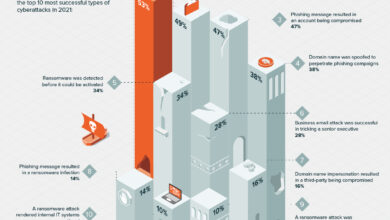
CISA Guidance Strong Data Security, Weak Web Access
Cisa guidance strengthens data security neglects web access security – CISA Guidance: Strong Data Security, Weak Web Access – that’s the unsettling truth I uncovered while digging into the latest cybersecurity recommendations. While the guidance rightfully emphasizes robust data protection measures, it surprisingly overlooks critical aspects of web application security. This imbalance leaves organizations vulnerable to a range of attacks, even with seemingly strong data safeguards in place.
It’s like fortifying your castle walls but leaving the front gate wide open! This post explores this critical gap and suggests how to bridge it.
The CISA guidance offers excellent advice on securing data itself, providing detailed steps for encryption, access control, and data loss prevention. However, the document falls short when it comes to securing the very pathways that attackers use to get to that data: web applications. This lack of attention to web access security – encompassing everything from authentication flaws to insecure coding practices – creates a significant vulnerability that undermines the effectiveness of all the other security measures.
CISA Guidance Focus
The Cybersecurity and Infrastructure Security Agency (CISA) provides crucial guidance for organizations seeking to bolster their cybersecurity posture. While the agency’s recent advisories have rightly highlighted the need for improved web access security, a significant portion of their recommendations centers on strengthening data security—a fundamental aspect of any robust cybersecurity strategy. This focus on data protection reflects the understanding that data breaches, often originating from vulnerabilities elsewhere, ultimately inflict the most damage when sensitive information is compromised.
Data Security Measures Emphasized by CISA
CISA’s guidance emphasizes a multi-layered approach to data security, encompassing various controls and best practices. This holistic strategy aims to protect data at rest, in transit, and in use. The agency strongly advocates for a proactive and preventative approach, prioritizing risk management and continuous monitoring. This contrasts with a reactive approach that only addresses issues after a breach has occurred.
CISA’s focus on data security is great, but it feels like they’re overlooking a crucial aspect: web application security. Strengthening backend data protection is only half the battle; secure front-end access is equally vital. This is why exploring modern development approaches like those discussed in this article on domino app dev the low code and pro code future is so important.
Ultimately, a robust security posture requires a holistic approach, addressing both data and access vulnerabilities.
Best Practices for Data Protection
CISA highlights several best practices for effective data protection. These include implementing robust access controls, regularly backing up data, encrypting sensitive information both at rest and in transit, and maintaining detailed audit logs. Furthermore, CISA stresses the importance of employee training and awareness programs to reduce the risk of human error, a major factor in many data breaches.
For example, phishing simulations and regular security awareness training sessions help employees identify and avoid malicious emails or websites.
Effectiveness of Data Security Measures in Mitigating Breaches
The effectiveness of these measures is demonstrably linked to a reduction in the severity and impact of data breaches. Implementing strong access controls, for instance, limits unauthorized access to sensitive data, minimizing the potential damage from a successful attack. Regular data backups enable swift recovery in the event of a ransomware attack or other data loss incident. Encryption ensures that even if data is stolen, it remains unreadable without the decryption key.
Finally, comprehensive audit logs provide valuable insights into system activity, facilitating incident response and investigation. The combined effect of these measures significantly strengthens an organization’s resilience against data breaches.
