalized product recommendations:[Descriptive Flowchart]The flowchart begins with the customer’s profile data being accessed. This data includes browsing history, purchase history, and demographic information. This data is then fed into a decision node that evaluates pre-defined business rules. One rule might be: “If the customer has viewed products in category A, recommend products from category B.” Another rule might be: “If the customer has purchased products from category C, recommend similar products or complementary products.” Based on these rules, the system selects the most relevant product recommendations.
Unica’s journey with dynamic content, using decision and engagement splits, is fascinating! It’s all about tailoring the user experience, and I’ve been thinking how this relates to the broader trend of app development. Check out this article on domino app dev the low code and pro code future to see how similar concepts are applied in a different context.
Ultimately, both approaches aim to create more engaging and personalized experiences, which is why I find the parallels so interesting. The flexibility of Unica’s approach is key to this personalized delivery.
These recommendations are then displayed to the customer. The entire process is dynamic, adapting in real-time to each customer’s unique profile and behavior.
Implementing Dynamic Content Strategies
Crafting effective dynamic content strategies within Unica Journey requires a blend of technical proficiency and a deep understanding of your audience. Success hinges on leveraging the platform’s capabilities to deliver personalized experiences that resonate with individual customer needs and preferences, ultimately driving engagement and conversions. This involves careful planning, meticulous execution, and continuous optimization based on performance data.
Effective dynamic content strategies within Unica Journey are built upon a foundation of high-quality data and precise segmentation. Without accurate and up-to-date customer information, personalized content delivery becomes a shot in the dark. Similarly, poorly defined segments lead to irrelevant messaging, diminishing the impact of your campaigns. Therefore, a robust data management strategy and a well-defined segmentation approach are paramount.
Data Quality and Segmentation for Personalized Content Delivery
Data quality is the cornerstone of personalized content delivery. Inaccurate or incomplete data leads to irrelevant messaging, frustrating customers and undermining campaign effectiveness. This includes ensuring data accuracy, completeness, and consistency across all sources. For example, ensuring email addresses are valid and up-to-date is crucial for successful email campaigns. Similarly, ensuring accurate customer demographics allows for targeted messaging based on age, location, or purchase history.
Robust data governance and cleansing processes are essential to maintaining high data quality. Effective segmentation allows you to group customers with similar characteristics and behaviors, enabling the delivery of highly relevant content. For instance, segmenting customers based on their past purchases allows you to offer personalized product recommendations, increasing the likelihood of conversion. Advanced segmentation techniques, such as predictive modeling, can further enhance personalization by identifying customers likely to respond positively to specific offers or messages.
Challenges of Managing and Updating Dynamic Content Across Multiple Channels
Managing and updating dynamic content across multiple channels presents significant challenges. Maintaining consistency of messaging and brand identity across different platforms (email, web, mobile, etc.) requires careful coordination and a centralized content management system. This often involves integrating Unica Journey with other marketing technologies and establishing clear workflows for content creation, approval, and deployment. Another key challenge lies in ensuring the timely update of content, especially when dealing with rapidly changing market conditions or promotional offers.
Automated workflows and robust version control systems are essential to streamline the update process and minimize the risk of errors. Furthermore, testing and quality assurance across all channels are crucial to ensure the seamless delivery of dynamic content and prevent any negative user experiences.
Step-by-Step Guide for Implementing a Dynamic Content Campaign
Implementing a dynamic content campaign using Unica Journey involves a structured approach.
- Define Objectives and KPIs: Clearly define the goals of your campaign, such as increasing website traffic, boosting sales conversions, or enhancing brand awareness. Establish key performance indicators (KPIs) to measure the success of your campaign, such as click-through rates, conversion rates, and return on investment (ROI).
- Data Preparation and Segmentation: Ensure your customer data is accurate, complete, and up-to-date. Segment your audience based on relevant criteria, such as demographics, purchase history, and engagement behavior. This step is crucial for delivering personalized content that resonates with each segment.
- Content Creation and Personalization: Create compelling content tailored to each segment. Utilize Unica Journey’s dynamic content capabilities to personalize messaging, offers, and calls to action based on individual customer profiles. This could involve using variables to insert personalized names or product recommendations within the content.
- Journey Design and Workflow Configuration: Design your customer journey within Unica Journey, mapping out the various touchpoints and interactions. Configure the workflow to deliver the appropriate dynamic content to each segment based on their behavior and profile. This involves setting up decision points and engagement splits to direct customers down different paths within the journey.
