Omnichannel Marketing Retail & Ecommerce Challenges and Opportunities
Omnichannel marketing challenges and opportunities in retail and ecommerce are reshaping the landscape of how businesses connect with customers. It’s no longer enough to simply have a website and a physical store; today’s savvy shoppers expect a seamless experience across all touchpoints – from browsing on their phone to picking up an order in-store. This means navigating a complex web of technological hurdles, data integration challenges, and the ever-present need to maintain a consistent brand voice.
But the rewards are huge: increased customer loyalty, higher sales, and the ability to deliver truly personalized experiences that keep customers coming back for more.
This post dives deep into the exciting world of omnichannel marketing, exploring both the significant challenges and the incredible opportunities it presents for retailers and e-commerce businesses. We’ll unpack the key strategies, analyze successful implementations, and discuss the future of this rapidly evolving field. Get ready to navigate the complexities and unlock the potential of a truly unified customer journey!
Defining Omnichannel Retail and Ecommerce
Omnichannel retail and ecommerce represent a significant evolution in how businesses engage with their customers. It’s no longer enough to simply have a website and a physical store; today’s successful retailers seamlessly integrate all their channels to create a unified and consistent brand experience. This approach fosters stronger customer relationships and drives increased sales.Omnichannel marketing, at its core, prioritizes a cohesive customer journey across all touchpoints.
The customer should be able to interact with the brand in whichever way is most convenient for them, whether that’s browsing online, making a purchase through a mobile app, picking up an order in-store, or contacting customer service via social media. The key is seamless integration and a consistent brand message across all channels.
