Cloud Environments Blamed for Security Vulnerabilities
Cloud environments blamed for security vulnerabilities? It’s a headline we’re seeing more and more, and it’s a chilling reality. The promise of scalability and cost-effectiveness in the cloud comes with a hefty price tag if security isn’t a top priority. From misconfigurations leaving gaping holes in your defenses to insider threats and third-party risks, the cloud presents a unique set of challenges.
This post dives deep into the most common culprits behind cloud security breaches, exploring the root causes and offering practical strategies to bolster your cloud security posture. We’ll look at real-world examples, best practices, and even delve into the complexities of different cloud service models.
We’ll examine how seemingly minor misconfigurations can lead to major data breaches, the importance of robust monitoring and logging, and the critical role of employee training. We’ll also discuss the often-overlooked risks associated with third-party vendors and the need for comprehensive security policies and controls. By the end, you’ll have a clearer understanding of the vulnerabilities inherent in cloud environments and a roadmap for mitigating them.
Misconfigurations in Cloud Environments
Cloud computing offers incredible scalability and flexibility, but its inherent complexity introduces significant security risks. One of the most prevalent sources of these risks stems from misconfigurations within the cloud environment itself. These errors, often unintentional, can expose sensitive data, compromise applications, and leave organizations vulnerable to attacks. Understanding common misconfigurations and implementing robust security practices is crucial for mitigating these threats.
Common Misconfigurations Leading to Security Vulnerabilities
Incorrectly configured cloud resources are a major security weakness. These misconfigurations range from overly permissive access controls to improperly secured storage buckets and exposed databases. For instance, leaving default credentials unchanged on virtual machines or databases is a common oversight with potentially devastating consequences. Similarly, failing to properly configure firewalls or network segmentation can expose entire networks to unauthorized access.
Another frequent mistake involves neglecting to encrypt data at rest and in transit, leaving sensitive information vulnerable to theft or unauthorized disclosure. These seemingly small oversights can lead to significant breaches.
Examples of Misconfigured Access Controls and Their Consequences
Misconfigured access controls represent a substantial threat. Imagine a scenario where an organization grants excessive permissions to a cloud storage bucket. Instead of restricting access to only authorized personnel, they grant public read access. The result could be the exposure of sensitive customer data, intellectual property, or confidential business information, leading to significant legal and financial repercussions. Similarly, improperly configured IAM (Identity and Access Management) roles can allow malicious actors to escalate privileges and gain unauthorized access to critical systems and data.
A lack of least privilege principle application—granting only the necessary permissions to users and applications—is a frequent cause of such breaches.
Best Practices for Securing Cloud Infrastructure Configurations
Implementing robust security practices is essential for mitigating the risks associated with cloud misconfigurations. This starts with a strong emphasis on the principle of least privilege, granting only the minimum necessary permissions to users, applications, and services. Regular security audits and penetration testing are vital for identifying and addressing vulnerabilities before they can be exploited. Automation plays a crucial role in configuration management, ensuring consistency and reducing the risk of human error.
Employing infrastructure-as-code (IaC) tools allows for the automated provisioning and management of cloud resources, enforcing consistent security policies across the entire environment. Furthermore, robust logging and monitoring capabilities are essential for detecting and responding to security incidents promptly. Regularly reviewing and updating security policies and procedures is crucial for maintaining a secure cloud environment.
Comparison of Security Risks Across Cloud Service Models
| Service Model | Misconfiguration Type | Vulnerability | Mitigation Strategy |
|---|---|---|---|
| IaaS (Infrastructure as a Service) | Improperly configured firewalls | Unauthorized network access | Implement robust firewall rules, regular security audits, and intrusion detection systems. |
| PaaS (Platform as a Service) | Insufficiently secured databases | Data breaches, SQL injection attacks | Utilize database encryption, access control lists, and regular security patching. |
| SaaS (Software as a Service) | Weak password policies | Account takeovers, data breaches | Enforce strong password policies, multi-factor authentication (MFA), and regular security awareness training. |
| IaaS | Unpatched operating systems | Exploitation of known vulnerabilities | Implement automated patching processes and regular vulnerability scanning. |
| PaaS | Misconfigured application settings | Denial of service attacks, data exposure | Follow secure coding practices, utilize application security testing tools, and regularly review application configurations. |
| SaaS | Lack of data encryption in transit | Data interception, eavesdropping | Ensure that the SaaS provider uses HTTPS and encrypts data in transit. Verify their security certifications. |
Data Breaches and Leaks in the Cloud
The seemingly limitless scalability and accessibility of cloud environments unfortunately also present expanded attack surfaces for malicious actors. Data breaches, once a concern primarily for on-premise systems, are now a significant threat in the cloud, demanding robust security measures and incident response plans. Understanding the various vectors of attack and the devastating consequences is crucial for organizations relying on cloud services.
