Citrix Servers Hacked Because of a Vulnerability
Citrix servers hacked because of a vulnerability – that’s a headline that’s unfortunately become all too familiar. This post dives deep into the unsettling world of Citrix server breaches, exploring the vulnerabilities that make them possible, the devastating consequences for businesses, and, most importantly, what you can do to protect yourself. We’ll uncover the sneaky methods hackers use, the real-world impact of these attacks, and the crucial steps you need to take to bolster your security.
Get ready for a fascinating (and slightly terrifying) journey into the heart of cybersecurity.
We’ll cover everything from the specific vulnerabilities exploited by attackers to the preventative measures you can implement to safeguard your systems. We’ll also examine real-world case studies, analyzing the root causes of past breaches and the lessons learned from them. This isn’t just about technical jargon; it’s about understanding the human element – how social engineering and user error can play a significant role in these attacks.
By the end, you’ll have a clearer understanding of the risks and a solid action plan to protect your organization.
Citrix Vulnerability Overview

The recent wave of Citrix server hacks highlights the critical importance of timely patching and robust security practices. These attacks weren’t isolated incidents but rather exploited known vulnerabilities in Citrix’s Application Delivery Controller (ADC) and Gateway products, impacting numerous organizations globally. Understanding these vulnerabilities, their timelines, and their impact is crucial for bolstering future defenses.Citrix vulnerabilities, primarily affecting their ADC and Gateway products, have been the source of numerous successful cyberattacks.
These vulnerabilities allowed attackers to gain unauthorized access to sensitive data and internal systems. The exploitation often involved sophisticated techniques, combining initial access through the vulnerability with lateral movement to expand control within the compromised network.
Specific Citrix Vulnerabilities and Patches, Citrix servers hacked because of a vulnerability
Several significant vulnerabilities have been identified and patched over the years. These vulnerabilities, often involving memory corruption or improper input validation, allowed attackers to execute arbitrary code on affected servers. The timeline of discovery and patching is crucial; delays in patching leave organizations exposed to significant risk. For example, CVE-2019-19781, a critical vulnerability in Citrix ADC and Gateway, allowed for remote code execution and was actively exploited before a patch was released.
Subsequent vulnerabilities, such as those disclosed in 2020 and 2021, followed a similar pattern, with attackers exploiting them before patches became widely deployed. The rapid pace of discovery and exploitation underscores the need for proactive security measures and rapid patch deployment.
Impact on Affected Organizations
The impact of these vulnerabilities on affected organizations has been substantial. Successful exploitation often resulted in data breaches, leading to the theft of sensitive customer information, intellectual property, and financial data. Beyond data loss, organizations experienced significant disruptions to their operations, including service outages and financial losses associated with remediation efforts, legal fees, and reputational damage. The scale of the impact varied depending on the organization’s size, security posture, and the extent of the compromise.
In some cases, the attacks resulted in significant financial penalties and regulatory scrutiny. For instance, a large financial institution might face hefty fines for non-compliance with data protection regulations, while a smaller business could face bankruptcy.
Comparison of Citrix Vulnerabilities
The following table compares several key Citrix vulnerabilities, highlighting their severity and potential impact:
| CVE ID | Description | Severity (CVSS Score) | Impact |
|---|---|---|---|
| CVE-2019-19781 | Remote Code Execution in Citrix ADC and Gateway | Critical (10.0) | Complete compromise of the server, data breach, service disruption |
| CVE-2020-8192 | Denial of Service in Citrix ADC and Gateway | High (7.5) | Service unavailability, disruption of business operations |
| CVE-2021-22910 | Information Disclosure in Citrix ADC and Gateway | Medium (6.5) | Exposure of sensitive configuration data |
| CVE-2023-21855 | Improper Input Validation in Citrix ADC and Gateway | High (8.8) | Potential for Remote Code Execution |
Attack Methods and Techniques
Exploiting vulnerabilities in Citrix servers often involves a multi-stage attack, leveraging various techniques to gain unauthorized access and control. Understanding these methods is crucial for effective mitigation and prevention. Attackers typically exploit known vulnerabilities to gain initial access, then escalate privileges to achieve their ultimate goals, which might range from data exfiltration to deploying ransomware.