Core Principles of Omnichannel Marketing
The fundamental principles of omnichannel marketing revolve around providing a unified and personalized experience. This means consistent branding, messaging, and customer service across all channels. Data integration is crucial, allowing retailers to understand customer behavior across different touchpoints and personalize their interactions. Finally, a robust technology infrastructure is essential to support the seamless integration of all channels.
This includes a unified customer database, inventory management systems, and order fulfillment capabilities that work together effortlessly.
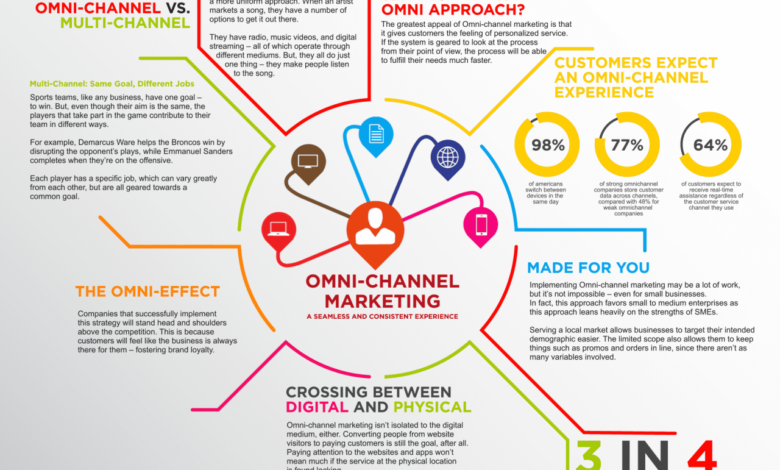
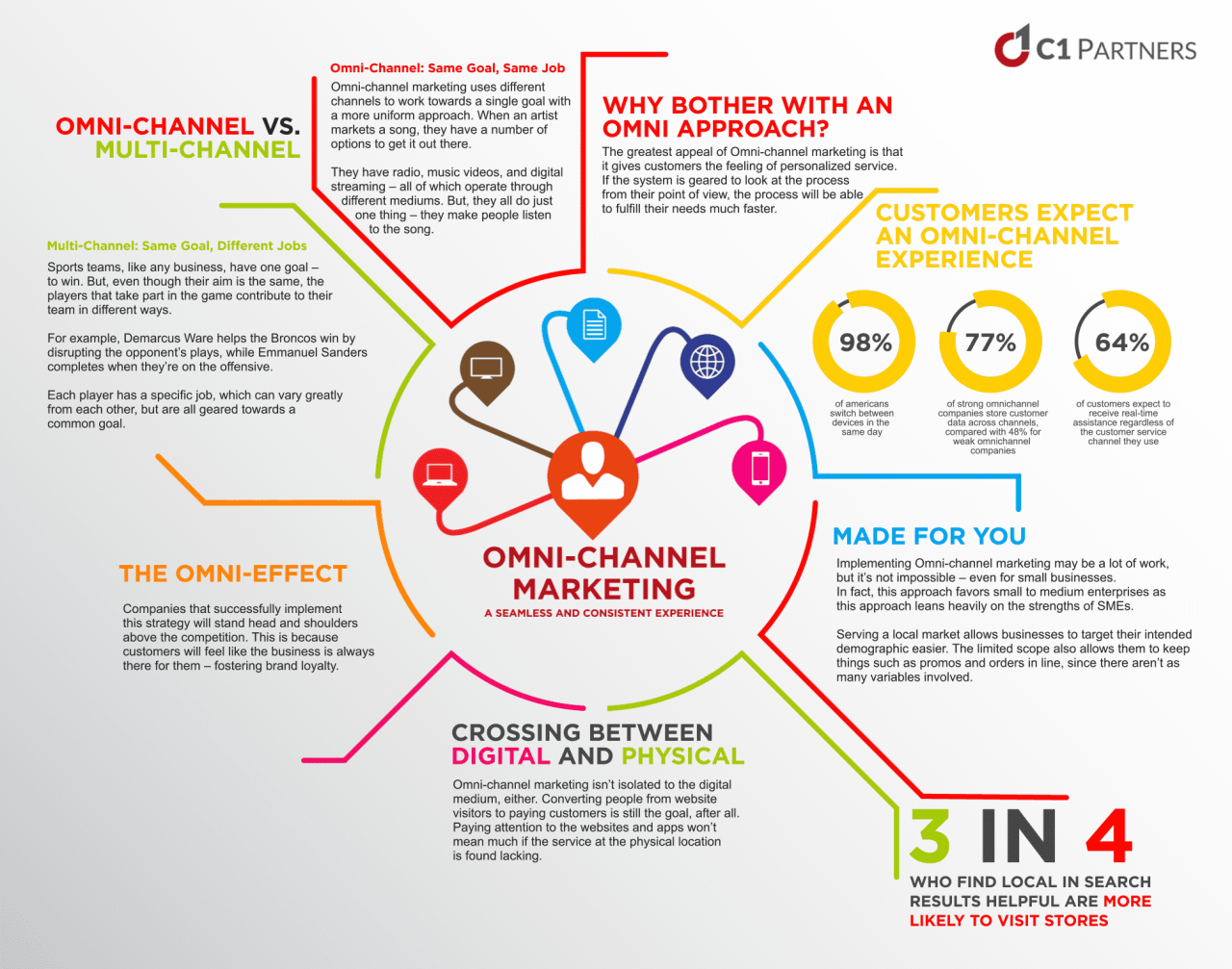
Multichannel vs. Omnichannel Strategies
While both multichannel and omnichannel strategies utilize multiple channels, the key difference lies in integration. Multichannel simply means having a presence across multiple channels (website, social media, physical store, etc.), but these channels operate independently. Omnichannel, on the other hand, integrates these channels to create a cohesive and seamless customer experience. Imagine ordering online and picking up in-store – that’s an omnichannel experience.
Ordering online and receiving a completely separate email confirmation, with no mention of in-store pickup options, is a multichannel experience. The difference is in the integration and unified experience.
Examples of Successful Omnichannel Implementations
Several retailers excel at omnichannel execution. Sephora, for instance, leverages its strong online presence with in-store beauty advisors who can access customer purchase history and preferences, providing personalized recommendations. Grocery stores like Kroger utilize their app for online ordering and in-store pickup or delivery, seamlessly integrating online and offline shopping. Apple, known for its excellent customer service, offers consistent experiences across its online store, app, and physical retail locations, ensuring a seamless transition between channels.