Causes of Cloud Data Breaches
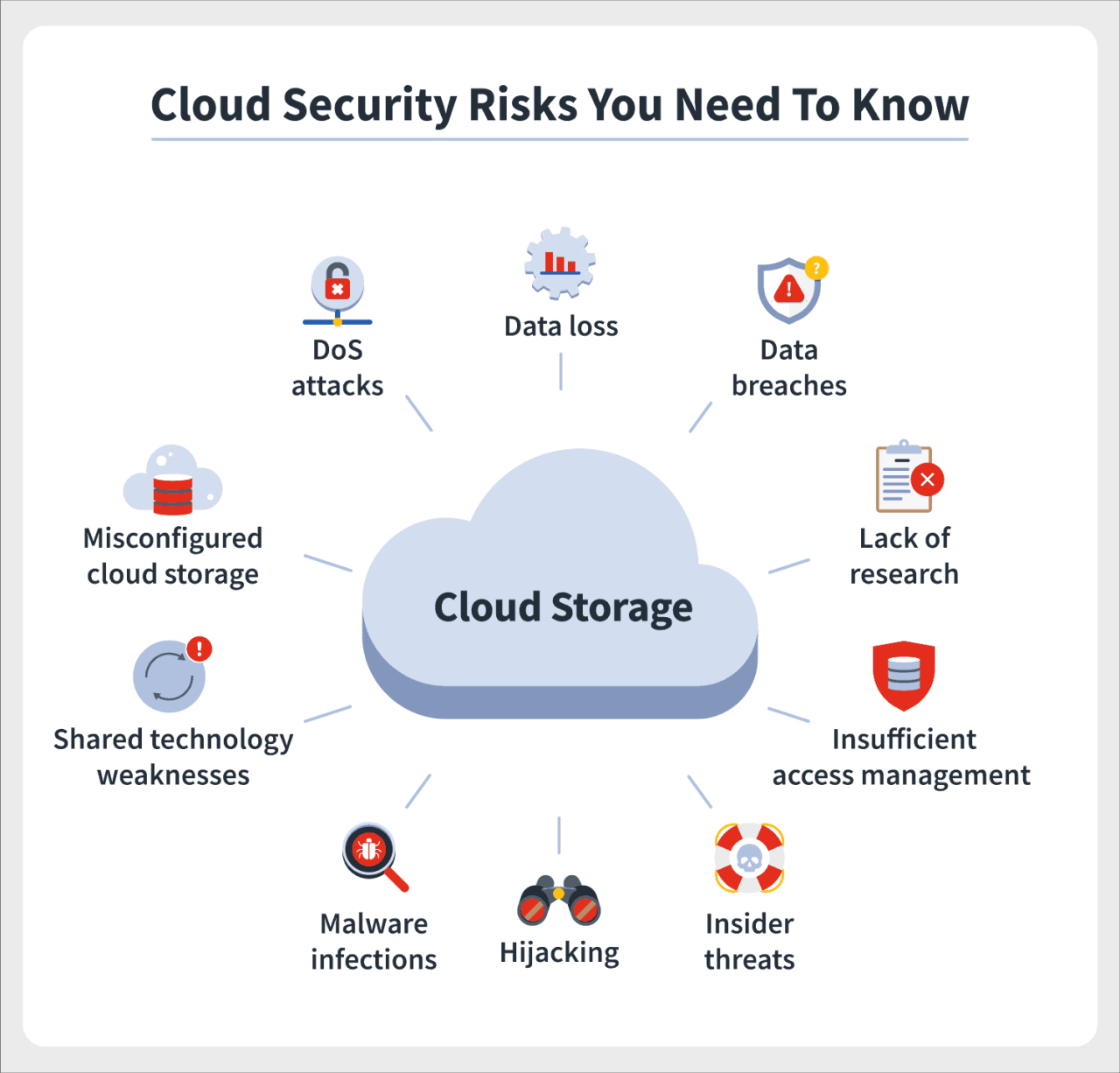
Data breaches in cloud environments can stem from a multitude of sources, often intertwined and complex. These breaches aren’t always the result of sophisticated hacking; surprisingly often, they’re caused by human error or inadequate security configurations. Understanding these root causes is the first step toward mitigation. Some key causes include misconfigured cloud storage, insecure APIs, compromised credentials, insider threats, and vulnerabilities in third-party applications integrated with cloud services.
