CISOs Laxity Fuels Cyberattacks
Cisos laxity towards cybersecurity is leading to more cyber attacks – CISOs’ laxity towards cybersecurity is leading to more cyber attacks. We’re seeing a disturbing trend: insufficient security measures, driven by CISO inaction or oversight, are leaving organizations vulnerable to increasingly sophisticated attacks. This isn’t just about technical failures; it’s about leadership failures, organizational cultures that prioritize speed over security, and a general lack of proactive cybersecurity strategies. The consequences are devastating – financial losses, reputational damage, and the erosion of customer trust.
This post delves into the root causes of this problem, explores real-world examples, and offers actionable steps to improve cybersecurity practices.
From budget constraints and a lack of skilled personnel to pressure from upper management, several factors contribute to a CISO’s inability to implement robust security measures. Different organizational structures and industry sectors also exhibit varying degrees of preparedness. We’ll examine how these factors interact, ultimately leading to the increased frequency and severity of cyberattacks. Furthermore, we’ll explore the role of external factors, such as the ever-evolving threat landscape and regulatory compliance demands, in shaping a CISO’s response (or lack thereof) to the escalating cyber threat.
Defining CISOs’ Laxity
The increasing frequency and severity of cyberattacks highlight a concerning trend: laxity among Chief Information Security Officers (CISOs) in implementing and enforcing robust cybersecurity practices. This isn’t necessarily malicious negligence, but rather a complex interplay of factors leading to insufficient security measures, ultimately leaving organizations vulnerable. Understanding the various forms this laxity takes is crucial to addressing the problem effectively.
CISO laxity manifests in several ways, from inadequate resource allocation and insufficient staff training to a failure to prioritize critical security updates and a lack of proactive threat hunting. It’s not always a deliberate act of omission; sometimes it’s a consequence of unrealistic expectations, limited budgets, or a lack of executive support. However, the outcome remains the same: increased organizational risk.
Scenarios Demonstrating Insufficient Cybersecurity Measures
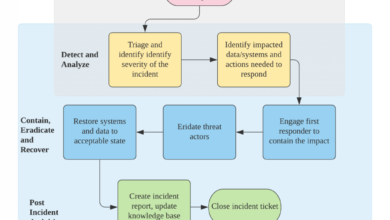
Numerous scenarios illustrate how insufficient cybersecurity measures, often stemming from CISO inaction or oversight, can expose organizations to significant threats. For instance, a CISO might fail to implement multi-factor authentication (MFA) across all systems, leaving sensitive data vulnerable to phishing attacks. Another common scenario involves neglecting regular security audits and penetration testing, leaving critical vulnerabilities undetected. Delayed patching of known software vulnerabilities, a lack of robust incident response planning, and insufficient employee security awareness training are further examples of the consequences of CISO laxity.
These failures create significant security gaps that malicious actors readily exploit. The resulting breaches can lead to data loss, financial losses, reputational damage, and legal repercussions.
Organizational Cultures that Encourage Laxity
Certain organizational cultures inadvertently foster or tolerate CISO laxity. A culture that prioritizes speed and efficiency over security can lead to shortcuts being taken, while a lack of accountability and a failure to address security incidents promptly can normalize risky behavior. Similarly, organizations with insufficient investment in cybersecurity resources or a lack of executive-level commitment to security often find themselves struggling to implement adequate security measures, even with a well-intentioned CISO.
A siloed approach to security, where different departments operate independently without coordinating their efforts, can also contribute to laxity. Finally, a culture of fear or blame, where employees are hesitant to report security incidents, can prevent the timely identification and mitigation of threats.