Table of Data Security Measures
| Measure | Description | Implementation Steps | Potential Benefits |
|---|---|---|---|
| Access Control | Restricting access to data based on the principle of least privilege. | Implement role-based access control (RBAC), regularly review and update access permissions, use multi-factor authentication (MFA). | Reduces the risk of unauthorized access, limits the impact of compromised credentials. |
| Data Encryption | Protecting data at rest and in transit using encryption algorithms. | Encrypt databases, use HTTPS for web traffic, encrypt sensitive files before storage or transmission. | Protects data confidentiality even if a breach occurs, ensures compliance with data privacy regulations. |
| Data Backup and Recovery | Regularly backing up data and testing the recovery process. | Implement a robust backup strategy (3-2-1 rule), regularly test backups, ensure offsite storage. | Enables quick data recovery in case of data loss, minimizes downtime and business disruption. |
| Security Awareness Training | Educating employees about cybersecurity threats and best practices. | Conduct regular training sessions, use phishing simulations, promote a security-conscious culture. | Reduces human error, improves employee awareness of potential threats, strengthens overall security posture. |
| Regular Security Audits | Periodically assessing the security posture of systems and applications. | Conduct vulnerability scans, penetration testing, security audits, review logs regularly. | Identifies vulnerabilities and weaknesses, allows for proactive remediation, improves overall security posture. |
CISA Guidance Shortcomings
While CISA provides valuable guidance on bolstering cybersecurity, its current recommendations exhibit a noticeable gap in addressing the crucial area of web access security. This oversight leaves organizations vulnerable to a range of sophisticated attacks, despite potentially robust data security measures elsewhere. A more comprehensive approach is needed to ensure a holistic security posture.
Insufficient Detail on Web Application Firewalls (WAFs)
The guidance offers general advice on securing web applications but lacks the granular detail needed for effective implementation. For example, the document should delve deeper into the selection, configuration, and ongoing maintenance of Web Application Firewalls (WAFs). Proper WAF configuration is critical for mitigating common web application vulnerabilities like SQL injection and cross-site scripting (XSS). Without clear guidance on selecting the right WAF for an organization’s specific needs and ensuring its rules are regularly updated, organizations risk leaving critical vulnerabilities exposed.
The current level of detail on WAFs is insufficient to ensure their effective deployment and management.
Inadequate Coverage of API Security, Cisa guidance strengthens data security neglects web access security
The increasing reliance on Application Programming Interfaces (APIs) is largely ignored in the current CISA guidance. APIs represent a significant attack surface, and their insecure configuration can lead to data breaches and other serious consequences. The guidance needs to include specific recommendations on securing APIs, including authentication and authorization mechanisms, input validation, and rate limiting. Failure to address API security leaves organizations vulnerable to attacks that exploit weaknesses in API design and implementation, such as unauthorized access to sensitive data or manipulation of business logic.
A real-world example would be a compromised API allowing attackers to modify pricing or customer information.
Limited Discussion of Secure Development Practices for Web Applications
The guidance lacks sufficient emphasis on integrating security into the software development lifecycle (SDLC) for web applications. Secure coding practices, such as input validation and output encoding, are essential for preventing vulnerabilities from entering production systems. The guidance should provide more detailed information on implementing secure coding practices, including the use of static and dynamic application security testing (SAST/DAST) tools.
The absence of this crucial information leaves developers without the necessary knowledge to build secure web applications from the ground up, increasing the likelihood of vulnerabilities. This is particularly relevant given the rise of DevOps and agile development methodologies, which often prioritize speed over security if security best practices are not deeply embedded in the process.
Consequences of Neglecting Web Access Security
Neglecting web access security can lead to a variety of serious consequences, including data breaches, financial losses, reputational damage, and legal liabilities. For example, a successful cross-site scripting (XSS) attack could allow attackers to steal user credentials or inject malicious code into a website, potentially compromising the entire system. Similarly, a SQL injection attack could grant attackers unauthorized access to sensitive data stored in a database.
These attacks can result in significant financial losses, as seen in numerous high-profile data breaches that have cost companies millions of dollars in remediation and legal fees. The lack of sufficient guidance on these issues leaves organizations ill-equipped to handle such events.
Disparity in Guidance Detail: Data Security vs. Web Access Security
A significant disparity exists between the level of detail provided on data security and web access security within the guidance document. Data security receives extensive coverage, including detailed recommendations on encryption, access control, and data loss prevention (DLP). However, web access security receives comparatively less attention, resulting in an unbalanced approach that fails to address the equally critical aspects of securing the organization’s online presence.
This imbalance leaves organizations vulnerable to attacks targeting their web applications and APIs, which can be equally damaging, if not more so, than data breaches stemming from internal vulnerabilities. A more balanced approach is necessary to ensure a comprehensive security posture.