The shared responsibility model of cloud security, where responsibility is divided between the cloud provider and the customer, further complicates the matter, as organizations often struggle to understand where their responsibilities begin and end.
Examples of Real-World Cloud Data Breaches
Several high-profile data breaches highlight the real-world consequences of cloud security failures. For instance, the 2017 Equifax breach, although not solely a cloud-related incident, involved a vulnerability in their Apache Struts framework, exposing sensitive personal information of millions. Similarly, the 2018 Capital One breach saw a misconfigured cloud firewall exploited, resulting in a massive data leak. These examples underscore the significant impact even seemingly small misconfigurations can have.
The scale of these breaches, in terms of the number of individuals affected and the financial repercussions for the organizations involved, demonstrates the critical need for robust security practices.
Impact of Data Breaches on Organizations
The impact of a cloud data breach extends far beyond immediate financial losses. Organizations face significant reputational damage, potentially leading to a loss of customer trust and business. Regulatory fines and legal battles can further strain resources. In addition to these direct costs, there are indirect costs associated with incident response, remediation, and the potential for long-term damage to brand reputation.
The recovery process can be lengthy and expensive, requiring significant investment in security enhancements and potentially impacting future business opportunities. Furthermore, the emotional distress experienced by affected individuals, particularly in cases involving sensitive personal information, should not be underestimated.
Cloud Data Breach Incident Response Flowchart
The following describes a typical cloud data breach incident response process. Imagine this as a flowchart, with each step leading logically to the next.
1. Detection
It’s become a common refrain: cloud environments are blamed for a surge in security vulnerabilities. But proactive measures exist! To combat this, solutions like cloud security posture management (CSPM) are crucial, and learning about bitglass and the rise of cloud security posture management is a great starting point. Ultimately, understanding and implementing robust CSPM strategies is key to mitigating the risks associated with cloud environments and preventing those security breaches we hear so much about.
The breach is identified, perhaps through internal monitoring, external security alerts, or user reports.
2. Containment
Immediate steps are taken to isolate the compromised systems and prevent further data exfiltration.
3. Eradication
The root cause of the breach is identified and addressed, including patching vulnerabilities and removing malware.
4. Recovery
Systems are restored to a secure state, and data is recovered or rebuilt as necessary.
5. Post-Incident Activity
A thorough post-incident review is conducted to identify lessons learned and implement preventative measures. This includes documenting the incident, updating security policies, and retraining staff.
6. Notification
Affected individuals and regulatory bodies are notified, as required by law.
Third-Party Risks and Vulnerabilities
Relying on third-party cloud services offers significant advantages in terms of scalability, cost-effectiveness, and specialized expertise. However, this reliance introduces a new layer of security risk that organizations must carefully manage. The security posture of your cloud environment is only as strong as the weakest link in your third-party ecosystem. A breach in a vendor’s systems can have devastating consequences for your organization, potentially leading to data loss, financial penalties, and reputational damage.Third-party cloud services introduce several potential security vulnerabilities.
These range from inadequate security practices on the vendor’s side, such as weak access controls or insufficient data encryption, to vulnerabilities within the third-party’s software or infrastructure. The complexity of modern cloud architectures, with their interconnected services and dependencies, can make identifying and mitigating these risks challenging. Furthermore, the lack of complete visibility into a vendor’s internal security practices can leave organizations exposed to unforeseen threats.
Security Measures for Third-Party Cloud Vendors
Organizations should implement robust security measures when collaborating with third-party cloud vendors. These measures should go beyond simply trusting vendor claims and delve into concrete verification and ongoing monitoring. A key aspect is establishing clear security requirements and expectations within service level agreements (SLAs). These SLAs should explicitly define responsibilities for security, incident response, and data protection. Regular security audits and penetration testing of the vendor’s systems should also be part of the agreement, providing independent verification of their security posture.
So many security breaches are attributed to misconfigurations in cloud environments, it’s becoming a real headache. But what if we could build more secure apps faster? That’s where exploring options like domino app dev, the low-code and pro-code future , comes in. Perhaps a shift towards more controlled development environments could help mitigate some of the cloud security risks we’re seeing.