- Testing and Optimization: Thoroughly test your campaign across different channels and devices to ensure seamless delivery and optimal performance. Monitor KPIs and analyze campaign performance to identify areas for improvement. Iteratively refine your strategy based on data-driven insights.
Measuring the Effectiveness of Dynamic Content
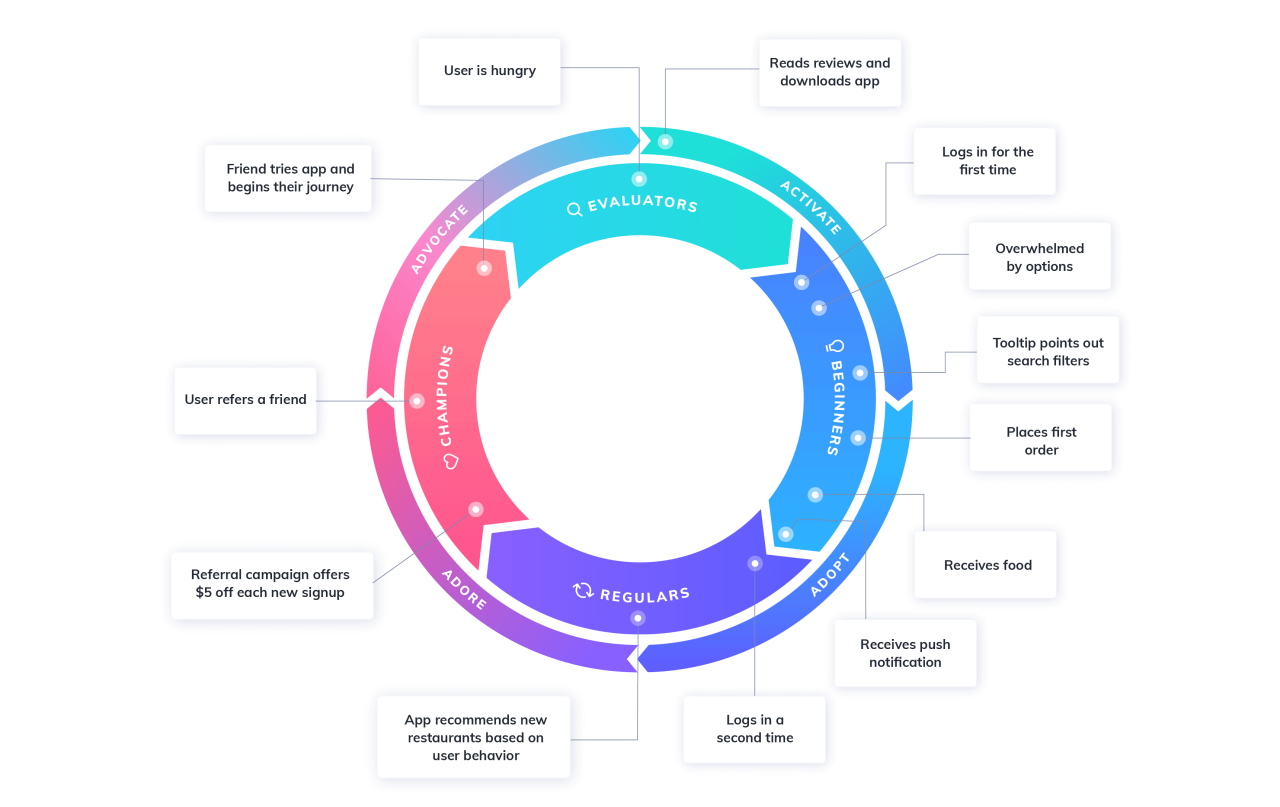
So, you’ve implemented dynamic content in your Unica Journey campaigns – fantastic! But how do you know if it’s actually working? Measuring the effectiveness is crucial to optimizing your strategy and maximizing ROI. This isn’t just about looking at raw numbers; it’s about understanding how your personalized content resonates with your audience and drives desired actions.
Understanding the impact of your dynamic content requires a robust measurement strategy. This involves selecting the right Key Performance Indicators (KPIs), implementing effective tracking mechanisms, and utilizing appropriate reporting and analytics tools. By carefully analyzing the data, you can gain valuable insights into what’s working, what’s not, and how to refine your approach for even better results.