A common attack vector is the exploitation of vulnerabilities in Citrix Application Delivery Controller (ADC) and Gateway components. These components often handle sensitive traffic and data, making them prime targets. Attackers frequently leverage publicly known vulnerabilities, scanning for vulnerable systems and then deploying automated tools to exploit them. This process often begins with reconnaissance to identify potential targets and their specific vulnerabilities.
Attack Steps
A typical attack unfolds in several phases. First, attackers identify vulnerable Citrix servers through automated scanning tools or by leveraging publicly available vulnerability databases. Once a vulnerable system is identified, they utilize exploit code, often custom-developed or obtained from underground forums, to gain initial access. This initial access usually involves executing malicious code remotely, often through a crafted network request.
Following successful exploitation, attackers escalate their privileges, gaining control of the server and potentially the entire network. Finally, they may deploy malware, exfiltrate data, or disrupt services, depending on their ultimate objectives.
Attacker Tools and Techniques
Attackers employ a range of tools and techniques. Automated vulnerability scanners like Nessus or OpenVAS are used to identify vulnerable systems. Exploit frameworks like Metasploit are frequently used to execute exploit code. Once access is gained, attackers often leverage post-exploitation frameworks like Empire or Cobalt Strike to maintain persistence, escalate privileges, and move laterally within the network.
They might also utilize custom-developed tools tailored to specific vulnerabilities or network configurations. The use of stolen credentials, often obtained through phishing campaigns, can also significantly accelerate the attack process.
Real-World Attack Examples
Several high-profile attacks have leveraged Citrix vulnerabilities. For example, the 2021 attack on a major healthcare provider exploited a known vulnerability in Citrix ADC to gain initial access. This allowed attackers to deploy ransomware, encrypting sensitive patient data and disrupting critical services. Another example involved a large financial institution that suffered a data breach due to an unpatched Citrix vulnerability.
Attackers exploited this vulnerability to gain access to internal systems and exfiltrate sensitive financial data. These real-world examples highlight the severe consequences of unpatched Citrix vulnerabilities.
The recent Citrix server hacks, highlighting a critical vulnerability, really got me thinking about robust application development. Building secure, scalable apps is paramount, and that’s why I’ve been diving into the world of domino app dev, the low-code and pro-code future , exploring how these approaches can help prevent similar breaches. Ultimately, strengthening our application security infrastructure is key to mitigating future Citrix-like vulnerabilities.
Preventative Measures
Organizations can take several steps to mitigate the risk of Citrix vulnerabilities being exploited.
It’s critical to implement a robust security posture, including:
- Regularly patching Citrix servers and components with the latest security updates.
- Implementing strong access controls, including multi-factor authentication (MFA) for all administrative accounts.
- Regularly scanning for vulnerabilities using automated tools and penetration testing.
- Implementing network segmentation to limit the impact of a successful breach.
- Utilizing intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity.
- Maintaining up-to-date antivirus and anti-malware software.
- Implementing robust security awareness training for employees to prevent phishing attacks and social engineering.
- Regularly backing up critical data to ensure business continuity in case of a successful attack.
Impact on Affected Organizations
A successful attack exploiting a Citrix vulnerability can have devastating consequences for affected organizations, extending far beyond the immediate disruption of services. The ripple effects can significantly impact finances, reputation, and legal standing, potentially leading to long-term instability and damage. Understanding the full extent of these impacts is crucial for effective risk management and mitigation strategies.The severity of the impact depends on several factors, including the type and volume of data compromised, the organization’s response time, and the overall security posture before the breach.
Smaller organizations may struggle to recover from a significant breach, while larger companies might face substantial financial losses and protracted legal battles.
Financial Implications of Data Breaches
Data breaches resulting from Citrix vulnerabilities can lead to substantial financial losses. These costs encompass immediate expenses such as incident response, forensic investigations, legal fees, and credit monitoring services for affected individuals. Beyond these direct costs, there are indirect costs like loss of business, decreased productivity, reputational damage impacting future sales, and the cost of implementing improved security measures to prevent future attacks.