Each of these examples demonstrates the power of a unified, integrated approach.
Customer Experience Across Different Channels
The following table illustrates the differences in customer experience across various channels, highlighting the need for omnichannel integration to provide a consistent and positive experience.
| Channel | Ease of Browsing | Purchase Process | Customer Service |
|---|---|---|---|
| Website | High, wide selection | Convenient, often with various payment options | Email, live chat, FAQs |
| Mobile App | High, personalized recommendations | Streamlined, often with mobile payment options | In-app chat, FAQs |
| Social Media | Medium, limited product display | Often redirects to website or app | Direct messaging, comments |
| Physical Store | Medium, limited selection compared to online | Immediate, tangible experience | In-person assistance, potentially longer wait times |
Challenges of Omnichannel Marketing
Creating a truly seamless omnichannel experience for customers is a significant undertaking, fraught with challenges that require careful planning and execution. The complexity arises from the need to integrate various technologies, manage vast amounts of customer data, and maintain a consistent brand image across numerous touchpoints. Failure to address these challenges can lead to frustrated customers, lost sales, and a damaged brand reputation.Technological Hurdles in Creating a Seamless Omnichannel ExperienceBuilding a truly unified omnichannel experience demands significant technological investment and expertise.
The integration of disparate systems, from CRM and ERP to e-commerce platforms and marketing automation tools, is often a major obstacle. For example, a retailer might struggle to integrate their in-store POS system with their online store’s inventory management system, leading to inaccurate stock information displayed online and potential customer disappointment. Further complicating matters are the differences in technology platforms across channels, making data exchange and synchronization a complex process.
The need for robust APIs and middleware solutions to bridge these gaps adds to the cost and complexity. Legacy systems, often inflexible and resistant to integration, present another significant hurdle. Modernizing these systems can be costly and time-consuming, yet necessary for achieving a true omnichannel experience.Data Integration and Customer Data Management Across ChannelsOne of the biggest challenges in omnichannel marketing is effectively integrating and managing customer data from various sources.
This data, ranging from purchase history and browsing behavior to social media interactions and customer service inquiries, resides in different systems and databases. Consolidating this data into a unified customer view is crucial for personalized marketing and a seamless customer experience. However, achieving this requires overcoming significant hurdles. Data silos, inconsistent data formats, and privacy concerns all complicate the process.
The need for robust data governance and security protocols adds another layer of complexity. For instance, a retailer might struggle to combine data from their loyalty program, website analytics, and social media listening tools to create a comprehensive understanding of a customer’s preferences and behaviors. This lack of a unified view can result in fragmented marketing efforts and missed opportunities for personalization.Maintaining Brand Consistency Across All TouchpointsConsistency in branding and messaging is paramount for building a strong brand identity and fostering customer loyalty.
However, maintaining this consistency across all channels – from physical stores and websites to mobile apps and social media – is a considerable challenge. Different teams managing different channels may have varying interpretations of the brand guidelines, leading to inconsistencies in tone, messaging, and visual elements. Furthermore, ensuring consistency in customer service across all channels requires rigorous training and standardized processes.
For example, a retailer might find that their customer service representatives in physical stores provide a different level of support than their online chat agents, leading to a disjointed customer experience. Maintaining brand consistency requires a clear brand strategy, well-defined brand guidelines, and a robust process for monitoring and enforcing consistency across all channels.Examples of Omnichannel Implementation Failures and Their CausesMany retailers have attempted omnichannel initiatives, only to fall short of their goals.
One common failure is the lack of a clear omnichannel strategy. Without a well-defined plan, integration efforts become fragmented and lack coherence. Another frequent cause of failure is underestimating the technological complexity and the resources required for successful implementation. Retailers often underestimate the time, effort, and cost involved in integrating disparate systems and managing customer data across channels.
A third common reason for failure is neglecting the importance of the customer experience. A successful omnichannel strategy requires a customer-centric approach, prioritizing seamless transitions between channels and personalized experiences. For example, a retailer that fails to integrate its online and offline inventory systems might find itself unable to fulfill online orders promptly, leading to customer dissatisfaction and lost sales.