Types of CISO Laxity and Their Consequences
| Laxity Type | Description | Impact | Mitigation Strategy |
|---|---|---|---|
| Inadequate Resource Allocation | Insufficient budget, staffing, or tools for effective cybersecurity. | Increased vulnerability to attacks, slow incident response. | Develop a comprehensive cybersecurity budget, prioritize hiring skilled professionals, invest in appropriate security tools. |
| Lack of Proactive Threat Hunting | Failure to actively search for and identify potential threats before they exploit vulnerabilities. | Delayed detection of attacks, increased damage from breaches. | Implement threat intelligence platforms, conduct regular penetration testing and vulnerability assessments. |
| Delayed Patching | Failure to promptly address known software vulnerabilities. | Exploitation of known vulnerabilities, data breaches. | Establish a robust patch management process, automate patching where possible. |
| Insufficient Employee Training | Lack of security awareness training for employees. | Increased susceptibility to phishing and social engineering attacks. | Provide regular security awareness training, conduct phishing simulations. |
Impact of Laxity on Cyber Attacks

The consequences of a Chief Information Security Officer’s (CISO) laxity in cybersecurity are far-reaching and devastating. A lack of proactive security measures, insufficient employee training, and delayed responses to vulnerabilities can directly contribute to successful cyberattacks, leading to significant financial losses, reputational damage, and legal repercussions. This section explores real-world examples and hypothetical scenarios illustrating the direct link between CISO negligence and the severity of cyberattacks.
Seriously, the rise in cyberattacks is directly linked to CISOs’ complacency. We’re seeing a dangerous lack of proactive security measures, and it’s costing businesses dearly. Building robust internal systems is crucial, and that’s where learning more about domino app dev the low code and pro code future could help. Ultimately, stronger security practices, including smarter app development, are the only way to combat this growing threat of cyberattacks fueled by lax security.
CISO laxity manifests in various ways, from neglecting to implement essential security controls to failing to adequately respond to known vulnerabilities. This inaction creates a breeding ground for cybercriminals, significantly increasing the likelihood and impact of successful attacks. The resulting damage isn’t limited to financial losses; it extends to the erosion of public trust and the potential for long-term business disruption.
Real-World Case Studies Illustrating CISO Laxity and its Consequences
Several high-profile data breaches highlight the catastrophic consequences of CISO negligence. The 2017 Equifax breach, for instance, resulted from the company’s failure to patch a known vulnerability in its Apache Struts framework. This failure, directly attributable to inadequate security oversight, exposed the personal information of over 147 million individuals. The resulting fines, legal battles, and reputational damage cost Equifax billions of dollars.
Similarly, the Target data breach in 2013, which compromised the personal information of millions of customers, stemmed from inadequate security measures and a failure to adequately address vulnerabilities in its network. These breaches demonstrate how a lack of proactive security measures, directly linked to CISO oversight, can lead to devastating consequences.
Financial and Reputational Damage Linked to CISO Negligence
The financial repercussions of cyberattacks stemming from CISO laxity are substantial. Costs include direct losses from stolen data, fines and penalties from regulatory bodies, legal fees associated with lawsuits, and the expense of remediation and recovery efforts. Beyond financial losses, reputational damage can be equally devastating. A successful cyberattack can severely damage a company’s brand image, leading to loss of customer trust, decreased sales, and difficulty attracting investors.
The long-term impact on a company’s ability to operate effectively can be significant, with some organizations never fully recovering from a major data breach directly linked to poor security practices.
Hypothetical Scenario: CISO Inaction Leading to a Major Data Breach
Imagine a mid-sized financial institution where the CISO consistently delays implementing crucial security updates and ignores warnings about vulnerabilities in its legacy systems. Employees lack adequate security awareness training, and phishing simulations are never conducted. A sophisticated phishing campaign targets employees, leading to a successful compromise of a senior employee’s credentials. The attacker gains access to the institution’s internal network, bypassing weak authentication controls.
Because of the lack of robust monitoring and intrusion detection systems, the attacker remains undetected for weeks, exfiltrating sensitive customer data. The eventual discovery of the breach leads to significant financial losses, regulatory fines, and a severe blow to the institution’s reputation, all directly traceable to the CISO’s inaction.
It’s frustrating to see how many cyberattacks stem from CISOs’ lax attitudes towards security. Companies are increasingly reliant on cloud services, making robust security crucial. This is where solutions like those discussed in this article on bitglass and the rise of cloud security posture management become essential. Ultimately, a more proactive approach from CISOs is needed to prevent these avoidable breaches.
