
Cloud Security Alliance Cautions on Quantum Computing Safety
Cloud Security Alliance cautions on the safety of quantum computing – a statement that’s sent ripples through the tech world. The rise of quantum computing, while promising incredible advancements, presents a serious threat to our current cybersecurity infrastructure. We’re talking about the potential for quantum computers to crack the encryption methods that protect our most sensitive data – think banking details, medical records, even national secrets.
This post dives into the CSA’s concerns, explores the vulnerabilities, and examines what we can do to prepare for this quantum leap into a potentially less secure future.
The Cloud Security Alliance (CSA) has highlighted critical vulnerabilities in our current cloud security systems, particularly concerning the impending threat of quantum computing. They’ve pinpointed specific encryption algorithms that are susceptible to quantum attacks, emphasizing the urgent need for proactive measures. This isn’t just a futuristic worry; the potential for widespread data breaches is real and growing closer with each quantum computing advancement.
We’ll delve into the specifics of these vulnerabilities, exploring the types of encryption at risk and the potential impact on both symmetric and asymmetric encryption methods.
The Cloud Security Alliance’s Statement
The Cloud Security Alliance (CSA), a leading organization in cloud security best practices, has issued several warnings regarding the potential threats posed by quantum computing to existing cloud security infrastructure. Their concerns aren’t about immediate, widespread attacks, but rather a future where sufficiently powerful quantum computers could render many current cryptographic methods obsolete, leaving cloud data and services vulnerable.
This necessitates proactive measures to prepare for this inevitable shift in the technological landscape.The CSA’s statements highlight the critical need for a paradigm shift in cloud security strategies, urging organizations to begin preparing for a post-quantum world now, rather than reacting to a crisis later. The potential disruption is significant, impacting everything from data confidentiality to system integrity.
Vulnerabilities in Existing Cloud Security Infrastructure
The CSA emphasizes that many widely used cryptographic algorithms, currently considered secure, will be easily broken by sufficiently advanced quantum computers. This includes algorithms underpinning public key infrastructure (PKI), which is foundational to securing numerous cloud services, such as secure communication channels (HTTPS), digital signatures, and authentication protocols. The threat extends beyond PKI; symmetric encryption algorithms, although generally stronger than asymmetric ones, could also become vulnerable with the advent of sufficiently powerful quantum computers.
The CSA’s analysis points to a significant risk to data confidentiality, integrity, and authenticity across the cloud ecosystem. Existing digital signatures used for software integrity verification and transaction authentication, for instance, could be easily forged, leading to serious security breaches.
CSA Recommended Actions and Preventative Measures
The CSA doesn’t advocate for a complete overhaul of cloud security immediately. Instead, they recommend a phased approach focusing on preparedness and migration. This involves several key strategies. Firstly, organizations should conduct thorough risk assessments to identify systems and data most vulnerable to post-quantum attacks. This risk assessment should consider the sensitivity of the data, the potential impact of a breach, and the timeline for quantum computing advancements.Secondly, the CSA strongly advocates for adopting post-quantum cryptography (PQC) algorithms.
These are cryptographic algorithms designed to be resistant to attacks from both classical and quantum computers. Several PQC algorithms are currently under standardization by NIST (National Institute of Standards and Technology), and integrating these into cloud systems is crucial. This transition should be carefully planned and implemented, considering compatibility issues and the potential need for software and hardware upgrades.
A gradual migration, starting with the most sensitive data and systems, is a prudent strategy.Finally, the CSA highlights the importance of collaboration and information sharing. Open communication between cloud providers, security vendors, and researchers is vital for accelerating the development and deployment of PQC solutions. Sharing best practices and threat intelligence will collectively strengthen the cloud security posture against future quantum threats.
Regular security audits and penetration testing, incorporating potential quantum attacks into the testing scenarios, are also recommended to proactively identify vulnerabilities.
Quantum Computing’s Threat Landscape

The advent of powerful quantum computers presents a significant threat to the security of our digital world, particularly within the cloud. Current encryption methods, which underpin the security of countless online services and data, are vulnerable to the computational power of these emerging machines. Understanding this threat landscape is crucial for developing effective mitigation strategies and ensuring the continued security of cloud-based systems.