The lack of a unified view of the customer across channels can also lead to impersonal marketing efforts and a fragmented customer experience.
Opportunities Presented by Omnichannel
Omnichannel marketing, when executed effectively, isn’t just about reaching customers across multiple touchpoints; it’s about creating a seamless and personalized brand experience that fosters loyalty, drives sales, and ultimately, boosts profitability. The interconnected nature of today’s digital landscape presents retailers and e-commerce businesses with unprecedented opportunities to leverage this strategy for significant growth.Omnichannel marketing significantly enhances the customer journey, leading to increased customer lifetime value.
By offering consistent messaging and experiences across all channels, businesses build trust and strengthen relationships with their customers. This unified approach reduces friction and enhances overall customer satisfaction.
Enhanced Customer Loyalty and Retention
A seamless omnichannel experience fosters loyalty. Customers appreciate the convenience of switching effortlessly between online and offline channels, whether they’re browsing products on their phone, researching reviews online, or picking up an order in-store. This convenience directly translates into increased customer loyalty and retention rates. For example, a retailer offering click-and-collect services sees higher repeat purchases from customers who appreciate the ease and flexibility of this option.
Consistent brand messaging and personalized communications across channels further reinforce the customer’s positive brand perception, leading to stronger loyalty.
Increased Sales and Revenue Generation
Omnichannel strategies directly contribute to increased sales and revenue. By offering a unified shopping experience, businesses can reach a wider audience and convert more potential customers. Customers can discover products through various channels (social media ads, email marketing, in-store displays), research them online, and then make a purchase through their preferred method (website, mobile app, in-store). This multi-faceted approach increases the likelihood of conversion compared to a single-channel strategy.
For instance, a retailer using targeted ads on social media directing customers to a specific product page on their website might see a significant lift in online sales.
Personalized Marketing and Targeted Promotions
Omnichannel marketing allows for highly personalized marketing and targeted promotions. By collecting and analyzing data from various customer touchpoints, businesses can create detailed customer profiles and tailor their messaging accordingly. This allows for more effective targeting of specific customer segments with relevant promotions and offers, increasing the effectiveness of marketing campaigns. For example, a retailer might send a personalized email to a customer who recently viewed a specific product online, offering them a discount code for that product.
This level of personalization increases engagement and the likelihood of a purchase.
Hypothetical Omnichannel Marketing Campaign: “Artisan Coffee Beans”
Let’s consider a hypothetical omnichannel marketing campaign for a specialty coffee bean retailer selling a new limited-edition blend, “Ethiopian Yirgacheffe.”The campaign would utilize several channels:
- Website: A dedicated landing page featuring high-quality images and detailed descriptions of the Ethiopian Yirgacheffe blend, including tasting notes and brewing suggestions. A prominent call-to-action encourages customers to purchase online.
- Social Media (Instagram, Facebook): Visually appealing posts showcasing the coffee beans, brewing process, and the unique characteristics of the Ethiopian Yirgacheffe. Targeted ads would reach coffee enthusiasts based on their interests and location.
- Email Marketing: Personalized emails sent to subscribers announcing the new blend and offering exclusive discounts for early purchases. These emails would include high-quality images and links to the product page.
- In-Store Experience: Sampling events in retail locations, with staff trained to educate customers about the unique flavor profile of the coffee beans. Point-of-sale displays featuring the new blend would be prominently placed.
- Mobile App: A loyalty program within the mobile app offering exclusive rewards and early access to new products like the Ethiopian Yirgacheffe. Push notifications would be used to announce the new blend and remind customers about their loyalty points.
This integrated approach aims to reach potential customers across various touchpoints, offering a consistent and personalized brand experience. The expected outcomes include increased brand awareness, higher sales of the Ethiopian Yirgacheffe blend, and enhanced customer loyalty through the loyalty program. Data analytics across all channels would be crucial in measuring the campaign’s success and optimizing future marketing efforts.