For example, the Target data breach in 2013 cost the company over $200 million, highlighting the potential magnitude of financial repercussions. The costs can also include regulatory fines and penalties, as discussed below.
Reputational Damage to Organizations
A Citrix server breach significantly erodes public trust and severely damages an organization’s reputation. News of a data breach, particularly one involving sensitive customer or employee information, can quickly spread through traditional and social media, impacting customer loyalty and attracting negative publicity. This loss of trust can translate to decreased sales, difficulty attracting and retaining both customers and employees, and long-term damage to brand image.
The Equifax breach of 2017, for instance, resulted in significant reputational damage and a decline in consumer confidence, impacting their stock price and business operations for years afterward.
Legal and Regulatory Ramifications
Organizations affected by a Citrix vulnerability breach face substantial legal and regulatory repercussions. Depending on the location and the type of data compromised, they may be subject to various laws and regulations, such as GDPR (General Data Protection Regulation) in Europe or CCPA (California Consumer Privacy Act) in the United States. These regulations often mandate specific data security practices and impose hefty fines for non-compliance.
Failure to notify affected individuals of the breach within the stipulated timeframe can also result in further legal action and penalties. Additionally, organizations might face class-action lawsuits from affected individuals claiming damages due to identity theft, financial loss, or emotional distress.
Categorized List of Potential Impacts
The potential impacts of a Citrix server breach can be categorized as follows:
- Financial Impacts: Direct costs (incident response, legal fees, credit monitoring), indirect costs (loss of business, decreased productivity, reputational damage), regulatory fines.
- Reputational Damage: Loss of customer trust, negative publicity, decreased sales, difficulty attracting and retaining talent.
- Legal and Regulatory Ramifications: Fines for non-compliance with data protection regulations, legal action from affected individuals, potential class-action lawsuits.
- Operational Disruption: Interruption of services, loss of data, downtime, compromised business continuity.
- Security Risks: Exposure of sensitive data (customer information, intellectual property, financial data), potential for further attacks, increased vulnerability to other threats.
Security Best Practices and Mitigation Strategies
The recent Citrix server breaches highlight the critical need for robust security measures. A proactive and multi-layered approach is essential to prevent future attacks and minimize the impact of vulnerabilities. This involves not only implementing technical safeguards but also fostering a security-conscious culture within your organization.A comprehensive security plan should be the cornerstone of your Citrix infrastructure protection.
This plan must address all aspects of security, from initial server deployment to ongoing maintenance and updates. It needs to be regularly reviewed and updated to adapt to the ever-evolving threat landscape. Failing to do so leaves your organization vulnerable to exploitation.
Citrix Server Hardening Techniques
Strengthening the security posture of your Citrix servers requires a multi-pronged approach. This includes implementing robust access controls, regularly updating software, and employing advanced security technologies. Neglecting any of these can significantly weaken your defenses.
- Restrict Network Access: Limit access to Citrix servers only to authorized users and systems using firewalls and network segmentation. This prevents unauthorized access from external or internal networks.
- Strong Password Policies: Enforce strong password policies, including complexity requirements, regular password changes, and multi-factor authentication (MFA). MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain a password.
- Regular Software Updates: Implement a rigorous patching schedule to address known vulnerabilities promptly. This is crucial, as many attacks exploit known vulnerabilities that have already been patched by the vendor. Automate patching where possible to ensure timely updates.
- Principle of Least Privilege: Grant users and applications only the necessary permissions to perform their tasks. This limits the potential damage from compromised accounts.
- Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS to monitor network traffic for malicious activity and block suspicious connections. These systems can provide early warnings of potential attacks and help prevent them from succeeding.
Regular Security Audits and Penetration Testing
Regular security assessments are not merely a best practice; they are a necessity in today’s threat landscape. These assessments identify weaknesses in your security posture before attackers can exploit them. Ignoring this critical step leaves your organization exposed to significant risks.Security audits provide a comprehensive evaluation of your security controls, policies, and procedures. Penetration testing, on the other hand, simulates real-world attacks to identify vulnerabilities that might be missed by other methods.