Inadequate Security Measures Exacerbating Cyberattack Impact
Inadequate security measures, a direct result of CISO laxity, can exponentially worsen the impact of cyberattacks. For example, a lack of robust data backup and recovery systems can lead to irreplaceable data loss. The absence of incident response plans can prolong the duration of an attack and increase the damage. Furthermore, insufficient employee training and awareness programs can make employees more susceptible to social engineering attacks, increasing the likelihood of a successful breach.
In short, a lack of comprehensive security measures, often stemming from CISO negligence, amplifies the negative consequences of a cyberattack, turning a minor incident into a catastrophic event.
Root Causes of CISO Laxity
The increasing frequency of successful cyberattacks highlights a concerning trend: a lack of proactive cybersecurity measures by many CISOs. This isn’t necessarily due to malice or incompetence, but rather a complex interplay of factors that often leave CISOs feeling overwhelmed and under-resourced. Understanding these root causes is crucial to improving overall cybersecurity posture across organizations.Budgetary constraints, insufficient staffing, and pressure from upper management significantly contribute to a CISO’s inability to fully implement robust security strategies.
These pressures often force prioritization, leading to compromises in long-term security planning in favor of immediate operational needs. This reactive approach, while seemingly efficient in the short term, leaves organizations vulnerable to sophisticated attacks that could have been mitigated with a more proactive approach.
Budgetary Constraints and Resource Allocation
Limited budgets directly impact a CISO’s ability to invest in necessary security tools, technologies, and personnel. The cost of advanced security solutions, including intrusion detection systems, security information and event management (SIEM) tools, and vulnerability scanners, can be substantial. Further complicating matters, the ongoing need for updates, maintenance, and skilled personnel to manage these systems adds to the financial burden.
Organizations prioritizing short-term profits over long-term security investments often leave their CISOs struggling to balance risk and budget, resulting in compromises on security measures. For example, a small business might choose to forgo a comprehensive penetration testing program due to its perceived high cost, despite the potential for significant financial losses from a successful breach.
Lack of Skilled Personnel and Expertise
The cybersecurity industry faces a significant skills shortage. Finding and retaining qualified security professionals is a major challenge for organizations of all sizes. This shortage often forces CISOs to rely on less experienced personnel or outsource security functions, potentially compromising the effectiveness of their security programs. Furthermore, the rapidly evolving threat landscape demands constant upskilling and training, which requires additional investment and time that many organizations are unwilling or unable to provide.
A lack of skilled analysts, for instance, can lead to delayed incident response times, allowing attackers more time to compromise systems and exfiltrate sensitive data.
Organizational Priorities and Risk Tolerance
Organizational priorities and risk tolerance significantly influence CISO decision-making. In some organizations, security might be viewed as a cost center rather than a strategic investment. This perspective often leads to underfunding of security initiatives and a reluctance to adopt proactive security measures. Conversely, organizations with a higher risk tolerance might be more willing to accept some level of risk in exchange for cost savings, potentially leading to a less robust security posture.
For example, a financial institution will naturally have a much lower risk tolerance than a small retail store, leading to vastly different security investment strategies.
Influence of Organizational Size and Industry
The approach to cybersecurity preparedness varies considerably depending on organizational size and industry. Larger organizations with substantial resources often have dedicated security teams and budgets for comprehensive security programs. However, even large organizations can struggle with the complexity of managing security across diverse systems and locations. Smaller organizations, on the other hand, may lack the resources to implement robust security measures, relying instead on basic security controls and outsourced services.
Industry regulations also play a significant role. Organizations in highly regulated industries, such as finance and healthcare, face stricter compliance requirements and often invest more heavily in security to mitigate risks and avoid penalties.