Data Management and Analytics in Omnichannel
In today’s hyper-connected world, understanding customer behavior is paramount for retail and e-commerce success. Omnichannel marketing, by its very nature, generates a massive amount of data from diverse sources. Effectively managing and analyzing this data is no longer a luxury but a necessity for businesses aiming to thrive. The ability to glean actionable insights from this data stream allows for targeted campaigns, personalized experiences, and ultimately, increased profitability.Data analytics provides the crucial link between disparate customer interactions across various channels.
By integrating and analyzing data from online and offline touchpoints, businesses gain a holistic view of the customer journey. This 360-degree perspective reveals patterns, preferences, and pain points that would otherwise remain hidden, leading to more effective strategies and optimized resource allocation. This understanding isn’t just about accumulating data; it’s about transforming raw information into actionable knowledge that fuels business growth.
Understanding Customer Behavior Across Channels Through Data Analytics
Analyzing omnichannel data allows businesses to map the complete customer journey, identifying key touchpoints and bottlenecks. For example, analyzing website traffic alongside in-store purchase data can reveal whether online browsing influences offline purchases, and vice-versa. This understanding allows for the optimization of both online and offline strategies to create a seamless customer experience. Furthermore, sentiment analysis of customer reviews and social media mentions provides valuable feedback, highlighting areas for improvement in products, services, or customer service.
By tracking customer interactions across email, social media, mobile apps, and in-store visits, a comprehensive picture of customer behavior emerges, revealing preferences, purchase patterns, and overall engagement levels. This level of insight empowers businesses to make data-driven decisions that enhance the overall customer experience and drive sales.
Leveraging Customer Data for Personalized Omnichannel Experiences
Customer data enables hyper-personalization across all touchpoints. Imagine a customer who browses hiking boots on your website but doesn’t purchase. Using email marketing, you can send a personalized email featuring those specific boots, perhaps with a discount code or highlighting positive customer reviews. Later, if that customer visits your physical store, in-store promotions could be tailored to their online browsing history, further enhancing the personalized experience.
Similarly, location-based mobile marketing can deliver targeted promotions to customers near your physical stores. This personalized approach significantly improves customer engagement and increases the likelihood of conversion. The key is to use data ethically and responsibly, ensuring transparency and respecting customer privacy.
Key Performance Indicators (KPIs) for Omnichannel Marketing Effectiveness
Several KPIs are essential for measuring the success of omnichannel marketing efforts. These include:
- Customer Lifetime Value (CLTV): Measures the total revenue generated by a customer over their relationship with the business. A high CLTV indicates successful customer retention and engagement.
- Website Conversion Rate: Tracks the percentage of website visitors who complete a desired action, such as making a purchase or signing up for a newsletter.
- Return on Ad Spend (ROAS): Calculates the revenue generated for every dollar spent on advertising across all channels.
- Customer Acquisition Cost (CAC): Measures the cost of acquiring a new customer across all channels.
- Average Order Value (AOV): Indicates the average amount spent per order, reflecting the effectiveness of upselling and cross-selling strategies.
- Channel Attribution: Determines which channels are most effective in driving conversions, allowing for optimized resource allocation.
Data Sources and Integration Challenges in Omnichannel Marketing
Effective omnichannel marketing relies on integrating data from various sources. However, this integration can present significant challenges.
- CRM Systems: Store customer information, purchase history, and interactions. Integration challenges include data silos and inconsistencies across different CRM platforms.
- E-commerce Platforms: Provide data on online transactions, website behavior, and customer preferences. Challenges include compatibility issues with other systems and data security concerns.
- Point-of-Sale (POS) Systems: Capture in-store transaction data. Integration requires bridging the gap between online and offline data.
- Social Media Platforms: Offer insights into customer sentiment, brand perception, and engagement. Accessing and analyzing this data can be complex due to API limitations and data privacy regulations.
- Email Marketing Platforms: Track email open rates, click-through rates, and conversions. Integration requires syncing email data with other customer data sources.