Vulnerable Cryptographic Algorithms
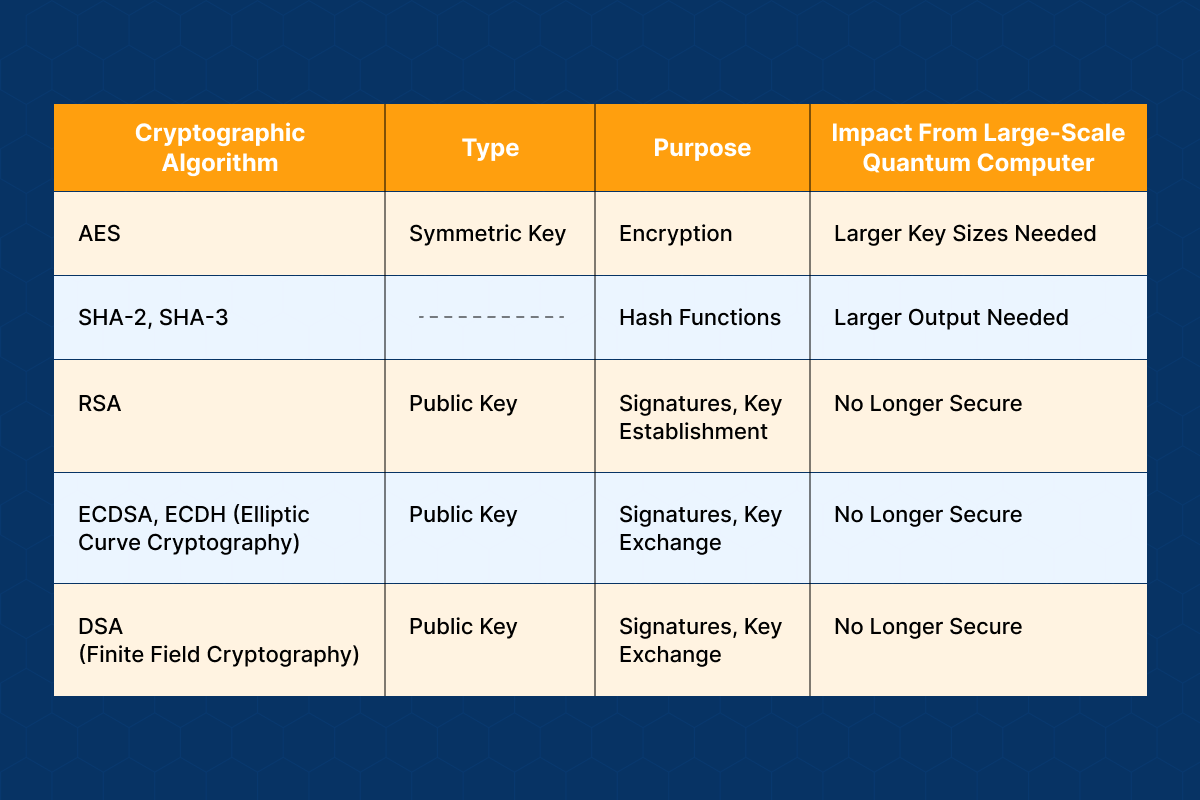
Many widely used cryptographic algorithms rely on the computational difficulty of specific mathematical problems for their security. These problems, while challenging for classical computers, are significantly easier to solve using quantum algorithms. This vulnerability affects both symmetric and asymmetric encryption techniques, impacting various aspects of cloud security, from data-at-rest protection to secure communication channels. The most prominent examples are those based on the difficulty of factoring large numbers (RSA) or the discrete logarithm problem (DSA, ECC).
Quantum Computer’s Impact on Encryption Methods
Quantum computers, leveraging algorithms like Shor’s algorithm, can efficiently solve the mathematical problems that underpin the security of many current encryption methods. For instance, Shor’s algorithm can factor large numbers exponentially faster than the best-known classical algorithms. This means that RSA encryption, widely used to secure online transactions and protect sensitive data, could be broken by a sufficiently powerful quantum computer.