Furthermore, organizations need to establish processes for monitoring the vendor’s performance and compliance with agreed-upon security measures. This continuous monitoring is crucial for early detection of any potential security issues.
The Importance of Thorough Vendor Due Diligence
Thorough vendor due diligence is paramount in mitigating third-party risks in cloud security. This involves a comprehensive assessment of the vendor’s security practices, including their infrastructure security, data protection policies, incident response plans, and compliance certifications (e.g., ISO 27001, SOC 2). Due diligence should also encompass an evaluation of the vendor’s overall reputation, financial stability, and the security track record of their client base.
It’s not enough to rely on self-reported information; independent verification and references from other clients are essential. The process should involve a careful review of their security documentation, potentially including site visits to their facilities for a firsthand assessment. Failing to conduct thorough due diligence can lead to significant security vulnerabilities and expose your organization to substantial risks.
For example, choosing a vendor with a history of data breaches could expose your sensitive data to similar threats.
Best Practices for Managing Third-Party Risks
A robust strategy for managing third-party risks requires a multi-faceted approach. The following best practices can help organizations effectively address these challenges:
- Establish a formal third-party risk management program: This program should define clear processes for selecting, onboarding, monitoring, and offboarding vendors.
- Conduct thorough risk assessments: Regularly assess the risks associated with each third-party vendor, considering factors such as the sensitivity of the data being processed and the vendor’s security controls.
- Negotiate strong security clauses in contracts: Include specific security requirements and responsibilities in all contracts with third-party vendors.
- Implement continuous monitoring and auditing: Regularly monitor the vendor’s security posture and conduct periodic security audits to verify compliance.
- Establish clear incident response procedures: Develop a plan for responding to security incidents involving third-party vendors, including communication protocols and escalation paths.
- Maintain a comprehensive inventory of third-party vendors: Keep a detailed record of all third-party vendors used, including their services, security controls, and contact information.
- Prioritize vendors based on risk: Focus resources on managing the risks associated with the most critical third-party vendors.
Lack of Visibility and Monitoring
The sheer scale and complexity of modern cloud environments present significant challenges to maintaining comprehensive visibility. Unlike on-premise systems, cloud resources are often distributed across multiple regions, providers, and even different account structures. This decentralized nature makes it difficult to gain a unified, real-time view of all assets, configurations, and activities. Without this holistic perspective, organizations are blind to potential security weaknesses and threats.The dynamic nature of cloud resources further complicates visibility.
Instances spin up and down, configurations change frequently, and new services are constantly being added. Tracking these changes manually is simply not feasible, requiring automated solutions to maintain a current understanding of the environment. A lack of proper visibility directly impacts the effectiveness of security measures.
Challenges in Maintaining Visibility into Cloud Environments
The dynamic and distributed nature of cloud environments makes comprehensive visibility extremely difficult to achieve. The sheer volume of data generated by cloud resources, combined with the complexity of integrating various security tools and services, can overwhelm security teams. Furthermore, the reliance on third-party providers introduces additional layers of complexity and reduces an organization’s direct control over its security posture.
A lack of standardized logging and monitoring practices across different cloud platforms exacerbates these issues. Finally, a skills gap within security teams often prevents organizations from effectively leveraging the advanced monitoring capabilities available in modern cloud environments.
Examples of Inadequate Monitoring Leading to Undetected Security Breaches
Inadequate monitoring can allow attackers to remain undetected for extended periods. For example, an attacker might exploit a misconfigured S3 bucket (Amazon S3) containing sensitive data. Without proper monitoring and alerting, this breach might go unnoticed until the data is already compromised and shared publicly. Similarly, a compromised virtual machine (VM) could act as a foothold for lateral movement within the cloud environment.
If the monitoring system fails to detect unusual network traffic or login attempts from the compromised VM, the attacker could move undetected to other sensitive resources. Another scenario involves insufficient logging of API calls, which could mask malicious activity. Without proper logging and analysis, unauthorized access or data exfiltration attempts might go entirely unnoticed.
Best Practices for Implementing Effective Cloud Security Monitoring and Logging
Implementing a robust cloud security monitoring and logging strategy requires a multi-faceted approach. This begins with centralized logging, aggregating logs from various cloud services and on-premise systems into a single platform for easier analysis. Real-time threat detection is crucial; utilizing security information and event management (SIEM) tools to analyze log data for suspicious activity is vital. Continuous monitoring of cloud configurations is essential to identify and address misconfigurations promptly.