Key Performance Indicators (KPIs) for Dynamic Content
Choosing the right KPIs is paramount. Focusing on the wrong metrics can lead to misinterpretations and wasted effort. The best KPIs will directly reflect your campaign goals. For example, if your goal is increased conversions, then conversion rate will be a key metric. If your goal is brand awareness, then metrics like engagement time and social media shares might be more relevant.
| Metric | Definition | Target Value | Actual Value |
|---|---|---|---|
| Conversion Rate | Percentage of recipients who completed a desired action (e.g., purchase, signup). | 15% | 12% |
| Click-Through Rate (CTR) | Percentage of recipients who clicked on a link in the email. | 20% | 25% |
| Open Rate | Percentage of recipients who opened the email. | 30% | 35% |
| Engagement Time | Average time spent interacting with the personalized content. | 60 seconds | 75 seconds |
Tracking User Engagement with Personalized Content
Tracking user engagement goes beyond simply monitoring clicks and opens. It involves understanding how users interact with the specific elements of your personalized content. This might include tracking time spent on specific pages, scroll depth, video views, and form completions. This granular level of data provides a richer understanding of user behavior and helps identify areas for improvement.
Implementing robust tracking requires careful integration of analytics tools within your Unica Journey campaigns. This often involves using tracking pixels, custom parameters in your links, and leveraging Unica Journey’s built-in reporting capabilities. For example, by tagging different sections of your email with unique identifiers, you can track which elements are most engaging and which ones need refinement.
Reporting and Analytics Tools
Several reporting and analytics tools seamlessly integrate with Unica Journey, providing comprehensive insights into your dynamic content campaigns. These tools offer advanced features such as real-time dashboards, custom reports, and data visualization capabilities. The choice of tool depends on your specific needs and existing infrastructure.
For instance, IBM’s own analytics platforms offer robust integration with Unica Journey, allowing for a holistic view of campaign performance. Other popular options include Google Analytics, which can be integrated via appropriate tracking mechanisms, providing detailed website traffic data linked to your email campaigns. The key is to select a tool that provides the level of granularity and visualization needed to effectively analyze your data.
Advanced Techniques and Considerations
Taking your Unica Journey dynamic content strategies to the next level requires exploring advanced techniques and carefully considering potential challenges. This involves leveraging powerful tools like machine learning, scaling personalization efforts, and proactively addressing security and error handling.
Successfully implementing advanced personalization requires a strategic approach encompassing technological capabilities, data management, and a robust error-handling strategy. Let’s delve into the key aspects.
Machine Learning for Content Personalization
Integrating machine learning (ML) into your Unica Journey workflows can significantly enhance personalization. ML algorithms can analyze vast amounts of customer data to predict preferences and behaviors, allowing for highly targeted content delivery. For instance, a model trained on past engagement data could predict which customers are most likely to respond positively to a specific offer, enabling you to optimize campaign targeting and resource allocation.
This approach moves beyond simple rule-based personalization, offering a more nuanced and effective approach. The implementation often involves integrating ML models (trained externally or using Unica’s built-in capabilities, if available) into the decisioning process within the Journey. The model’s output (e.g., a probability score) then informs the selection of personalized content.
Implementing Personalization at Scale
Scaling personalization requires a robust infrastructure and well-defined processes. This includes ensuring your data architecture can handle the volume of data required for effective personalization, optimizing your Unica Journey workflows for performance, and establishing clear governance around data usage. A phased rollout approach, starting with a smaller segment of customers before expanding, is often advisable. This allows for iterative testing and refinement of the personalization strategy, minimizing disruption and maximizing effectiveness.
Consider using A/B testing to compare the performance of different personalization strategies before implementing them across the entire customer base.
Security and Privacy Considerations
Handling personalized data necessitates strict adherence to security and privacy best practices. This includes employing robust data encryption methods both in transit and at rest, implementing access controls to restrict data access to authorized personnel only, and ensuring compliance with relevant data privacy regulations (e.g., GDPR, CCPA). Regular security audits and penetration testing should be conducted to identify and address potential vulnerabilities.
Transparency with customers regarding data collection and usage practices is crucial for building trust and maintaining compliance. Consider implementing a consent management platform to effectively manage customer preferences and ensure compliance with data privacy regulations.
Handling Unexpected Scenarios and Errors
Robust error handling is crucial for a smooth user experience. This involves implementing mechanisms to detect and manage errors during content delivery, such as gracefully handling situations where personalized content is unavailable or there are issues with data retrieval. Implementing fallback mechanisms (e.g., default content) ensures that users always receive some content, preventing a negative user experience. Comprehensive logging and monitoring of the dynamic content delivery process allows for timely identification and resolution of issues.