Similarly, the elliptic curve cryptography (ECC), often preferred for its efficiency in mobile and embedded systems, also faces significant vulnerabilities under quantum attack. Imagine a scenario where a quantum computer breaks the encryption protecting a major cloud provider’s database – the consequences could be catastrophic, leading to data breaches, financial losses, and reputational damage. The impact extends beyond individual systems; the compromise of a single, critical system could trigger a chain reaction, destabilizing entire networks.
Comparison of Symmetric and Asymmetric Encryption Vulnerability
The potential impact of quantum computing varies depending on the type of encryption used. Symmetric encryption, which uses the same key for encryption and decryption, is generally considered more resilient to quantum attacks than asymmetric encryption. However, this is not an absolute guarantee, and even symmetric algorithms could be vulnerable to specialized quantum attacks, depending on the key length and the specific algorithm used.
Asymmetric encryption, which relies on a pair of keys (public and private), is significantly more vulnerable because the underlying mathematical problems are directly susceptible to Shor’s algorithm.
| Algorithm Type | Current Security Level | Vulnerability to Quantum Attacks | Mitigation Strategies |
|---|---|---|---|
| RSA (Asymmetric) | High (with sufficiently large key sizes) | High (Shor’s algorithm) | Transition to post-quantum cryptography; increase key sizes (temporary measure) |
| ECC (Asymmetric) | High (with appropriately sized curves) | High (Shor’s algorithm) | Transition to post-quantum cryptography; increase key sizes (temporary measure) |
| AES (Symmetric) | High (with sufficiently large key sizes) | Medium (Grover’s algorithm reduces security by a square root factor) | Increase key sizes; explore post-quantum symmetric algorithms |
| Triple DES (Symmetric) | Low | Low to Medium | Do not use; migrate to AES or post-quantum cryptography |
Post-Quantum Cryptography (PQC)
The advent of quantum computers poses a significant threat to current cryptographic systems. These powerful machines could break widely used algorithms like RSA and ECC, jeopardizing the security of sensitive data and online transactions. Post-quantum cryptography (PQC) aims to develop cryptographic algorithms resistant to attacks from both classical and quantum computers, ensuring future security in a post-quantum world.
The transition to PQC is a complex undertaking, requiring careful consideration of various algorithms and their implications.Post-quantum cryptography encompasses a range of techniques based on mathematical problems believed to be hard even for quantum computers. These algorithms are currently undergoing rigorous testing and standardization to ensure their suitability for widespread adoption. Several promising candidates are emerging, each with its own strengths and weaknesses.
Promising Post-Quantum Cryptography Algorithms
Several algorithms are currently under consideration for standardization, offering diverse approaches to post-quantum security. These algorithms represent different mathematical hard problems, providing a level of diversification crucial for robust security. Choosing a single algorithm would be risky, so a diverse portfolio of algorithms is being developed and evaluated.
- Lattice-based cryptography: This approach relies on the hardness of finding short vectors in high-dimensional lattices. Examples include CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Dilithium (for digital signatures). These algorithms offer relatively good performance and are considered strong candidates for standardization.
- Code-based cryptography: This family of algorithms leverages the difficulty of decoding random linear codes. McEliece is a prominent example, offering strong security but often with higher computational overhead compared to lattice-based methods.
- Multivariate cryptography: This approach uses the difficulty of solving systems of multivariate polynomial equations over finite fields. Algorithms like Rainbow are examples of this type, but concerns about security have led to some being dropped from consideration.
- Hash-based cryptography: This method uses cryptographic hash functions to create digital signatures. While offering strong security, these algorithms often have limitations in terms of performance and key sizes, making them suitable for specific applications rather than widespread general use.
Challenges and Limitations of PQC Adoption
The transition to PQC is not without its challenges. Widespread adoption requires overcoming significant hurdles in terms of implementation, performance, and interoperability.The performance overhead of some PQC algorithms can be considerably higher than their classical counterparts. This can impact the speed and efficiency of applications, particularly in resource-constrained environments. Furthermore, the larger key sizes associated with many PQC algorithms can lead to increased storage requirements and communication bandwidth consumption.