- Mobile Apps: Collect data on app usage, location, and in-app purchases. Integration necessitates secure data transfer and real-time data synchronization.
Technology and Tools for Omnichannel Success
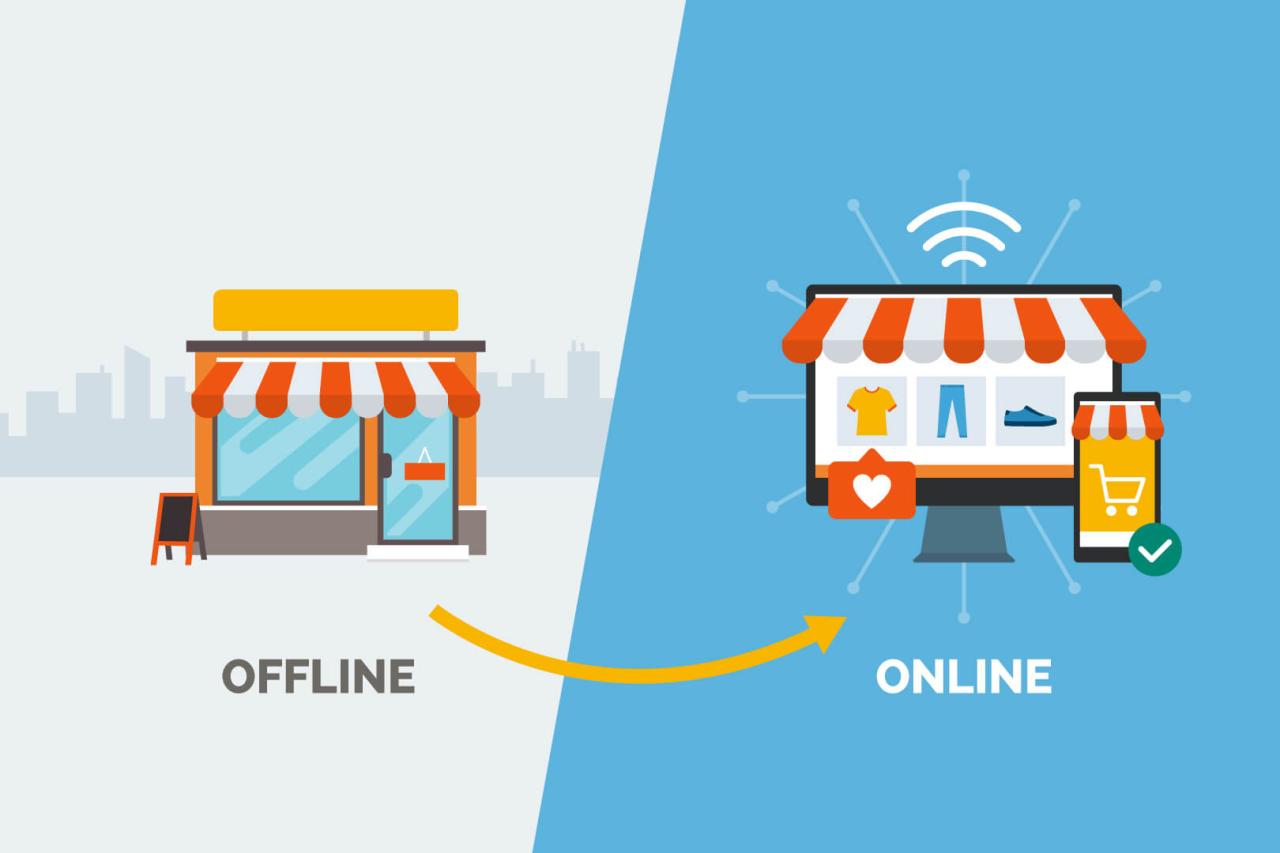
Successfully navigating the omnichannel landscape requires a robust technological foundation. The right tools and their seamless integration are crucial for delivering consistent, personalized experiences across all touchpoints, ultimately driving customer loyalty and boosting sales. This section will explore essential technologies and their role in achieving omnichannel excellence.