Impact of the Imbalance
CISA’s guidance rightly emphasizes robust data security, but its relative neglect of web access security creates a significant vulnerability. A strong data fortress is useless if the gates are left unlocked. This imbalance leaves organizations exposed to a range of threats, even when internal data is meticulously protected. The following scenarios illustrate this critical weakness.
Real-World Scenarios Illustrating Insufficient Web Access Security
The lack of comprehensive web access security measures can lead to devastating consequences, regardless of the strength of other security protocols. Even with encrypted data and robust internal controls, weak web access can be the entry point for malicious actors.
| Scenario | Web Access Vulnerability | Data Breach Potential | Mitigation Strategy |
|---|---|---|---|
| Phishing Attack Targeting Employees | Lack of robust anti-phishing training and email filtering; weak password policies. | Compromised employee credentials could grant access to internal systems and sensitive data, leading to data exfiltration or ransomware attacks. | Implement comprehensive security awareness training, enforce strong password policies (including multi-factor authentication), and deploy advanced email filtering systems. Regularly update and patch systems. |
| Exploitation of Unpatched Web Application | Outdated or vulnerable web applications with known security flaws (e.g., SQL injection vulnerabilities). | Attackers could exploit these vulnerabilities to gain unauthorized access to databases containing sensitive customer information, financial records, or intellectual property. | Regularly scan web applications for vulnerabilities, promptly apply security patches, and implement robust input validation and sanitization techniques. Conduct penetration testing to identify and address weaknesses. |
| Compromised Third-Party Vendor Access | Insufficient vetting of third-party vendors and inadequate access controls to systems they manage. | A compromised vendor’s access credentials could allow attackers to infiltrate the organization’s network, potentially leading to a widespread data breach. | Thoroughly vet all third-party vendors, implement strong access control mechanisms (e.g., least privilege access), and regularly monitor their activities. Use secure communication channels for data exchange with vendors. |
The impact on an organization’s operations and reputation can be severe. A data breach, even one stemming from a seemingly minor web access vulnerability, can result in significant financial losses due to fines, legal fees, and remediation costs. It can also damage customer trust, leading to loss of business and reputational harm. In some cases, a breach can even result in criminal prosecution.
The cost of inaction far outweighs the cost of implementing robust web access security measures.
Recommended Enhancements to CISA Guidance

CISA’s existing guidance on data security provides a valuable foundation, but its relative neglect of web access security represents a significant gap. Strengthening this area is crucial given the prevalence of web applications as attack vectors and the increasing sophistication of cyber threats targeting them. This section proposes specific enhancements to comprehensively address web access security vulnerabilities and best practices.
These recommendations aim to provide a more holistic and effective approach to securing organizations’ digital assets.
The current guidance lacks the granular detail needed to effectively mitigate the wide range of web application vulnerabilities. Many organizations struggle to implement robust security measures due to a lack of clear, actionable advice. Adding specific recommendations on common vulnerabilities, secure coding practices, and robust authentication and authorization mechanisms will significantly improve the guidance’s practical value.
Addressing Common Web Application Vulnerabilities
The CISA guidance should include a dedicated section detailing common web application vulnerabilities and their mitigation strategies. This section should move beyond general advice and provide specific, actionable steps. For example, it should cover the OWASP Top 10 vulnerabilities, explaining each vulnerability in detail and offering practical mitigation techniques, including code examples where appropriate. This detailed approach will empower organizations to proactively address these risks.
This section should include clear explanations of how to implement secure coding practices to prevent vulnerabilities from arising in the first place.
Secure Web Access Controls
Effective web access controls are fundamental to securing web applications. The CISA guidance should expand on the current recommendations by providing detailed examples of best practices for implementing access controls. This should include guidance on:
- Implementing robust input validation to prevent injection attacks (SQL injection, cross-site scripting).
- Using strong password policies and multi-factor authentication (MFA) to enhance user authentication.
- Leveraging least privilege principles to restrict user access to only necessary resources.
- Regularly reviewing and updating access control lists (ACLs) to ensure they remain accurate and effective.
- Implementing role-based access control (RBAC) to manage user permissions effectively.
The importance of these controls cannot be overstated. A breach stemming from weak access controls can have devastating consequences, including data loss, financial damage, and reputational harm. The guidance should emphasize the importance of regular audits and reviews to ensure the continued effectiveness of these controls.