Regular testing and quality assurance processes are essential to proactively identify and address potential problems before they impact customers. For example, implementing exception handling within your Unica Journey workflows to catch and log any errors encountered during content personalization and then providing a default message to the user, rather than displaying a generic error message, significantly improves the user experience.
Case Studies and Examples
Dynamic content in Unica Journey isn’t just a theoretical concept; it’s a powerful tool driving real-world results for businesses across various sectors. Let’s delve into some compelling case studies and practical examples to illustrate its effectiveness. We’ll examine how different companies leveraged Unica Journey’s capabilities to enhance customer engagement and achieve measurable improvements.
This section will showcase specific examples of successful dynamic content implementation, highlighting the strategies employed, the outcomes achieved, and the lessons learned. We’ll also explore diverse types of dynamic content, from personalized emails to targeted website banners, demonstrating the versatility of Unica Journey in creating engaging customer experiences.
A Retail Giant’s Personalized Email Campaign
A major online retailer utilized Unica Journey to personalize email marketing campaigns based on customer purchase history and browsing behavior. They segmented their audience into groups based on past purchases (e.g., clothing, electronics, home goods) and tailored email content accordingly. For example, customers who frequently purchased clothing received emails featuring new arrivals and style recommendations, while electronics buyers saw promotions on related products and tech gadgets.
This highly targeted approach resulted in a 25% increase in click-through rates and a 15% boost in conversion rates compared to their previous generic email campaigns. The key lesson learned was the importance of granular segmentation and the power of hyper-relevant messaging.
Dynamic Website Banners for Increased Engagement
An insurance company implemented dynamic website banners using Unica Journey. These banners displayed personalized messages based on the visitor’s demographics and browsing history. For instance, a young professional visiting the site might see a banner promoting travel insurance, while an older individual might see a banner highlighting retirement planning products. The company tracked banner performance and found a significant increase in click-through rates and lead generation.
This example demonstrates the ability of Unica Journey to deliver contextually relevant messaging directly on a website, maximizing engagement and conversion opportunities.
Push Notifications for Timely Product Updates
A software company leveraged Unica Journey to send targeted push notifications to its mobile app users. These notifications provided timely updates about new features, software updates, and relevant articles based on user activity within the app. For users who frequently used a specific feature, the notifications highlighted new functionalities related to that feature. This strategy led to increased app engagement, higher user retention rates, and improved customer satisfaction.
The success here highlights the power of real-time, personalized communication.
Successful Dynamic Content Strategies Across Industries
The examples above only scratch the surface of what’s possible with Unica Journey. Many successful strategies exist across various industries. Here are a few key approaches:
- Personalized Product Recommendations: E-commerce companies use purchase history and browsing data to suggest relevant products to individual customers.
- Targeted Promotional Offers: Businesses tailor promotions based on customer segments, demographics, and purchase behavior to maximize impact.
- Location-Based Messaging: Companies use location data to deliver relevant messages and offers to customers in specific geographic areas.
- Lifecycle-Based Content: Businesses tailor communication to match customers’ stage in the customer journey (e.g., welcome emails, onboarding sequences, retention campaigns).
- A/B Testing and Optimization: Continuously testing different versions of dynamic content to identify the most effective approaches.
Conclusive Thoughts
Mastering dynamic content within Unica Journey is about more than just technology; it’s about understanding your audience and crafting compelling experiences. By strategically utilizing decisioning, engagement splits, and robust data analysis, you can transform your interactions with users, boosting engagement and driving measurable results. Remember, data quality and a well-defined strategy are key to success. This journey through Unica Journey’s dynamic content capabilities equips you with the knowledge and insights to create truly personalized and impactful campaigns.
FAQ Insights
What are the limitations of Unica Journey’s dynamic content capabilities?
While powerful, Unica Journey’s capabilities are limited by the data available and the complexity of the business rules you implement. Performance can also be impacted by the volume of data processed and the number of personalization rules in use.
How does Unica Journey handle data privacy and security?
Unica Journey incorporates security measures to protect user data, adhering to relevant privacy regulations. Specific security features and compliance certifications should be verified with Unica’s documentation and support team.
Can Unica Journey integrate with other marketing platforms?
Yes, Unica Journey offers integration capabilities with various other marketing platforms and data sources. The specific integrations available will depend on your version and configuration.
What type of training is available for Unica Journey’s dynamic content features?
Unica typically provides training resources, including documentation, tutorials, and potentially formal training courses, depending on your licensing agreement. Check with your Unica provider for details.