Interoperability issues arise from the variety of algorithms being considered; ensuring seamless integration across different systems and platforms is crucial. Finally, the cryptographic agility needed to migrate systems and maintain security during the transition poses a major logistical and operational challenge. For example, migrating legacy systems to support PQC might require significant investment in software updates and infrastructure upgrades.
Organizations need to plan and execute this transition carefully, considering the potential costs and disruption.
Performance and Security Trade-offs in PQC Algorithms, Cloud security alliance cautions on the safety of quantum computing
Different PQC algorithms offer varying levels of performance and security. There is often a trade-off between these two factors. For example, lattice-based algorithms generally provide good performance but may require larger key sizes compared to code-based algorithms, which offer strong security but often with higher computational overhead. Multivariate algorithms present a range of complexities, with some exhibiting promising performance while others have raised security concerns.
Hash-based signatures offer strong security but are typically less efficient than other approaches. The choice of algorithm will depend on the specific application’s security requirements and performance constraints. A risk-based approach, carefully considering the trade-offs, is essential for selecting appropriate algorithms.
Impact on Cloud Security Architectures: Cloud Security Alliance Cautions On The Safety Of Quantum Computing

The advent of quantum computing presents a significant challenge to existing cloud security architectures. The potential for quantum computers to break widely used public-key cryptography algorithms necessitates a proactive and comprehensive approach to securing cloud environments. This involves not only adopting Post-Quantum Cryptography (PQC) but also re-evaluating and strengthening various aspects of cloud security design. Failure to adapt could leave cloud-based systems vulnerable to devastating attacks.A hypothetical cloud security architecture incorporating PQC and other quantum-resistant security measures would need to be layered and robust.
This involves integrating multiple security controls to mitigate risks at various points in the system. The reliance on solely one security measure is highly discouraged, given the potential for unforeseen vulnerabilities.
A Hypothetical Quantum-Resistant Cloud Security Architecture
This architecture prioritizes a defense-in-depth strategy, combining various security measures to provide multiple layers of protection. It begins with secure hardware, moves through secure communication channels, and ends with robust authentication and authorization systems. The foundation of this architecture is the transition to PQC algorithms for encryption and digital signatures. This transition, however, needs to be carefully planned and implemented to avoid disruption and compatibility issues.
Furthermore, regular security audits and penetration testing, specifically designed to test against quantum-resistant algorithms and techniques, are essential. This allows for early identification and remediation of vulnerabilities before they can be exploited. The architecture would also incorporate advanced threat detection systems capable of identifying anomalies that could indicate a quantum-based attack. Finally, a robust incident response plan, tailored to handle quantum-related security breaches, is crucial.
Changes Required to Existing Cloud Infrastructure
Adapting existing cloud infrastructure to the threat of quantum computing requires a multi-faceted approach. The most immediate change involves transitioning from current cryptographic algorithms to PQC alternatives. This requires updates to all software and hardware components that rely on public-key cryptography. For example, VPNs, TLS/SSL connections, and digital signature systems all need to be updated to support PQC algorithms.
The Cloud Security Alliance’s warnings about quantum computing’s potential to crack current encryption are pretty serious, making me think about the future of secure app development. Building robust, secure apps is crucial, and that’s where platforms like Domino come in; check out this great article on domino app dev the low code and pro code future to see how they’re tackling this.
Ultimately, the CSA’s concerns highlight the need for innovative approaches to security in our increasingly complex digital world.
Beyond cryptography, significant changes are also needed in the way cloud systems are designed and managed. This includes implementing stricter access control measures, enhancing intrusion detection systems, and developing quantum-resistant key management systems. The adoption of hardware security modules (HSMs) that support PQC is also crucial for securing cryptographic keys. Finally, extensive training for cloud security personnel is essential to ensure they understand the implications of quantum computing and are equipped to handle the new security challenges.
Consider the example of a large financial institution migrating its cloud infrastructure: this would require significant investment in updating software, hardware, and employee training, all to ensure their sensitive data remains secure in the quantum era.
Costs and Complexities of Upgrading Cloud Systems
Upgrading cloud systems to be quantum-resistant is a complex and costly undertaking. The cost will vary depending on the size and complexity of the cloud infrastructure, the specific PQC algorithms chosen, and the level of security required. Consider the potential costs associated with software updates, hardware upgrades, employee training, and the development of new security protocols. These costs can be substantial, particularly for large organizations with extensive cloud deployments.