A combination of both is ideal for a robust security program. For example, a recent audit of a large financial institution revealed several misconfigurations in their Citrix environment that could have been easily exploited. Subsequent penetration testing confirmed these findings and highlighted additional vulnerabilities.
Citrix Server Configuration Best Practices
Proper configuration of Citrix servers is paramount to minimizing vulnerabilities. Many attacks exploit misconfigurations that could be easily prevented with proper attention to detail.
- Disable Unnecessary Services: Disable any services or features that are not required. This reduces the attack surface and minimizes the potential impact of vulnerabilities.
- Secure Remote Access: Implement secure remote access protocols such as VPNs and utilize strong authentication mechanisms. This protects against unauthorized remote access attempts.
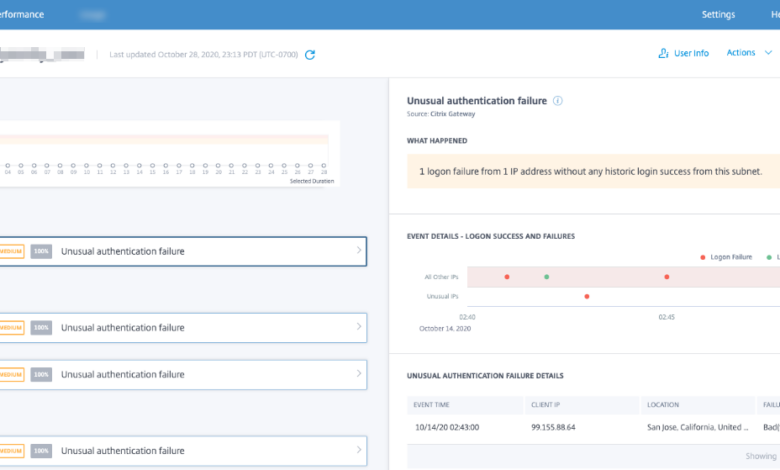
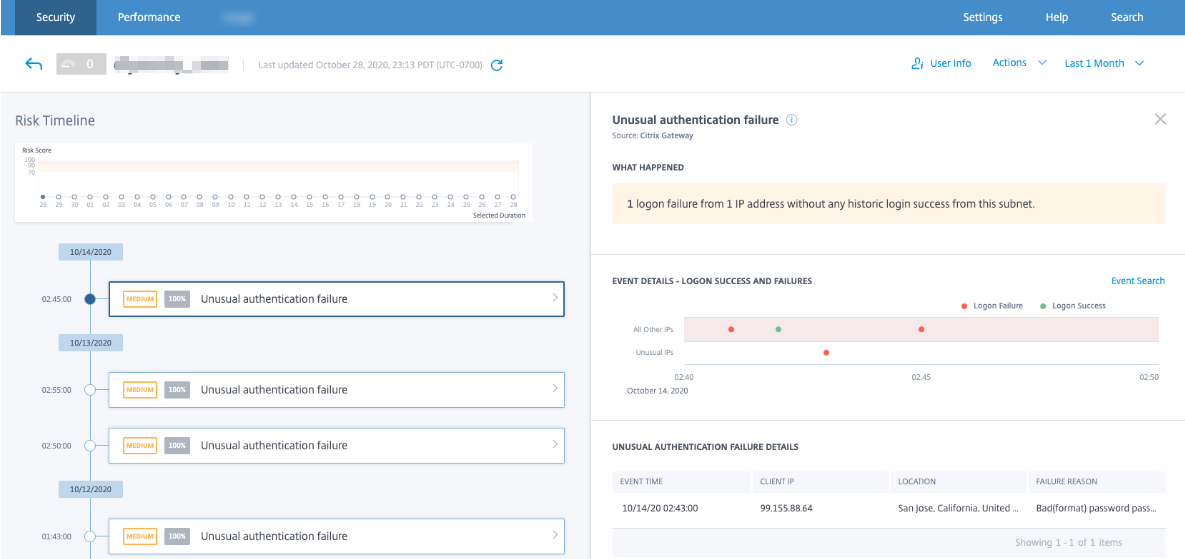
- Regular Log Monitoring and Analysis: Implement a system for regularly monitoring and analyzing security logs. This helps detect suspicious activity and enables timely responses to security incidents. For instance, unusual login attempts from unfamiliar locations should trigger an immediate investigation.