Automated security assessments, including vulnerability scanning and penetration testing, should be performed regularly to identify and mitigate potential weaknesses. Finally, a well-defined incident response plan is necessary to handle security incidents effectively. This plan should Artikel procedures for detecting, investigating, and remediating security breaches.
Creating a Comprehensive Cloud Security Monitoring Dashboard
A hypothetical cloud security monitoring dashboard could display key metrics using various visualizations. A geographical heatmap could show the location of all cloud resources, highlighting any unusual concentrations or anomalies. A real-time dashboard displaying CPU utilization, network traffic, and storage usage of critical resources would help detect unusual spikes indicating potential attacks. A graph visualizing the number of security alerts over time could reveal trends and patterns in threat activity.
A table displaying the status of security assessments, including the number of vulnerabilities identified and their severity levels, would provide an overview of the organization’s security posture. Finally, a customizable dashboard could allow users to filter and sort data based on specific criteria, providing a tailored view of the security landscape. For example, the dashboard might show that the ‘US-East-1’ region has experienced a significant increase in network traffic in the last hour, triggering an alert, while a specific VM is showing unusually high CPU usage, potentially indicating a malware infection.
The dashboard would integrate with the organization’s SIEM and other security tools, providing a consolidated view of security events and alerts.
Insider Threats and Employee Negligence
The cloud, while offering incredible scalability and flexibility, introduces new avenues for security breaches. One of the most significant and often overlooked risks stems from insider threats and employee negligence. These vulnerabilities aren’t always malicious; sometimes, a simple mistake can have devastating consequences. Understanding these risks and implementing preventative measures is crucial for maintaining a secure cloud environment.Employee negligence can manifest in various ways, significantly impacting cloud security.
A seemingly minor oversight can expose sensitive data or compromise the entire system. This section will explore the role of insider threats and employee negligence, provide concrete examples, and highlight the importance of robust security awareness training.
Examples of Employee Negligence Compromising Cloud Security
Negligence isn’t always intentional malice; it’s often a result of insufficient training, lack of awareness, or simply human error. Examples include accidentally sharing sensitive data via unsecured channels (like personal email), failing to implement strong passwords or multi-factor authentication, leaving devices unattended, or clicking on phishing links. For instance, an employee might inadvertently download malware onto their work laptop, granting attackers access to the company’s cloud resources.
Another example could be an employee using their personal device to access sensitive cloud data without utilizing a VPN, opening a pathway for attackers to intercept the information. These seemingly small mistakes can have catastrophic results.
The Importance of Security Awareness Training for Cloud Users
Comprehensive security awareness training is paramount to mitigating the risks associated with insider threats and employee negligence. Training should cover a wide range of topics, including password security, phishing awareness, data loss prevention techniques, and the importance of following company security policies. Regular training sessions, coupled with simulated phishing attacks and regular assessments, can significantly improve employee awareness and reduce the likelihood of accidental breaches.
The training should be tailored to the specific roles and responsibilities of employees, focusing on the potential risks and consequences of their actions. For example, developers should receive training on secure coding practices, while administrative staff should be educated on the importance of access control and privilege management.
Hypothetical Scenario: Insider Threat Mitigation
Imagine a scenario where a disgruntled employee, Sarah, has access to the company’s cloud storage containing sensitive customer data. Feeling overlooked and undervalued, she decides to download a significant portion of this data onto a personal USB drive. This act constitutes a serious insider threat.To mitigate this risk, several measures could have been in place: Firstly, implementing robust access control policies, limiting Sarah’s access to only the data necessary for her role.
Secondly, employing data loss prevention (DLP) tools that monitor and block unauthorized data transfers. Thirdly, regular security audits and monitoring of employee activity could have detected Sarah’s unusual behavior. Finally, a strong security awareness training program might have discouraged Sarah from engaging in such actions by emphasizing the severity of the consequences. The combination of these preventative measures significantly reduces the likelihood of successful insider threats and minimizes their impact.
Insufficient Security Controls and Policies

A robust security posture in the cloud isn’t just about deploying the latest technology; it hinges on comprehensive security policies and controls. Without a well-defined framework, even the most advanced security tools become ineffective, leaving your cloud environment vulnerable to a range of threats. This section delves into the importance of establishing and maintaining strong security controls and policies, comparing different frameworks, and outlining the elements of a truly effective cloud security policy.The importance of comprehensive security policies and controls cannot be overstated.