Furthermore, the complexity of integrating PQC into existing systems should not be underestimated. The transition to PQC algorithms requires careful planning and execution to avoid compatibility issues and service disruptions. Testing and validation of the upgraded systems are also critical to ensure that they are truly quantum-resistant. The complexity is further compounded by the lack of standardization in PQC algorithms, making interoperability a significant concern.
For example, a global e-commerce company with a massive cloud infrastructure would face significant challenges and expenses in upgrading its systems to support PQC, potentially affecting its operations and budget significantly. The lack of widely available PQC-ready hardware and software also adds to the complexity and cost.
Regulatory and Governance Aspects
The looming threat of quantum computers capable of breaking current encryption standards necessitates a proactive approach from governments and industry bodies. Failing to adapt regulatory frameworks and establish robust industry standards will leave critical infrastructure and sensitive data vulnerable to attack in the near future. This section explores the crucial role of regulation and governance in mitigating the risks associated with quantum computing.The potential impact of quantum computing on data privacy and security is profound.
Current regulations, designed for classical computing threats, may not adequately address the unique challenges posed by quantum algorithms. This necessitates a reassessment of existing frameworks and the development of new legislation tailored to the quantum era.
Data Privacy Regulation Updates
The General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), among others, focus on protecting data from unauthorized access and breaches using current cryptographic methods. However, these regulations need updating to explicitly address the threat of quantum computers capable of breaking these methods. Future iterations of these laws should mandate the adoption of post-quantum cryptography (PQC) for sensitive data protection, potentially setting timelines for migration and outlining penalties for non-compliance.
This could involve specifying acceptable PQC algorithms and requiring regular audits to ensure their effective implementation. Furthermore, regulations might need to address the potential for quantum computers to be used to retroactively decrypt previously intercepted data, necessitating additional safeguards and incident response protocols.
Government Regulation and Industry Standards
Governments play a vital role in setting the stage for a secure quantum-resistant future. This includes funding research and development in PQC, establishing national cybersecurity strategies that incorporate quantum threats, and fostering collaboration between government agencies, industry, and academia. The development of clear guidelines and standards for PQC implementation is crucial, ensuring interoperability and minimizing fragmentation. International collaboration is also essential to harmonize regulations and prevent a patchwork of disparate approaches.
Examples of this could include collaborative efforts between national standards bodies (like NIST in the US) to agree on common PQC algorithms and best practices.
Best Practices for Quantum Readiness
Organizations must proactively prepare for the quantum computing era. A multi-faceted approach is necessary to minimize vulnerabilities and ensure business continuity.
- Assess Current Cryptographic Infrastructure: Conduct a thorough inventory of all systems and data relying on encryption, identifying vulnerabilities to quantum attacks.
- Develop a Migration Plan to PQC: Establish a roadmap for transitioning to PQC algorithms, considering the complexities of implementation and potential compatibility issues.
- Invest in Quantum-Resistant Technologies: Explore and adopt PQC algorithms certified by trusted authorities like NIST, integrating them into existing systems and applications.
- Enhance Cybersecurity Training and Awareness: Educate employees about the quantum computing threat and the importance of robust security practices.
- Collaborate with Industry Peers and Government Agencies: Engage in information sharing and collaborative efforts to develop and implement effective security strategies.
- Monitor Technological Advancements: Stay abreast of the latest developments in quantum computing and PQC, adapting security measures accordingly.
Future Implications
The long-term impact of quantum computing on cloud security is profound and multifaceted. While still in its nascent stages, the potential for quantum computers to break widely used encryption algorithms poses a significant threat to the confidentiality, integrity, and availability of data stored and processed in the cloud. This necessitates a proactive and adaptable approach to cloud security, moving beyond current practices to anticipate and mitigate the risks posed by this emerging technology.The development and deployment of quantum computers will likely unfold in phases, each bringing its own set of challenges for cloud security.
Understanding this timeline is crucial for effective mitigation strategies.