Authentication and Authorization Best Practices
The guidance should provide a comprehensive overview of modern authentication and authorization mechanisms, moving beyond simple password-based systems. This should include:
- Detailed explanations of various MFA methods, including their strengths and weaknesses, and recommendations for choosing appropriate methods based on risk assessment.
- Guidance on implementing OAuth 2.0 and OpenID Connect (OIDC) for secure third-party access.
- Best practices for securing API access, including API keys, JWTs, and other authentication mechanisms.
- Recommendations for implementing robust authorization mechanisms, such as attribute-based access control (ABAC).
The emphasis should be on implementing layered security, combining multiple authentication and authorization methods to create a robust defense against unauthorized access. The guidance should also include clear instructions on how to integrate these mechanisms into existing web applications.
Comparison with Other Security Frameworks
CISA’s guidance on data security, while valuable, presents a somewhat skewed focus compared to other established frameworks. This section analyzes the similarities and differences between CISA’s approach and that of NIST, highlighting strengths and weaknesses in addressing web application security, a critical area where CISA’s guidance currently falls short. A comparative analysis allows for a more holistic understanding of best practices and potential areas for improvement.
The primary difference lies in the breadth of coverage. While CISA provides crucial guidance tailored to specific US government agencies and critical infrastructure, NIST offers a more comprehensive and broadly applicable framework, encompassing a wider range of security controls and best practices. This difference stems from their distinct mandates and target audiences. NIST’s Cybersecurity Framework (CSF), for example, is designed to be adaptable across various sectors and organizations, whereas CISA’s guidance is often more prescriptive and targeted towards specific threats and vulnerabilities relevant to the US government context.
NIST Cybersecurity Framework (CSF) Compared to CISA Guidance
Both CISA and NIST aim to improve cybersecurity posture, but their approaches differ significantly regarding web application security. NIST CSF adopts a risk-based approach, emphasizing the identification, assessment, and mitigation of risks across all aspects of an organization’s IT infrastructure, including web applications. It provides a flexible framework allowing organizations to tailor their security controls based on their specific risk profiles and resources.
CISA’s latest guidance is great for beefing up data security, but honestly, it feels like they’re overlooking a huge piece of the puzzle: web access security. The focus on data is crucial, but we need a holistic approach. That’s where solutions like those discussed in this article on bitglass and the rise of cloud security posture management become essential, addressing the broader security landscape.
Ultimately, strengthening data security without securing web access leaves organizations vulnerable, highlighting a critical gap in current cybersecurity strategies.
In contrast, CISA’s guidance, while addressing data security comprehensively, often lacks the detailed, prescriptive guidance on securing web applications that is readily available in the NIST CSF.
Strengths and Weaknesses of Each Framework in Relation to Web Application Security
NIST CSF’s strength lies in its adaptability and comprehensive coverage of web application security risks. Its framework allows organizations to implement controls addressing vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). However, its flexibility can also be a weakness, as it requires a deeper understanding of security best practices and risk management to effectively implement and tailor the framework.
CISA’s guidance, on the other hand, offers a more targeted approach, beneficial for organizations with limited resources or expertise. However, its relative lack of detail on web application security leaves organizations to fill the gaps with additional research and potentially less consistent implementation.
| Aspect | CISA Guidance | NIST Cybersecurity Framework (CSF) | Comparison |
|---|---|---|---|
| Focus | Data security, primarily for US government and critical infrastructure | Broad cybersecurity framework applicable across sectors | CISA is more targeted; NIST is more comprehensive. |
| Web Application Security Coverage | Limited; often lacks detailed guidance | Comprehensive; addresses various web application vulnerabilities | NIST provides significantly more detailed guidance. |
| Approach | Prescriptive, often focusing on compliance | Risk-based, allowing for customization | CISA is more directive; NIST emphasizes flexibility and risk management. |
| Implementation | May require supplemental guidance for web application security | Requires a strong understanding of security principles and risk assessment | CISA is easier to implement initially, but NIST offers better long-term security. |
Illustrative Example: A Secure Web Application Architecture: Cisa Guidance Strengthens Data Security Neglects Web Access Security
This section details a secure web application architecture designed to mitigate the shortcomings identified in the CISA guidance, particularly its relative neglect of web access security compared to its emphasis on data security. This architecture prioritizes a layered security approach, implementing robust controls at each stage of the application lifecycle and user interaction.The architecture focuses on a defense-in-depth strategy, utilizing multiple layers of security controls to ensure that even if one layer is compromised, others remain in place to prevent successful attacks.