Internal and External Pressures Influencing CISO Decisions, Cisos laxity towards cybersecurity is leading to more cyber attacks
The following factors exert significant pressure on CISOs, shaping their decisions regarding cybersecurity:
- Internal Pressures: Budgetary limitations, lack of executive support, competing priorities, limited staff resources, pressure to meet deadlines, internal political dynamics, lack of clear security strategy, resistance to change.
- External Pressures: Evolving threat landscape, increasing regulatory compliance requirements, pressure from industry peers, public perception and reputational risk, media scrutiny following breaches, competitor actions, insurance requirements.
Improving CISO Cybersecurity Practices

The increasing sophistication and frequency of cyberattacks demand a significant shift in how CISOs approach cybersecurity. Moving beyond reactive measures to a proactive, preventative stance is crucial for organizational survival. This requires a fundamental overhaul of training, culture, policy, and risk assessment methodologies, all spearheaded by a highly competent and empowered CISO.
Enhanced CISO Training Programs
Effective CISO training must go beyond technical skills. Programs should incorporate advanced threat modeling, proactive vulnerability management techniques, and strategies for building resilient systems. A strong emphasis on leadership skills, communication, and the ability to effectively articulate risk to the board of directors is also essential. For example, training could include simulations of real-world cyberattacks, forcing CISOs to make critical decisions under pressure, and honing their crisis management capabilities.
This hands-on approach, combined with theoretical knowledge of emerging threats and best practices, creates well-rounded, proactive security leaders.
Cultivating a Strong Security Culture
The CISO plays a pivotal role in fostering a security-conscious culture. This involves more than just issuing policies; it requires actively engaging employees at all levels. Effective methods include implementing regular security awareness training, using gamification to make learning engaging, and rewarding employees for reporting security vulnerabilities. Open communication channels, where employees feel comfortable reporting incidents without fear of reprisal, are critical.
For instance, a company could establish a “bug bounty” program, incentivizing employees to identify and report security flaws. A strong security culture is not merely a checklist item; it’s a continuous process of education, engagement, and reinforcement.
Establishing Clear Cybersecurity Policies and Procedures
Clear, concise, and regularly updated cybersecurity policies and procedures are non-negotiable. These policies must be easily accessible to all employees, clearly defining acceptable use of company resources, data handling procedures, and incident response protocols. The CISO is responsible for ensuring that these policies are not just created but actively enforced and regularly reviewed. Accountability is key; policies should Artikel clear consequences for non-compliance, and regular audits should assess adherence to these policies.
A well-structured policy framework should incorporate industry best practices and relevant legal and regulatory requirements, such as GDPR or CCPA, depending on the organization’s location and operations.
Developing a Robust Cybersecurity Risk Assessment Framework
A robust risk assessment framework is the cornerstone of proactive cybersecurity. This framework should identify, analyze, and prioritize potential threats and vulnerabilities, taking into account both technical and non-technical factors. The CISO leads this process, working closely with other departments to gather relevant data and assess potential impacts. The framework should include a clear methodology for identifying assets, threats, and vulnerabilities, quantifying the likelihood and impact of potential incidents, and defining mitigation strategies.
Regularly scheduled risk assessments, coupled with ongoing monitoring and updates, are crucial for maintaining a dynamic and relevant security posture. This continuous improvement cycle ensures that the organization remains adaptable to the ever-evolving threat landscape.
The Role of External Factors

The effectiveness of a CISO isn’t solely determined by internal factors; external forces significantly shape their responsibilities and the challenges they face. A constantly evolving threat landscape, stringent regulatory demands, the need for external validation, and a persistent cybersecurity skills gap all contribute to the pressure CISOs experience and, in some cases, their perceived laxity. Understanding these external pressures is crucial to fairly assessing CISO performance and developing effective solutions.The evolving threat landscape and the emergence of sophisticated cyberattacks dramatically impact CISO effectiveness.
New attack vectors, such as AI-powered malware and sophisticated social engineering techniques, require CISOs to constantly adapt their strategies and invest in advanced security solutions. The speed at which these threats emerge often outpaces the ability of organizations to implement adequate defenses, leaving CISOs struggling to keep up and potentially leading to vulnerabilities. For example, the rapid rise of ransomware-as-a-service (RaaS) has created a readily available market for malicious actors, making organizations of all sizes vulnerable to financially motivated attacks.