Timeline of Quantum Computing Advancements and Cloud Security Implications
The advancement of quantum computing is not a linear progression, but rather a series of breakthroughs and incremental improvements. It’s difficult to predict precise dates, but we can Artikel likely stages and their security implications.
- Phase 1 (Next 5-10 years): Focus on niche applications and specialized algorithms. Cloud security impact will be limited to specific sectors (e.g., financial institutions handling high-value transactions) that become early targets for quantum attacks on existing cryptographic systems. This phase will see the initial development and deployment of Post-Quantum Cryptography (PQC) solutions, alongside increased scrutiny of existing cryptographic implementations in cloud environments.
- Phase 2 (10-20 years): More powerful and accessible quantum computers emerge, potentially capable of breaking widely used asymmetric encryption algorithms like RSA and ECC. This phase will necessitate a widespread migration to PQC across all cloud-based systems. We’ll likely see increased regulatory pressure to adopt PQC, alongside a rise in quantum-resistant security solutions and services offered by cloud providers.
- Phase 3 (Beyond 20 years): The potential for large-scale, fault-tolerant quantum computers. This phase could represent a significant paradigm shift in cloud security, potentially requiring fundamental changes to cryptographic architectures and security protocols. The development of entirely new security paradigms based on quantum mechanics might be necessary to safeguard against powerful quantum attacks.
Visual Representation of Cloud Security Evolution
Imagine a graph with time on the x-axis and security strength on the y-axis. The initial curve (representing current cloud security) shows a steady, but relatively gradual increase in security strength, driven by traditional cryptographic methods and security best practices. Around the 10-year mark, a sharp inflection point occurs, representing the increasing threat of quantum computing. The curve then plateaus for a short period, indicating a period of vulnerability as existing cryptographic systems become increasingly susceptible.
The Cloud Security Alliance’s warnings about quantum computing’s potential to break current encryption are seriously concerning. This highlights the urgent need for robust cloud security solutions, and that’s where tools like those discussed in this article on bitglass and the rise of cloud security posture management become incredibly important. Proactive security posture management is crucial to mitigating the risks the CSA has identified, especially as we move towards a future where quantum computing poses a real threat.
Then, a new curve emerges, steeper than the initial one, reflecting the adoption of PQC and the development of new quantum-resistant security measures. This new curve demonstrates a rapid increase in security strength, though potentially not reaching the same level of security as the pre-quantum era due to the inherent challenges of PQC and potential new attack vectors. Finally, a long-term, potentially asymptotic, increase suggests the ongoing development and refinement of quantum-resistant security technologies, adapting to the evolving capabilities of quantum computing.
The image showcases a period of vulnerability, highlighting the urgency of proactive adaptation to the quantum threat. The different slopes of the curves visually represent the different paces of security advancement pre- and post-quantum era.
Epilogue
The Cloud Security Alliance’s warning about quantum computing’s threat to cloud security isn’t just a hypothetical scenario; it’s a call to action. While the technology holds immense promise, the potential for catastrophic data breaches is undeniable. The transition to post-quantum cryptography (PQC) is crucial, but it’s a complex undertaking requiring significant investment and collaboration across industries and governments.
Staying informed, adapting our security strategies, and advocating for robust regulations are vital steps in navigating this evolving landscape and securing our digital future. The journey towards quantum-resistant security is underway, and proactive measures are key to safeguarding our data in the quantum age.
Top FAQs
What is Post-Quantum Cryptography (PQC)?
PQC refers to cryptographic algorithms designed to be secure against attacks from both classical and quantum computers. They are crucial for maintaining data security in the post-quantum era.
How long until quantum computers pose a real threat?
Estimates vary, but experts believe powerful enough quantum computers to break widely used encryption could emerge within the next decade or two. Proactive measures are essential.
What can individuals do to protect themselves?
While individual actions are limited, staying informed about the issue, supporting strong cybersecurity practices from service providers, and advocating for stronger regulations are all helpful.
Are all encryption methods equally vulnerable?
No, some encryption methods are more vulnerable than others. Asymmetric encryption (like RSA) is generally considered more vulnerable to quantum attacks than symmetric encryption (like AES), although both are at risk with sufficiently powerful quantum computers.