They provide a structured approach to managing risk, ensuring compliance with regulations, and maintaining the confidentiality, integrity, and availability of your data and systems. A strong policy framework acts as a roadmap, guiding decisions and actions related to security, ensuring consistency across the organization and minimizing the chances of human error. It also serves as a crucial element in demonstrating due diligence in the event of a security incident.
Cloud Security Control Frameworks: NIST vs. ISO 27001
Several frameworks offer guidance on establishing and implementing effective cloud security controls. Two of the most widely recognized are the National Institute of Standards and Technology (NIST) Cybersecurity Framework and ISO/IEC NIST provides a flexible, risk-based approach focusing on identifying, assessing, and mitigating cybersecurity risks. It categorizes security activities into five core functions: Identify, Protect, Detect, Respond, and Recover.
ISO 27001, on the other hand, is a globally recognized standard that establishes an Information Security Management System (ISMS). It provides a detailed framework for establishing, implementing, maintaining, and continually improving an organization’s information security. While both frameworks are valuable, the choice depends on specific organizational needs and regulatory requirements. For instance, organizations subject to specific government regulations might find NIST more applicable, while others might prefer the more comprehensive and internationally recognized ISO 27001 standard.
Elements of a Robust Cloud Security Policy
A robust cloud security policy must encompass several key elements to be truly effective. It needs to clearly define roles and responsibilities, outlining who is accountable for specific security tasks and ensuring clear lines of communication. The policy should detail acceptable use of cloud resources, outlining what activities are permitted and prohibited. Data security is paramount, so the policy should include specific guidelines on data encryption, access control, and data loss prevention.
Regular security assessments and audits are also crucial, and the policy should specify the frequency and scope of these activities. Finally, a comprehensive incident response plan is vital, outlining procedures for handling security breaches and ensuring a swift and effective response. This plan should cover everything from initial detection to recovery and post-incident analysis.
Sample Cloud Security Policy Document, Cloud environments blamed for security vulnerabilities
The following Artikels key principles and procedures for a sample cloud security policy. This is a simplified example and should be adapted to the specific needs and context of each organization.
Principle 1: Data Security: All sensitive data stored in the cloud must be encrypted both in transit and at rest. Access to data will be granted based on the principle of least privilege. Regular data loss prevention (DLP) scans will be conducted.
Principle 2: Access Control: Strong passwords and multi-factor authentication (MFA) will be mandatory for all cloud accounts. Access will be regularly reviewed and revoked when no longer needed. Role-Based Access Control (RBAC) will be implemented to manage user permissions effectively.
Principle 3: Security Assessments: Regular vulnerability scans and penetration testing will be conducted to identify and mitigate security weaknesses. Results will be reviewed and addressed promptly.
Principle 4: Incident Response: A comprehensive incident response plan will be in place, outlining procedures for handling security incidents, including breach notification and recovery. Regular incident response drills will be conducted.
Principle 5: Compliance: The organization will comply with all relevant data privacy regulations and security standards.
This sample policy highlights the crucial elements; a complete policy would require far greater detail and specificity tailored to the unique characteristics of the organization and its cloud environment. Regular review and updates are vital to ensure the policy remains effective and relevant.
Closing Notes: Cloud Environments Blamed For Security Vulnerabilities
Securing your cloud environment isn’t a one-time fix; it’s an ongoing process requiring vigilance, proactive measures, and a deep understanding of the ever-evolving threat landscape. From meticulously configuring access controls and implementing robust monitoring to fostering a strong security culture within your organization and carefully vetting third-party vendors, the journey to a secure cloud demands commitment. While the challenges are real, the rewards of a well-protected cloud infrastructure are immeasurable – protecting your data, your reputation, and ultimately, your business.
FAQ
What are the most common types of cloud misconfigurations?
Common misconfigurations include improperly configured access controls (e.g., overly permissive permissions), insecure storage of sensitive data, and lack of proper encryption.
How can I improve my cloud security monitoring?
Implement robust logging, utilize security information and event management (SIEM) tools, and establish automated alerts for suspicious activity.
What’s the best way to manage third-party risks in the cloud?
Conduct thorough due diligence on vendors, enforce strict security requirements in contracts, and regularly audit their security practices.
How can I prevent insider threats?
Implement strong access controls, conduct regular security awareness training for employees, and establish clear security policies.