This constant need to react and adapt can be overwhelming, potentially leading to decision fatigue and overlooked security measures.
Evolving Threat Landscapes and Emerging Cyber Threats
The ever-changing nature of cyber threats necessitates continuous learning and adaptation from CISOs. New attack methods, such as zero-day exploits and advanced persistent threats (APTs), require proactive security measures and rapid response capabilities. The increasing sophistication of these threats often necessitates investment in advanced security technologies, skilled personnel, and robust incident response plans. Failure to adapt to these evolving threats can directly contribute to successful cyberattacks, highlighting the importance of staying ahead of the curve.
For example, the shift towards cloud-based services has introduced new attack surfaces and vulnerabilities that require specialized security expertise and cloud-specific security solutions.
Regulatory Compliance Requirements
Regulatory compliance requirements, such as GDPR, CCPA, and HIPAA, significantly influence CISO responsibilities and actions. Meeting these regulations demands substantial resources, expertise, and ongoing effort. Failure to comply can result in hefty fines and reputational damage. The complexity and evolving nature of these regulations require CISOs to stay abreast of updates and implement appropriate security controls. This regulatory burden can sometimes divert resources away from other crucial security initiatives, potentially creating a false sense of security in areas with less stringent regulatory oversight.
The pressure to comply can lead to a focus on check-box compliance rather than a holistic security posture.
External Security Audits and Penetration Testing
External security audits and penetration testing play a vital role in identifying and addressing CISO-related security gaps. These independent assessments provide objective evaluations of an organization’s security posture, revealing vulnerabilities that internal teams might overlook. The findings from these audits can help CISOs prioritize security investments, improve security awareness training, and strengthen overall security practices. Regular audits and penetration testing are crucial for maintaining a strong security posture and demonstrating compliance with regulatory requirements.
For instance, a penetration test might reveal a weakness in a web application, allowing a CISO to address the vulnerability before it’s exploited by malicious actors.
The Cybersecurity Skills Gap
The cybersecurity skills gap significantly impacts CISO effectiveness and resource allocation. The shortage of qualified cybersecurity professionals makes it challenging for CISOs to find and retain skilled personnel, hindering their ability to implement and maintain robust security programs. This shortage can also lead to overworked security teams, increasing the risk of human error and potentially compromising security. Organizations often struggle to compete with larger companies offering higher salaries and better benefits, making it difficult to attract and retain top talent.
This lack of skilled personnel can directly affect a CISO’s ability to effectively manage and mitigate cyber risks.
Outcome Summary
The rise in cyberattacks directly linked to CISO laxity demands immediate attention. Addressing this issue requires a multi-pronged approach: improving CISO training to emphasize proactive strategies, fostering a strong security culture, implementing robust cybersecurity policies, and conducting regular risk assessments. By acknowledging the multifaceted nature of this problem – encompassing internal pressures, external threats, and the skills gap – and actively working towards solutions, organizations can significantly reduce their vulnerability to cyberattacks.
Ultimately, a proactive and security-conscious CISO is crucial for organizational survival in today’s digital world.
Essential Questionnaire: Cisos Laxity Towards Cybersecurity Is Leading To More Cyber Attacks
What are some common signs of CISO laxity?
Ignoring security alerts, failing to implement basic security controls, insufficient employee training, and a lack of proactive threat hunting are all red flags.
How can boards of directors hold CISOs accountable?
Regular security briefings, clear performance metrics tied to security outcomes, and independent security audits can enhance accountability.
What role does insurance play in mitigating the impact of CISO negligence?
Cybersecurity insurance can help cover some financial losses, but it doesn’t replace the need for robust security practices. It also often requires demonstrable security efforts.
How can organizations attract and retain skilled cybersecurity professionals to support their CISOs?
Competitive salaries, professional development opportunities, and a positive work environment are key to attracting and retaining top talent.