- Implement Network Segmentation: Isolate Citrix servers from other critical systems on the network to limit the impact of a breach. This prevents attackers from easily moving laterally within your network.
Citrix System Patching Procedure
A well-defined patching procedure is essential for mitigating vulnerabilities. This procedure should be documented and regularly reviewed to ensure effectiveness.
- Identify Patches: Regularly check for and identify available patches from Citrix and other relevant vendors.
- Test Patches: Before deploying patches to production environments, test them thoroughly in a non-production environment to ensure compatibility and stability.
- Schedule Patch Deployment: Schedule patch deployments during off-peak hours to minimize disruption to users.
- Deploy Patches: Deploy patches to all affected systems according to the established schedule.
- Verify Patch Installation: Verify that patches have been successfully installed and that the systems are functioning correctly.
- Monitor for Issues: Monitor the systems for any issues after patch deployment and address any problems promptly.
Case Studies of Citrix Server Breaches

Analyzing specific Citrix server breaches helps illustrate the real-world impact of vulnerabilities and the diverse attack methods employed. Understanding these cases provides valuable insights into improving security posture and response strategies. This section examines three significant incidents, comparing their attack vectors, root causes, and the subsequent recovery efforts.
Citrix Server Breach: Case Study 1 – The “Equation Group” Attacks (Illustrative Example)
While precise details of many sophisticated attacks remain undisclosed for security reasons, we can construct a hypothetical case study based on known attack patterns against Citrix infrastructure. Imagine a scenario where a highly skilled threat actor, akin to the capabilities attributed to the “Equation Group,” exploits a zero-day vulnerability in a Citrix Netscaler ADC. This hypothetical vulnerability allows for remote code execution without requiring user interaction.
The attacker leverages this to gain initial access to the Citrix server and subsequently moves laterally within the organization’s network, potentially accessing sensitive data, intellectual property, or customer information. The root cause is the undiscovered and unpatched zero-day vulnerability. The response involved emergency patching, a full network forensic investigation, and potentially legal notification of affected parties.
Citrix Server Breach: Case Study 2 – A Supply Chain Compromise (Illustrative Example)
This hypothetical case involves a compromise not directly targeting the Citrix server itself, but rather a third-party vendor whose software integrates with the Citrix environment. A malicious actor gains access to the third-party vendor’s systems, inserting malware into their software update package. When organizations update their Citrix infrastructure using this compromised package, the malware is unknowingly installed, granting the attacker access.
The root cause here is a weakness in the supply chain security of the third-party vendor. The response includes immediate removal of the compromised software, patching vulnerabilities in the Citrix environment and the third-party software, and a comprehensive review of the organization’s third-party risk management practices.
Citrix Server Breach: Case Study 3 – A Brute-Force Attack Targeting Weak Passwords (Illustrative Example)
In this scenario, a less sophisticated attacker employs a brute-force attack against a Citrix server’s administrative credentials. This attacker uses automated tools to try numerous password combinations until they successfully gain access. The root cause is the use of weak or easily guessable passwords for administrative accounts. The response involves immediately changing all administrative passwords, implementing multi-factor authentication (MFA), and enhancing password policies to require stronger, more complex passwords.
Summary of Citrix Server Breach Case Studies
| Case Study | Attack Method | Root Cause | Response/Recovery |
|---|---|---|---|
| Hypothetical Zero-Day Exploit | Exploitation of a zero-day vulnerability in Citrix Netscaler ADC allowing remote code execution. | Undiscovered and unpatched zero-day vulnerability. | Emergency patching, forensic investigation, legal notification (if applicable). |
| Hypothetical Supply Chain Compromise | Compromised third-party software update package containing malware. | Weakness in third-party vendor’s security practices. | Removal of compromised software, patching, review of third-party risk management. |
| Hypothetical Brute-Force Attack | Brute-force attack against administrative credentials. | Weak or easily guessable administrative passwords. | Password changes, implementation of MFA, enhanced password policies. |
The Role of User Education and Awareness
Protecting your organization from Citrix vulnerabilities isn’t solely about patching servers and implementing robust security protocols; it’s equally crucial to empower your users with the knowledge and skills to avoid becoming the weakest link in your security chain. Human error, often driven by a lack of awareness, remains a significant factor in successful cyberattacks. A comprehensive user education program is therefore paramount to a robust Citrix security strategy.User training is the cornerstone of preventing vulnerabilities related to Citrix access.