Essential Technologies for Omnichannel Marketing
A successful omnichannel strategy relies on several key technologies working in harmony. These technologies enable businesses to collect, analyze, and act upon customer data to create personalized experiences. Without these foundational tools, a true omnichannel approach is difficult, if not impossible, to achieve.
- CRM Systems: Customer Relationship Management (CRM) systems are the backbone of omnichannel marketing. They provide a centralized repository for all customer data, including purchase history, interactions across channels, and preferences. Examples include Salesforce, HubSpot, and Microsoft Dynamics 365. These systems enable personalized communication and targeted marketing campaigns based on individual customer profiles.
- Marketing Automation Platforms: Marketing automation platforms automate repetitive marketing tasks, allowing marketers to focus on strategy and personalization. These platforms manage email marketing, social media campaigns, and other automated processes. Popular examples include Marketo, Pardot, and ActiveCampaign. They enable the creation of automated workflows triggered by customer actions, ensuring timely and relevant communication.
- Order Management Systems (OMS): OMS provide a single view of inventory across all sales channels, ensuring accurate order fulfillment regardless of where the customer places the order. This eliminates stock discrepancies and improves order accuracy, leading to increased customer satisfaction. Effective OMS solutions integrate with e-commerce platforms, warehouses, and shipping providers for seamless order processing.
- Personalization Engines: These platforms leverage customer data to deliver highly personalized experiences across all channels. They analyze customer behavior and preferences to recommend products, tailor messaging, and optimize the customer journey. For example, a personalization engine might recommend products based on past purchases or browsing history, or it might dynamically adjust website content based on the customer’s location or device.
Comparison of Omnichannel Marketing Platforms
Different platforms offer varying functionalities and levels of integration. The best choice depends on a business’s specific needs and resources. A thorough evaluation of features, scalability, and cost is crucial before selecting a platform.
| Platform | Strengths | Weaknesses |
|---|---|---|
| Salesforce Marketing Cloud | Robust features, excellent integration with Salesforce CRM, strong analytics | Can be expensive, complex to implement |
| Adobe Experience Cloud | Comprehensive suite of tools, strong personalization capabilities, excellent analytics | High cost, requires specialized expertise |
| HubSpot | User-friendly interface, affordable pricing options, good integration with other HubSpot tools | Fewer advanced features compared to enterprise-level platforms |
The Role of Mobile Technology in Enhancing the Omnichannel Customer Journey
Mobile technology is pivotal in creating seamless omnichannel experiences. Customers increasingly interact with brands through their smartphones, making mobile optimization crucial.
- Mobile Apps: Well-designed mobile apps provide a convenient and personalized shopping experience, allowing customers to browse products, manage orders, and access customer service easily. Push notifications can be used for targeted promotions and updates, further enhancing engagement.
- Mobile-Optimized Websites: A responsive website that adapts to different screen sizes is essential for providing a consistent experience across devices. This ensures that customers can easily access information and make purchases regardless of whether they’re using a smartphone, tablet, or desktop computer.
- Mobile Payment Options: Offering various mobile payment options, such as Apple Pay and Google Pay, streamlines the checkout process and improves the overall customer experience. This convenience encourages quicker purchases and higher conversion rates.
Integrating Technologies for a Seamless Customer Experience
The key to omnichannel success lies in the seamless integration of different technologies. Data synchronization across platforms is crucial to ensure a consistent customer view and personalized experiences. For example, a customer adding an item to their online shopping cart should see that item reflected in their mobile app and vice versa. Real-time data synchronization enables personalized recommendations and targeted promotions based on the customer’s latest actions across channels.
This unified approach avoids frustrating inconsistencies and strengthens brand loyalty.
The Future of Omnichannel Retail and Ecommerce
The next five years promise a dramatic reshaping of the omnichannel landscape, driven by technological advancements and evolving consumer expectations. We’ll see a blurring of lines between physical and digital experiences, a hyper-personalization of shopping journeys, and a relentless focus on seamless transitions across channels. This evolution will reward retailers who embrace innovation and prioritize customer-centricity.