This approach addresses the imbalance in the CISA guidance by proactively securing the web access layer, preventing many attacks before they reach the data layer.
Network Layer Security
This layer focuses on securing the network infrastructure connecting the web application to the internet and internal systems. It involves implementing a robust firewall, intrusion detection/prevention systems (IDS/IPS), and a web application firewall (WAF). The WAF acts as the first line of defense, filtering malicious traffic and preventing common web attacks like SQL injection and cross-site scripting (XSS).
The IDS/IPS monitors network traffic for suspicious activity, alerting administrators to potential threats and automatically blocking malicious connections. The firewall controls network access, restricting inbound and outbound connections based on pre-defined rules, only allowing authorized traffic to reach the application servers. Regular security audits and penetration testing of this layer are crucial to maintain its effectiveness.
Application Layer Security
The application layer focuses on securing the application itself, including its code, configuration, and runtime environment. This includes implementing secure coding practices to prevent vulnerabilities, such as input validation and output encoding to prevent injection attacks. Regular security assessments and penetration testing of the application code are vital to identify and remediate vulnerabilities. The application should also employ robust authentication and authorization mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC), to ensure only authorized users can access sensitive data and functionality.
Regular security updates and patching are also critical to address known vulnerabilities.
Data Layer Security
This layer focuses on securing the data stored and processed by the web application. This includes employing data encryption both in transit (using HTTPS) and at rest (using database encryption). Data loss prevention (DLP) tools can be used to monitor and prevent sensitive data from leaving the organization’s control. Access control mechanisms, such as RBAC, ensure that only authorized users and processes can access sensitive data.
Regular data backups and disaster recovery planning are also essential to protect against data loss. Data masking and anonymization techniques can be used to protect sensitive data during development and testing.
Visual Representation of the Secure Architecture
Imagine a layered pyramid. At the base is the Network Layer, represented by a strong foundation, incorporating the firewall, WAF, and IDS/IPS, acting as a barrier against external threats. Above this sits the Application Layer, a sturdy structure built with secure coding practices, authentication mechanisms (MFA and RBAC), and regular security updates. At the apex is the Data Layer, a secure vault protected by encryption (both in transit and at rest), access controls, and data loss prevention measures.
Each layer interacts with the others, with data flowing upwards through the application and outwards to the user, while security controls operate at each level, providing a robust and layered defense against attacks. The entire pyramid is continuously monitored and maintained through regular security assessments, penetration testing, and vulnerability management. This visual representation emphasizes the interconnectedness and interdependence of each security layer, highlighting the importance of a holistic approach to web application security.
Final Review
In short, while CISA’s emphasis on data security is commendable, its neglect of web access security is a serious oversight. Organizations need a holistic approach, addressing both data protection and web application vulnerabilities to truly secure their systems. Ignoring the web access component is like building a house with a solid foundation but a flimsy roof – a storm could easily blow it all away.
By strengthening web access security and integrating it with strong data protection measures, organizations can create a truly resilient security posture. Let’s work together to close this dangerous gap.
Answers to Common Questions
What specific web application vulnerabilities are often overlooked in the CISA guidance?
Common vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms are often not adequately addressed. The guidance needs more detail on secure coding practices and penetration testing.
How can I practically implement better web access security based on the CISA guidance’s strengths?
Leverage the CISA guidance’s strong points on access control and apply those principles to web applications. Implement strong authentication, authorization, and input validation techniques. Regularly update software and conduct penetration testing to identify and fix vulnerabilities.
Are there any other frameworks besides CISA that offer better guidance on web access security?
Yes, NIST (National Institute of Standards and Technology) offers comprehensive frameworks that address web application security in more detail. OWASP (Open Web Application Security Project) is another valuable resource for best practices and vulnerability information.