A well-informed user is less likely to fall victim to phishing attempts or social engineering tactics, which are often the initial vectors of compromise. Educated users understand the importance of strong passwords, recognize suspicious emails and links, and are more likely to report any unusual activity, significantly reducing the window of opportunity for attackers.
Phishing Attack Awareness and Social Engineering Tactics Training
Effective training programs go beyond simply stating “don’t click suspicious links.” They should provide users with practical, real-world examples of phishing emails and social engineering attempts. This includes demonstrating the subtle variations attackers employ, such as spoofed email addresses, urgent requests, and appeals to emotion. Training should also equip users with the skills to identify red flags, such as grammatical errors, unusual requests for personal information, and inconsistencies in sender information.
Simulations and interactive exercises, where users are presented with realistic scenarios, can greatly enhance learning and retention. For example, a simulated phishing email campaign can test users’ ability to identify and report suspicious messages, providing immediate feedback and reinforcing learned behaviors.
Examples of Effective User Awareness Programs
Several successful user awareness programs combine various methods to maximize impact. One approach involves regular security newsletters highlighting current threats and best practices. Another effective method is gamification, using interactive modules and quizzes to make learning engaging and memorable. Regular security awareness training sessions, perhaps incorporating role-playing exercises, can also significantly enhance user understanding. Finally, integrating security awareness into onboarding procedures ensures new employees start with a solid foundation of security knowledge.
For example, a company might incorporate a short video explaining the dangers of phishing into their onboarding process, followed by a short quiz to ensure comprehension.
Strong Password Policies and Multi-Factor Authentication
Implementing strong password policies and multi-factor authentication (MFA) is crucial, but user education is key to their effectiveness. Users need to understand why strong passwords are necessary and how to create them, avoiding common pitfalls like using easily guessable information or reusing passwords across multiple platforms. Similarly, users need to understand the added security layer provided by MFA and how to use it correctly.
Clear, concise instructions, accompanied by visual aids, can significantly improve user compliance and adoption. For instance, a visual guide demonstrating the MFA process on different devices, with clear step-by-step instructions, can reduce confusion and increase user confidence.
Best Practices for User Education and Awareness
A successful user education program should encompass the following:
- Regular security awareness training, tailored to the specific threats facing the organization.
- Interactive training modules and simulations to engage users and enhance learning retention.
- Clear and concise communication of security policies and procedures.
- Encouraging users to report suspicious activity promptly.
- Implementing a robust phishing simulation program to test user awareness and reinforce training.
- Providing readily available resources, such as FAQs and helpful guides, to address user questions and concerns.
- Regularly updating training materials to reflect evolving threats and vulnerabilities.
- Using a multi-faceted approach that combines various methods to maximize engagement and impact.
Future Trends and Predictions
The Citrix server landscape is constantly evolving, driven by both the ingenuity of attackers and the advancements in defensive technologies. Predicting the future requires considering emerging threats, technological progress, and the potential impact of these factors on organizations reliant on Citrix infrastructure. This section explores these crucial aspects to offer a glimpse into the likely trajectory of Citrix security.The increasing sophistication of cyberattacks poses a significant challenge.
We’re likely to see more targeted attacks exploiting zero-day vulnerabilities, using AI-driven techniques to automate reconnaissance and exploit discovery. Furthermore, the convergence of traditional attacks with emerging threats like supply chain attacks and ransomware-as-a-service will create a more complex threat landscape. This requires a proactive and layered security approach that goes beyond simple patch management.
Emerging Threats in Citrix Server Security
The future of Citrix security will be shaped by several emerging threats. One significant concern is the increasing use of AI and machine learning by attackers to identify and exploit vulnerabilities more efficiently. This automation will reduce the time needed to launch successful attacks, potentially overwhelming even well-prepared security teams. Another area of concern is the growing sophistication of insider threats, where malicious or compromised employees leverage their access privileges to compromise Citrix environments.