Future Trends in Omnichannel Marketing, Omnichannel marketing challenges and opportunities in retail and ecommerce
Several key trends will define omnichannel marketing over the next five years. Artificial intelligence will power increasingly sophisticated personalization engines, predicting customer needs and preferences with unprecedented accuracy. Augmented and virtual reality technologies will revolutionize product discovery and visualization, allowing customers to experience products in immersive ways before purchasing. The rise of the metaverse will create new opportunities for brand engagement and interactive shopping experiences.
Finally, sustainability and ethical considerations will increasingly influence consumer choices, prompting retailers to adopt more responsible omnichannel strategies. For example, we can expect to see a rise in platforms that offer detailed information on a product’s carbon footprint or ethical sourcing practices, integrated directly into the shopping journey.
Innovative Omnichannel Strategies
Leading retailers are already pioneering innovative omnichannel strategies. Nike’s app, for example, seamlessly integrates online and offline experiences, allowing customers to reserve products for in-store pickup, track their orders, and access personalized fitness content. Sephora utilizes augmented reality to let customers virtually try on makeup, enhancing the online shopping experience and reducing the risk of returns. Starbucks’ loyalty program rewards customers for purchases across all channels, encouraging repeat business and fostering brand loyalty.
These are just a few examples of how forward-thinking retailers are leveraging technology to create seamless and engaging omnichannel experiences.
Impact of Emerging Technologies
Artificial intelligence (AI) is transforming omnichannel marketing through personalized recommendations, predictive analytics, and automated customer service. Augmented reality (AR) and virtual reality (VR) are enhancing product discovery and visualization, allowing customers to experience products in immersive ways. The metaverse presents new opportunities for brand engagement and interactive shopping experiences, creating virtual stores and interactive product demonstrations. These technologies are not just improving the customer experience; they are also optimizing operations, improving inventory management, and enhancing supply chain efficiency.
A Potential Future Omnichannel Shopping Experience
Imagine a future where shopping begins with a personalized AI-powered recommendation engine, suggesting products based on your past purchases, browsing history, and even your current location. You can then use AR to visualize the products in your own home, experiencing them in a 3D environment. You can consult with a virtual stylist through a VR headset, receiving personalized advice on outfit choices or home décor.
After making your selection, the purchase is seamlessly integrated into a unified shopping cart across all channels. Delivery is optimized using AI-powered routing and predictive analytics, ensuring swift and efficient delivery. Post-purchase, you receive personalized follow-up communications, including proactive customer service and exclusive offers. This seamless integration of online and offline channels, powered by AI, AR/VR, and other advanced technologies, represents the future of omnichannel retail.
Concluding Remarks: Omnichannel Marketing Challenges And Opportunities In Retail And Ecommerce
The journey into omnichannel marketing is undeniably complex, demanding significant investment in technology and a deep understanding of customer behavior. However, the potential rewards—enhanced customer loyalty, boosted sales, and a competitive edge—make it a worthwhile pursuit. By embracing data-driven strategies, investing in the right technology, and prioritizing a seamless customer experience, businesses can overcome the challenges and unlock the transformative power of omnichannel marketing.
The future of retail and e-commerce hinges on this ability to connect with customers on their terms, across all channels, creating a unified and personalized shopping experience that fosters lasting relationships and drives sustainable growth.
FAQ Compilation
What’s the difference between multichannel and omnichannel marketing?
Multichannel simply uses multiple channels (website, social media, etc.) independently. Omnichannel integrates these channels for a seamless customer experience.
How can I measure the success of my omnichannel strategy?
Key Performance Indicators (KPIs) like customer lifetime value (CLTV), conversion rates across channels, and customer satisfaction scores are crucial.
What are some common omnichannel marketing mistakes to avoid?
Inconsistent branding, poor data integration, neglecting mobile optimization, and failing to personalize the customer journey are major pitfalls.
How much does implementing an omnichannel strategy cost?
Costs vary widely depending on existing infrastructure, chosen technology, and the scope of implementation. Expect a significant investment, but consider the potential ROI.