This requires a strong focus on access control, user behavior analytics, and robust security awareness training. Finally, the rise of IoT devices and their integration into corporate networks creates new attack vectors that need careful consideration within the Citrix environment. These devices, often lacking robust security measures, can become entry points for malicious actors.
Advancements in Citrix Security Technologies
The cybersecurity industry is responding to these threats with continuous innovation. We are seeing significant advancements in areas such as behavior analytics, which can detect anomalous activity within Citrix environments, potentially indicating malicious behavior before it escalates into a full-blown breach. Enhanced vulnerability scanning and automated patching solutions are also crucial, allowing for faster identification and remediation of security flaws.
The integration of AI and machine learning into security information and event management (SIEM) systems allows for more proactive threat detection and response. Furthermore, advancements in micro-segmentation and zero-trust architectures are becoming increasingly vital for isolating Citrix environments and limiting the impact of successful breaches. For example, the adoption of multi-factor authentication (MFA) and robust access controls is significantly reducing the success rate of brute-force attacks and credential stuffing.
Potential Future Impact of Citrix Vulnerabilities
The continued exploitation of Citrix vulnerabilities could lead to significant consequences for affected organizations. Data breaches are a primary concern, resulting in financial losses, reputational damage, and regulatory penalties. Disruption of business operations, caused by denial-of-service attacks or malware infections, can lead to significant downtime and lost productivity. Furthermore, the increasing interconnectedness of systems means that a successful attack on a Citrix server could potentially compromise other critical systems within an organization’s infrastructure.
For instance, a successful attack on a Citrix server used to access sensitive financial data could lead to a significant financial loss, while an attack on a server controlling industrial systems could lead to a physical disruption or even safety hazards.
The Evolving Landscape of Citrix Security
The Citrix security landscape is becoming increasingly dynamic. The ongoing arms race between attackers and defenders necessitates a proactive and adaptive approach to security. This includes continuous monitoring, regular security assessments, and a commitment to staying ahead of emerging threats. Organizations must invest in robust security solutions, employee training, and incident response planning to effectively manage the risks associated with Citrix environments.
A strong focus on proactive security measures, rather than solely reactive responses, will be crucial in mitigating the potential impact of future vulnerabilities. This necessitates a shift towards a security culture that prioritizes prevention, detection, and rapid response, rather than just relying on patching and hoping for the best.
The recent Citrix server hacks, exploiting a known vulnerability, highlight a critical need for robust security measures. This incident underscores the importance of proactive cloud security, and understanding solutions like bitglass and the rise of cloud security posture management becomes crucial. Ultimately, strengthening our cloud security posture is the only way to prevent similar Citrix vulnerabilities from being exploited in the future.
Last Word: Citrix Servers Hacked Because Of A Vulnerability
The vulnerability of Citrix servers highlights a critical truth: cybersecurity is an ongoing battle, requiring constant vigilance and adaptation. While the technical aspects are crucial, the human element – user education, strong passwords, and multi-factor authentication – remains paramount. By understanding the attack vectors, implementing robust security measures, and staying informed about emerging threats, organizations can significantly reduce their risk.
Don’t wait for a breach to happen; proactive security is the best defense. Take control, strengthen your defenses, and protect your valuable data.
Popular Questions
What types of data are most at risk in a Citrix server breach?
Sensitive data like customer information, financial records, intellectual property, and confidential business documents are all at significant risk.
How long does it typically take to patch a Citrix vulnerability?
Patching time varies depending on the complexity of the vulnerability and the size of the organization’s infrastructure, but it can range from hours to days or even weeks.
Are there any free tools available to help assess Citrix server security?
While comprehensive security assessments often require paid tools, some free open-source tools can offer basic vulnerability scanning capabilities.
What is the role of insurance in mitigating the financial impact of a Citrix server breach?
Cybersecurity insurance can help cover the costs associated with a breach, including legal fees, data recovery, and notification costs, but policies vary greatly.